Modern network monitoring software includes sophisticated tools, such as graphical representations and analytical tools. However, there will be times when you will need to go back to the nuts and bolts analysis techniques of capturing packets as they travel around the network. Port mirroring is a packet capture technique.
Packet capture requires a hardware element, which is called a TAP (test access point). Fortunately, you already have hardware that channels all of your network traffic: switches and hubs. You can harness the capabilities of these devices to eliminate the need to buy a separate inline sensor or traffic splitter. The technique of using your network equipment to capture traffic is called “port mirroring.” This guide will give you all of the information you need to implement port mirroring on your network.
>>> Jump to the list of recommended monitoring tools below<<<
Switch traffic processing
A very small network would only have one switch or hub. However, it doesn’t take much growth in the network to create a requirement for another switch. When you have several switches on your network, they move traffic on without channeling all packets through a central point.
This decentralized configuration means that you can’t select just one switch on the network for data gathering if you want to sample traffic from all of your data. This is because the other switches on your network will be exchanging traffic between them that doesn’t need to be channeled through your chosen device. However, this issue would also arise if you chose to implement a TAP as a packet capture tool.
When capturing network traffic, you need to decide whether your requirements can be fulfilled by the packets passing one point, or whether you need to see all network traffic behavior on the entire network all at once.
In reality, it is more probable that you will need to look at the traffic per link. In such a scenario, you will probably be trying to see why one link on your network is overloaded and which types of traffic you could reroute or throttle in order to resolve the problem.
Although you might want to see all network traffic, capturing all of it all at once soon becomes an overambitious goal. If you could capture all incoming and outgoing packets you would become overwhelmed by all of the collected data.
In order to properly assess the performance of your network, you are going to categorize all traffic by network device anyway, so it is better to use port mirroring on a device-by-device basis. Other tools are better suited to giving you a whole network visibility. In these instances, you would be better off using NetFlow to sample data from several network points simultaneously. You would need a sophisticated network traffic analysis tool to aggregate and summarize all traffic data.
What is port mirroring?
Port mirroring offers a method of duplicating network traffic and directing the copy towards a data store.
In a splitter, you use a device that duplicates all traffic with one copy continuing to its intended destinations and the other showing on a screen or going to a file. With port mirroring, you use exactly the same technique, but you alter the settings of your switch to create a data duplication function, thus removing the need to install a separate physical device.
Essentially, a port mirroring instruction tells the switch to send a copy of traffic to a specific port. The methodology includes a range of options, enabling you to choose specific traffic originating from or traveling to given IP addresses, or choosing to copy all traffic. Once the switch has split the required traffic, all you have to do is collect the packets that are sent to the port designated as the data delivery point.
Switches and hubs
A link, or “hop,” on a network is the connection between two devices. The link might be the last stretch that connects an endpoint, or it might be between two network devices. There will always be a network device on at least one end of the link. For traffic within a network, that device will be either a switch or a hub.
A hub transmits all of the traffic that it receives on one of its connections out to all of the others. It doesn’t pay attention to the destination address on the incoming packets. A switch is more selective because it examines packet headers and forwards each to the port that it has listed for that address. The cable connected to that destination port might not lead to the endpoint that is identified by that address. If there is another network device between that switch and the endpoint, the cable that receives the moving data will lead to that intermediate device, which, in turn, will forward it on.
Fortunately, for packet capture, switches and hubs don’t forge temporary physical links between the source and destination ports in a connection. Instead, the device collects the incoming data. It then creates an exact copy of that data and applies it to the destination port. In the case of hubs, this action creates duplication. For example, if a hub receives a packet on one of its ten ports, it will send that same packet out on all of its other nine ports.
So, one packet becomes nine copies. A switch does exactly the same thing with packets that are marked for broadcast. Traffic that is traveling to one destination only gets copied onto the port that the switch has listed for that address. So there continues to be only one instance of that data as it travels out of the switch.
The duplication of packets performed by switches and routers is exactly the same as the work performed by a traffic splitter.
