Effective network configuration is the backbone of a secure and high-performing IT infrastructure. It involves setting up and managing the various devices and systems that make up your network, such as routers, switches, firewalls, and servers. Properly configuring these devices ensures that your network runs smoothly, securely, and efficiently, while also supporting the needs of your users and business operations.
Network configuration management (NCM) is a critical practice for IT teams, focusing on the ongoing setup, maintenance, and monitoring of network devices. It involves tracking device configurations, managing firmware and software updates, and ensuring that changes are properly documented to maintain network security and operational integrity. When network devices are misconfigured, security vulnerabilities can arise, leading to potential data breaches, downtime, or performance degradation.
One key aspect of network configuration management is staying on top of firmware and software updates for your network devices. Manufacturers frequently release patches and updates to address newly discovered security exploits, and failing to apply these updates can leave your network exposed to threats. Regularly updating device firmware is an essential part of maintaining a secure and stable network environment.
In this guide, we’ll explore the best network configuration tools and software available today. These tools help network administrators manage, monitor, and secure network configurations, automate device configurations, and simplify change management. Whether you’re managing a small business network or a large enterprise infrastructure, the right network configuration management software can significantly enhance the efficiency, security, and reliability of your network.
Regardless of the size of your network, it inevitably becomes difficult to track the firmware on each device, so installing a network configuration management tool is a must.
Here is our list of the best network configuration management (NCM) tools:
- Auvik EDITOR’S CHOICE This cloud-based network monitoring and management platform includes a network configuration manager as well as network discovery and documentation, network device status monitoring, and traffic analysis. Access a 14-day free trial.
- FirstWave Open-AudIT (FREE TRIAL) An automated asset discovery tool that creates a hardware, software, and firmware inventory and stores device configurations. Installs on Windows Server and Linux.
- ManageEngine Network Configuration Manager (FREE TRIAL) Written to network change, configuration, and compliance management (NCCCM) standards, this tool can run on Windows Server or Linux.
- Site24x7 Network Configuration Management (FREE TRIAL) This cloud-based service forms part of a package of system monitoring and management tools that is also available in an MSP edition. Start a 30-day free trial.
- ConfiBack Named as a contraction of “configuration backup,” this tool is free to use and runs on Windows, Linux, and Mac OS.
- WeConfig Free configuration manager for industrial networks.
- SolarWinds Network Configuration Manager Top-of-the-line configuration manager that runs on Windows Server.
- rConfig Free configuration management tool that runs on Linux.
- Net LineDancer NetLD runs on Windows Server and Linux. Its services include automatic device discovery and monitoring.
- TrueSight Network Automation Compliant with a list of data security standards, this tool installs on Windows Server and Linux.
- Device 42 Available for installation or as a Cloud-based service, this tool monitors your network constantly for device errors as well as protecting and updating configurations. Runs on Windows and Mac OS.
- Lan-Secure Configuration Center After autodiscovery and device config backups, this monitor will prevent all unauthorized changes to the setup of your equipment.
Network Configuration Manager Criteria
Network configuration managers enable you to keep track of the statuses and operations of your network devices. So a NCM tool needs to:
- Establish a configuration baseline
- Backup configuration snapshots
- Monitor for unauthorized configuration changes
- Enable settings rollbacks
- Distribute firmware updates
Those are the basic functions that you need from a network configuration management tool. Some nice extras are:
- Auditing for standard compliance
- Bulk configuration updates
- Firmware patch management
- Customizable user accounts for teams
The best network configuration management (NCM) tools
The list we created, making sure to cover all the essential requirements of a configuration manager, turned up some star finds. These go above and beyond your basic configuration needs to provide you with a wealth of features
Our methodology for selecting network configuration management tools
We reviewed the market for network configuration management software and analyzed the options based on the following criteria:
- A service that is able to discover all network devices and log them in an inventory
- A scanner that reads in all device settings and presents them in a dashboard screen for standardization
- A utility that takes an image of standard-setting and applies it to all relevant devices
- A configuration backup service that will restore approved settings on a device after tempering
- An action log that is available to system security auditors
- A free trial for a risk-free assessment period or a money-back guarantee
- Value for money that is represented by useful functions that will improve efficiency
Take a read through the descriptions of each of these suggestions.
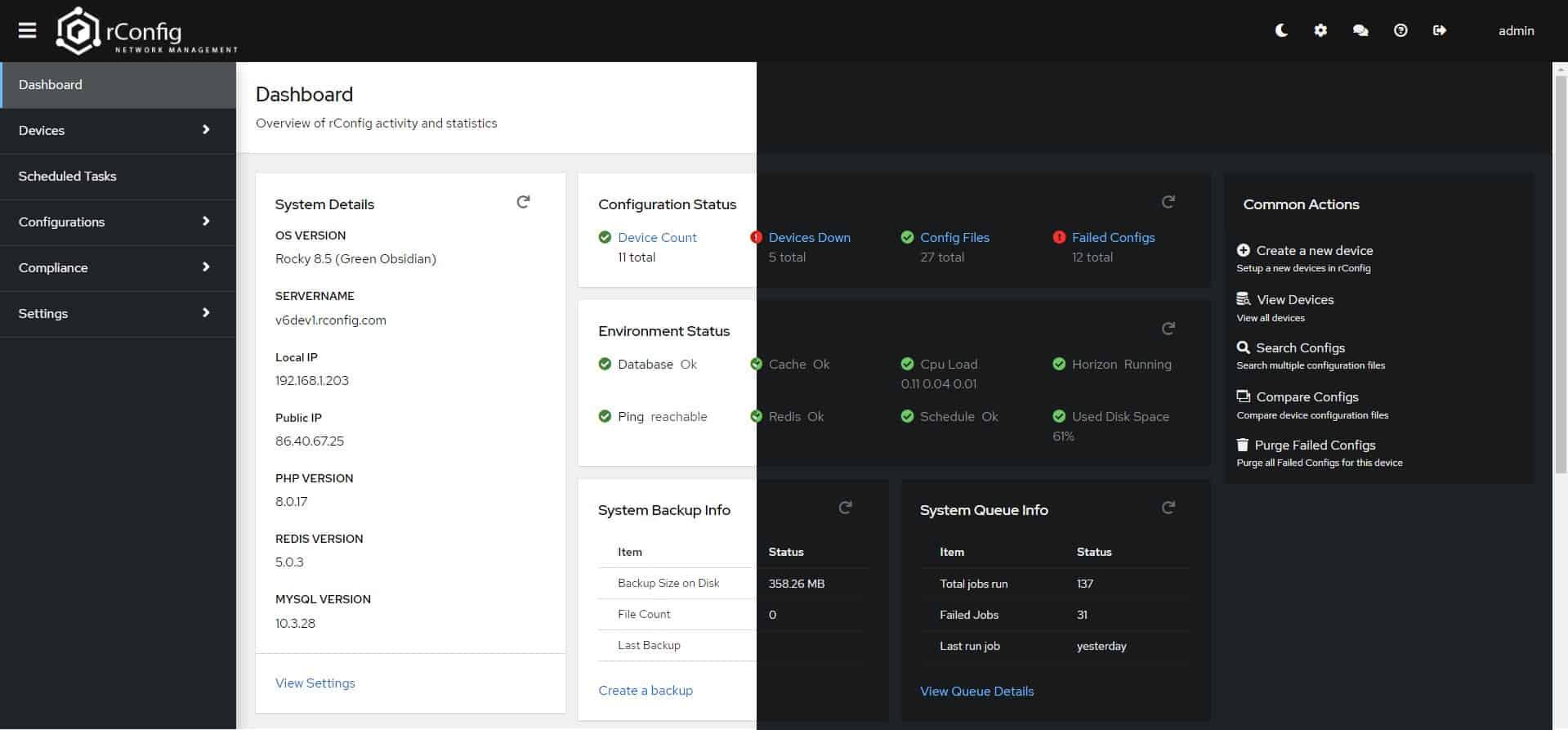
1. Auvik (FREE TRIAL)
Auvik is a SaaS package that is available in versions for IT departments and managed service providers. It provides monitoring services for networks but it has one system management unit, which is its network configuration manager.
