IT systems face a wide range of potential threats, and it’s important to recognize that hacker attacks are not the only risks that organizations need to protect against. In addition to external cyberattacks, businesses must also consider the dangers posed by insider threats, whether intentional or accidental and the possibility of data loss or damage due to unforeseen circumstances.
A comprehensive approach to cybersecurity requires addressing both internal and external risks, and this necessitates a wide array of activities to ensure the robustness of your security framework. One of the most critical steps in securing your IT systems is conducting regular and thorough IT security audits. These audits help identify potential vulnerabilities and confirm that all aspects of your security strategy are functioning as intended.
Without regular audits, there is a higher chance of security gaps going unnoticed, which could be exploited by attackers. During an audit, it is essential to follow a structured approach, utilizing a detailed checklist to guide the review process. Relying on ad-hoc checks can be insufficient, as they often focus only on obvious security measures and leave out areas that may require more attention.
It is the overlooked or forgotten elements of system security that can create the greatest risks to your business. While focusing on commonly recognized threats is important, failing to address lesser-known vulnerabilities can leave your systems exposed to exploitation.
Overlooked gaps may become the weak points, or the “Achilles’ heel“, of your cybersecurity defenses. Therefore, it’s essential to take a thorough and methodical approach during audits to ensure every aspect of your IT infrastructure is secured against potential threats. This proactive strategy will help safeguard your business from both external and internal security risks. So, let’s look into how you can ensure that your system is as secure as it can possibly be.
Here is our list of the best automated IT security tools:
- ManageEngine ADAudit Plus EDITOR’S CHOICE This software package provides protection for Active Directory, file integrity monitoring, and compliance reporting. Available for Windows Server, AWS, and Azure. Download a 30-day free trial.
- ManageEngine Vulnerability Manager Plus (FREE TRIAL) This package scans all assets for security weaknesses including configuration errors and out-of-data software. Runs on Windows Server. Get a 30-day free trial.
- SolarWinds Access Rights Manager This manager for Active Directory helps to coordinate multiple instances of the ARM and aids in documenting user activity for compliance reporting.
- LogicGate A cloud-based IT risk assessment system.
What is an IT security audit?
An audit is an assessment of the system. There are many levels of security audits and different reasons to perform one. An audit can be performed in house with automated tools, others may require the input of external consultants to identify and adjust working practices that create security weaknesses.
Automated IT security audits are also known as vulnerability assessments, while procedural issues are dealt with by risk management. The cost and disruption of an external audit can be off-putting and so it is better to schedule those types of IT security audits less frequently than automated system scans. Installing standard-compliant monitoring software will perform compliance auditing tasks for you automatically.
Monitoring tools that can be adapted by standards conformance templates impose a set of working practices and produce compliance documentation without human intervention. An IT security audit can be made easier by instituting best practices that are software-enforced.
Types of security audit
An IT security audit examines systems and working practices, looking for weaknesses that could enable a data breach to occur or looking for evidence that a data breach has occurred. The auditor role is a professional position and there are standards body that issue certification for professionals who take out membership of the institute and sit exams to prove their knowledge. So, there are Certified Information Systems Auditors and Certified Internet Auditors who are qualified to carry out IT security audits.
Internal Audit
As the name implies, an internal audit is performed by a member of the organization. An internal audit is usually commanded by the board of directors rather than an elective exercise carried out by the IT department. The demand for an audit should also specify the standard to be achieved.
An internal audit is usually an infrequent exercise. It can be a system assessment that ensures that the business would pass an external audit.
The IT security audit is meant to identify problems that IT department managers hadn’t noticed and suggest potential loopholes that those managers hadn’t thought of, so those same managers are not the right people to set the agenda for the audit.
Some larger businesses have an internal audit department. Only very large companies have the volume and scope of business that enables them to justify having a qualified IT specialist auditor on staff. The audit department of smaller businesses might hire a specialist IT security consultant to strengthen the auditing team for the duration of the IT security audit.
External Audit
An external audit has more authority than an internal audit. Although an external auditor is being paid for by the company being audited, that auditing business is expected to be independent. It should not be susceptible to pressure in order to fudge the findings of the audit to put the IT system in a positive light.