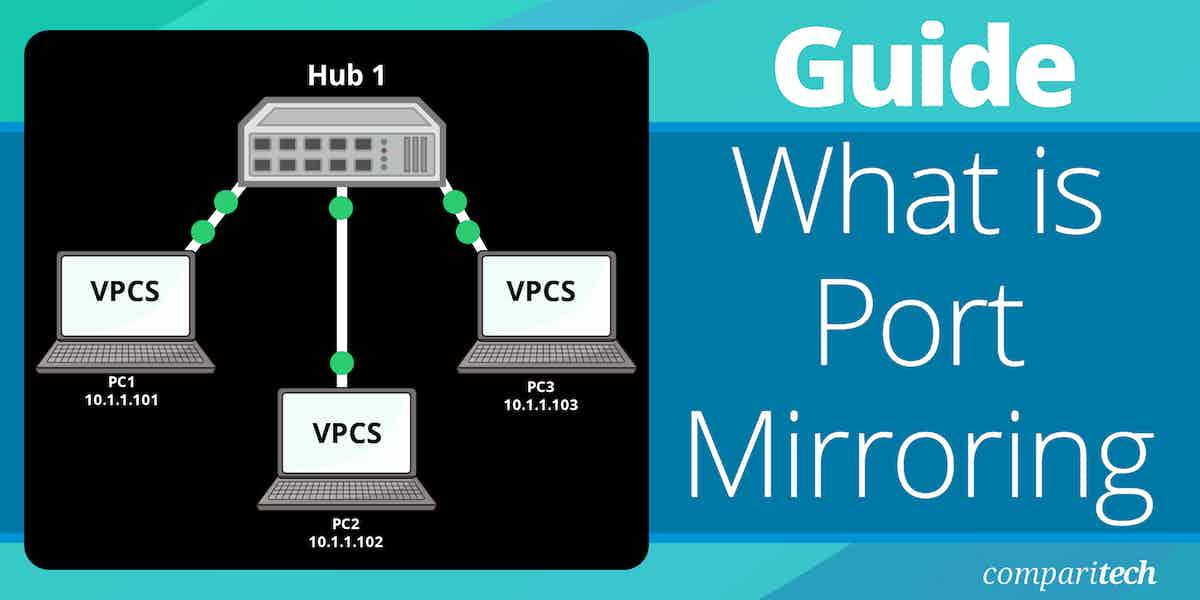
Port mirroring with a hub
As you can see from the descriptions of how switches and hubs work, a hub automatically duplicates all of the traffic that it receives. So, if you only have hubs on your network, it is very easy to get a copy of all of the traffic circulating on it. The hub sends all traffic to all endpoints. If that traffic has to travel through other network devices to reach some of the endpoints on the network, that won’t block the traffic getting to those endpoints if the intermediate devices are also hubs.
As your own computer is connected to one of the hubs on the network, all of the traffic on the network will automatically get sent to your computer without having to alter the settings of the hub. Your computer won’t read in all of that traffic, however.
The firmware on your computer’s network interface card has an identifier hard-coded into it: this is the MAC address, which stands for “media access controller.” The network card will only react to arriving messages that have that MAC address on them. All others will be ignored. Think of the network card as a doorman at a private club. Anyone arriving has to give a password in order to get in; those without the password get blocked from entering. The MAC address is that password.
If you want to see all of the traffic on a network that is equipped entirely with hubs, all you have to do is tell the network card to drop the requirement for its own MAC address. In network terminology, this setting is called “promiscuous mode.”
Purists will argue that putting your network card in promiscuous mode is not “port mirroring,” because your network card is not duplicating packets. They say the card is just dropping the requirement for its MAC address in order to recognize arriving packets and forward them to applications on your computer.
In truth “port mirroring on a hub” is a redundant concept because the hub duplicates all packets by default. Generally, the term “port mirroring” is only applied to switches.
Port mirroring with a switch
When a switch receives a packet, it references the destination address in the header of the datagram. It then makes a copy of the packet and sends that new version out on the port number that it has associated with that MAC address.
In standard operations, which is termed “unicast,” only one copy is made of an incoming message and that is sent out only on one port. Switches are capable of duplicating traffic, however. For example, when the switch receives a broadcast message, it makes the same number of copies as its count of active ports and sends one copy out on each of those ports. Switches also have “multicast” capabilities, which require them to create a limited number of copies.
As all switches are programmed with the ability to handle broadcast and multicast messages, the task of duplicating packets does not present their hardware with a problem. Conceptually, getting your switch to perform packet duplication requires very few tasks:
- The switch is instructed to make a copy of all traffic.
- The switch sends all traffic onto its intended destination.
- The switch sends a copy of all traffic to a nominated port.
- You collect all traffic at the nominated port.
Getting all packets duplicated traveling through a switch is a very simple job and doesn’t use up very much extra processing effort on the part of the device. If you want to examine the packets traveling through a specific switch, you just need to tell it to duplicate all of that traffic and send it to a port and also tell it to associate the MAC address of your computer with that designated port number. You then need to put your computer’s network card into promiscuous mode to ensure that it will pick up all traffic and not just those datagrams with its MAC address on them.
