Account takeover (ATO) attacks are one of the most common and damaging cyber threats today. Cybercriminals use various techniques to gain unauthorized access to user accounts, often exploiting weak passwords, stolen credentials, and vulnerabilities in multi-factor authentication (MFA) systems. Once an attacker successfully takes control of an account, they can commit fraud, steal sensitive data, or perform other malicious activities that harm both individuals and organizations.
If you are short of time and just need to glance over the tools we review below, here is our list of the ten best account takeover prevention systems:
- Avanan Account Takeover Prevention EDITOR’S CHOICE This email protection system protects Microsoft Exchange and Gmail against phishing, malware, spam, and scams. This is a cloud-based service with data loss prevention in its highest plan.
- SpyCloud ATO Prevention This provider produces both employee and customer account takeover prevention systems.
- Okta Account protection systems for workforce and customer accounts.
- Sift Account Defense Roots out fake accounts and protects the accounts of genuine users.
- ReliaQuest GreyMatter Digital Risk Protection This platform provides disclosure detection from Dark Web scans and also analysts.
- Radware Bot Manager A detection system for automated attacks that includes account cracking activities.
- TransUnion TruValidate This customer validation system is part of a platform of eCommerce protection systems.
- Experian Fraud prevention, device intelligence, and knowledge-based questioning to block account takeover.
- Agari Advanced threat protection, brand defense, incidence response, and fraud protection.
- Netacea Account Takeover Prevention Uses AI processes to identify normal behavior and then spot anomalous actions.
The consequences of an account takeover can be severe, including financial loss, reputational damage, and compromised customer trust. Given the growing frequency and sophistication of ATO attacks, it has become imperative for businesses to invest in advanced account takeover prevention tools. These tools detect suspicious activity, prevent unauthorized access, and secure user accounts by leveraging advanced security measures such as real-time fraud detection, behavior analysis, and machine learning algorithms.
By integrating these tools into their cybersecurity strategies, businesses can proactively defend against ATO attempts and minimize the risks associated with compromised accounts.
In this guide, we’ll explore the top account takeover prevention tools available on the market. We will review their key features, capabilities, and how they help businesses identify and mitigate ATO threats. With the growing number of cyber threats, now is the time for businesses to implement strong solutions to secure their accounts and protect against ATO attacks.
Security policies
You need to put in place a number of policies before you embark on your account security improvements.
Many account takeover prevention measures can be implemented through working practices and user education because errors by users in the way they use their accounts provide the main access routes for account hijackers.
Account takeover strategies involve how your system administration monitors account activity and how it responds to suspicious behavior as much as it concerns tightening up access procedures.
You need to consider the following approaches:
- User education
- Intrusion prevention systems
- Anti-phishing firewalls
- Email content filtering
- Access hardening
- Account takeover prevention
Account takeover prevention is a category of security software, which we will explain further.
Account Takeover Prevention in ITIL
Account Takeover prevention falls into the Security Management section of ITIL. This is registered as ISO/IEC 27001:2005. The primary goal of this process is to control access to information and that means making access credentials sufficiently tight so that an accidentally disclosed password does not result in data loss.
Access control should ensure confidentiality, integrity, and availability. An access control strategy should be written in conjunction with the service level agreements (SLAs) to which the company is committed within its contracts.
The security management process is divided into four activities:
- Control
- Plan
- Implement
- Evaluate
The Control action involves defining account protection requirements and setting policy. The Plan action requires the creation of security commitments in SLAs, the creation of contracts to support those commitments, and the definition of operational needs in order to implement those commitments. The Implementation activity requires the creation of asset classification and control documents, personnel security training, security policies, and access control.
The core of the Implementation action is the Access Control sub-activity. This requires fine-tuning the security measures available in existing access rights management systems, and buying in extra security software to reinforce those measures should they have been assessed to be insufficient.
The Evaluation action requires self-assessment from the IT department, an internal audit, and an external audit. Any weaknesses identified at each stage of the Evaluation process should be addressed before progressing to the next sub-activity in the Evaluation action.