The driving force behind an external audit is usually a contractual requirement or a legal obligation of the company to prove there are no security problems in its IT system. Currently, the main purpose of an IT security audit is to prove compliance with a data security standard, such as HIPAA, PCI-DSS, or SOX.
IT security audit methods
The two frameworks for IT security auditing are manual audits and automated audits. In reality, no IT audit will be entirely manual because auditors rely on tools to extract data from the system. Similarly, no audit can be entirely automated because a human needs to set the parameters of the automated tools and check the veracity of their output. However, there is more human involvement in a manual audit than in an automated audit.
Manual Audit
A manual audit is time-consuming and expensive. In order to be worthwhile and authoritative, the people running the audit need to be qualified IT auditing professionals, who command high salaries.
A professional auditor has the experience that directs the audit towards the important factors to look out for and the training that ensures the audit will be performed methodically and thoroughly.
A manual audit has the advantage of being able to include interviews with key staff. It can assess the competence of those running the IT system. A manual audit is also able to cover geographical issues, such as the location of key IT equipment and the physical security measures taken by the business.
The validity of a manual audit is dependent on the competence and reputation of the senior auditor that leads the investigator and the trust invested in the team that carries out the audit.
Automated Audit
A Computer-Assisted Audit Technique (CAAT) isn’t entirely automated. There need to be people to check and verify the implementation of the audit and its results. However, CAAT is a lot easier to perform than a traditional manual audit.
Automated audits are more effective when they are put into place permanently. The document base for an IT security audit can be built up over time, checking each transaction and event as it occurs. So, an automated audit can be performed incrementally. When an audit report needs to be submitted, it can be extracted immediately.
Ongoing auditing, implemented by automated processing also keeps the IT department on the straight and narrow. Standards templates built into the IT system prevent sloppy working practices and make it less likely that the business will fail any audit demanded by an external authority.
See also: Best Network Security Auditing Tools
IT security standards
While financial auditing is demanded by tax authorities, IT security audits are usually driven by a requirement to comply with a data protection standard – driven by contractual obligations or industry conventions. The main standards that require an audit for compliance proof are:
- PCI-DSS – PCI-DSS is a payment card processing requirement. A business will not be able to take payments from customers without PCI-DSS accreditation. The PCI-DSS standard is not interested in the security of a business’s entire IT system, just payment card details, and customer personal information.
- HIPAA – This standard applies within the health industry and those businesses that supply it. It is concerned with the personal information of patients.
- SOX – SOX stands for the Sarbanes-Oxley Act. It is a national legal standard in the USA that aims to prevent businesses from falsifying reports of their profitability and financial viability. Although this standard only applies to US businesses, it needs to be implemented in all overseas subsidiaries of US companies as well.
- GDPR – This data protection standard applies to EU countries. However, any non-EU business that wants to do business in the EU. It specifically relates to the security of personally identifiable information (PII) held in digital format.
- ISO/IEC 27000 – A family of standards produced by the International Organization for Standardization (ISO). These standards are not directly. However, they are often requirements set by businesses when writing contracts with associate companies, such as suppliers.
IT security audit frequency
Unlike financial audits, there is no government-enforced blanket requirement for IT security audit frequency. Many of the IT security standards include an accreditation renewal, which requires an audit. If you seek accreditation to one of those standards, you should follow the auditing requirements of that particular standard.
The convention with financial audits and IT security standards accreditation is to perform them annually and so that is the best practice for IT security auditing.
Proactive, automated auditing happens continuously. On-going auditing provides all of the necessary documentation required for a standards audit. If an external audit is commanded, a requirement of the business being audited is that it must have all of its records available for inspection without warning.
A common trigger for an IT security audit is the discovery of a data breach or a serious cybersecurity attack. After recovering from the attack, the company executives are likely to ask for an IT security audit to ensure that another security incident doesn’t happen.
IT security audit tips
IT security audits can be very disruptive. A manual audit in particular requires IT staff to take time out of their regular activities to support the information requirements of the auditors. Preparing for an audit can also be very time-consuming because it requires all relevant records to be located and made available in a suitable format.