Duplicating all network traffic
The solution above is a simplified version of what actually happens in a switch when it performs port mirroring. In reality, the task is a little more complicated. For example, it would be inconvenient to have to connect your computer directly with a cable to a switch in order to pick up all of its traffic. In the old days, that was a requirement of LAN analyzers, and a location-specific connection is still a key feature of network TAPs.
Thanks to routing technology, modern port mirroring is more sophisticated. You can examine the traffic passing through any switch anywhere in the world, just as long as that switch is reachable from your location either over the network or across the internet. You do not need to physically connect your computer to that switch. When traveling across the internet, port mirroring gets a little more complicated because datagrams need extra packaging at the Internet network layer. For this guide, we will only deal with port mirroring from within a network.
Most switches have the capability to deliver captured packets across a network, traveling through other network devices. Each switch manufacturer produces its own firmware for its switches and the management console menu is different for each. For the purposes of this guide, we will focus on the methods used by Cisco Systems to make port mirroring available on its network switches.
About Cisco SPAN switches
The Cisco switch port mirroring facility is called SPAN. This stands for Switched Port Analyzer. SPAN gives you all of the capabilities to capture packets on any Cisco switch, whether or not you are directly connected to that switch. However, you need to have a spare port on a switch that can become the collection point for duplicated packets.
In SPAN terminology, a “source port” is a port that traffic is being duplicated from. The “destination port” is the address of the port that the duplicated packets are sent to for collection. Be very careful to remember these distinctive terms because you will be tempted to refer to your traditional networking terminology when you are looking at packets that run from a source port to a destination port.
The SPAN system is able to monitor one port or many ports. It is also possible to identify the direction of traffic at that port, giving you only inflow, only outflow, or both. However, if you are examining a number of ports at once, they all have to have the same traffic flow direction monitored.
You aren’t able to specify the from and to ports to capture, (i.e. only get traffic arriving at a specific port that leaves from a specific port). If this is the functionality you are looking for, pick the inflow port and capture all of the received packets there. You can then filter out all traffic except that leaving on the transmitted port of interest once you have all of the data in your analysis software.
In a session, you can either monitor ports or monitor VLANs – you can’t cover both types of ports at once.
Cisco SPAN modes
Cisco SPAN enables you to capture packets via three modes:
- Local SPAN: Monitor traffic on a switch to which you are directly connected.
- Remote SPAN (RSPAN): Monitor traffic on a remote port, but get the captured packets sent to a port on your local switch for collection.
- Encapsulated Remote SPAN (ERSPAN): The same process as RSPAN except that the transfer of mirrored packets to your local switch is carried by GRE encapsulation.
The RSPAN option isn’t available on Express 500/520, 5500/5000, 3500 XL, 2940, 2948G-L3, and 2900XL switches.
Cisco SPAN availability
SPAN is available on all of the following Cisco switch models:
Catalyst Express 500 / 520 Series
- Catalyst 1900 Series
- Catalyst 2900XL Series
- Catalyst 2940 Series
- Catalyst 2948G-L2, 2948G-GE-TX, 2980G-A
- Catalyst 2950 Series
- Catalyst 2955 Series
- Catalyst 2960 Series
- Catalyst 2970 Series
- Catalyst 3500 XL Series
- Catalyst 3550 Series
- Catalyst 3560 / 3560E/ 3650X Series
- Catalyst 3750 / 3750E /3750X Series
- Catalyst 3750 Metro Series
- Catalyst 4500/4000 Series
- Catalyst 4900 Series
- Catalyst 5500/5000 Series
- Catalyst 6500/6000 Series
Unfortunately, the command set is not the same on all switches. This is mainly because the company has a specialized firmware for some of its Catalyst devices, which is called CatOS. Other Cisco switches use an operating system called IOS, which is not the same as the iOS operating system used by Apple devices.
A few Cisco switches do not have native port mirroring capabilities, but there is a free utility that you can use in these circumstances, which you will read about shortly.
Set up SPAN on IOS switches
For switch models with the IOS firmware, you need to get to the device’s operating system and issue a command in order to specify the SPAN port and the port to monitor. This task is implemented by two lines of commands. One needs to specify the source, which means the port that will have its traffic replicated and the other gives the port number that the sniffer is connected to – this is the destination line.
monitor session <number> source [interface | remote | vlan] <port number or range> [rx | tx | both]
monitor session <number> destination interface <port number >Once you have finished defining the mirror, you need to press CTRL-Z to end the port mirroring configuration definition.