The system extracts the settings of a network device and stores it in an archive. If a change is discovered, the tool creates a new backup, bumping all previous versions back, but still keeping all previous configurations in a version history. This means that it is possible to roll back to an older configuration.
Key Features:
- Network discovery: Provided as part of the network monitoring services
- A network device scan every 60 minutes: Compares the current settings to the most recently stored backup
- Takes a copy of a changed configuration: Stores the new settings without overwriting the previous version in the archive
- Provides a configuration viewer: Look through each version of the stirred device configuration in the Auvik console
- Allows a previous configuration to be restored: You don’t have to just rely on the latest backup
Why do we recommend it?
The network configuration tool in Auvik supplements the monitoring features in the platform. Auvik has many more network monitoring features than system management tools – the configuration manager is the only network management service on the platform. The network configuration manager also includes automated device monitoring, looking at whether settings have changed.
No businesses would subscribe to the Auvik platform for just the network configuration manager. This device security protection service is an integral part of the network monitoring package. The network discovery and documentation service on Auvik provides an important foundation for the network management system.
The platform’s cloud base places the monitor outside any LAN. The network’s LAN would block any instructions and scanning attempts sent from outside the network. To get around this security block, the Auvik service downloads an agent unit onto a server within the network. This enables the collection of data and its upload without any security issues arising.
The agent acts as an SNMP Manager, which is a component of the Simple Network Management Protocol. The other important unit in SNMP is the device agent – all network devices ship with this SNMP agent already installed on them. The Auvik unit broadcasts a request, which all device agents listen for and respond to. As the request is broadcast, the Auvik service doesn’t need to be provided with a list of devices on the network.
The responses that come back from the broadcast are uploaded to the Auvik server. These transmissions tell the Auvik monitor what devices are on the network. The details of the response are extensive and populate a network inventory. This inventory tells the network configuration manager the addresses of all of the network devices that it needs to scan.
The discovery scan also triggers the creation of a network map. That graphic is assembled from data held in the inventory, which includes a list of all the interfaces on each device and which other device is connected to the other end of the cable plugged into each interface. The discovery scan repeats and any changes that the system discovers are automatically reflected by updates to the inventory and map.
The SNMP scan also provides a device status report. This information is interpreted into live monitoring information in the Auvik console. This screen will also show any alerts that are sent by device agents in the event of a component failure.
The final monitoring service in the package is the traffic analysis system. This communicates with switches and routers using flow protocols. Each network device manufacturer takes an independent decision over which of these protocols to use, so a network manager might find that each device uses a different statistics gathering method. Auvik is loaded with the protocols for NetFlow, IPFIX, J-Flow, and sFlow. With this list of capabilities, the Auvik network traffic analyzer can operate on a multi-vendor network.
The network traffic analyzer provides breakdowns of traffic volumes by source, destination, and protocol. This information will enable you to adjust automated and batch processes to shift traffic volumes to less pressured periods.
The network configuration manager scans all devices every 60 minutes. It takes an image of each device’s set up and stores it in an archive. When the scanner runs again, 60 minutes later, it compares the current configuration to the most recently stored copy. If there is a difference, the tool copies the configuration again and stores it.
The new version of a device’s configuration going into the archive doesn’t overwrite the existing record. Instead, the backup service preserves each version. The network configuration manager console includes a data comparison tool. This enables you to compare different versions to each other or even pick a configuration version and compare it to the related device’s running config.
The network configuration manager won’t automatically restore a saved version if a device’s settings have been changed. This is a decision that needs to be taken by the network manager and implemented manually. This system allows the rollback to a version earlier than the most recently stored copy.
Who is it recommended for?
The Auvik system is suitable for any type or size of business that runs a network. Companies that run networks on several sites and want to centralize their management would particularly benefit from this package. The Auvik platform is available in a multi-tenant version that enables managed service providers to keep the data of their clients separate in sub-accounts.
Pros:
- A cloud-based platform: You don’t need to host the monitoring software on your own server
- An option for managed service providers: Offers a multi-tenant configuration
- Simultaneously managers multiple networks: Can centralize the monitoring of many sites in one console
- Network device status monitoring: Uses SNMP
- Network traffic analysis: Uses NetFlow, IPFIX, J-Flow, and sFlow
Cons:
- No price list: Request a quote
You can request a 14-day free trial to assess the Auvik platform.
EDITOR'S CHOICE
Auvik is our top pick for a network configuration management tool because it is integrated into a cloud-based network monitoring package. This platform installs a local agent and then populates its own console through a network scan. The dashboard maintains an inventory and a network map, which are kept constantly up to date. The system then provides network device status tracking with SNMP and traffic analysis with flow protocols. The network configuration manager unit of the package implements the protection of the network by examining devices every 60 minutes, looking for unexpected changes. Whenever a change to a device’s configuration is detected, the tool backs up the current config. Each change causes a new version to be created in the archive. Network managers can compare different versions of a configuration in the archive and also compare any of the versions with the running config of a device. It is then possible to make the decision on whether to restore an earlier configuration and wipe out recent changes.
Download: Access a Quote & FREE Trial
Official Site: https://www.auvik.com/features/#trial
OS: Cloud-based
2. FirstWave Open-AudIT (FREE TRIAL)
FirstWave Open-AudIT is an IT asset management and auditing tool that includes strong configuration management services.
Key Features:
- Automatic Device Discovery: Automatically discovers and maps devices on the network, providing a comprehensive view of the network infrastructure.
- Configuration Snapshots: Captures and stores configuration snapshots of devices for auditing and reference purposes.
- Asset Locator: Helps locate and track assets within the network, assisting in inventory management.
- Compliance Auditing: Provides features for compliance auditing, ensuring that network configurations adhere to specified standards.
Why do we recommend it?
FirstWave Open-AudIT is an IT asset inventory management system. It provides asset discovery and automatically generates hardware and software inventories. Details of each asset include configuration information, which can be used for vulnerability auditing. The system provides maps to locate each asset and also generates compliance documentation.
A key feature of the FirstWave system is the auto-discovery service. Open-AudIT scans a network and logs every connected device in an asset inventory. The inventory is stored in a database and includes details about each piece of equipment such as the make, model and operating system. When a device is discovered, the system runs audit scripts to document the operating system and identify all of the installed software. This creates a software inventory that supports license management.
The configuration management section of Open-AudIT visits each discovered device and takes a snapshot of its settings. These settings are stored in a database, called Baselines. Once a baseline has been established for each device type, it is possible to compare the settings for all devices of that type and highlight any discrepancies.
The discovery process can be scheduled to suit any requirement, further making it possible to compare the settings on the same device over time. This illustrates any unexpected changes that have been made. The Baselines system can also be used to reimpose standard settings if a device experiences a disaster or is replaced.
