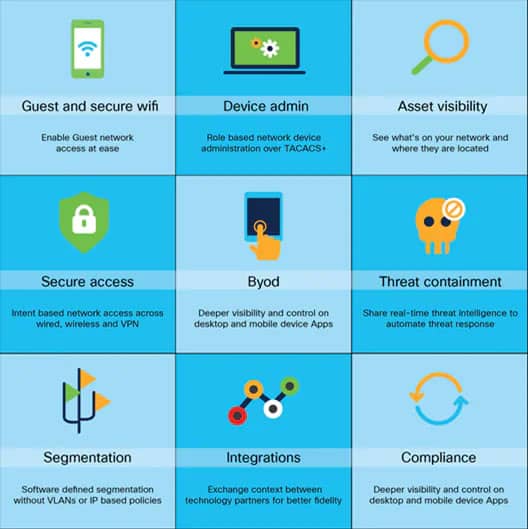
As BYOD policies and the number of mobile devices accessing networks continue to proliferate, the enterprise attack surface grows wider, bringing in new security risks and vulnerabilities. It is therefore critical to have tools that provide improved network visibility and access management to protect devices and indeed the entire network from threats.
To address these challenges, Network Access Control (NAC) solutions are the answer. NAC solutions support network visibility and access control through policy enforcement on devices and users of corporate networks. It aims to do exactly what the name implies—control access to a network with policies, including pre-admission endpoint security policy checks and post-admission controls over which users and devices can go on a network, and what they can do.
Here is our list of the best network access control software:
- Twingate EDITOR’S CHOICE This software package enables the operators of hybrid systems to implement a range of secure network strategies that protect both on site assets and cloud platform resources. Host it on Linux or a cloud platform. Get a 14-day free trial.
- ThreatLocker Network Access Control (GET FREE DEMO) This cloud-based tool implements a form of security policy posture management that selectively allows or denies devices to connect through the corporate network. Access a free demo.
- Cisco Identity Services Engine (ISE) This package focuses on access controls for zero trust access strategies and deals with device security – it covers wireless protection as well as LAN and virtual network security. Available as a physical or virtual appliance.
- Forescout Platform A SaaS system that will connect to and protect a multi-vendor environment and is suitable for large organizations.
- Fortinet FortiNAC A device scanner that assesses exhg device for security risk level before allowing it onto the network. Offered as a device or a virtual appliance.
- HPE Aruba ClearPass Policy Manager A SaaS platform that provides security scoring for devices on and off the network before allowing them to connect and includes a self-enrollment portal.
- Ivanti NAC Device discovery, security scanning, and onboarding from this system that is delivered as a network device or a virtual appliance.
- OPSWAT MetaAccess NAC A device detection and security assessing tool that pre-checks devices so that they can connect to the network. Offered as a physical or virtual appliance.
A NAC application can be set up to assess the security posture of devices attempting to connect to your network to determine if they meet predefined standards such as device type, OS version, update, and antivirus status, among others. If it doesn’t, the user is either denied access or placed onto a quarantined network segment until problems are rectified.
When evaluating NAC software or appliances, you need to ensure that it has the right features and capabilities that address your security risks and policy requirements. Some of the key questions to consider include: What do you need a NAC solution for; to manage guests, BYOD, IoT devices, or a combination of those? Is the NAC software able to integrate with existing software and network infrastructure? Does it support all kinds of endpoint devices—PC, Mac, Linux, Android, etc? Does it contribute to achieving compliance requirements? Is vendor support available in your region, and to what extent? Other factors to consider include features, agent or agentless implementation, and of course total cost of ownership.
The best network access control software
With such a huge range of NAC applications out there, choosing the right one for your business and budget can be challenging. In this article, we’re going to review the six best NAC applications in the market. Hopefully, this will guide you as you decide on the right NAC solution for your business.
Our methodology for selecting a network access control system
We reviewed the market for NAC software and analyzed the options based on the following criteria:
- Network segmentation for stronger security
- Compatibility with widely-used network management systems
- Covers all major operating system
- New device detection
- Data protection standards compliance
- A free trial or a demo service that offers a cost-free assessment opportunity
- Value for money from a comprehensive and easy-to-use system at a fair price
Using this set of criteria, we looked for network access control software that will enforce your system security.