The session number just enables you to create several different monitors running simultaneously. If you use the same monitor session number in a subsequent command, you will cancel the original trace and replace it with the new specification. Port ranges are defined by a dash (“-“) and a sequence of ports are separated by commas (“,”).
The last element in the command line for the source port (the port to be monitored) is the specification of whether the switch should replicate packets transmitted from either port, or both.
Set up SPAN on CatOS switches
More recent Catalyst ranges are shipped with a newer operating system, called CatOS, instead of the older IOS operating system. The commands used to set up SPAN mirroring in these switches is a little different. With this operating system, you create mirroring with just one command instead of two.
set span <src_mod/src_ports...|src_vlans...|sc0> <dest_mod/dest_port> [rx|tx|both]
[inpkts <enable|disable>]
[learning <enable|disable>]
[multicast <enable|disable>]
[filter <vlans...>]
[create]The source ports are defined by the first element in this command, which is the “src_mod/src_ports” part. A second port identifier on the command is automatically read as the destination port – that is, the port to which the packet sniffer is attached. The “rx | tx | both” element tells the switch to replicate the packets transmitted from either port, or both.
There is also a set span command to turn off mirroring:
set span disable [dest_mod/dest_port|all]Set up SPAN on Catalyst Express 500 and Catalyst Express 520 switches
If you have a Catalyst Express 500 or Catalyst Express 520 switch, you don’t enter the SPAN settings at the operating system. In order to communicate with the switch and alter its settings, you need to install the Cisco Network Assistant (CNA). This network management software is free and it runs on the Windows environment. Follow these steps to get SPAN active on the switch.
- Log into the switch through the CNA interface.
- Select the Smartports option in the CNA menu. This will display a graphic representing the port array of the switch.
- Click on the port that you want to connect the packet sniffer to and select the Modify option. This will bring up a pop-up window.
- Select Diagnostics in the Role list and select the port that will have its traffic monitored from the Source drop-down list. If you want to specifically monitor a VLAN, select it from the Ingress VLAN list. If you aren’t aiming to just watch traffic for a VLAN, leave this value at its default. Click on OK to save the settings.
- Click on OK and then Apply in the Smartports screen.
One problem with the CNA method is that the software only runs on Windows versions up to Windows 7.
Captured packet processing
The port mirroring set up on your switch will not store or analyze the captured packets. You can use any network analysis software to process the packets that are sent to your device.
A key issue that you are going to have to recognize when you capture packets is that you are going to have to deal with a very large amount of data. A raw text dump of passing network traffic is almost impossible to comb through without a guided data viewer. This is the very lowest category of data accessing tool that you should consider. A full traffic analysis utility would be even better.
You can see a comprehensive list of recommended network traffic analysis tools in the article, Best Packet Analyzers / Packet Sniffers. For convenience, the top two network tools in that review are summarized below.
SolarWinds Deep Packet Inspection and Analysis tool (FREE TRIAL)
SolarWinds produces a large catalog of network monitoring and management tools. For port mirroring output analysis, you should consider the company’s Deep Packet and Analysis tool to be your best option. This is part of the company’s Network Performance Monitor, which is its central product.
Why do we recommend it?
SolarWinds Network Performance Monitor provides a range of network monitoring services that include the Deep Packet Inspection tool. This system examines packet headers for information such as port numbers for protocol analysis. With this information, you can see what traffic is traveling around your network and in what volumes.
This tool is able to interpret data sourced from a wide range of packet collection tools and will let you see where traffic surges occur. You need to look at the applications that are generating most of the demand on your network in order to construct strategies to improve performance. This analysis tool supports those investigations.
Who is it recommended for?
The Network Performance Monitor is a comprehensive package and it is suitable for use with large networks. The system’s main function is as a device health monitor and it detects all of the equipment on a network to create an inventory and a network topology map.
Pros:
- Takes a holistic approach to server performance and health monitoring
- Supports auto-discovery that builds network topology maps and inventory lists in real-time based on devices that enter the network
- Supports both SNMP monitoring as well as packet analysis, giving you more control over monitoring than similar tools
- Uses drag and drop widgets to customize the look and feel of the dashboard
- Robust reporting system with pre-configured compliance templates
Cons:
- Designed for IT professionals, not the best option for non-technical users
The Network Performance Monitor is a top-of-the-line tool and it isn’t free. However, you can get a 30-day free trial. Remember that packet capture is not really a feasible option to monitor all of the traffic on all of your network. For those situations, you would be better off with the SolarWinds NetFlow Traffic Analyzer. This employs Cisco NetFlow functionality to sample traffic from the network. It is also able to communicate with Juniper Networks equipment through the J-Flow packet sampling standard, with Huawei devices, using NetStream, and it can also use the manufacturer-independent sFlow and IPFIX traffic analysis systems. You can also get the NetFlow Traffic Analyzer on a 30-day free trial.