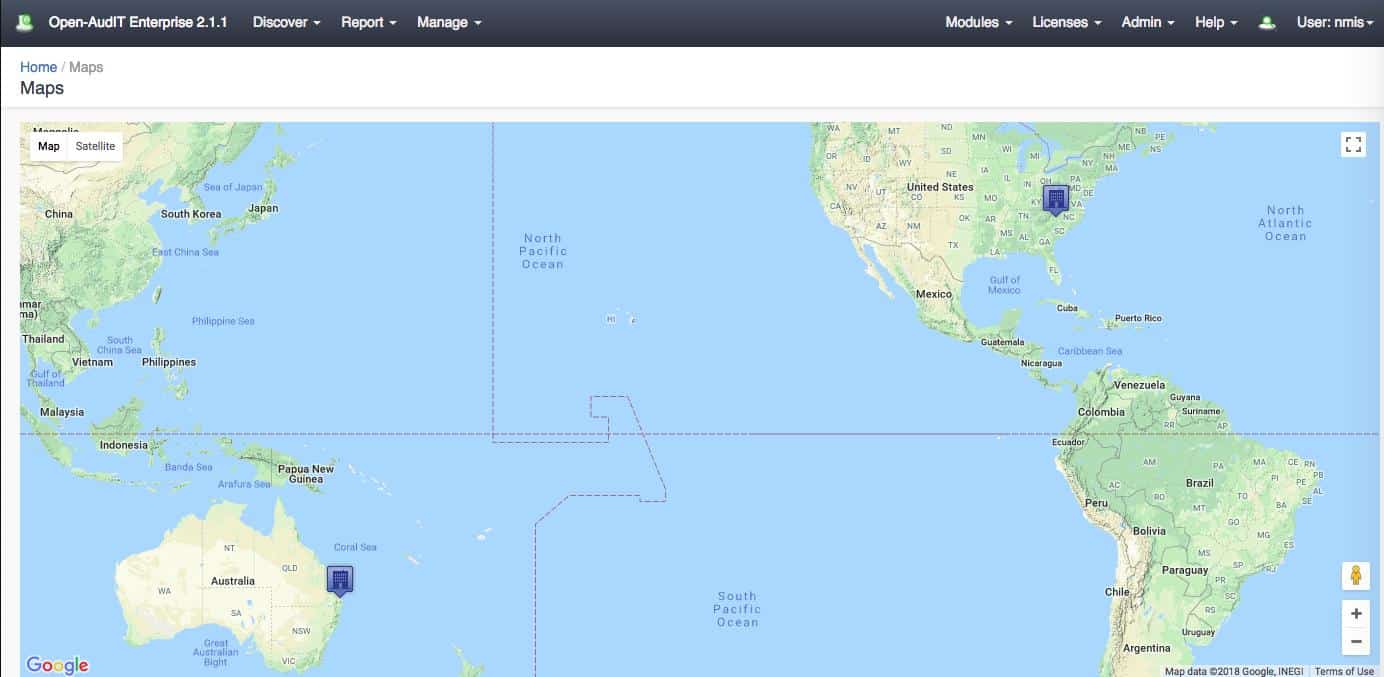
The asset inventory is made available in the system dashboard as a list of devices with click-through details available. Discovery processes can reach out to the Cloud, identifying company resources there, and they are also able to identify assets on remote sites. The tool can plot asset locations on a real-world map. This system is based on Google maps and is zoomable. Each location is indicated by a marker that can be queried to see how many devices are on the site.
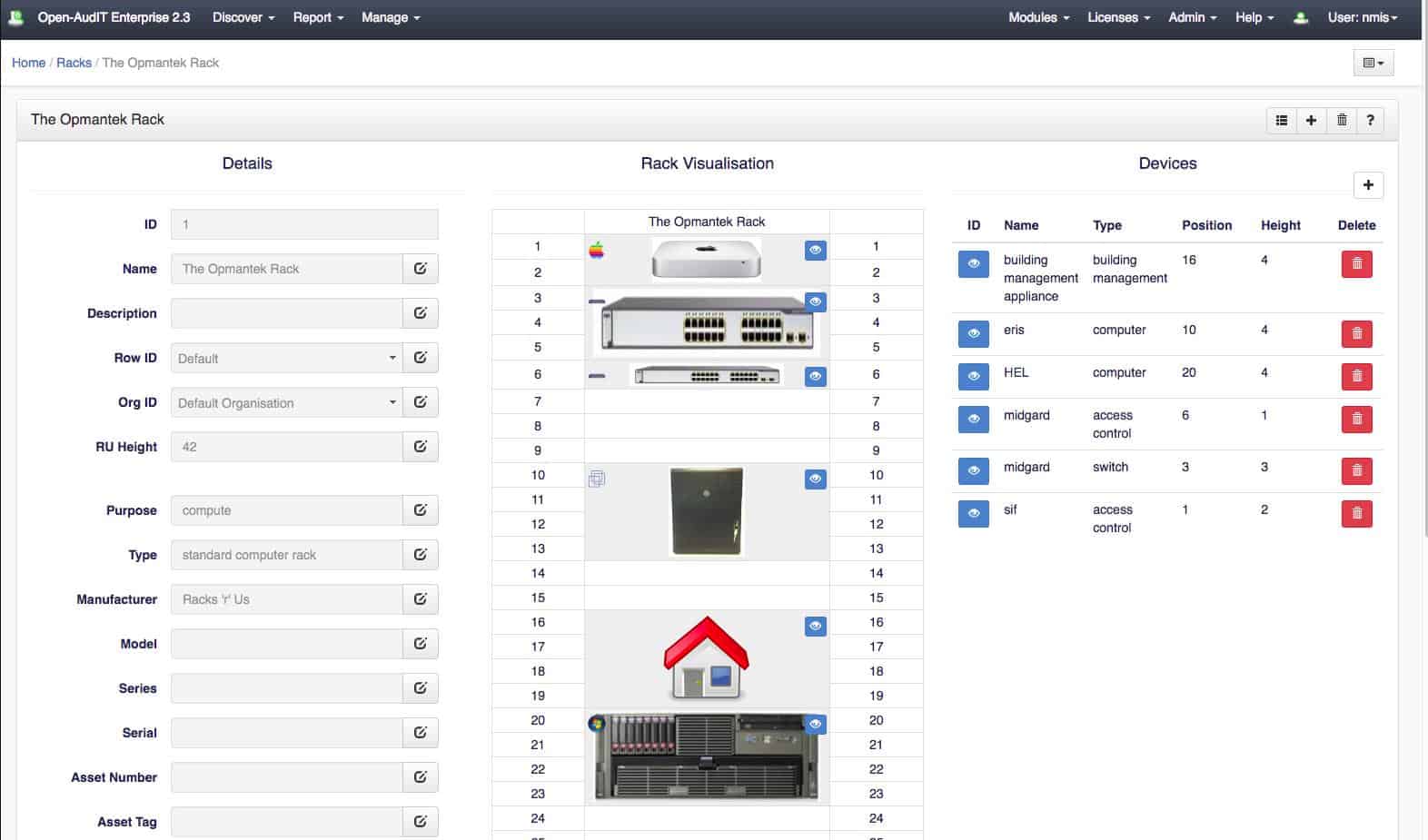
The service is able to identify assets that are housed together in a rack. Each element is documented individually and then the rack itself is also scanned for its services. The Open-AudIT service is able to produce a rack visualization that indicates the relative positions of assets held in each rack. It is also possible to group assets by room and by floor.
The Open-AudIT system is delivered as on-premises software and is available for Windows Server and Linux or it can be used online through a cloud service. It can also be installed over a hypervisor to create a virtual appliance.
The package is charged for on an annual license with a rate set in bands of devices to be monitored. There are three editions of Open-AudIT, which are Community, Professional, and Enterprise. The Community edition doesn’t have many features but it is free to use. The Professional edition is also free to use to monitor up to 20 devices – great for evaluation purposes.