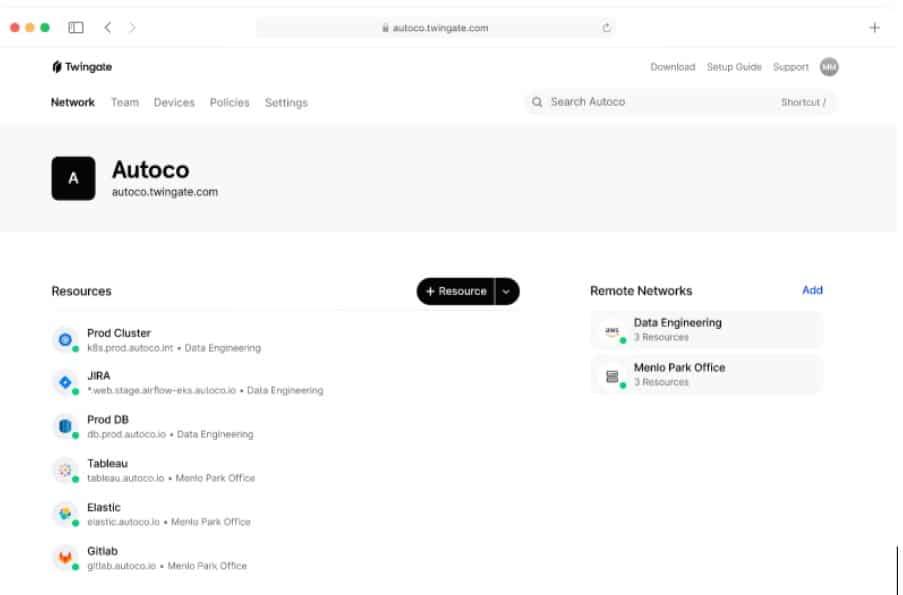
1. Twingate (FREE TRIAL)
Twingate is a software solution for network access controls – you won’t get an appliance with this package. The Twingate solution controls access to applications and resources rather than implementing specific network access controls. This is because Twingate addresses the current dilemma that network manager face, which is that the office network no longer holds all of the resources that users need.
Key Features:
- Zero Trust Access: Application fencing
- Network Policy Enforcement: Scans devices for security weaknesses
- User Access Apps: Combines internet security with access authentication
- Single Sign-On: The app login gets rippled through to application access
- Hybrid System: Protects on-premises and cloud resources
Why do we recommend it?
Twingate is a VPN-based solution. The VPN client that goes on each user’s desktop requires a login and it enables credentials to flow through to access controls for network resources, applications, and SaaS accounts. This is a very easy system for any system administrator to set up and manage.
Access Control Lists can implement specific controls for different resources deep within a network while being run at the edge of the network. Using these techniques allows the segmentation of the network into security zones. Taking this segmentation down to its ultimate level, access control narrows down to protecting specific devices and then each application on each device.
Taking network segmentation down to its smallest unit is called micro-segmentation and it is the basis of Zero Trust Access (ZTA). this is where Twingate operates. Administrators don’t have to deal with Access Control Lists (ACLs) when using Twingate. This system operates in a similar format to Active Directory. Administrators create user accounts and a resource list. The resources are usually applications – particularly cloud-based SaaS systems – rather than infrastructure elements, such as a network or a server.
Who is it recommended for?
Twingate is a suitable network access control solution for any type or size of business. Small businesses can access the free Starter plan, which accommodates five users and covers network access control. The two paid plans are sized for mid-sized businesses and large enterprises.
Pros:
- Easy Access for Users Via a Small App: VPN-style interface that most users can understand without training
- AD-Style Setup that Avoids Complicated ACL Definitions: Assign applications to the app menu for each user
- Micro-Segmentation to Protect Each Resource: Imposes access control for each resource
- Single Sign-On Mechanism to Ease User Movements: Alleviate the inconvenience of repeated login requirements
- Treats On-Premises and Cloud Applications Equally: Access goes through the Twingate server for all connections
Cons:
- Not Actually a Network Access Control Package: This is a VPN-style service for internet-based virtual networks
Twingate is a software package that you have to host yourself. It will run on Linux but if you want to run your business on the cloud, you can run Twingate on AWS or Azure. You can also containerize Twingate with Helm or Docker. The Twingate system is offered on a 14-day free trial.
EDITOR'S CHOICE
Twingate is our top pick for a network access control software package because it takes you through the strategy of network access control and on to the concepts of Zero Trust Access (ZTA). With the Twingate service, you can choose to just control access to networks but the package is able to implement access controls at a more finite level. You can take access controls right down to individual applications. This is microsegmentation, which is considered to be the future of network access control.
Download: Access Demo & 14-day FREE Trial
Official Site: https://auth.twingate.com/signup/
OS: Linux, Docker, Helm, AWS, and Azure
2. ThreatLocker Network Access Control (GET FREE DEMO)
ThreatLocker Network Access Control is part of a platform of system security tools that build a Zero Trust Access (ZTA) strategy. The NAC implements ZTA by forming part of the security policy enforcement. It is an endpoint posture management service that scans an endpoint before allowing it to connect to the network.
Key Features:
- Security Policies: Checks the security of an endpoint
- Blocks Rogue Devices: Controls are linked to a client app
- Dynamic ACLs: Interprets rules into access control entries
- Controls Access to Servers: Blocks unauthorized software
Why do we recommend it?
ThreatLocker Network Access Control is an interpreter for router access control lists (ACLs). It interprets your access policy into ACLs and inserts them into your routers. This eliminates the stress of trying to get all of your allow and deny lines in the right order – the tool has automated expertise built-in.
ThreatLocker is a cloud-based system, so it can take a God’s eye view of your network, even if the physical network has no clear boundary. This is a good solution for virtual networks. In fact, it is a key mechanism in the creation of a virtual network that can unify sites and include remote workers.
The NAC allows a device to connect to the corporate network or blocks it. The system can also impose controls on which endpoints can access which servers. One of the criteria that can be used when assessing an endpoint is its physical location. This is a great feature for businesses that need to comply with GDPR, which specifies that data can only be stored and processed within the EU.