The Network Performance Monitor and the NetFlow Traffic Analyzer make a good combo for network analysis because they give you an overview perspective and the tools to examine packet traffic running through individual devices. SolarWinds offers these two tools together as the Network Bandwidth Analyzer Pack, which you can also get on a 30-day free trial.
Paessler Packet Capture Tool
Paessler PRTG is a network monitoring tool that is composed of many individual sensors. One of these tools is a packet capture sensor. This sensor doesn’t come with a physical TAP; instead, it relies on the data supplied in a stream from your switches. This tool offers great data visualizations for both live data and for packets read from file storage.
The great thing about PRTG is that it can offer you different layers of visibility from within the same tool. It also includes sensors that sample network data, capturing just packet headers from different locations on the network. You can also reduce the amount of data that needs to be processed by the monitor by specifying sampling.
As well as the packet sniffing sensor, PRTG includes the following traffic sampling systems:
- A NetFlow sensor
- An sFlow sensor
- A J-Flow sensor
With this system, you could use the NetFlow, sFlow, and J-Flow sensors to get an overview of your entire network and then go to the packet sniffer to focus on the typical flows at one device. Once you have isolated an overloaded switch, you can then home in on the specific ports that have too much traffic and look at the traffic types that are overwhelming it. With this information, you can either implement traffic shaping measures or choose to add on more infrastructure to reroute heavy traffic points and spread the load.
The packet sniffer sensor only processes the headers of traffic datagrams traveling around the network. This strategy reduces the amount of processing needed to aggregate flow metrics and greatly speeds analysis.
Why do we recommend it?
Paessler PRTG provides the Packet Sniffer sensor, which reads the headers of packets on your network. This tool doesn’t store packet headers or display them. Instead, the system aggregates data from all packets to provide you with counts of packets per protocol and identifies issues such as the most active endpoints.
Who is it recommended for?
PRTG is a bundle of sensors and you pay for an allowance of them. This makes the system suitable for businesses of all sizes because you can tailor it to give you only the monitors that you need. The software installs on Windows Server and it is also available as a SaaS platform.
Port mirroring issues
Full packet capture and storage might run you into problems with data confidentiality. Although most of the traffic passing on your network will be encrypted, if it is destined for external sites, not all in-house traffic will be encrypted. Unless your organization has decided to implement extra security for emails, the mail traffic around your network will not be encrypted by default.
As an alternative traffic analysis technique, you could consider using NetFlow. This is a messaging system that is enabled on all Cisco devices and it will forward just the headers of packets to a central monitor. You can read about network monitors that collect NetFlow data in the article Best NetFlow Analyzers and Collector Tools.
Once you have the information at your fingertips about all of the traffic monitoring capabilities of your Cisco switches, you will be in a better position to decide which packet capture method to use.
Choosing the right network analysis strategy
Hopefully, this guide has made you aware of the issues that surround port mirroring. Although there are times when you really can’t avoid getting down to packet level in order to properly assess your network traffic, you should narrow down your research with other tools before you arrange a packet capture as a task.
Port mirroring has its problems – it breaks data confidentiality and it can generate very large amounts of data. Explore methods to aggregate traffic information as your first line of investigation and get to port mirroring once you have identified links with problems. Once you set up port mirroring on your switches, be sure to channel all of the data into an analysis tool so that you can make proper use of all of the information that this strategy will generate.
Port Mirroring FAQs
What is the difference between port mirroring and traffic mirroring?
The main difference between port mirroring and traffic monitoring is that a traffic monitor collects statistics on packets as they pass through switched and routers but port mirroring takes a complete copy of all of those packets.
Does port mirroring affect network performance?
According to Cisco Systems, the leading producer of network switches, port mirroring does not place a heavy load on switches. The switch doesn’t have to process the extra stream that is generated by mirroring, it only duplicates an output that it was already having to work on.
What is a span port on a switch?
A span port is really a SPAN port – SPAN stands for Switched Port Analyzer. The SPAN port is dedicated to providing a channel for packet analysis – it is actually a virtual port.