Who is it recommended for?
The most important feature of this system is that it enables you to locate assets. If you run a very small network and don’t need to move from your desk to see all your equipment, you won’t need this system. Open-AudIT is a necessary assistant to large businesses with more assets than they can track.
Pros:
- Open-Source Option: Open-AudIT offers a free, open-source version, making it a cost-effective solution for organizations with limited budgets.
- Customizable Reports: Open-Audit allows you to generate reports tailored to your specific needs. This is crucial for informed decision-making.
- Software License Management: Open-Audit helps you track software licenses and identify potential compliance issues.
Cons:
- Technical Expertise Required: Might require some technical expertise, particularly for leveraging its advanced features. Smaller organizations without dedicated IT staff might find it challenging to implement and utilize effectively.
- Customization Needs: While Open-AudIT offers customization options, it might require some scripting or development knowledge to tailor reports and functionalities to your specific needs.
The full complement of utilities is only available in the Enterprise edition. This is the only bundle that includes the configuration management service. Cloud discovery and rack visualization are also reserved for the Enterprise edition. However, automatic device discovery is included in every package.
3. ManageEngine Network Configuration Manager (FREE TRIAL)
ManageEngine is a contender for SolarWinds’ crown as the leader in the network admin software industry. The company sells a series of separate modules that can also fit together and interact to create a unified infrastructure and IT service quality monitoring system. The company’s Network Configuration Manager is a very comprehensive solution to help you ensure the integrity of your network devices. The tool is compatible with multi-vendor environments. It is able to manage configurations for switches, routers, and firewalls plus any other network device type that you have on your system. The tool is designed in compliance with the network change, configuration, and compliance management (NCCCM) standards.
Key Features:
- Device Discovery and Inventory: Automatically discovers network devices and creates a comprehensive inventory with detailed information like device type, operating system, and IP address.
- Configuration Backup and Management: Automates configuration backups for all discovered devices, allowing you to restore configurations in case of accidental changes or outages.
- Configuration Change Automation: Enables automation of repetitive configuration tasks, saving time and reducing the risk of human error.
- Compliance Management: Helps ensure compliance with security regulations by allowing you to define and enforce configuration baselines.
Why do we recommend it?
ManageEngine Network Configuration Manager is a close competitor to SolarWinds Network Configuration Manager. This system performs all of the functions that the SolarWinds tool offers and additionally, it also updates the firmware of network devices. Like the SolarWinds system, this tool protects network devices against tampering.
Start off by backing up the configuration of all of your network devices into storage in the Network Configuration Manager. This process is automated for you. The ManageEngine tool includes a lot of automated processes that will relieve the burden of maintaining the configurations of your network devices. The next phase of operation is a constant sweep of devices to look out for any unauthorized configuration changes. You can set up actions to be performed automatically when configuration variance is detected.
You can get reports on the differences between the configurations of similar devices and decide on a set of configuration policies, applying different policies to different device types. Once you have standardized the configurations of your equipment, you can update your config backups, giving you a set of standard settings that you can automatically apply to new devices. The update service of the Network Configuration Manager can also be applied in bulk.
The backup store is also useful when you need to roll back from accidental changes or configuration changes that impair performance and need to be reversed.
The configuration management system includes a logging function, which records the users who make changes to the settings of network devices. Those accounts can be suspended automatically, and the information you get out of the logs will show you if a user account has been compromised.
The dashboard for the ManageEngine Network Configuration Manager is very attractive and includes a number of visualization devices to help you spot changes quickly. The console can be adapted for user roles, which makes this a good system for teams supporting a network.
The final benefit of the configuration manager is its ability to poll for patches and updates for the firmware of your network devices. When new software is available, the manager will roll it out and update all appropriate devices. So, you get an integrated patch manager with this tool.
Who is it recommended for?
This system is suitable for businesses of all sizes. Very small businesses with only two network devices to manage can use the Free edition. The base price for the lowest-paid edition covers 10 devices, which is also suitable for SMBs. Very large businesses with more upto 50,000 devices can use this tool.
Pros:
- Increased Efficiency: Automating configuration tasks and backups saves time and resources for network administrators.
- Improved Security: ManageEngine NCM helps prevent unauthorized changes and enforce compliance with security standards.
- Cost-Effective: Compared to some competitors, ManageEngine NCM offers a good value proposition with its feature set and pricing options.
- Available on Multiple OS: Supports multiple operating systems, including Windows, Mac, and Linux, offering flexibility in deployment.
Cons:
- Potential Learning Curve: While user-friendly, some advanced features might require some learning time for administrators unfamiliar with network configuration management tools.
This system is better suited to middle-sized and large networks. The software installs on Windows and Linux. There is a free version of the Network Configuration Manager, which is limited to two devices. There probably aren’t many networks out there that only have two devices on them, but this offer would be suitable for a test environment. If you decide to buy, you can try out the system first for free on a 30-day trial.
Related: Best Linux Patch Manager
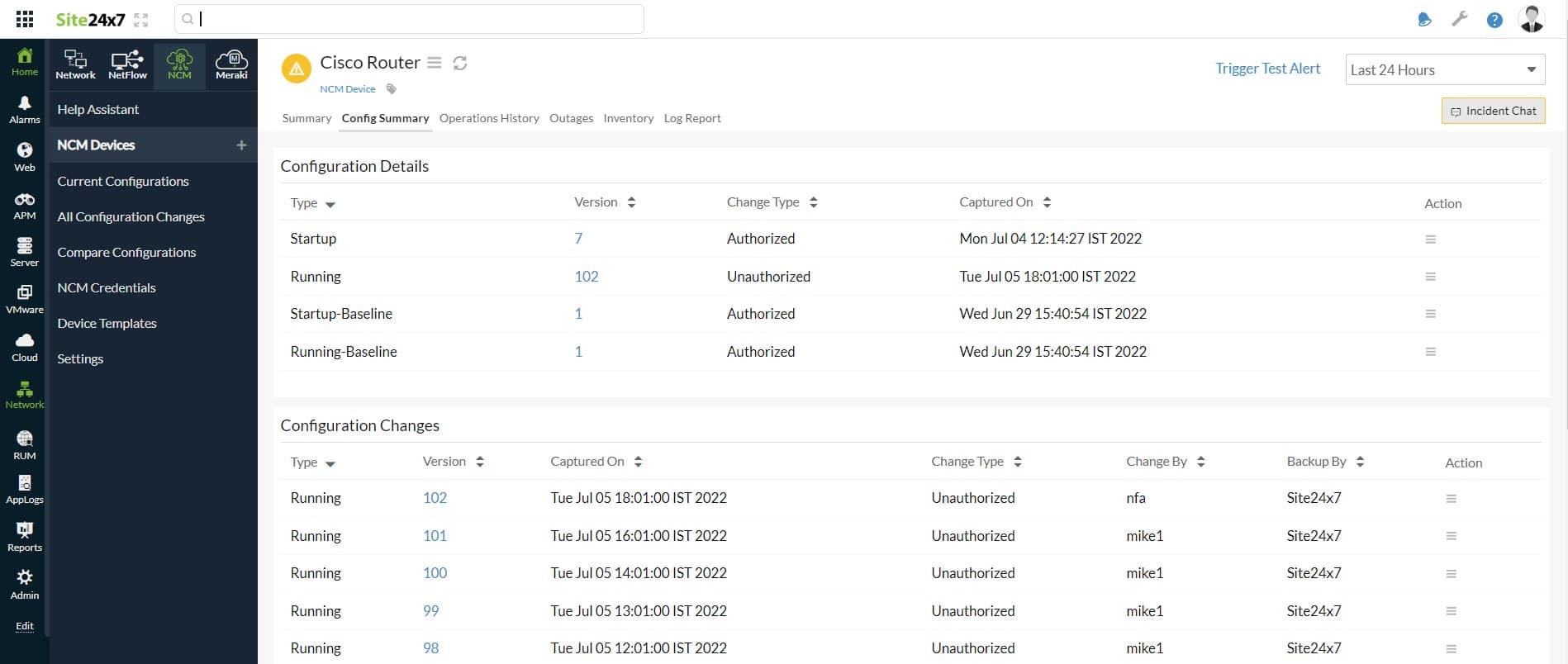
4. Site24x7 Network Configuration Management (FREE TRIAL)
Site2x7 Network Configuration Management is one unit in a package of system monitoring and management services that is delivered from the cloud. The bundle also provides a network discovery routine that populates an inventory of all the devices on the network. The list of hardware provides a starting point for the management of device firmware and settings. The system can operate in a multi-vendor environment, covering equipment supplied by Cisco, Aruba, Fortinet, SonicWall, and others. It will manage switches, routers, wireless access points, and hardware firewalls.