Imagine a scenario of a business that holds user accounts in France and allows its invoicing clerks to work from home. One clerk decides to become a digital nomad, moving to Morrocco and still logging into the business to carry on with the same job from that laptop that used to be at home in Paris. Suddenly, that endpoint that was approved for access become unsuitable. The business manager doesn’t need to be notified about the move and the network manager doesn’t need to manually block that user’s account because the security policies and the NAC in ThreatLocker take care of all of the work automatically.
Who is it recommended for?
The ThreatLocker package is a very easy system to implement and it provides more than network access control. It will also block all malware and provide access controls for applications. This system compensates for any skills shortfall in your network management team and removes human error.
Pros:
- A Menu of Services: Enables the implementation of a wide range of policies
- Automated Blocking of Rogue or Unsuitable Devices: Only authorized devices allowed
- Management of Virtual Networks: Connects sites to site and remote workers into the office
- Compliance Management: For NIST, HIPAA, CIS, and PCI DSS
Cons:
- Doesn’t Include a Full Access Rights Manager: Focus on endpoint posture management
As a cloud-based system, ThreatLocker allows you to construct a corporate network that includes different sites and cloud platforms. The main focus of this system is to concentrate access rights on applications rather than physical resources. You can assess this strategy by accessing a demo of the ThreatLocker system.
3. Cisco Identity Services Engine (ISE)
With the Cisco ISE software, IT administrators can exercise controls over who, what, when, where, and how endpoints are allowed on the network. ISE uses Cisco TrustSec software-defined segmentation and other technologies to enforce security policies, including BYOD policies. ISE integrates well with other Cisco products, which makes it a natural fit for Cisco infrastructure network environments. It has been named a 2020 Gartner Peer Insights Customers’ Choice.
Key Features:
- Zero Trust Access: Network segmentation
- Adds on to Network Management: Also provides device discovery
- Zones of Trust: Enables the creation of a BYOD zone
Why do we recommend it?
Cisco Identity Service Engine applies network access control methods to cloud resources. This is a new type of service strategy called Infrastructure-as-Code (IaC) and it provides a dynamic ACL service that can adapt in response to detected threats. The service also integrates a threat detection service.
ISE checks for device policy compliance and posture using the Cisco AnyConnect agent, which also doubles as a VPN client app for desktop and laptop checks. ISE is available as a physical or virtual appliance for VMware, Red Hat, and Microsoft hypervisors. It can also be used to create ISE clusters to support the high availability and failover requirements of a critical enterprise network. Some of the features and capabilities include, but are not limited to:
- Built-in AAA services and support for multiple identity and directory services such as Active Directory, LDAP, RADIUS, RSA, OTP, etc.
- Centralized policy management and role-based access control
- Integrated BYOD, mobility, and guest lifecycle management
- Customizable mobile and desktop guest portals
- Device profiling and endpoint posture service
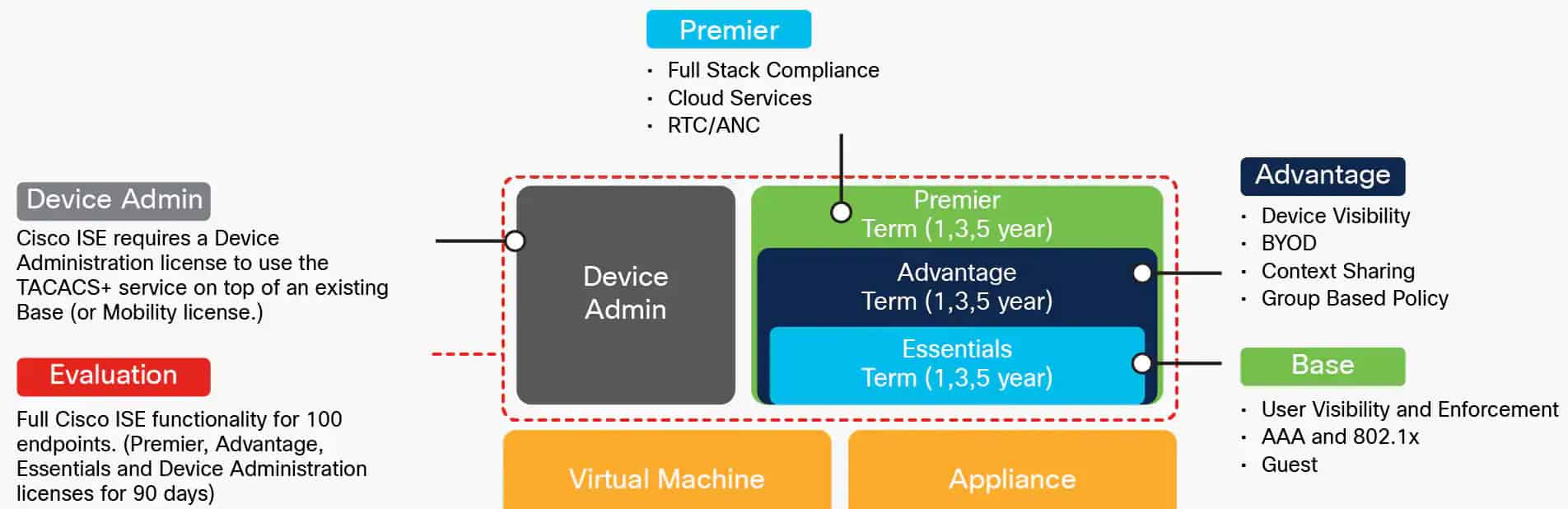
There are four primary ISE licenses available to customers as shown in Figure 2.0. These licenses as well as technical support can be purchased directly from Cisco certified partners.