There are steps that you can take to ensure that an audit runs smoothly and with minimum disruption to ongoing IT department activities.
- Identify sensitive data – A standards-driven IT security audit will focus on one specific data pool, such as payment card data (for PCI-DSS) or personal information (for HIPAA). Identify all data store locations for this type of data. Where possible, centralize all of the critical data types and focus security efforts there. If centralization is not possible, ensure that high-security measures are applied to all of the locations where that data is stored.
- Manage log files – Data standards require that all log files are available on demand for examination by an external auditor without notice. The retention period for this requirement varies by the standard. Archiving is OK, but archives should be easily restored to live availability for examination.
- Control resource access – institute an access rights management policy that coordinates access to layers of data and application sensitivity. Record all access events so that data breaches can be properly investigated.
- Enforce secure working practices – Use password lockers and credential distribution systems that rule out the necessity to send login credentials via email or written on pieces of paper. Ensure all activities are performed within the framework of the IT system so that they can be automatically logged and traced.
Make sure you know exactly which data standard you are expected to comply with and what data or transactions that standard relates to. Remove manual processes wherever possible and log all activities within the IT system.
IT Security Audit Checklist
Ease the audit process by ensuring that your IT department is prepared to support any audit demands at a moment’s notice.
- Specify the audit standard to which you need to comply.
- Identify the resources that the audit will examine.
- Allocate system security responsibility to key personnel for different system attributes.
- Train data security managers so that they are fully aware of their responsibilities.
- List current system security software: eg, firewalls, AV, SIEM tools, etc.
- Check all software and operating systems are fully patched and updated to the latest versions.
- Check log archives are available for searching.
- Create a set of security policies and document them, holding them in a specific folder, either digitally or on paper.
- Perform regular system vulnerability sweeps.
- Tighten physical access to servers document personnel security access levels.
- Implement centralized authentication control.
- Enforce password strength, 2FA, and password rotation on all user accounts.
- Remove inactive accounts.
- Implement peripheral device controls and reverse firewalls for data loss prevention.
- Enforce encryption to all data transmissions.
- Implement automated security scans and activity logging.
When an external audit team arrives, the above steps will ensure that they can perform a comprehensive security audit without your IT staff having to stop their regular work.
The best automated IT security audit tools
Deploy systems that control activities to block unsecured working practices and incrementally compile audit documentation. These tools make sure that you are constantly compliant with data security standards and could easily pass any flash audit.
Our methodology for selecting an IT security monitoring tool
We reviewed the market for security monitoring systems and analyzed tools based on the following criteria:
- Assessment of access rights management data
- Log collection and correlation
- Assessment tailoring for data privacy standards
- Automated assessment tools
- Formatted compliance reporting templates
- A free trial or a demo package that offers an opportunity for a no-cost assessment
- Value for money from an auditing tool that will save time and is offered at a reasonable price
With these selection criteria in mind, we have identified a range of tools that you should consider to support your IT system auditing requirements.
