PCI DSS gets its name from the institution that created it; the Payment Card Industry Association. The organization has a division, called the Payment Card Industry Security Standards Council, which commissions and sponsors standards to help protect the finance industry and its customers. The “DSS” part of the standard’s name stands for Data Security Standards.
PCI DSS is not enforced by law. However, it is a requirement of Visa, Mastercard, American Express, Discover, and JCB, so if you don’t comply, you won’t be able to process card payments from the customers of those systems.
The protection of the personal information of customers is a strong legal requirement of the General Data Protection Regulation (GDPR), which is applied in the whole of the European Union (EU).
Here is our list of the best PCI DSS compliance tools:
- Access Rights Management
- ManageEngine ADAudit Plus EDITOR’S CHOICE This package provides user behavior analytics linked to Active Directory. It, therefore, protects AD as its foundational resource and will produce user management reports for PCI DSS compliance. Runs on Windows Server, AWS, and Azure. Get a 30-day free trial.
- SolarWinds Access Rights Manager (FREE TRIAL) Monitors Active directory implementations including Exchange Server and SharePoint permissions. Runs on Windows Server.
- Software Patch Management
- SolarWinds Patch Manager (FREE TRIAL) Keeps software up to date in order to close of exploits. Runs on Windows Server and is PCI DSS compliant.
- Security Information and Event Management Tools
- SolarWinds Security Event Manager (FREE TRIAL) Monitors log access and passing data to detect unauthorized data access attempts.
- ManageEngine EventLog Analyzer (FREE TRIAL) Syslog manager that includes pre-written PCI DSS compliance audits and reports, plus HIPAA and FISMA auditing.
- Intrusion Prevention Systems
- OSSEC A highly respected log analysis tool that is open-source and free to use. It lacks a user interface.
- Splunk Enterprise A live traffic analyzer that runs on Windows or Linux. Available in free and paid versions.
- Anti-Malware Systems
- Malwarebytes Endpoint Protection and Response An anti-malware system that has PCI DSS Requirement 5 certification. Runs on Windows.
- Trend Micro Security for Mac Provides certified PCI DSS Requirement 5 compliance and runs on Mac OS.
- Cardholder Data Environment Protection
- ManageEngine Endpoint DLP Plus (FREE TRIAL) This package of data loss prevention tools includes a discovery and categorization system for sensitive data and applies controls over data access and movement. Runs on Windows Server.
- SENF A free sensitive data locator that runs on Windows, Linux, Mac OS, and Unix.
- PowerGREP A sensitive data locator with a 3-month money-back guarantee.
- Wireless Security Monitoring
- OpenWIPS-NG An intrusion prevention system for wireless networks. This utility is free to use and install on Linux.
- Aruba RFProtect A wireless intrusion prevention system that complies with PCI DSS specifications.
- Password Protection Lockers
- KeePass Password Safe A free password protection system for Windows, Linux, Mac OS, Linux, and memory sticks.
- Password Gorilla A widely-used password protector for Windows, Linux, Mac OS, and Unix.
- Network Monitoring Systems
- SolarWinds Network Performance Monitor (FREE TRIAL) The leading network performance monitor with SNMP-based routines that runs on Windows Server.
- Paessler PRTG Network Performance Monitor An all-in-one monitor that covers networks, servers, and applications. Runs on Windows Server.
- Configuration Management
- ManageEngine Network Configuration Manager This tool protects switches, routers, and firewalls against unauthorized configuration changes.
- SolarWinds Network Configuration Manager (FREE TRIAL) A configuration manager that is compliant with PCI DSS and integrates with other SolarWinds infrastructure management tools.
Introducing data protection measures is a wise idea. It will protect your business’s sensitive information as well as ensuring that you don’t get sued by customers or employees for data disclosure.