Cisco ISE is a great tool, but it is best suited for organizations that have invested in Cisco hardware. If your network infrastructure is made up of equipment from different vendors, you may want to consider a NAC solution that is more suitable for your environment.
Who is it recommended for?
The presentation of this system is very technical and you would have need to have taken a network security course just to understand the website. Fortunately, the administration console makes implementing the system a lot easier than it sounds. However, this is a solution that is best suited for large companies with complicated hybrid networks.
Pros:
- Offers Compliance Monitoring: Through endpoint posture management
- Includes VPN Client for Remote Access: Create a virtual network across the internet
- Supports a Wide Range of Identity Services: Including LDAP and RADIUS
Cons:
- No Price List: You have to contact the company for a quote
With Cisco Identity Services Engine, you can actually host it on your own network – these days NACs tend to be cloud services. This is an extensive service that examines both user accounts and devices with possible combinations of those two areas of security. The service is great for managing hybrid environments, being able to handle security policies for on-site and internet-based virtual networks as well as LANs and wireless systems. ISE is a great component for Zero Trust Access (ZTA) and is comprehensive, so it will be able to form part of the security strategy of any new network configuration that comes along. You can start by registering for a demo.
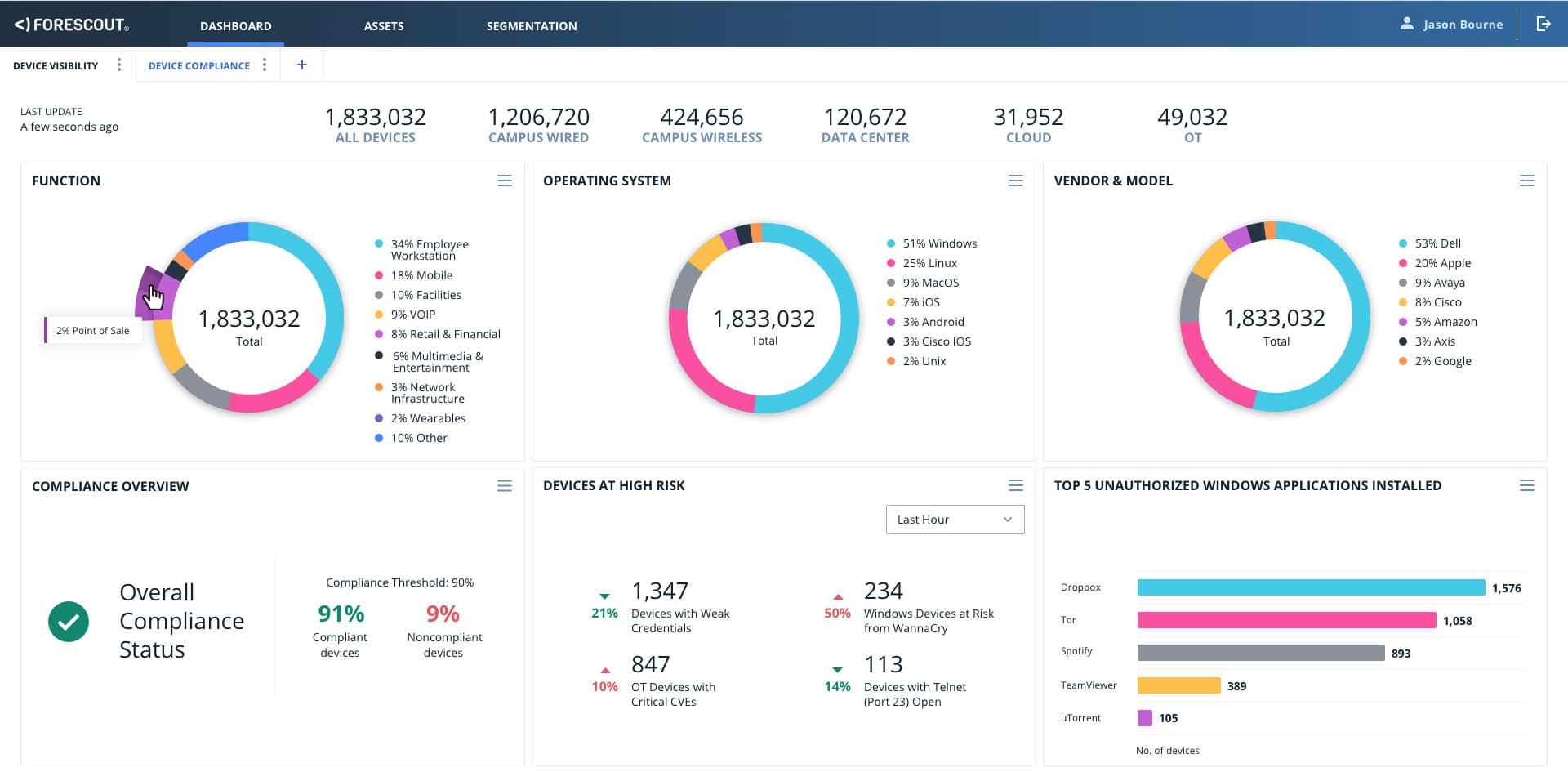
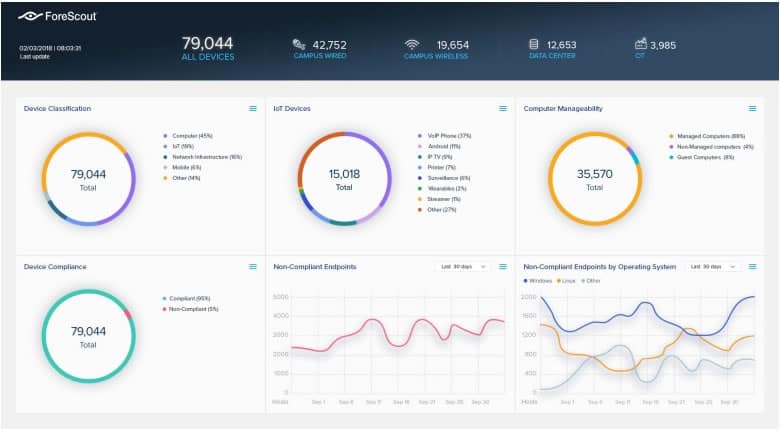
4. ForeScout Platform
ForeScout platform stands out among the rest in its space. It is a highly flexible and robust product that offers agentless detection and management of network devices ranging from IT to IoT and even operational technology (OT) devices. ForeScout NAC solution is among the 2020 Gartner Peer Insights Customers’ Choice for NAC.
Key Features:
- Cloud-Based: Integrates with network infrastructure
- Evaluates Device Suitability: Posture management
- Implements Segmentation: Enforces least privileged access
Why do we recommend it?
The Forescout Platform is an ever-expanding system that now includes an XDR as well as its access controls. This enables the system to combine its regular system access controls with threat detection and response. The platform includes several modules that include access control to apps and network resources.