1. ManageEngine ADAudit Plus (FREE TRIAL)
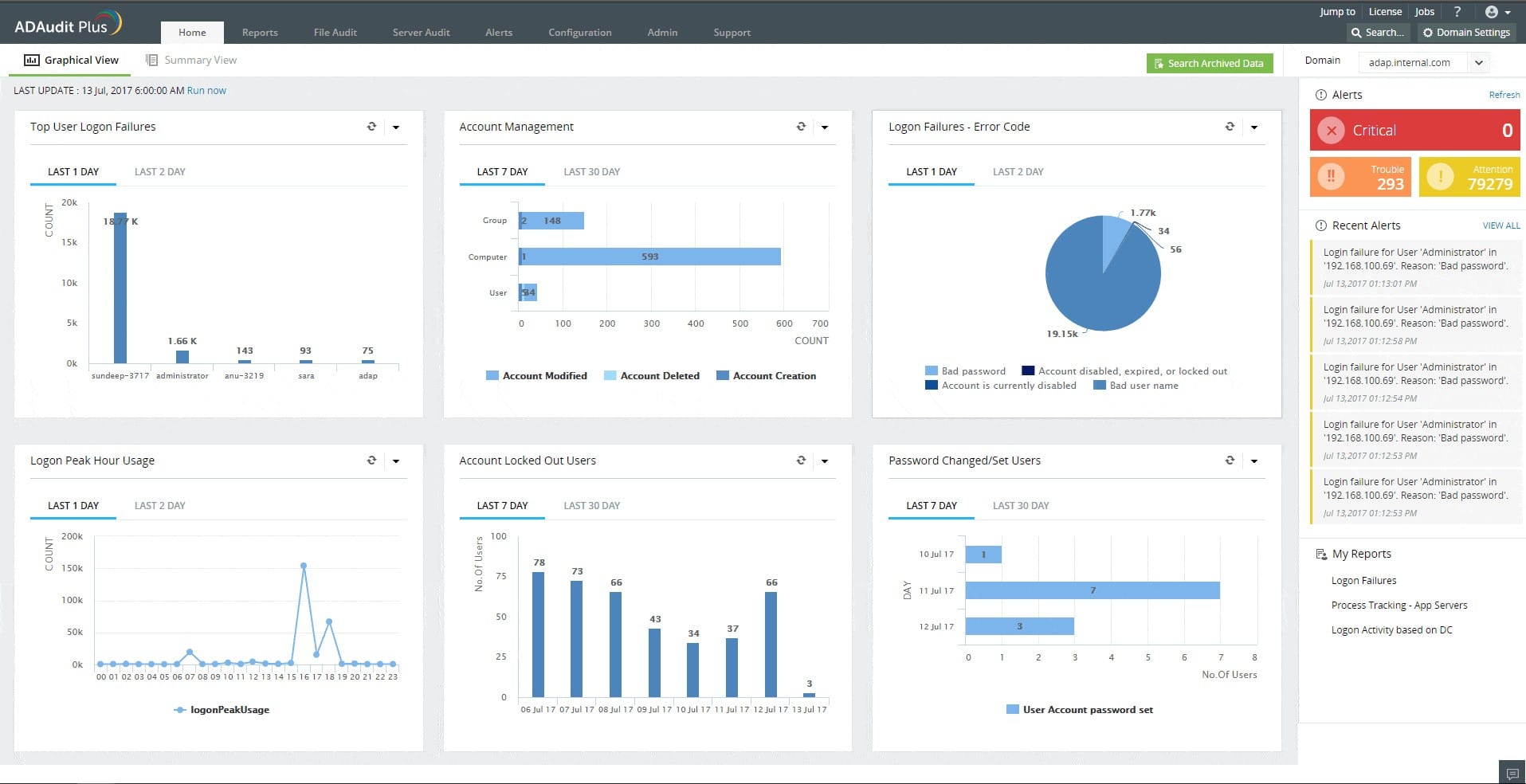
ManageEngine ADAudit Plus lays down the logs that security auditing needs to access. Without activity logs, you can’t report on what events occurred and whether they breached system security. By linking file access events to Active Directory, ADAudit Plus is able to log exactly which account did what to which files.
Key Features:
- File integrity monitoring
- User activity logging
- Log analysis
Why do we recommend it?
ManageEngine ADAudit Plus is a large package that tracks user activities and logs them. This is an ideal function for compliance auditing and for data loss prevention. The package is similar to the SolarWinds service because it relies on Active Directory as a reference for user accounts and device permissions.
ADAudit Plus also protects Active Directory instances because relating activity to users is meaningless if a hacker has created fake user accounts. This system includes a reporting module that scans through the logs that it created and summarizes them. This provides compliance reporting that is compatible with SOX, HIPAA, PCI-DSS, FISMA, and GLBA.
Who is it recommended for?
As it is linked to Active Directory, this system will only appeal to businesses that use AD for access rights management. The Free edition will appeal to small businesses because it can collect log data from 25 workstations. The base paid package is accessibly priced for small businesses and adds more functions to the 25-station data collection capacity of the Free plan.