Key Features:
- Automated Configuration Backups and Version Control: Automates regular backups of network device configurations. This allows you to restore previous configurations if needed.
- Configuration Change Automation: Enables automation of repetitive configuration tasks, saving time and minimizing errors.
- Network Inventory: Offers a comprehensive network inventory, providing visibility into the devices and configurations within the network.
- Secure Configuration Storage: Ensures secure storage of configurations, safeguarding critical data from unauthorized access or tampering.
- Configuration Lockdown: Implements configuration lockdown, adding an extra layer of security to prevent unauthorized changes.
Why do we recommend it?
The Site24x7 Network Configuration Management service provides protection for your system by blocking unauthorized changes to network devices and also preserving all of your hard work in setting up all systems by storing configurations for instant recovery if hardware gets damaged by an environmental disaster. The package includes firmware vulnerability scanning.
The main mechanism of this package is the copying of a device’s configuration as an image. The image then gets stored. The tool will scan a device’s firmware, spotting when it is out of date and needs to be upgraded. The service also gives you the opportunity to quickly onboard a replacement device or replicate settings to multiple switches.
Once the service has stored a copy of each device’s configuration, it will repeatedly compare that image to current settings. If the device has been changed unexpectedly, the Site24x7 platform will automatically restore the authorized configuration.
Who is it recommended for?
The Site24x7 cloud platform provides many system monitoring and management tools and they are offered as packages rather than individually. Each package includes configuration management for one device. Each subscriber then adds more devices to the account – there is a charge for each – which makes the plans scaleable and suitable for all sizes of businesses.
Pros:
- Seamless Integration: Integration with other Site24x7 tools promotes better network visibility and simplifies overall management.
- Cost-Effective: Site24x7 offers various pricing plans, making NCM accessible to organizations of different sizes and budgets.
- Reduced Errors: Automating tasks minimizes the risk of human error during configuration changes.
Cons:
- Missing Pricing Information for Extra Devices: The pricing information for additional devices is not listed, which may pose a challenge for organizations evaluating the cost implications of scaling the solution.
- Potential Learning Curve: While user-friendly, some advanced features might require some initial learning for administrators without prior experience in NCM tools.
All plans on the Site24x7 platform include network configuration management for one device, except for the MSP edition, which includes five. Add on extra capacity to cover your whole network. You can examine the Site24x7 system with a 30-day free trial.
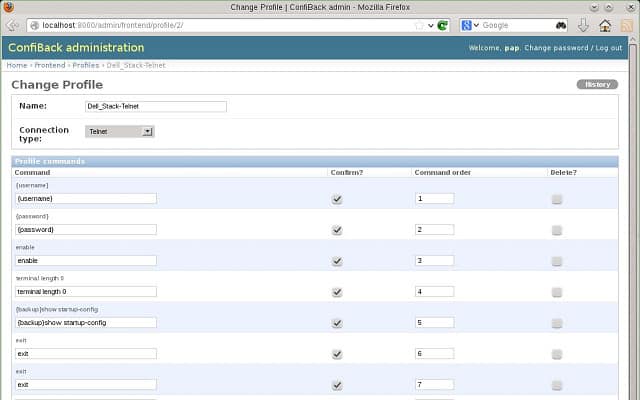
5. OnWorks ConfiBack
OnWorks ConfiBack is also known as Configuration Backup. This software is free of charge and you can install it on Windows, Linux, and Mac OS. This is a configuration manager that would fit a small business to protect its network devices. This tool is not nearly as sophisticated as the previous three options on this list. However, if you have no money for a configuration manager, getting ConfiBack is a much better option than going without.
Key Features:
- Multi-Vendor Device Support: ConfiBack boasts compatibility with a wide range of network devices from various vendors, including routers, switches, firewalls, and load balancers.
- Configuration Diff and Rollback: ConfiBack allows you to compare different versions of a configuration and identify changes made over time.
- Compliance Management: ConfiBack assists in maintaining compliance with security standards by enabling you to define configuration baselines.
- Security Features: ConfiBack offers security features like role-based access control (RBAC) to restrict unauthorized access and ensure only authorized personnel can manage configurations.
Why do we recommend it?
OnWorks ConfiBack provides a free backup storage service on cloud servers. The system requires the download of an agent onto one of the endpoints on your network to back up the configurations of all of your devices. You can use the stored image to check for changes manually and then restore if necessary.
You need to prompt the system to back up configurations for devices. However, you can schedule the backup process to take place regularly. Change detection is an interface-supported manual process. You need to back up the current version of a device and then compare it to the original backup with a diff command. This process synchronizes the lines in two files and outputs those lines that are different. The results of this utility are saved to a text file.
The ConfiBack software is an open-source project, so you can comb through the programming code if you want. This openness is a common method of ensuring users that there are no hidden security weaknesses in programs and that they do not contain hacker code.
Who is it recommended for?
If you don’t think you have the budget for a network configuration manager, sign up for this service – it’s free. OnWorks offers lots of free stuff, including cloud servers and Web hosting, so if you are a penniless startup or a hobbyist looking for a launchpad, take a look at their site.
Pros:
- Very Lightweight Tool: ConfiBack is a lightweight tool that can run on practically any machine, making it versatile and accessible.
- Easy Installation and Setup: Offers easy installation and setup, providing access through a simple web interface, enhancing user convenience.
- Free to Use: ConfiBack is available at no cost, making it a freely accessible configuration backup solution.
Cons:
- Not Ideal for Large Environments: Due to its focus on small networks, ConfiBack may not be suitable for larger environments with more complex configuration management needs.
- Lacks Support for Team Logins with Access Control: The tool lacks support for team logins with access control, potentially limiting collaborative usage in larger team settings.
The free ConfiBack software doesn’t include any user authentication procedures and it doesn’t have a patch manager module.
See also: Best Network Configuration Backup Software
6. WeConfig
WeConfig is billed as a configuration manager for industrial networks. The tool is a product of Westermo, which makes durable network equipment for shop-floor environments. The configuration manager is really only meant for Westermo devices. However, it also works with the network equipment of other manufacturers because it relies on the universal SNMP system.
Key Features:
- Designed for Shop Floor Equipment: Tailored for managing network configurations specific to shop floor equipment, catering to the needs of industrial environments.
- Network Scanning and Logging: Provides network scanning capabilities and logging functionalities to enhance visibility and monitoring of shop floor networks.