As noted earlier, the ability to integrate with existing software and network infrastructure is one of the factors to consider when evaluating NAC products. ForeScout’s NAC software integrates well with most network security applications such as vulnerability assessment and SIEM tools, among others. ForeScout’s solution places emphasis on device visibility, and with its access to millions of device profiles, it can seamlessly identify a variety of them. And through its security policy engine, it is able to provide network access control, segmentation, and even automatic incident response.
ForeScout’s flagship product, ForeScout 8.2—a unified device visibility and control platform for IT and OT networks, dynamically identifies and evaluates network devices and applications as they connect to an organization’s network. It provides the basis for automating and enforcing a wide array of policy-based controls for network access, endpoint compliance, and mobile device security. ForeScout even offers advice on how its products can be used to meet regulatory compliance for PCI DSS, SOX, HIPAA, and others. It can be deployed as physical software, or virtual appliance solution. Other related NAC component applications include:
- eyeSight—provides visibility into a network by discovering, classifying, and assessing devices as they establish a connection without requiring agents.
- eyeControl—helps to enforce and automate policy-based controls, as well as respond to incidents.
- eyeSegment—provides network segmentation or logical security zones across the enterprise.
ForeScout makes its products available through a partner reseller network, which can assist with integration if required. There are three levels of support available to customers: ActiveCare Basic, ActiveCare Advanced, and ForeScout Premium Care. Each includes access to an online support portal, email support, plugins, and software updates.
Who is it recommended for?
This system is suitable for large corporations and it can cover industrial networks and IoT devices as well as office and cloud systems. The tool provides administration and security services and will also give you live performance statistics and compliance reporting. The service can also provide an event feed for third-party threat detection systems.
Pros:
- Uses Agentless Detection to Manage Assets: Scans traffic
- Dynamically Detects and Manages Access: Great for BYOD environments
- Offers Features for Meeting Compliance Standards: Suitable for PCI DSS and HIPAA
Cons:
- Not the Best Option for Smaller Networks: Requires a knowledgeable network manager to implement
ForeScout platform is a great choice for organizations that have network equipment from different vendors, as it can easily gather information, and control different products from the same pane of glass. However, ForeScout NAC is best suited for large organizations, due to its support for the most variety of devices and compliance modules.