There are many categories of security tools that you will need in order to enforce security on your system in order to protect customer data and card transaction information. These are:
- Access rights management
- Security information and event management tools
- Intrusion prevention systems
- Anti-malware systems
- Cardholder Data Environment protection
- Wireless security monitoring
- Password protection lockers
- Network monitoring systems
- Software patch management
- Configuration management
We will explain each of these types of software and propose the two best tools in each category.
Access rights management
You need to control who has access to cardholder data. In cases where operators need to see transaction and customer information, for refunds and customer inquiries, for example, you need to limit the categories of data that can be accessed.
The usernames and passwords of authorized users are the targets of a type of hacker attack, called “phishing”. This hacking method tricks staff into disclosing their login accounts. If you also allow external access to your network, such mistakes over the confidentiality of user credentials can threaten the security of your data.
Access rights management software will help you keep track of the activities of the company’s authorized users and make sure that they don’t engage in unauthorized activities. User activity tracking is a requirement of PCI DSS. You need to keep logs of each user session to present for any PCI DSS audit.
Our methodology for selecting a PCI DSS compliance tool
We reviewed the market for services that enable you to comply with PCI DSS requirements and analyzed options based on the following criteria:
- Logging of all actions
- Storage of logs in a meaningful directory structure and in collections that are cohesive and clearly labeled
- Facilities to identify the user account involved in each action
- Encryption to protect data in transit and at rest
- File access controls for sensitive data
- A free trial or a demo package that enables a risk-free assessment
- Value for money from a comprehensive security tool that doesn’t cost the earth
With these selection criteria in mind, we identified a list of system management and monitoring tools that will protect bank account data and enforce compliance with PCI DSS.
The two best access rights management systems that you should look into are:
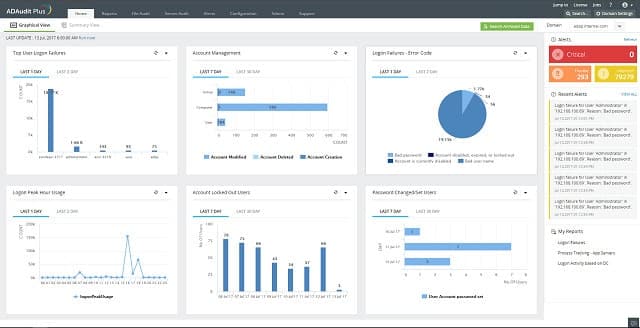
1. ManageEngine ADAudit Plus (FREE TRIAL)
Tested on: Windows Server
ManageEngine ADAudit Plus is very good for implementing PCI DSS compliance and running audit reports to automatically prove your worthiness. This tool focuses on Active Directory, monitoring, and logging any changes to permissions recorded in AD. It will log user actions entering and exiting different systems. It tracks changes to audit file and folder permissions, which will alert you to intruder activity. You can archive alert data for up to three years and generate audit reports.
Key Features:
- Active Directory Tracking: Monitors changes and logs activities within Active Directory for security.
- Compliance Reporting: Generates detailed compliance reports for various standards including PCI DSS and HIPAA.
- Multi-Domain Support: Capable of handling multiple domains, making it suitable for large enterprises and multi-tenant environments.
- Visual Permissions Analysis: Provides a graphical overview of share permissions and security group details.
Why do we recommend it?
ManageEngine ADAudit Plus is a user activity tracker that relies on Active Directory as a source of information on user accounts. You would use this system to look for evidence of insider threats or account takeovers. The package also locks down AD objects, tracking changes and reversing those that were unauthorized.
Who is it recommended for?
This package is particularly useful for companies that need to comply with PCI DSS, SOX, HIPAA, and GDPR. The package isn’t limited to working with on-premises Active Directory for general system access. It will also operate its security scanning for Azure AD, Google Workspace, and Microsoft 365.
Pros:
- Extensive Reporting: Offers thorough reporting capabilities for compliance across major standards.
- Enterprise Ready: Supports multiple domains and provides delegation features for NOC or helpdesk teams.
- Security Insights: Delivers clear visual insights into share permissions and security groups for better access control.