- Backup and Restore Configurations: Offers the capability to back up and restore configurations, ensuring data integrity and facilitating recovery.
Why do we recommend it?
Westermo WeConfig is another free configuration manager. However, the Westermo system is designed for use with industrial equipment. This tool provides network device firmware management and network settings controls. The system also provides an on-demand network scan that compiles a network inventory and topology map.
Anyone can download the WeConfig software for free from the Westermo website. The tool installs on Windows environments. After installing the software, you need to tell it to scan the network. This will compile a network map and log all network devices in the WeConfig database. You can reorganize the network map manually if the display of icons is a little cluttered. Once you are happy with the layout, you can lock it to prevent anyone from accidentally moving or deleting elements. Each icon is a link to details about the device that it represents and an Analysis view shows graphs on the operation of the network equipment on your network. The device database won’t update automatically; you have to issue a scan command again whenever you want the inventory updated.
The configuration manager allows you to command the storage of the configuration of a device to a file and load a configuration file onto a device. You can delete or edit configurations on a device.
The WeConfig system requires a lot of manual intervention. However, this service management enables you to store copies of configurations. In order to check for alterations to device configurations, you would have to task a copy of the current configuration and do a file comparison with the store of the original settings. In order to introduce your own automated procedures, you could set up the collection and comparison of configuration file versions in a batch job.
The features of WeConfig include some useful basic network monitoring functions. However, data gathering is only performed on-demand, so you won’t get alerts on unexpected conditions. The interface doesn’t include any user authentication and you can’t adapt the dashboard, so this is not a tool that you would distribute to a team of administrators. This tool is suitable for small networks.
Who is it recommended for?
We Config is meant for use with factory networks to check on the configurations of shop-floor equipment and network devices. The need for manual intervention to command network sweeps, compare configurations and transfer image files means that it is more suitable for small networks. Administrators of larger networks could use workload automation software for these tasks.
Pros:
- Sleek and Simple Interface: Features a sleek and simple interface that is easy to navigate, providing an intuitive user experience.
- Focus on Config Automation and Provisioning: Places a strong emphasis on configuration automation and provisioning, streamlining network management tasks.
- Simple and Intuitive Visualizations: Utilizes simple yet intuitive visualizations to map device relationships and dependencies, aiding in network understanding.
Cons:
- Designed for Industrial Environments: As a solution designed for industrial environments, some features may not be directly applicable or optimized for smaller networks outside of industrial settings.
- Steeper Learning Curve: The platform may have a steeper learning curve when it comes to automating tasks, potentially requiring more effort for users to fully utilize automation features.
7. SolarWinds Network Configuration Manager
The Network Configuration Manager ensures that your network devices don’t get tampered with and that you can roll back from mistakes made when adjusting their settings. Added to those functions are a switch port mapper, an end-user tracker, a WAN performance monitor, and an IP address manager.
Key Features:
- Automatic Device Discovery: Automatically discovers new devices on the network and provides templated health reports, offering immediate insights upon installation.
- Configuration Management: Offers configuration management capabilities, allowing teams to efficiently backup and restore changes that may impact network performance.
Why do we recommend it?
SolarWinds Network Configuration Manager is a vulnerability scanner and a device settings protector. The tool guides on how to tighten security in the configurations of each device type. You set up one device perfectly and then take an image of that setup. That image gets stored and can then be applied to all devices of that type.
The installation process includes a system scan that discovers all of your devices and stores snapshots of their current configurations. From then on, when you want to alter the configurations of your devices, or just want to update one, you make those changes through the manager tool. The configuration manager is able to interact with a long list of device brands, so you don’t have to worry about restricting your equipment purchases to one vendor in order to keep your configuration management simple. That said, the tool does have a few more features that work with Cisco equipment than it can provide for the products of other manufacturers.
The Cisco enhancements include the integration of checks with the Cisco National Vulnerability Database into audit sweeps. This gives you very powerful alerts to shortfalls in security that can be obliterated quickly with a patch, an update, or an adjustment in the settings of a network device. If you have a Cisco Adaptive Security Appliance, the SolarWinds Network Configuration Manager gives you insights into the device’s settings and helps you manage and audit access control lists. The configuration manager will check for updates and patches to your ASA’s firmware and install them automatically. You get a similar service if you have a Cisco Nexus. The Network Configuration Manager is also a network software updater that will help you update and audit its access control lists and give you virtual defense context support for parent/child relationships.
The automation of network configuration tasks means that you don’t need to take equipment offline or work overnight when you need to alter the settings of your network devices.
The auditing module of the Network Configuration Manager lets you demonstrate compliance with security standards. You will be able to spot unauthorized configuration changes and roll them back instantly with this tool. You can even automate the correction of those changes as well as a lot of other routine device management tasks.
The Network Configuration Manager maintains a database of configurations for each device. This well-organized, indexed, and searchable archive makes it really easy for you to manually locate a config file should you need to replace a piece of equipment and get all of the settings of the old device uploaded onto the new one. The tool can even monitor the lifecycle of a device and notify you when it is nearing the end of its service life.
Strictly speaking, patch management is usually the responsibility of a separate tool. This is the case with the SolarWinds division of responsibilities. However, there is a fully-compatible Patch Manager module available from SolarWinds that will keep the firmware of your network devices up-to-date.
Who is it recommended for?
This is a particularly useful tool for large networks that have many switches and routers. You can standardize the settings of each drive and also use stored images to onboard new devices. The tool constantly scans all devices; if it spots unauthorized changes, it restores the saved configuration.
Pros:
- Built for Medium to Large Networks: Tailored for medium to enterprise-size networks, offering features that streamline troubleshooting and provide quick restoration of configuration settings.
- Automates Onboarding: Automates the onboarding process for new devices, simplifying the integration of new elements into the network.
Cons:
- Not Ideal for Home Networks: SolarWinds Network Configuration Manager is specifically tailored for use in enterprise environments.
SolarWinds offers you a 30-day free trial of the Network Configuration Manager and the Patch Manager, which installs on the Windows Server environment. The same free 30-day trial offer is available for the Network Automation Manager deal.
8. rConfig
Another free configuration manager that you could try is called rConfig. This open-source tool is available from the GitHub website. GitHub makes the code of the tool available so you can check through it for security weaknesses or even adapt it to write your own version. The software runs on CentOS and RHEL Linux.
Key Features:
- Continuous Monitoring and Autodiscovery: Offers continuous monitoring, ensuring that network changes are tracked, and autodiscovery of new devices and hosts is supported.
- Push and Backup Configurations: Allows the pushing of new configurations to devices and hosts while also offering the capability to take backups of each device’s settings.
- Autodetection: Features autodetection, allowing the tool to identify and recognize devices and hosts automatically.
Why do we recommend it?
The rConfig package is another free configuration manager. This tool provides more task automation than ConfiBack and you can integrate it into workload automation and network monitoring tools. The tool can also be run at the command line for easier use in batch files. Unfortunately, the latest version is not free to use.
The tool is able to detect all of your network devices and you can command it to copy off the configurations of each into files. The recording of configurations can be scheduled, giving you a regular view of statuses. All actions can be performed on all devices, on categories of devices, or on individual devices.
The checks on changes in configurations require some manual intervention and are based on a file comparison model. You can distribute configurations from the file store out to devices. Again, this can be broadcast to all devices, an update of just one category of device, or to an individual device. You can set policies in the rConfig system and use the Configuration Compliance Manager to check that all the configurations on your network comply with those specifications.