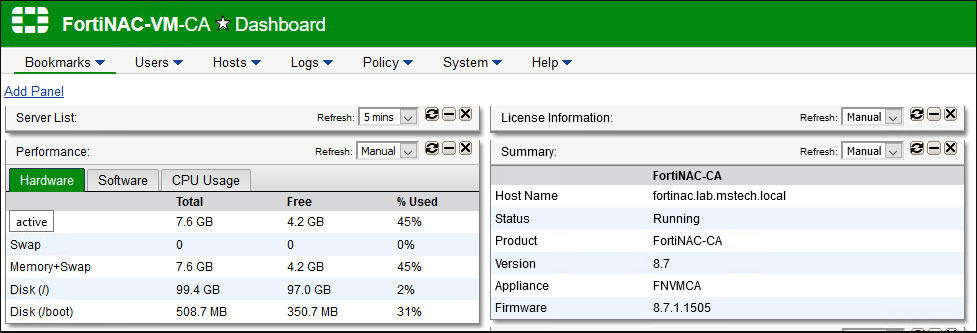
5. Fortinet FortiNAC
FortiNAC is Fortinet’s NAC solution that provides visibility, profiling, control, and real-time automated response for everything that connects to the network including IoT devices. It also delivers network segmentation using dynamic role-based access control, and policy enforcement.
Key Features:
- Physical or Virtual Appliance: Can integrate with other Fortinet products on a single appliance
- Role-Based Access Control: Provides segmentation
- Device Security Risk Assessment: Counts towards compliance
Why do we recommend it?
Fortinet FortiNAC is part of a list of products that can be slotted together to form an enterprise-wide security strategy, which Fortinet calls the security fabric. This tool can be loaded onto the FortiGate appliance, which is Fortinet’s signature product. It can also be run over a VM or on a cloud platform.
FortiNAC performs device assessment to see if it matches approved profiles such as software updates and vulnerabilities patches. The assessment can be done actively or passively and can utilize permanent agents, dissolvable agents, or no agents.
FortiNAC is a flexible and scalable solution targeted at medium and large enterprises in areas like healthcare, education, IoT, and managed service providers. It can be deployed in virtual machines (VMWare/AWS/Azure/KVM) or on hardware appliances. FortiNAC is an ‘out of band’ solution, which means that it does not sit in-line with user traffic, and therefore poses little or no impact on network performance. There are three elements to the FortiNAC solution:
- Application and Control (required): Application and Control provide the visibility and configuration capabilities, as well as automated response features.
- Management (optional): The Management portion enables the sharing of concurrent users across a multi-server deployment.
- FortiAnalyzer for Reports (optional): FortiAnalyzer provides reports and analytics based on the information gathered from the network through FortiNAC.
FortiNAC offers three licensing options based on the features and functionalities your business requires. The three options are:
- BASE license: The BASE license level is appropriate for organizations that need to secure IoT and other network devices, but do not require advanced user/network controls or automated threat response.
- PLUS license: PLUS license is appropriate for organizations that want complete endpoint visibility and control, but do not require automated threat response.
- PRO license: The PRO license is appropriate for organizations that want complete endpoint visibility, control, and automated response.
FortiNAC is a powerful NAC solution for managing network devices, especially BYOD and IoT devices. Although it supports third-party network devices, it is however best suited for network environments that are mainly based on Fortinet network equipment such as firewalls, access points, and others.
Who is it recommended for?
This is a big business solution, particularly if it is delivered in a ForitGate device as part of a suite of security solutions. The cloud implementation makes the system more affordable, but it is still a little too extensive and pricey to be suitable for small businesses.
Pros:
- Highly Focused on Automation: Improves productivity
- Supports Auditing and Risk Assessment Scans: Documents findings for compliance auditing
- Can Support IoT Environments: Also BYOD
Cons:
- Could Benefit from an Updated Interface: Looks a little clunky
6. HPE Aruba ClearPass Policy Manager
ClearPass Policy Manager from HPE Aruba is listed in the 2020 Gartner Peer Insights Customers’ Choice for NAC. The solution which was acquired by HP in 2015 enables organizations to securely admit guests, onboard and manage devices, and enforce network policies. ClearPass provides role- and device-based secure network access control for corporate, IoT, and BYOD devices across any multi-vendor wired, wireless, and VPN infrastructure.
Key Features:
- Cloud-Based: Unifies wired, wireless, and cloud access
- Guest Self-Registration: Implements secure BYOD access
- References Access Rights Managers: Integrates with your existing user accounts
Why do we recommend it?
HPE Aruba Networks ClearPass Policy Manager is the Aruba solution for Zero Trust Access (ZTA). Aruba Networks is particularly strong at providing equipment for wireless systems and the software to manage them. The ClearPass package applies security controls to those networks and it can also extend to wired networks and cloud services.
ClearPass employs self-care mechanisms such as guest self-registration portals and also leverages contextual data about user roles, devices, application use, location, and time stamp to deploy BYOD and streamline network operations across wireless, wired, and VPNs. ClearPass is available as either hardware or software virtual appliances. Key features and capabilities include:
- Comprehensive integration with third-party systems such as SIEM, IPS/IDS, and EMM/MDM.
- Supports multiple authentication/authorization sources (AD, LDAP, SQL) within one service.
- Self-service device onboarding with a built-in certificate authority (CA) for BYOD.
- Supports NAC and EMM/MDM integration for mobile device assessments.
- Role-based network access enforcement for heterogeneous networks
- Guest access with extensive customization and branding.
- Reporting of all user valid authentications and failures.
- Built-in profiling using DHCP and TCP fingerprinting.

ClearPass is composed of three different modules—OnBoard, OnGuard, and Guest. You can create separate profiles on each module.