Cons:
- Complex Interface: Features a steep learning curve compared to similar tools, requiring more time to become proficient.
This software runs on Windows and is available in both free and paid editions. You can get a 30-day free trial of the Professional edition.
EDITOR'S CHOICE
ManageEngine ADAudit Plus is our top pick for a PCI DSS compliance tool because it provides user account protection and user activity tracking to combat insider threats and account takeover. You can’t have a secure system without secure user accounts, so this is an essential service for any data protection measure, not just for PCI DSS compliance. The package implements user behavior analytics and raises an alert if user activity suddenly changes from its normal pattern. This package verifies and secures user accounts in Active Directory and can also operate with Azure AD.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/products/active-directory-audit/download.html
OS: Windows Server, AWS, and Azure
2. SolarWinds Access Rights Manager (FREE TRIAL)
Tested on: Windows Server
The SolarWinds Access Rights Manager contributes to PCI DSS compliance. The tool monitors Active Directory, Exchange Server, SharePoint, and file servers. It produces logs that detail the user, the system accessed, and the times of access. The dashboard links to user information to show you not just the username, but also the real name of the account holder.
Key Features:
- Active Directory Management: Simplifies user account and permissions management across multiple domains.
- Compliance Reporting: Automates the generation of compliance reports for standards like PCI DSS, HIPAA, and GDPR.
- Visualization of Permissions: Offers a graphical representation of file and folder permissions for easy understanding.
- Self-Service Portal: Includes a portal for users to manage their accounts and passwords independently.
Why do we recommend it?
SolarWinds Access Rights Manager provides a new interface for Active Directory that makes the management of user accounts and device permissions easier and also implements coordination between domains. The tool removes the need to access AD screens directly. It helps you tighten access controls and track user activity.
SolarWinds Access Rights Manager is a reliable PCI DSS compliance tool because properly managed user authentication and access rights are the bedrock of data security. This package runs on your own site and assesses all of the entries in your AD global catalog. It will ensure that user groups and their permissions are well defined and that abandoned accounts have been removed. With this tool, you can enforce a strong and effective password policy and reduce the threat of hacker attacks. Being able to track user activity is fundamental to PCI DSS and control of access to sensitive data can’t be enforced without proper user account management.
Who is it recommended for?
This package is an on-premises system but it can also manage Azure AD. It is particularly necessary for those companies that follow the PCI DSS, HIPAA, and GDPR data protection standards because it can enforce those rules and automatically generate compliance reporting. This software needs to be hosted on Windows Server.
Pros:
- Enhanced Visibility: Offers in-depth insights into permissions and file structures with automatic mapping and visualization.
- Compliance Simplified: Preconfigured reports facilitate easy compliance demonstration, highlighting and remedying compliance issues.
- Customizable Control: Allows sysadmins to tailor access rights and permissions across Windows and other applications.
Cons:
- Learning Curve: Its comprehensive features demand a significant time investment to master fully.
The ARM integrates user management function as well, including a self-service portal that enables users to check on their accounts and perform simple admin tasks, such as changing their passwords. This tool gives you the ability to oversee a large number of users from one dashboard. It is a paid tool that runs on Windows Server and you can get it on a 30-day free trial.
Software patch management
The failure to keep application software up-to-date creates a security weakness. Many updates to software are only produced when a new vulnerability in existing systems is discovered. The software houses that provide these programs quickly write updates to close off the exploit. It is very difficult to keep all software up-to-date so automated tools for patch management help to keep a network secure and compliant with PCI DSS Requirement 6. Here are two patch managers that we recommend.