Vulnerable accounts
Employee user accounts are easier to protect than accounts open to the general public. This is because you have a clear idea of who needs access to the system. However, with a system that encourages self-created accounts is open to the creation of fake accounts, which are set up purely for the intention of damaging the company’s reputation or exploring ways to exploit the system.
Automatically-generated account requests also need to be rooted out. These fake accounts are created by automated processes set up by hackers.
Another form of unproductive account both in the employee sphere and customer areas are abandoned accounts. These accounts that are no longer active need to be identified and removed from the system because they are gateways for intruders.
Account theft
The main point of weakness in any user account system comes from hijacked accounts. These are valid accounts that get appropriated by intruders. Employee accounts and paid-for accounts have fewer possibilities of credentials disclosure than free accounts. An account that costs the user nothing to set up has less value than credentials that guard important information and financial data that the account holder values.
Accounts that have value to the user can still be compromised through trickery. Phishing scams involve a hacker-controlled copy of a website. The user is tricked into entering the account credentials into the fake site, which gives the username and password to the hacker.
Another trick to win account credentials comes in the form of an impersonation scam. An overworked employee receives a call from a supposed colleague claiming to have been locked out of the system and needing to complete an important task. The victim is asked for his account login details as an urgent measure. This trick often works, but it requires research into the names and habits of at least two employees of the business.
The amount of damage that account hijacking can cause depends on the privileges allowed to the compromised account. Therefore, categorizing accounts by their importance is a strategy that can focus on account takeover prevention actions on the most important accounts on the system.
Account protection measures
There are procedural steps that you can take to prevent account takeover and there is specialist system software that you can buy to help you implement stronger account security.
Whether the account scope that needs to be protected serves in-house users or customers, your account protection strategy needs to be sufficiently intelligent so that it allows genuine users to continue to enjoy full access to their system accounts.
Identifying compromised accounts is the hardest task in ATO prevention. Many of these systems deploy innovative technologies, such as artificial intelligence in order to pick off the intruders without hindering legitimate users.
Remediation methods need to be swift and can be implemented automatically by the account takeover prevention software. You will be able to allow the security software to suspend accounts so that intruders no longer have access.
Post-intrusion actions
The success of your post-intrusion measures will either save or worsen the situation. Compromised accounts should be suspended rather than deleted. Particularly in the case of customer accounts, the user might want to continue having access and shouldn’t be penalized because of the actions of an intruder.
Your automated process might not be able to spot hijacked accounts. However, one hacker strategy is to alter the account recovery processes in the profile’s settings and then change the password, making it impossible for the legitimate user of the account to gain access.
Your system or sites should give clear instructions to users on how to recover their accounts in these situations. Usually, these procedures involve a call or an email to the system’s support desk, where the user can be queried further for identification. Those support technicians should be able to rollback account settings to allow the user to regain access quickly. However, the identification process should be sufficiently rigorous to prevent tricksters from getting access to accounts by posing as legitimate users.
Information about hijacking events needs to be stored for analysis to see what measures should be taken in order to prevent such account takeovers from happening again. However, these should not involve resetting passwords to give technicians access to the account. A hijacker might taint an account knowing that the takeover will be quickly reversed but carry out the action for the purposes of giving access to the account by a corrupt technician.
There are many subtle lines in account takeover prevention – between controlling account access without locking out legitimate users and between shutting down compromised accounts while allowing continued activity by the legitimate owner of the account.
The management of these sensitive decisions shouldn’t be left to technicians. Human intervention leaves too much to the judgment of the individual and results in inconsistent treatment of users. Automated monitoring of accounts and remediation handle the problems caused by account takeover fairly and efficiently. Deploying ATO prevention software is a better strategy than training technicians in the field.
The best account takeover prevention software
Account takeover prevention is a growing specialization in cybersecurity. There are many worthy ATO prevention systems available. They don’t all use the same tactics. As outlined above, your account takeover prevention plan needs to start with a strategy. Once you have a policy that fits the specific activity of your business and its accounts, you will be able to assess which ATP prevention system fits your needs.