Pros:
- Operates on Active Directory implementations on Windows Server, Azure, and AWS
- Records file access events by users
- Compliance reporting for SOX, HIPAA, PCI-DSS, FISMA, and GLBA
Cons:
- This is not a SaaS package
The ManageEngine ADAudit Plus is available for Windows Server, AWS, and Azure. The three editions for ADAudit Plus are Free, Standard, and Professional. The Free edition monitors up to 25 workstations and is a good tool for small businesses because it also includes compliance auditing. The Standard edition monitors activity on servers as well as workstations. The Professional edition has all of the functions of the Standard version plus Active Directory monitoring. You can get the Professional Edition on a 30-day free trial.
EDITOR'S CHOICE
ManageEngine ADAudit Plus is our top pick for an IT security audit tool because it provides comprehensive, real-time auditing and monitoring capabilities for Active Directory environments, ensuring strong security across IT infrastructures. With the increasing complexity of modern networks, securing sensitive data and monitoring user activities have become critical tasks. ADAudit Plus specializes in tracking changes to Active Directory, file systems, and user activities, offering detailed insights into who did what, when, and where. One of the most important features of ADAudit Plus is its ability to monitor and generate alerts for suspicious activities in real-time. It tracks login attempts, privilege escalations, failed authentication attempts, and modifications to critical objects in Active Directory. By instantly notifying administrators of any irregularities or potential security breaches, the tool enables rapid response, minimizing the risk of data theft, unauthorized access, or internal threats. ADAudit Plus supports customizable reports for compliance standards such as PCI DSS, HIPAA, and GDPR, making it easier for organizations to meet regulatory requirements. The tool’s in-depth audit trails allow for forensic analysis, enabling teams to trace security incidents back to their source. With its real-time alerts, detailed reports, and compliance-ready features, ManageEngine ADAudit Plus is an essential IT security audit tool for organizations seeking to enhance security, maintain audit trails, and ensure regulatory compliance.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/products/active-directory-audit/download.html
OS: Windows Server
2. ManageEngine Vulnerability Manager Plus (FREE TRIAL)
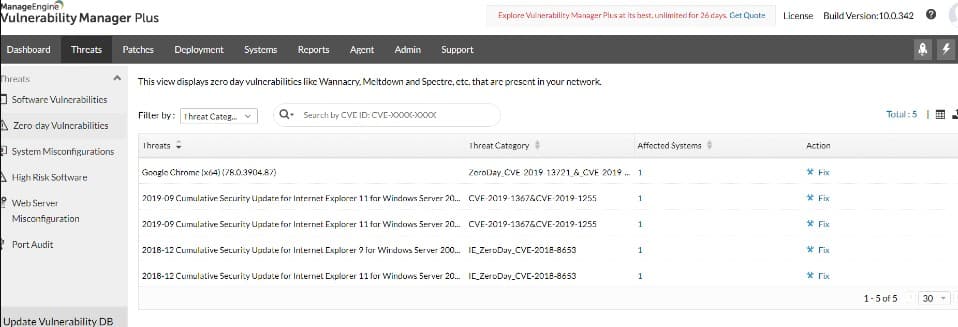
ManageEngine Vulnerability Manager Plus is the ultimate security audit system because it will scan all of your devices and identify their security weaknesses. The list of errors includes a button that commands an automated fix. If this is not available and manual action is needed, the system provides tips on how to fix the problem.
Key Features:
- CIS benchmark compliance
- Security tips
- Automated fixes
Why do we recommend it?
ManageEngine Vulnerability Manager Plus is a good choice for preventing threats rather than waiting for them to happen in order to discover system weaknesses. This preventative service will identify both configuration mistakes and out-of-date software. A patch manager within the bundle takes care of necessary software updates.
The package is able to scan computers running Windows, macOS, and Linux. The top plan, called the Enterprise edition, can even scan devices on multiple sites from one location. That edition is also necessary if you need a full compliance reporting function included in the package. ManageEngine provides a Free edition, which is able to manage 25 endpoints.
Who is it recommended for?
This package is suitable for businesses of all sizes. However, you need to have a host running Windows Server, so if you don’t have that operating system on site, you will need to look elsewhere for a vulnerability manager. The Free edition will appeal to small businesses and the Professional edition is reasonably priced for mid-sized companies.
Pros:
- Includes a patch manager for automated software updates
- Provides configuration tightening
- Compliance reporting in the Enterprise edition
Cons:
- Only available for Windows Server
You can download a 30-day free trial.