A shortfall of rConfig in comparison with other tools on this list is that it doesn’t include any user authentication, so it should only be installed on one secured computer. This means that the tool is only suitable for small networks and not those that are managed by a team.
Who is it recommended for?
The recent update to the rConfig system makes this a superior tool. However, it isn’t free and in fact, it’s quite pricey. This version is suitable for large networks, while smaller businesses could opt for the free older version, which has a less sophisticated interface and not so much automation.
Pros:
- Completely Free and Open Source: Being free and open source makes rConfig an accessible option for Linux systems without incurring licensing costs.
Cons:
- Lacks Paid Support: As a free and open-source tool, rConfig may lack dedicated paid support, which could result in potential delays in resolving bugs or issues.
9. Net LineDancer
Net LineDancer, which is also known as NetLD, is not free to use, but you can try it on a 30-day free trial. Net LineDancer has all of the features that you need from a configuration manager. It automatically logs all devices and takes a snapshot of their configurations to establish a stored baseline. Subsequent configuration sweeps can identify changes to each device. Those comparisons can also be made on-demand.
Key Features:
- Autodiscovery: Automatically discovers devices within the network, providing visibility into the network infrastructure.
- Keeps Snapshot of Each Configuration: Maintains a repository of configuration images for each device, offering a snapshot of the configuration state.
- Integrations Support: Provides support for various integrations, facilitating centralized configuration management across multiple devices.
- Supports Cisco PnP Devices: Specifically supports Cisco Plug and Play (PnP) devices, enhancing compatibility with Cisco networking equipment.
Why do we recommend it?
Net LineDancer is designed for use by large networks. The system provides device discovery and inventory creation. It can be used to update multiple devices with the same OS versions simultaneously and then lock configurations and protect the devices from tampering. The service offers a distributed device management option.
The stored configuration files can be re-loaded onto equipment in bulk, by device type, or individually. The software can manage thousands of devices and the monitoring processes can be automated through the tool.
Reporting features of the tool log the users that make changes to the settings of devices. An addition to the software can help you monitor VLANs and VMs. Net LineDancer installs on Windows Server versions and also on CentOS and RHEL Linux. A second product from LogicVein is called Net StreetDancer. This is a cut-down version of Net LineDancer, which covers 80 percent of the capabilities of Net LineDancer. Net StreetDancer, which is also called NSD and netSD, is free to use.
Net LineDancer and Net StreetDancer cover all of the essential functionality that you need from a configuration manager. However, it doesn’t include the higher features that you would need for a team-maintained complex system – it doesn’t have access controls. These two systems also don’t include any patch management functions. Net LineDancer and Net StreetDancer would be ideal for small networks.
Who is it recommended for?
As well as large networks, this tool is designed for use by managed service providers. The software is multi-tenanted and you can create a local collector – or “Smart Bridge” in each client network. The tool provides automated change detection for security management and automated restoration of authorized settings.
Pros:
- Available for Both Windows and Unix OS: Supports both Windows and Linux/Unix operating systems, offering flexibility in deployment across different platforms.
- Free Version Available: Offers a free version, providing basic configuration management capabilities at no cost.
Cons:
- Interface May Feel Crowded: The interface can feel crowded, especially in larger environments, potentially affecting user experience in terms of navigation and usability.
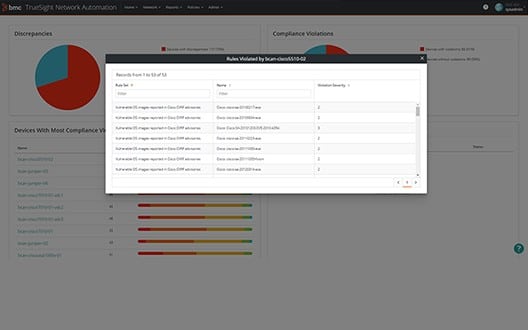
10. TrueSight Network Automation
BMC Software recently changed the name of its network monitoring tool from BladeLogic Network Automation to TrueSight Network Automation. This newly-revamped package is worth a look if you are in the market for a configuration manager.
Key Features:
- Autodiscovery: Automatically discovers devices within the network, providing visibility into the network infrastructure.
- Automatic Configuration Correction: Offers the capability to automatically correct configurations, ensuring that devices remain in compliance with defined standards.
- Automated Standards for Compliance: Allows the establishment of automated standards to maintain compliance with industry standards such as HIPAA, PCI DSS, NIST, and SOX.
- Automatic Recovery to Last Known State: Can automatically recover devices to their last known “good” state, minimizing the impact of configuration issues.
Why do we recommend it?
BMC TrueSight Network Automation is a vulnerability manager for network devices. The package checks on configurations, highlights security weaknesses, and supports improvements. It stores configuration images and then checks all devices for unauthorized changes, restoring the stored original where necessary. The package also includes a patch manager for firmware.
BMC has done a very nice job with its new configuration system because it has paid attention to the standard requirements with which many data-driven businesses have to comply in order to win contracts and keep to service level agreements (SLAs). Configuration standards are dictated by “policies.” The system ships with pre-written policies that guarantee regulatory compliance with a range of system integrity requirements: NIST, HIPAA, PCI, CIS, DISA, SOX, and SCAP. There doesn’t seem to be a pre-written policy for GDPR yet.
If you are contractually or legally bound to enforce one of these standards, you will be greatly aided in your duties by TrueSight Network Automation. Not only does the system list the settings that network devices need in order to comply with a given standard, it enforces those requirements. This method will save you a lot of time reading through standards documents and trying to work out how to translate the requirements into device settings.
The system starts off by scanning the system, logging all devices, checking for compliance requirements, and adjusting device settings. After that, the monitor will back up all configurations. TrueSight will continue to scan and prevent any changes or alert you when they happen. You can restore standard configurations manually, but the automated option of TrueSight will perform that task for you.
The console of TrueSight Network Automation can be allocated in sections to different user groups. This will allow you to make different dashboards available for different team members.
Changes to configurations and updates to firmware can be rolled out in bulk. The system will detect new patches and updates and alert you to them; these will then be installed automatically on all relevant devices with your approval.
TrueSight Network Automation has a companion module, called TrueSight Vulnerability Management. This optional extra will scan for security threats and block them. It also keeps in touch with vendor sources and the NIST National Vulnerability Database to detect security weaknesses and alert you to the need to patch the system when a relevant solution is made available. This vulnerability monitoring applies to servers as well as to network devices.
The tool can be installed on Windows Server and RHEL and Ubuntu Linux. You have to pay for this network configuration software. Although BMC offers free trials for some of its products, there aren’t free trial periods available for True Sight Network Automation or TrueSight Vulnerability Management.
Who is it recommended for?
BMC provides a suite of cloud-based automation tools and so if you are already a user of BMC Control-M or Helix services, you will be attracted by the TrueSight Network Automation option. The package also provides system documentation and security auditing proof, which is needed for compliance reporting.
Pros:
- Pre-configured Workflows: Comes with numerous pre-configured workflows, allowing users to start managing configurations immediately without extensive setup.
- Standards Compliance Policies: Enables the implementation of standards compliance policies, ensuring that network configurations adhere to industry and regulatory standards.
Cons:
- Bare-Bones Interface: The interface is described as fairly bare-bones, potentially making it tougher to navigate compared to competing products.
11. Device42
Device42 is an impressive combination of infrastructure management modules. The tool includes IT asset management, IP network address management, data center infrastructure management, and configuration management. If you operate a data center whether for in-house services or as an external provider, you should pay attention to this configuration management option. The accompanying functions of this tool make it extremely interesting for data centers.
Key Features:
- Configuration Backup: Facilitates the backup of configurations, ensuring data preservation and recovery options.