Our methodology for selecting an account takeover prevention system
We reviewed the market for account takeover prevention tools and analyzed the options based on the following criteria:
- Options for system and email account protection
- Behavior analysis for activity pattern baselining
- Anomaly detection
- Fraud detection systems
- Data protection standards compliance
- A free trial or a demo service that allows a cost-free
- Value for money provided by a comprehensive threat detection system at a reasonable price
Using this set of criteria, we looked for a range of account activity tracking systems with packages that are suitable for system access, email accounts, and card fraud scanning.
In order to present a wide enough selection that will cater to all protection strategies, we have created a shortlist of ten systems.
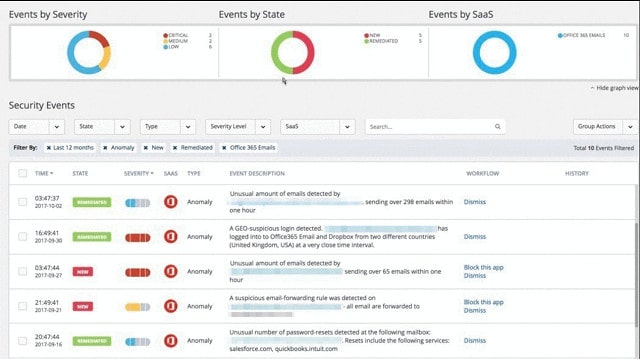
1. Avanan Account Takeover Prevention
Avanan offers a cloud-based account protection service that is available in three editions. The service is built with modules and each successively more expensive plan includes more modules. One of those modules is the Account Takeover Prevention service.
Key Features:
- Cloud-Based: A SaaS platform
- Email Protection: Options for collaboration tool protection
- Behavior Analysis: Spots anomalous behavior
- Automatic Account Locking: Blocks account takeovers immediately
- Technical Analysis: Attack examination
Why do we recommend it?
Avanan Account Takeover Prevention is part of the wider Avanan system security platform. This service is a retroactive service that looks at breaches that have already happened and learns from them. Lesson number one is to identify the user account used in the account and suspend it.
The ATO prevention system examiners the origins of incoming emails, the behavior of user email accounts, the location of the devices logging into the system, and unexpected measures that undermine account security.
Who is it recommended for?
The Avanan package is reasonably priced and subscription rates are calculated per user, so any type and size of business would find the service suitable. Plans are structured to cover the email systems of Microsoft 365 and Gmail or to also cover collaboration systems, including Teams and Slack.
Pros:
- An Overview Dashboard: Provides overviews of current statuses
- Drill-Down Details: Look at information on each individual event
- Preventative Security Measures: Can automatically deactivate or delete inactive accounts
- Spam Filtering: Also malware blocking
- Detects Shadow IT: Alerts to unauthorized application usage
Cons:
- No Price List: You must ask for a quote
The Avanan system will automatically lock suspicious accounts by resetting their passwords and notify administrators of the discovery.
EDITOR'S CHOICE
Avanan Account Takeover Prevention is our top pick for an account takeover prevention system because it identifies attempts to trick credentials our of authorized users and block data movement out of the network via email if account takeover is successful by other means. This cloud-based service is particularly strong at protecting Outlook/Exchange accounts in Microsft 365’s cloud platform and the Gmail service of Google Workspace. This system also includes a a secure Web gateway that assesses websites for threat before allowing them through to protected Web browsers.
OS: Cloud based
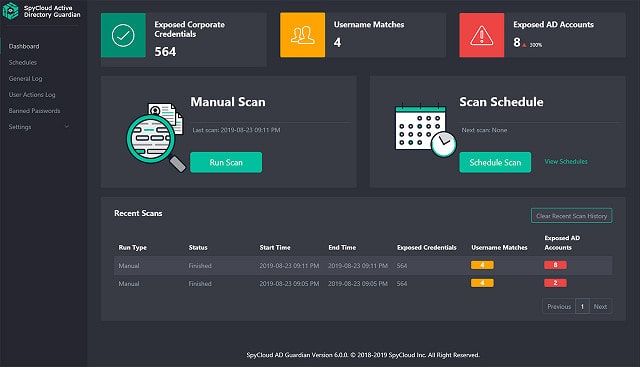
2. SpyCloud ATO Prevention
SpyCloud offers two types of ATO prevention: Employee ATO Prevention and Consumer ATO Prevention. Both systems are cloud-based. The employee account protection service includes more actions than the consumer version. This is because the employee protection system includes the monitoring of email activity and extra scrutiny of privileged accounts.