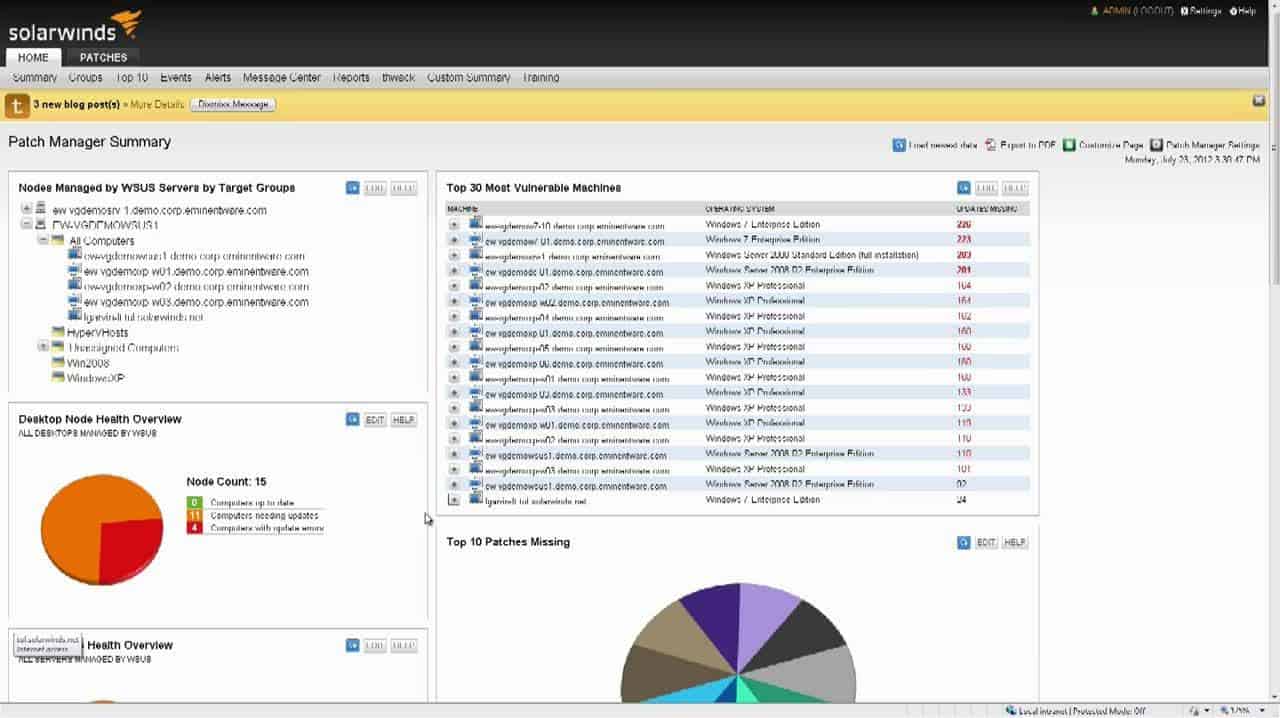
3. SolarWinds Patch Manager (FREE TRIAL)
The SolarWinds Patch Manager runs on Windows Server and integrates Microsoft WSUS patch management and SCCM. This is a vulnerability management system that logs all software running on your site and stays alert for any updates available for those packages. The dashboard lists available patches and will roll them out automatically upon approval. The system also produces audit reports to help show compliance with PCI DSS.
Key Features:
- Microsoft Integration: Enhances Microsoft WSUS and SCCM patch management with additional third-party patching capabilities.
- Compliance Audits: Generates audit reports showcasing compliance with PCI DSS requirements through up-to-date patching.
- Simplified Dashboard: Offers an easy-to-navigate dashboard for tracking patches and their deployment across networks.
- Third-Party Patching: Supports a broad range of third-party patches, integrating them seamlessly into the patch management process.
Why do we recommend it?
SolarWinds Patch Manager extends the native Microsoft WSUS and SCCM systems so that it includes patches from third-party systems. This helps you to unify your software asset management work in one tool. The package also provides patch status reporting for compliance documentation.
Who is it recommended for?
Patch management is a requirement of all data protection standards because it blocks newly-discovered exploits in software. Out-of-date operating systems and software provide a major opportunity for hackers to gain access and for global campaigns of malware, such as ransomware to spread. This package runs on Windows Server and will only patch Windows devices.
