Onion over VPN is the phrase used to describe a setup in which you use both a VPN and Tor simultaneously. Also called Tor over VPN, it offers many security and privacy advantages over using either of the two tools alone.
An Onion over VPN setup requires just three things to get set up:
- Internet access
- A VPN
- Tor Browser, or some other means of connecting to the Tor network
We’ll explain the benefits, disadvantages, topology, and alternatives to Onion over VPN below. But if you just want a quick tutorial, here’s how to set up Onion over VPN:
- Open your VPN app and connect to it. We recommend NordVPN.
- After the VPN connection is established, open Tor Browser
And that’s it. Really! You can now benefit from the combined anonymity, security, and privacy of both Tor and a VPN.
Why use onion over VPN? Pros and cons
The onion over VPN setup offers several benefits:
- Your ISP can see that you’re using a VPN, but not that you’re using Tor
- Your VPN cannot see what sites you visit or the contents of your connection
- You can access both dark web .onion sites
- You can anonymously surf the clear web
- The Tor entry node cannot see your real IP address, only that of the VPN server
- You get the flexibility to use a VPN by itself with a normal browser for non-critical tasks
But, there are also some drawbacks:
- Websites and apps can see that you’re visiting through a Tor exit node. Some sites might block you or not function well as a result.
- Your VPN can see your real IP address and knows you’re using Tor
- You could potentially expose data to compromised Tor exit nodes
- Using a VPN and Tor together will significantly slow down your connection
How does the Onion network work – in simple terms?
The Onion network, or more commonly known as Tor, is like a secret passageway for data, designed to keep your online activities private. It started it’s development in the mid-1990s by the United States Naval Research Laboratory. This was to protect American intelligence communications online. It works like this: your data is a letter, and Tor wraps it up in multiple layers of encryption, just like an onion. This onion is then sent on a random, winding journey through several nodes or relay points.
At each stop along the way, one layer of encryption is peeled off to reveal the next destination, but each node only knows where the onion came from and its next stop, not the whole route. This means no one can trace the data from start to finish.
However, it’s not foolproof. While Tor makes it hard for anyone to see where your data is going, the final recipient can still see it came from you unless you take extra steps to hide your online identity, like your IP address. Plus, if someone controls both the entry and exit nodes, they could potentially spy on your data.
So, while Tor isn’t a silver bullet for online privacy, it’s a very useful tool to make it harder for prying eyes to follow your digital footprints.
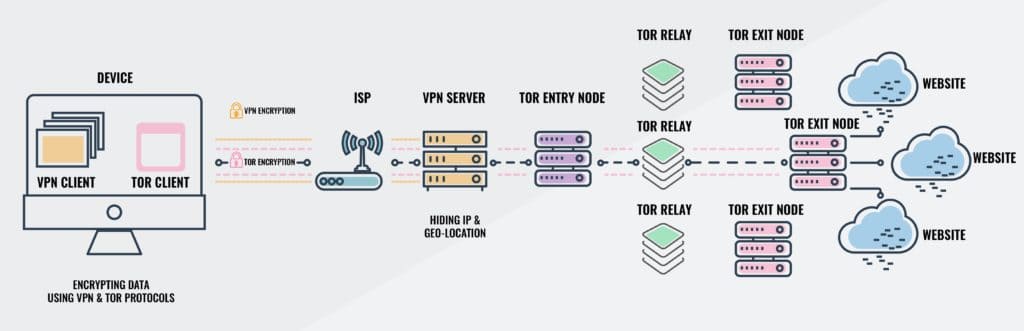
Onion over VPN encryption and traffic flow
When using Tor over VPN, your outbound internet data flow looks like this:
- Data is encrypted by the VPN
- Data is encrypted again by Tor
- Data is sent to the VPN server
- The VPN decrypts the data, but it is still encrypted by Tor
- Data is sent through the Tor network
What happens next depends on whether you’re accessing the dark web or clear web. If you’re visiting a .onion site on the dark web, your data is decrypted upon arriving at its destination. If you’re visiting the clear web, data is decrypted at a Tor exit node and forwarded to the website.
Read more: Step by step guide to safely accessing the dark web
For inbound traffic, the flow is as follows:
- Data is sent from a website, app, or service
- Tor encrypts the data
- The data is sent through the Tor network to the VPN server
- The VPN encrypts the data again
- The twice-encrypted data is sent from the VPN server to the end user device
- Tor decrypts the data
- The VPN decrypts the data again
VPNs with built-in onion over VPN support
A few VPNs come with built-in support for onion over VPN, which means you don’t need Tor browser to get it set up. Just connect to a Tor over VPN server and you’ll be good to go.
Some VPNs that offer onion over VPN servers include:
Note, however, that such a feature has its pros and cons.
On the plus side, you can now use any application with Tor, not just Tor browser. Configuring individual applications to use Tor can be a pain, so having it built into the VPN is definitely convenient.
On the downside, the VPN provider could hypothetically analyze your traffic before it’s encrypted by the Tor network. Be sure to choose one with a no-logs policy. You also don’t get the other benefits of using Tor browser, like script and tracker blocking. If you opt to use your normal browser, websites could still identify you through stored cookies and other identifiers.
Onion over VPN vs VPN over onion
An alternative to onion over VPN is VPN over onion. It switches up the flow order, swapping Tor and the VPN. Although it might seem similar at first glance, it usually serves a very different purpose and comes with different pros and cons. Setting up VPN over onion is more difficult and beyond the scope of this article, but we’ll contrast it with onion over VPN:
- Your ISP can see you’re using Tor, but not the VPN
- You can only visit clear web sites, not dark web .onion sites
- Your VPN can see your data and what sites you visit
- You can access websites and apps that normally block connections from Tor exit nodes
- Less vulnerable to compromised exit nodes
- No packet discrimination by Tor exit nodes
- Requires VPN provider’s assistance to set up
- Tor entry nodes see your real IP address
Generally speaking, onion over VPN is much easier to set up and offers more utility than VPN over Tor, but both have their place.
Is Onion over VPN safe and secure?
While generally safe, there are risks. The Tor network is run by volunteers, so bad guys could run some nodes. Also, your Tor activities could be exposed if your VPN connection drops. So, it’s best to use a VPN with a kill switch feature that blocks internet access if the VPN connection fails. Remember, Onion Over VPN isn’t for everyone. Consider your needs and the potential risks before using it.
See also: How to block ISP tracking