Key Features:
- Activity Monitoring: Systems for employee and customer accounts
- Cloud-Based: A SaaS platform
- Device Security Posture Management: Scans endpoints for security issues before allowing them to connect to the network
- API Implementation: Integrate the ATO tool into your own programs
Why do we recommend it?
SpyCloud ATO Prevention is a data collection system that identifies credentials leaks and other signs of account disclosure that improves your other threat detection services. SpyCloud isn’t a standalone system – you still need an XDR and if you have a SOAR element to that service, all the better.
Both systems can be integrated into your existing interfaces through APIs, so the credential protection service doesn’t require the login procedure to be ported to a cloud server.
Who is it recommended for?
SpyCloud improves the performance of your existing threat detection system by supplying threat intelligence from a Dark Web scanner and from event analysis. You would still need an XDR or a next-gen SIEM, so this is an extra expense and would be suitable for large companies that have big IT security budgets.
Pros:
- A SOAR Service: Can collect data and security signals from third-party tools
- Playbooks: Automate threat resolution by suspending accounts
- Allows Businesses to Provide Dark Web Scanning as a Service: Gathers large volumes of data
- Threat Intelligence: Access attack data from the experiences of other businesses
Cons:
- Not a Small Business Service: Better suited for MSPs and larger organizations
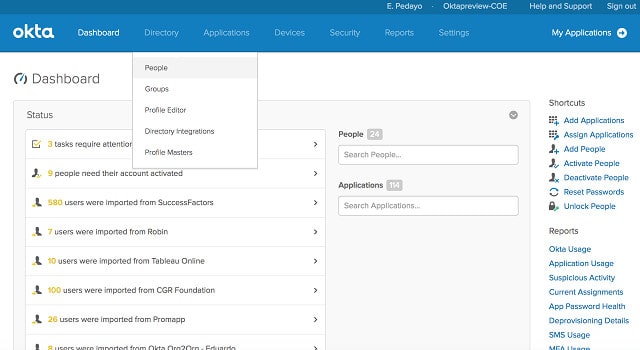
3. Okta
Okta’s ATO prevention systems are segmented into a Workforce Identity service and a Customer Identity service. Both are cloud-hosted services that can be called into software under development through APIs. The authentication services include multi-factor authentication, a single sign-on system, and a centralized access rights system to unify the various AD and LDAP controllers that run on your site.
Key Features:
- Cloud-Based: Operates externally and can protect any service that is accessed over the internet
- Employee and Customer Account Detection Modules: Workforce Identity Cloud and Customer Identity Cloud modules
- Single Sign-On: The core service of Okta
Why do we recommend it?
Okta provides identity protection system for customer accounts and for employees. The identity security management services of Okta include a single sign-on environment that is one of the leading SSO systems on the market. This platform can also implement multi-factor authentication. The system is based in the cloud and its protection system can span platforms.
Who is it recommended for?
The Okta system is affordable for any business because each module, such as the SSO system, is priced separately and charges are calculated per user. So, you only need to pay for the features that you need. The system manages application access but can also cover specific servers.
Pros:
- A Unifying Access Rights Manager: Coordinates the records of numerous ARMs
- Focuses on User Identification: Tracks behavior to detect attacks
- Supports a Wide Range of Integrations: Interfaces with LDAP and provides an API
Cons:
- No Price List: You need to ask for a quote
4. Sift Account Defense
Sift Account Defense scans new account creation actions to spot fraudsters and prevents them from setting up fake accounts. The service also implements measures to protect genuine accounts from takeover. The purpose of the Sift strategy is to block bad accounts without disturbing genuine users.