Pros:
- Unified Management: Simplifies software asset management by integrating patching for Microsoft and third-party applications.
- Compliance Assistance: Facilitates compliance with data protection standards by ensuring timely application of patches.
- Efficient Patching: Streamlines patch deployment across large networks, enhancing security and compliance.
Cons:
- Enterprise Focus: Primarily designed for larger networks, which may not suit smaller setups or personal use.
SolarWinds Patch Manager is available for download on a 30-day free trial.
Security information and event management tools
Security Information and Event Management (SIEM) offers two tracking methods that enable you to track activity on your system. These are the monitoring of log files and the examination of the activity that passes along your network.
The protection of log files is particularly important for PCI DSS compliance. You need to be able to demonstrate full tracking of all data access events. These should be recorded in log files, but hackers who want to destroy or steal your data know that, and they either delete or alter those files. SIEM tools back up log files, check for changes, and restore the original versions. They also enable you to search through all event logs for pertinent records because the number of event records that any system produces can be overwhelming. SIEM software also tracks network traffic looking for suspicious activities.
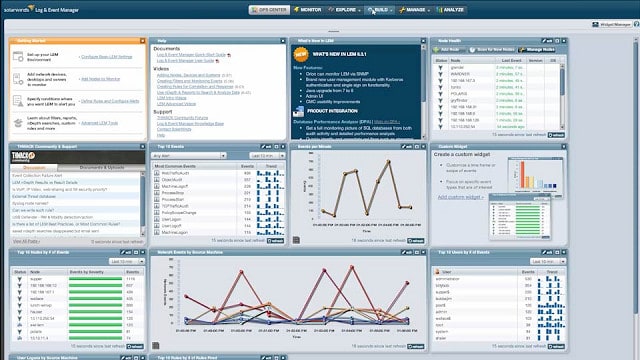
4. SolarWinds Security Event Manager (FREE TRIAL)
The SolarWinds Security Event Manager secures log files, raising alerts when tampering is detected. You can watch log messages live in the dashboard and read data from files to an analyzer. The tool ships with pre-written reports that prove PCI DSS compliance.
Key Features:
- Log Security: Protects log files from tampering and allows for real-time monitoring and analysis.
- Automated Responses: Capable of executing automated actions in response to detected security threats.
- Compliance Reporting: Generates pre-written reports to assist with PCI DSS compliance documentation.
- Cross-Platform Compatibility: Supports log collection from any operating system, enhancing flexibility.
Why do we recommend it?
SolarWinds Security Event Manager is a log manager and a SIEM tool. Log collection and storage is a requirement of most data security standards, including PCI DSS. So having some form of log management tool is essential for compliance management. The package also produces documentation for compliance reporting.
The Security Event Manager runs on Windows Server but can collect log messages from any operating system and is also able to manage log file storage on a memory stick. It is also capable of automating responses to a detected intrusion. These measures include the ability to suspend or block access to specific addresses, shut down programs and processes, disable user accounts, and block USB storage devices.
Who is it recommended for?
This system is most suitable for large organizations, and its log management and security tracking services offer value for money. The tool can also be set up to implement automated responses, which saves time and blocks threats when technicians are too busy to pay attention to alerts.
Pros:
- Broad Integration: Supports a wide array of integrations, catering to enterprise needs effectively.
- Proactive Protection: Identifies and mitigates unauthorized access swiftly, safeguarding sensitive information.
- Template Efficiency: Provides templates for quick setup, minimizing the need for extensive customization.
- Anomaly Detection: Features historical analysis tools for spotting unusual behavior, streamlining sysadmin tasks.
Cons:
- Learning Investment: Demands significant time to master due to its advanced features and capabilities.
The Security Event Manager is a paid tool that is suitable for large networks. You can check it out on a 30-day free trial.