- ClearPass Onboard provides automated provisioning of devices (Windows, iOS, Android, Linux, etc) via a self-guided portal. Network, device, and security settings are automatically configured on authorized devices.
- ClearPass OnGuard delivers endpoint posture assessments over wireless, wired, and VPN connections via flexible deployment options including agentless, dissolvable agents, and agent-based configuration.
- ClearPass Guest simplifies visitor workflow processes to enable non-technical staff such receptionists or HR staff to create temporary guest accounts for secure wireless and wired access which allows visitors to access the network for a specified period of time.
Who is it recommended for?
This tool is very strong at managing a blend of wireless and mobile devices that includes both fleet and user-owned equipment, so if you have a roaming workforce and BYOD consultants then you would benefit from this service. It is particularly good for wireless networks that need to link through to cloud services.
Pros:
- Access Features: Guest access and timed access control
- Can Support BYOD Environments: Also caters to IoT infrastructure and devices
- Includes Comprehensive Integrations: Can feed data into a SIEM system
Cons:
- No Free Trial: You can get a demo
ClearPass is fairly cost-effective especially in relation to other NAC software, but to really take advantage of it you should consider purchasing all or most of the feature sets. However, this can become very pricey for SMBs.
7. Ivanti NAC
Ivanti NAC solution enables organizations to gain visibility, understand their security posture, and enforce role-based access and endpoint security policy for network users, guests, and IoT devices. The Ivanti NAC solution enables organizations to meet numerous industry regulatory requirements from the government to healthcare to finance. It can streamline endpoint compliance and remediation, BYOD onboarding, and IoT security, as well as automated threat response.
Key Features:
- Deployment Options: Physical device, virtual appliance, or a cloud service
- Creates Zones of Trust: Important for BYOD and IoT security
- Security Assessment for Candidate Devices: Endpoint posture management
Why do we recommend it?
The Ivanti NAC, which is also called Ivanti Policy Secure is a package for securing wireless networks and roaming workers. It is a way to integrate BYOD into your hybrid network, letting user-owned devices into your system that includes VPN-protected stretches across the internet between sites and to cloud services.
Ivanti NAC can be deployed on physical, virtual, and cloud platforms, and it integrates well with a wide range of network hardware such as NGFWs, IPS, and SIEM from different manufacturers. The Ivanti NAC solution is made up of three main components:
- Profiler: This provides network visibility, endpoint identification, and classification, reporting, and behavior analytics.
- Policy Secure: This provides a unified policy engine that leverages contextual information from users, endpoints, and applications.
- Client: Pulse client offers agent and agentless options for pre- and post-admission control and endpoint’s security posture verification.
Some of the key capabilities and features of Ivanti NAC include, but are not limited to:
- Interoperability – enables easy integration with third-party network and security devices
- A wizard-based configuration that takes the complexity out of setting up a NAC solution
- A Profiler that identifies and classifies endpoint devices, including IoT
- A Host Checker that identifies the security posture of the device
- Self-service guest access support
- Centralized policy management
- RADIUS and TACACS+ support
- Automated threat response
Who is it recommended for?
This solution is built for large businesses that operate multiple sites, use cloud platforms, welcome BYOD in the office, and need to integrate roaming and remote workers into their hybrid network. The system constantly detects devices on the network and provides an onboarding mechanism for guest users.
Pros:
- Compliance Settings: Suitable for healthcare to government departments
- Security Controls: Includes endpoint verification, tracking, and behavior monitoring
- Supports a Unified Policy Management System: Ideal for enterprise access orchestration
Cons:
- No Price List: Would benefit from more transparent pricing
Ivanti NAC is delivered as a physical device or you can run the software on your own service over a VM as a virtual appliance. It will run on VMware, Hyper-V, or KVM. You can get a perpetual license or use the system on a subscription. A perpetual license includes one year of support. There are four levels of support contacts available. Assess Ivanti Policy Secure NAC with a free trial.