Key Features:
- Fraud Detection: Prevents payment card fraud
- Operates with Self-Service Accounts: Enables long-term account holder assessments
- Behavior Analysis: Predicts which users are likely to commit fraud
Why do we recommend it?
Sift Account Defense examines the user account creation process to identify hacker activity. It also analyzes each login attempt to identify account takeover. The system operates for employee accounts and for customer accounts. This platform is able to process large quantities of account activities and highlights anomalies and borderline cases for manual review.
The service uses AI techniques to compile a list of regular activities. It also pools the discoveries of threats on all of its clients’ sites to build up a constantly updated threat intelligence database, which informs activity scans and identifies suspicious accounts.
Who is it recommended for?
This is designed for businesses that manage a large number of accounts and the platform is particularly strong at tracking fraud in customer accounts. The platform also includes a payment fraud protection system to guard against tricks such as chargeback fraud. This is a cloud-based service.
Pros:
- Focuses on Preventing Fake Account Creation: Cuts out more work later during sales transactions
- Leverages AI and Data Science: Sophisticated detection techniques against fraud and ATO attack
- Includes a Blacklist: Continuously updates its library through a backend threat intelligence database
Cons:
- A Trial Version Would be Preferable: Only a demo available
5. ReliaQuest GreyMatter Digital Risk
ReliaQuest GreyMatter Digital Risk Protection performs a vulnerability analysis of your account management system, comparing it to their own model of the ideal, secure system. The service highlights these weaknesses in a report. It also constantly scans the Dark Web and other Web resources used by hackers to identify credentials exposure.
Key Features:
- Risk Analysis: Adapts to your security model
- Dark Web Scanning: Identifies stolen credential
- Security Analysts: Provide a tailored service
Why do we recommend it?
ReliaQuest GreyMatter Digital Risk Protection is a cloud platform that fronts a team of cybersecurity analysts. The service combines both automated and manual research methods to identify credentials theft. It also identifies security weaknesses in your existing system and recommends improvements. The service can feed intelligence into your SIEM or XDR.
The ReliaQuest system is a tailored service and so there isn’t a free trial. However, you can get a demo.
Who is it recommended for?
This service is intended as an enhancement for your existing security system. Therefore, it is intended for use in conjunction with an existing next-gen SIEM or XDR. This is a solution for large organizations that are likely targets for activists as well as for hackers. The threat scanner goes beyond the Dark Web to discover all threats to an organization.
Pros:
- GreyMatter Verify: An attack simulator
- Threat Intelligence: Keeps abreast of current ATO strategies
- SIEM and XDR Source Data: Provides an automated intelligence feed
Cons:
- Doesn’t Include Automated Responses: Informs other tools to implement remediation
6. Radware Bot Manager
Radware Bot Manager detects a range of automated attacks and that includes account takeover attempts. Radware has created a detection system, called the Intent-based Deep Behavior Analysis (IDBA). This is a model that is based on a combination of machine learning, user behavior analytics, device printing, and a blacklist database.
Key Features:
- Anomaly Detection: Looks for breaks in patterns account holder of behavior
- Attack Logging: Opportunities for manual analysis
- Bot Blocking: Passes search engine bots
Why do we recommend it?
Radware Bot Manager is able to tell the difference from a malicious automated probe of your system and the acceptable Web crawlers of search engines. This means that you don’t get alerted for every bot contact with your website or mobile app. All activity is summarized in the system dashboard and offers the option for manual threat analysis.
Who is it recommended for?
This system is more focused on combatting attacks on Web applications and mobile apps and is particularly strong at protecting customer accounts. The system operates as a global blacklist database that is constantly updated with each detected threat. Companies with a Website for user access particularly need this service.
Pros:
- Protects Mobile Apps and Websites: Also API protection
- Multiple Protection Strategies: Blocks DDoS attacks and payment fraud
- Threat Intelligence: Constantly updates a threat reference table
Cons:
- More for Customer Account Protection: Not so strong at employee account security
7. TransUnion TruValidate
TransUnion TruValidate is a fraud detection service for eCommerce systems. This tool is a customer account protection system rather than an employee account security service. The package provides checks on users when setting up accounts as well as during access events.