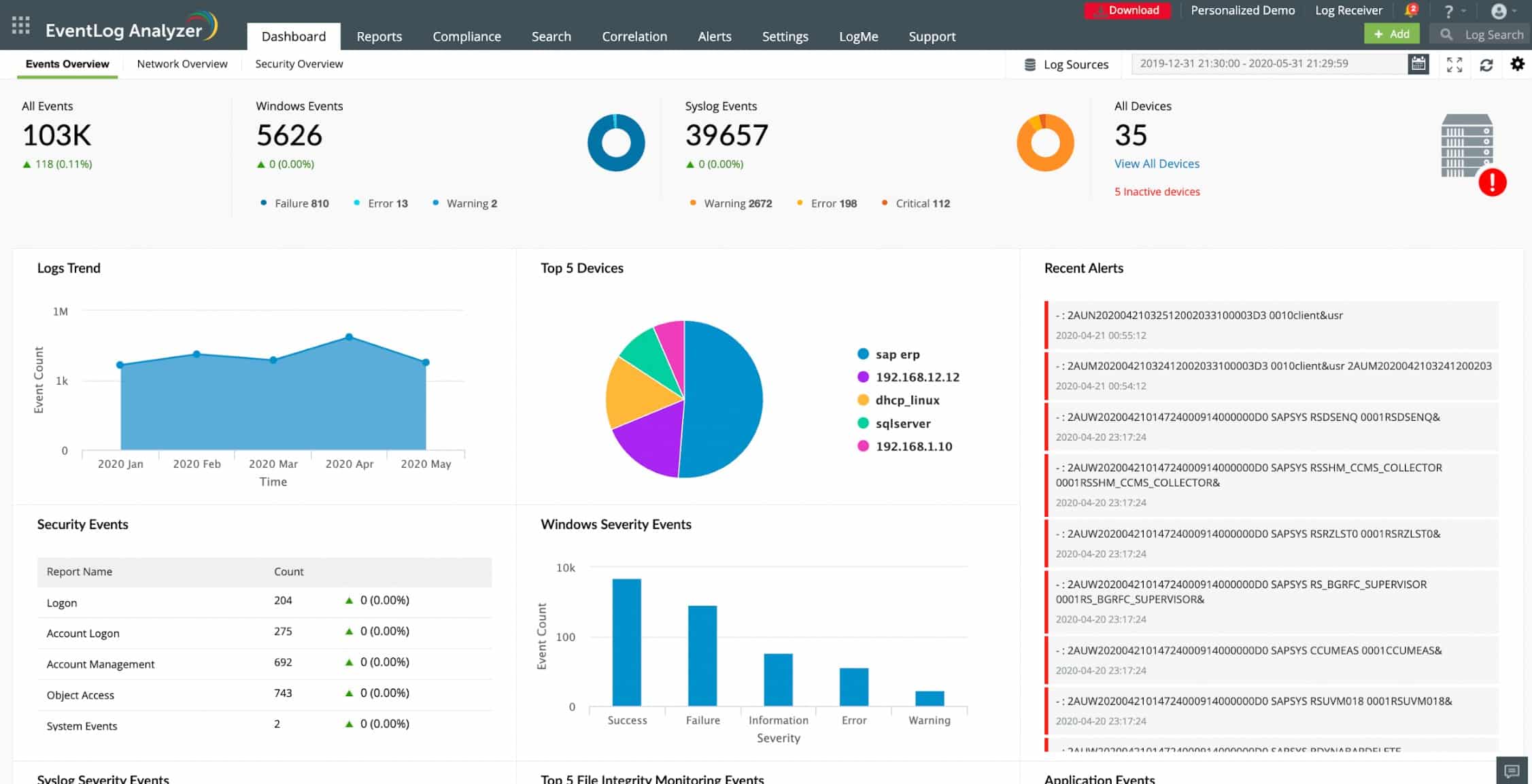
5. ManageEngine EventLog Analyzer (FREE TRIAL)
The ManageEngine EventLog Analyzer tracks Syslog messages and looks for anomalous activity on networks by employing SNMP procedures. The data viewer is able to operate on both live data and filed messages with data operations, such as sorting, search, filtering, and grouping utilities.