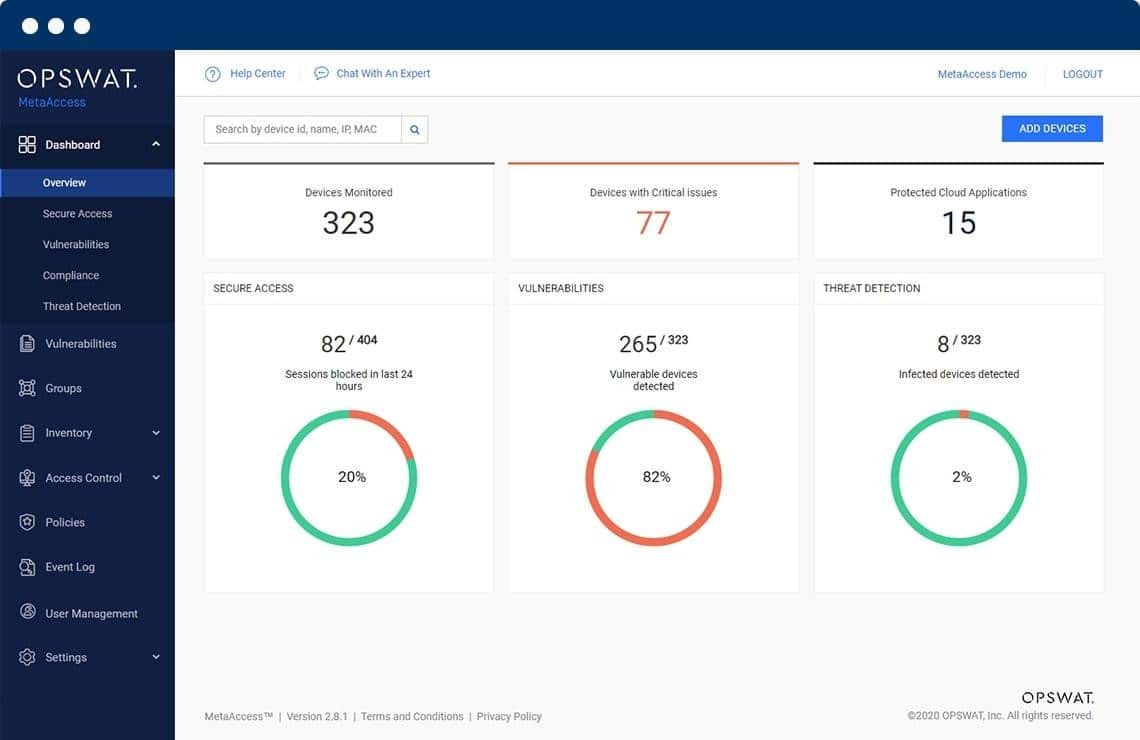
8. OPSWAT MetaAccess NAC
SafeConnect NAC solution was acquired by OPSWAT in 2019 and it is now called MetaAccess NAC. The solution ensures that every device (wired or wireless) connected to your network is visible, automatically checked that it meets prescribed security standards, and then either granted or denied access in real-time based on predefined security standards or policy requirements. MetaAccess agentless identifies, profiles, and provides access control for devices connecting to your network.
Key Features:
- Deployment Options: Physical or virtual appliance
- Compliance Reporting: For GDPR, GLBA, PCI DSS, HIPAA, and SOX
- Unified Network Management: Wired and wireless networks
Why do we recommend it?
OPSWAT MetaAccess NAC offers a method to detect all devices on a network and allow user-owned laptops, phones, and tablets, and IoT devices to connect. The system crosses security for network and application access and integrates controls for wireless networks. The system automatically scans each device for risk factors before allowing access to proceed.
MetaAccess is an “out-of-line” solution, which means that it poses little or no impact on network performance. Like most NAC solutions, it can be deployed as an on-premises physical or software virtual appliance. Each MetaAccess appliance scales up to thousands of concurrent endpoints and can be assembled into a cluster for larger environments. This makes it particularly attractive in the education sector where thousands of students onboard at the same time with all sorts of devices.
As noted earlier, one of the key factors to consider when evaluating NAC solutions is its ability to support organizations in meeting regulatory compliance. The MetaAccess NAC solution helps organizations achieve security certification and regulatory compliance including HIPAA, PCI DSS, SOX, GDPR, and ISO-27001. Some of the key features and capabilities include:
- Automatic software updates/upgrades and daily remote backups
- Application usage policies and Acceptable User Policy (AUP) enforcement
- Role-based access control and port level control
- Flexible network integration options
- Contextual Intelligence Publishing
- Guest and IoT self-registration
- Agentless device profiling
- Customization of policies
Who is it recommended for?
OPSWAT added this NAC to its existing list of security systems that include vulnerability management, patching, and threat detection, so the network access control system would be of particular interest to businesses that already use OPSWAT security products or those enterprises that want an extensive security package.
Pros:
- Automated System Management Services: Backup, updates, and health checks
- Agentless Profiling to Minimize Resource Consumption: Scans traffic from endpoints
- Deep Endpoint Assessments: For computers running Windows and macOS and also mobile devices
Cons:
- Updates Can Only be Applied by the Vendor: Not the best solution for companies wanting full control
MetaAccess licensing can be either perpetual, subscription, or modularly priced based on customer needs. It is budget-friendly, and that makes it attractive to SMBs with low budgets and heterogeneous network environments. One of the main concerns with MetaAccess is the fact that updates/upgrades on the appliances can only be performed by the vendor. This can be a turn-off for organizations that want a bit more control when applying updates to a system.
Network Access Control Software FAQs
What does a network access control do?
Network access control checks on the security attributes of devices before allowing them to connect. This task has become a great deal more complicated thanks to BYOD and virtual networks. NAC is an important requirement in modern system management because it is the first line of defense for corporate applications and data.
What is a NAC solution?
Network Access Control (NAC) isn’t a user account management system; it deals with devices instead. The NAC approach is to ensure that a device has no security weaknesses before allowing it to connect to the network. The system works with a series of policies, which are lists of requirements for each type of device. New devices are scanned to enroll them, which makes connections faster. However, security checks still occur every time that the device wants to connect to the network.
Is firewall a network access control?
Both a firewall and network access control defend a network. However, a firewall is a network device that stands at the boundary, examines traffic as it enters the network, while NAC operates within a network. Network access control examines each device and assesses its security strength before allowing it to connect.