Key Features:
- Risk Prioritization: Examines the user’s device as well as identity indicators
- Protection for eCommerce Systems: Protects websites that collect payments
- Threat Intelligence Feed: Provides indicators to look out for
Why do we recommend it?
The TransUnion TruValidate system implements user account authentication in stages, which starts when the user creates an account. Observing each user’s activities on a website enables the detection system to identify possible account takeovers or bot activity. The ultimate goal of the system is to prevent payment fraud.
The service uses a range of signals and checks to identify whether the user accessing the account matches the user who created it. This looks at issues such as assessing devices through fingerprinting, and location detection through IP addresses. The service gives each user a risk score and will recommend that a purchase transaction be accepted or blocked.
Who is it recommended for?
This system is suitable for websites that sell to the general public. It offers validation methods, such as challenge questions and it is also possible to add–on biometric checks, such as a fingerprint scan on a mobile device. The service builds a profile of each user and lowers that accounts reliability score if anomalous behavior is detected.
Pros:
- Gradual Accumulation of Background Information: The behavior assessment begins when a customer sets up an account
- User Behavior Analytics: looks at all the activities of a user account
- Based Around a Reputation Score: A combination of factors can trigger an alert
Cons:
- No Free Trial: No demo
8. Experian
 Experian is a credit reference agency that has branched out into a range of account security services and fraud protection. The company’s Fraud Prevention Platform includes customer account takeover prevention. The Experian Digital Device Intelligence is able to identify fake accounts and block fraud attempts without disrupting the user experience of legitimate customers. The company’s Knowledge-Based Authentication system helps root out impersonators while allowing access to genuine users.
Experian is a credit reference agency that has branched out into a range of account security services and fraud protection. The company’s Fraud Prevention Platform includes customer account takeover prevention. The Experian Digital Device Intelligence is able to identify fake accounts and block fraud attempts without disrupting the user experience of legitimate customers. The company’s Knowledge-Based Authentication system helps root out impersonators while allowing access to genuine users.
Key Features:
- Fraud Detection: Provided by a credit scoring platform
- Customer Account Protection: Scans for anomalous activity
- Spots Impersonators: Allows the use of third-party assessors
Why do we recommend it?
The Experian Account Takeover Prevention system is an identity management service from a credit scoring platform. The Experian system builds up a profile of each user with background information such as location and device details. The platform provides a list of tools that customers can choose from.
Who is it recommended for?
The Experian package isn’t an out-of-the-box solution. The user can choose which of the measures available on the platform to implement. This means that there is a design element present in the decision to use the Experian platform and integrate it. So, the tool would be of particular interest to startups who are still building an eCommerce site.
Pros:
- Well-Known Brand: Trusted in the credit industry
- Has Vast Data Resources: Speed up the identification of fraud and ATO attacks
- Multi-Factor Checks: Uses device ID as well as behavior analytics to stop attacks
Cons:
- No Price List: Better suited for enterprise organizations
9. Agari
Agari Advance Threat Protection and Agari Incident Response combine to provide ATO prevention and mitigation. The Advanced Threat Protection service includes ATO prevention. It monitors the source of emails for known scammer locations and also examines the locations of those attempting to log in to an account.
Key Features:
- Account System Hardening: Focused on email systems
- Email Source Assessment: Looks for signs of impersonation
- Data Leak Detection: Blocks the movement of sensitive data
Why do we recommend it?
Agari Email Security scans inbound and outbound emails. It looks for changes in patterns of emails in the authorized accounts on a business email service. It also noted the source of each email because a hacker can send occasional emails from a spoofed address allowing the regular use of the account to continue.
The app monitors both incoming and outgoing mails, looking for interaction patterns that indicate that the credential might have been given away. Threat intelligence causes the Agari system to block mails from known suspicious actors.
Who is it recommended for?
This system focuses on employee email account takeover. The behavior of an account will trigger a warning that registers an account for deeper scrutiny. This is important for very large companies where technicians could not possibly pay attention to every user email account.