3. SolarWinds Access Rights Manager
SolarWinds Access Rights Manager was created with standards compliance procedures so it is a validated tool for conforming to GDPR, PCI-DSS, HIPAA, plus other data security standards. Auditing reports are built into the Access Rights Manager, which makes both internal and external audits quicker and easier to complete.
Key Features:
- User account management
- Account clean up
- Operates on Active Directory
- Compliance with PCI-DSS, HIPAA, and GDPR
- Self-service portal for users
Why do we recommend it?
SolarWinds Access Rights Manager provides an interface to Active Directory that makes domain controllers easier to manage and coordinate. The system also provides object change logging and user behavior tracking. Both of these functions are important for compliance management. The system provides auditing for file servers, SharePoint, and Exchange Server.
This software installs on Windows Server and it pays attention to Active Directory implementations, centralizing account management across sites and applications. It includes account analysis features that enable you to identify insecure and inactive accounts. It also includes a self-service portal to enable users to update their own accounts and it can enforce password strength and renewal policies. You can get a 30-day free trial of the SolarWinds Access Rights Manager.
Who is it recommended for?
This solution is most suitable for large organizations. This is a high-end tool with a lot of features and smaller companies probably wouldn’t need all of the capacity of this service. The SolarWinds system is specifically designed for auditing and managing Microsoft tools and it needs a host running Windows Server.
Pros:
- Provides a clear look into permission and file structures through automatic mapping and visualizations
- Preconfigured reports make it easy to demonstrate compliance
- Any compliance issues are outlined after the scan and paired with remediation actions
Cons:
- SolarWinds Access Rights Manager is an in-depth platform designed for sysadmin which may take time to fully learn
4. LogicGate
LogicGate is a cloud-based governance, risk management, and compliance (GRC) tool. Among LogGate’s services is an IT security risk assessment system that can be tailored to specific data standards, such as GDPR, PCI-DSS, and SOX.
Key Features:
- Cloud-based
- GDPR, PCI-DSS, and SOX compliance
- Risk assessment
Why do we recommend it?
LogicGate provides compliance auditing for the major data security standards. Fortunately, compliance reporting is not an isolated function and while ensuring that the business is compliant with data protection standards, the business also performs comprehensive security auditing with this tool. This is a cloud-based system that relies on log collector agents.
This service creates a risk framework tailored to your industry and the standards that you need to comply with. LogicGate can also produce IT security audit guidelines, which are useful for a pre-assessment check as well as a tool for those performing the audit itself.
Who is it recommended for?
LogicGate offers a range of risk management tools from its cloud platform and that list includes security auditing. Annoyingly, the company doesn’t publish its price list and that will deter price-conscious small businesses and startups from enquiring about this platform. The system is able to extend auditing out to suppliers and other associated businesses.
Pros:
- Supports GDPR as well as other popular compliance standards
- Features a customer portal where third parties can make data requests in a secure and auditable way
- Automated alerts can keep teams informed of compliance issues as well as breaches
- Sysadmin can build their own asset inventories and apply custom permissions based on their needs
Cons:
- Pricing is not transparent
- Must contact sales for a demo, no free download
IT Security Audit FAQs
What are the key elements of an IT security audit?
The outline for an IT security audit includes five stages:
- Objectives definition
- Audit plan
- Implementation
- Reporting
- Adapt the system where recommended
What is IT security audit and how does it work?
An IT security audit is a systematic check on the security procedures and infrastructure that relate to a company’s IT assets. The purpose of the audit is to uncover systems or procedures that create security weaknesses. This is a management process that is similar to the technical exercise of a vulnerability scan. The IT security audit extends beyond a check of all software settings to working practices and issues such as user security awareness.
What are the 3 broad types of IT security?
The three types of IT security are:
- Physical – Measures to prevent unauthorized personnel from getting access to the computers and other IT infrastructure elements owned y the company.
- Administrative – Relates to working practices and the involvement of humans in the IT system, this also covers issues such as access rights management and password policies.
- Technical – Defines system settings and security monitoring that provide automated security controls and remediation.