- Settings Protection: Implements settings protection to safeguard critical configurations against unauthorized changes.
- Automatic Topology Maps: Can produce automatic topology maps and dependency mapping, enhancing visibility into the network infrastructure.
- Designed for Config Management and Application Mapping: Designed to serve both configuration management and application mapping needs, providing a comprehensive solution.
Why do we recommend it?
Device42 is an ITIL-based IT asset management package. It provides documentation for all assets, which includes endpoints, network devices, software packages, and cloud services. This tool can identify all of your devices and it will create an asset inventory. This is a good tool for documenting your system and identifying firmware versions.
The Device42 system is available for on-premises installation or as a cloud-based service. Installation begins by logging an inventory of your equipment and backing up the configurations of each. The monitor sweeps the network continuously to look out for changes in the settings of your network devices. The tracker not only logs all device settings, it records the firmware versions of each. It also covers the operating systems of your servers and all of the applications and software loaded onto them.
The Device42 facilities are all locked off by authentication procedures. You can add new accounts for individual team members, so this tool would be great for middle-sized and large networks that are team-supported.
Device42 is paid for by a subscription. There are three plan levels for the tool, and fortunately, the configuration management module is included in the Core plan, which is the cheapest version of the software. You can get a look at the system with a free online demo. If you want to go ahead and buy the system, you get a 30-day trial period, so you can back out in the first month and get all of your money back. The software can be installed on Windows, Mac OS and you can get it on Linux computers through a virtual environment. You can also integrate the service with Azure, and AWS online services.
Who is it recommended for?
The Device 42 system keeps evolving and it configuration controls for physical devices are giving way to expanded cloud management features. This tool is a good option is your main need is to document all of your assets on a hybrid system and identify the physical, virtual, and procedural connections between them.
Pros:
- Unique Rack-Level Visualization: Offers a unique rack-level visualization, aiding on-site technicians in mapping physical infrastructure to specific services.
- SaaS or On-Premises: Provides flexibility in deployment with the option for Software as a Service (SaaS) or on-premises installation.
Cons:
- Complex Initial Configuration: The initial configuration process can be complex and time-consuming, potentially requiring more effort during the setup phase.
- Challenges in Creating Custom Affinity Groups: Users may find it challenging to create custom affinity groups, suggesting a potential area for improvement in customization features.
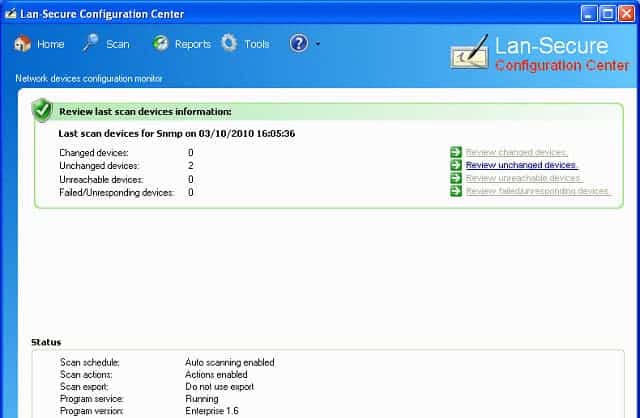
12. Lan-Secure Configuration Center
The Configuration Center from Lan-Secure has a no-frills interface, but it delivers a competent configuration management service. The tool has all of the essential capabilities that you need to control the settings of your network devices.
Key Features:
- Autodiscovery: Automatically identifies and discovers devices within the network, aiding in comprehensive visibility.
- Configuration Alignment to Standards: Ensures that configurations adhere to predefined standards, enhancing compliance and security.
- Automatic Settings Rollback: Provides the ability to automatically roll back settings to a previous state, mitigating the impact of undesired changes.
Why do we recommend it?
Lan-Secure Configuration Center has all of the features of the SolarWinds Network Configuration Manager but in a simpler interface. Use this utility as a terminal emulator to connect to a device and alter its configuration. You can then create a backup library and set the tool up to periodically check for deviations from the standard setup.
The Configuration Center will scan your system to register all of your network devices and then make backups of their settings. Once this admin phase has been completed, you can examine the configurations of your devices and decide on the correct policies for your company’s sector and data integrity obligations.
The network management software is able to manage a multi-vendor environment and will enable you to update the settings of all devices, specific device types, or individual devices.
The Configuration Center software will periodically check the settings of each device and compare them to the configuration backups it holds in storage. Depending on how you set up the system, the detection of an unauthorized configuration change will either prompt an alert or an automatic rollback to the approved settings held in the backup for that device. Alerts can be sent by email to a team member who has been allocated responsibility.
The tool can manage remote sites as well as the center where all of your configuration backups are stored. Inter-site communications are covered by SSH security.
Who is it recommended for?
There are two editions for this tool. The first is Configuration Center Workgroup, which will manage up to 10 devices. This is a good fit for SMBs and it is reasonably priced. The other option is Configuration Center Enterprise, which has no limit on the number of devices that it can manage.
Pros:
- Prevents of Changes to Hardware Settings: Can actively monitor and prevent changes to hardware settings, enhancing security and stability.
- Utilizes prominent Network Protocols: Utilizes popular network protocols such as SSH, Telnet, and SNMP to locate and communicate with devices, ensuring a versatile approach.
Cons:
- Rudimentary Interface: The interface is described as rudimentary, making it less ideal for larger deployments where advanced visualizations and features may be desired.
- Limited Mapping: Offers very limited mapping and dependency visualizations, potentially limiting insights into complex network structures.
The software can be installed on Windows. You have to pay for the Configuration Center, but it is very reasonably priced. You can get a 30-day free trial of the system to assess it before you buy.
Choosing a Network Configuration Management Tool
You will find some very comprehensive systems in this list and some worthy contenders that cost little to no money. When you select a configuration management system for your network, you will need to consider the system requirements, particularly the operating systems that the software can run on in order to narrow down your choices.
The size of your network and the availability of funds will be other important considerations that will guide you towards the right NCM tool for your company. The ability to try out a system on a free trial or the offer of a money-back guarantee should help you narrow down your assessment. If you can try before you buy without obligation, you will be more confident to install software. Otherwise, you might discover too late that it is difficult to use or inappropriate for your configuration management needs.
The field of cybersecurity is becoming very hot right now. However, don’t limit your network protection to just internet-facing equipment and measures. Sometimes, firewalls, attack protection services, and intruder detection systems fail. Your second line of defense lies in the control over the settings of your network devices and a policy to keep all firmware and operating systems up-to-date with the latest system updates and patches.
The comprehensive automation offered by many of the tools in this list means that you won’t need to spend too much time covering device configuration management. So, even if you run the network for a small company, there are no excuses for not implementing configuration management and change control on your network.
Have you implemented a configuration management system for your network? Which manager did you choose, and why? Leave a message in the Comments section below to share your experiences with the rest of the community.
Network Configuration Management FAQs
What is configuration management in network security?
Network configuration management involves standardizing the settings of network devices, such as switches, routers, and firewalls to make intrusion more difficult. One tactic that some hackers use to aid their undetected exploration of the network is to alter certain settings on switches. The security aspect of network configuration management requires that any unauthorized changes get rolled back immediately.
How do I check my network configuration?
There are many different aspects to look out for in network configuration. Visit the management console of each switch, check on IP address allocation through an IP address manager, and check on the port statuses of all devices connected to the network. This is a mundane and time-consuming activity that specialist software can achieve more effectively than manual procedures.

















i want to download best esay to use configration