Pros:
- Robust ATO Detection: Uses AI and behavior monitoring
- Dark Web Scanning: Looks for disclosed credentials
- Identifies Compromised Accounts: Monitors incoming and outgoing emails
Cons:
- No Free Trial: No price list
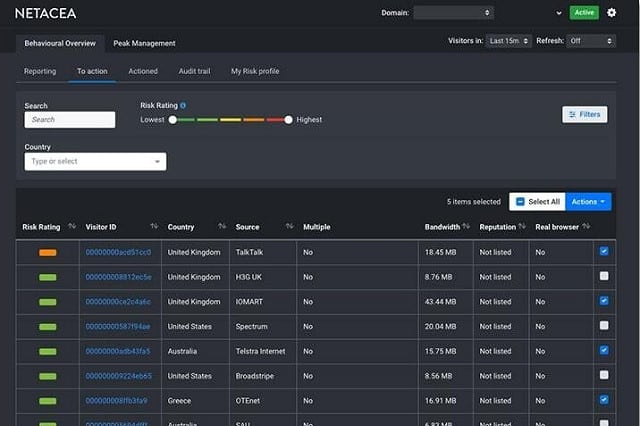
10. Netacea Account Takeover Prevention
Netacea Account Takeover Prevention uses machine learning to identify credential stuffing and brute-force password cracking attempts. The system doesn’t rely on just blocking log-in attempts from a particular source because hackers are known to direct their password-cracking attempts through multiple locations.
Key Features:
- Blocks Bots: Brute force attack protection
- Source Fingerprinting: Catches the same bot operating from different IP addresses
- Activity Logging: Helps with attack analysis
Why do we recommend it?
Netacea Account Takeover Prevention focuses its protection on customer accounts. The system combines a range of detection methods that include behavior analytics. This is a managed service that the buying business doesn’t need to monitor. Instead, the Netcea team will either impose identity challenges or notify you to shut down an account.
Who is it recommended for?
This package is suitable for use by eCommerce sites. It is a white glove system with technician support included, so it would be priced more for large organizations – the company doesn’t publish a price list. Small businesses need the security analysis features of this tool, but it might prove too expensive for them.
Pros:
- Leverages Machine Learning: Identifies manual and automated attacks
- Supports Auditing: User monitoring data collection
- Dynamically Stops Attacks: Uses artificial intelligence
Cons:
- No Price List: Must contact sales for pricing
Selecting an account protection strategy
Now that you have a better idea about account takeover threats, it is time to start making plans to block them. Your starting point needs to be with the formulation of a policy that fits the specific operations of your business. Once you are clear about the vulnerabilities of your system, you can start to investigate suitable software to help you prevent account takeover threats.
Account takeover prevention FAQs
What is account takeover protection?
Account takeover is another term for credentials theft. This phenomenon frequently hits members of the public in attempts to steal login credentials for online banking and other Web-based services, such as Netflix. Typical scam strategies include sending fake emails that seem to be from a genuine service that include links through to fake login screens – this is called phishing. Those credentials thieves use the same techniques to steal data from businesses. Account takeover defeats intrusion detection systems because the inttudr is able to use genuine user accounts to access data. The strongest way to guard against data theft through account takeover si to block phishing emails.
What is account takeover monitoring?
Account takeover monitoring is a difficult tasks because it involves examining the activities of legitimate users to see which accounts are behaving suspiciously. It is impossible for any security software producer to ship their account takeover monitoring system with out-of-the-box rules to identify compromised accounts. Therefore, account takeover monitoring packages uswe Machiner Learning (ML) to establish a profile of regular activity for each account and with that pattern of acceptable actions established, the account takeover monitoring task looks from changes in behavior to identify account takeover.
What are ATO attacks?
Account takeover attacks are simply credentials theft. Once an outsider has access to an account, all of the resources that are available to that account become accessible to the outsider. So account takeover is a method of implementing attacks rather than a specific attack.








Don’t forget to add Perception-Point.io!