Key Features:
- Syslog and SNMP Monitoring: Tracks and analyses Syslog messages and SNMP data for network anomalies.
- Compliance Support: Facilitates compliance with PCI DSS, HIPAA, FISMA, GDPR, and SOX through dedicated auditing and reporting.
- Data Security: Implements log file encryption and compression, along with checksum monitoring for integrity.
- Versatile Dashboard: Offers customizable dashboards for effective network operation management.
Why do we recommend it?
ManageEngine EventLog Analyzer is a rival to the SolarWinds Security Event Manager. This package provides both log management and a SIEM system, both of which are necessary for compliance with PCI DSS. This system is also suitable for businesses that need to comply with HIPAA, FISMA, GDPR, and SOX.
The tool protects log files with compression and encryption, imposing authentication on access to the contents. It also monitors the checksums on log files, generating alerts when they change. The EventLog Analyzer includes compliance auditing for the PCI DSS. It also has processes and reports that will assist your compliance with FISMA and HIPAA standards.
Who is it recommended for?
This package is suitable for businesses of all sizes. ManageEngine offers a Free edition for use by small businesses. That version is the same as the Premium edition, but it is limited to collecting logs from five sources, which will probably be too few for most enterprises. The Premium edition is reasonably priced.
Pros:
- Adaptive Dashboards: Customizable interfaces enhance the operational efficiency of network centers.
- Anomaly Detection: Utilizes anomaly detection to aid technicians in identifying and addressing issues promptly.
- Early Warning System: Features file integrity monitoring, serving as an alert mechanism for potential security threats.
- Compliance Assurance: Supports forensic log audit capabilities, enabling compliance with regulatory standards through detailed reports.
Cons:
- Exploration Time: Navigating through the extensive features of the platform requires a considerable time commitment.
The software runs on Windows or Linux and you can get it on a 30-day free trial.
Intrusion prevention systems
Intrusion prevention systems are very similar to SIEM systems. They record standard traffic patterns on a network and then look out for variations to that baseline. They also examine the behavior of passing packets and look for identifiers in the packet headers for warning signs. The key characteristic of an IPS system is that it not only detects intrusion but takes automated steps to shut down that activity. As explained above, OSSEC has intrusion prevention capabilities. Here are two other IPS tools that we recommend:
6. OSSEC
OSSEC is a free host-based intrusion detection system that features log file analysis and live log message processing. This tool has a great analytical engine, but a terrible front-end. However, there are many free data viewing tools that are compatible with OSSEC, such as Graylog, Splunk, and Kibana.
Key Features:
- Cross-Platform Operation: Compatible with multiple operating systems, ensuring broad usability.
- SIEM and HIDS Capabilities: Doubles as a SIEM and Host-based Intrusion Detection System (HIDS) for comprehensive security.
- Customizable Interface: Offers a flexible and visually appealing interface that can be tailored to specific needs.
- Community Templates: Provides community-developed templates for quick deployment and configuration.
Why do we recommend it?
OSSEC is a free, open-source host-based intrusion detection system, which can be turned into a full SIEM if you channel network activity records into it. This service operates on log messages and looks for signs of malicious events, which includes malware activity. There are now several versions of the tool available.
This system is owned by Trend Micro, which is a prominent cybersecurity firm. The software installs on Windows, Linux, Unix, and Mac OS. It is able to collect log messages from the network that originate from any operating system, no matter which of them it is installed on.
The tool archives log files whenever they are changed, making it possible to rollback if they are interfered with. It uses a rule base to detect anomalous behavior on the network. The log monitoring functions of OSSEC fulfill the requirements of PCI DSS Requirement 10 and the file integrity enforcement features of the tool comply with PCI DSS sections 10.5.5 and 11.5.
Who is it recommended for?
OSSEC is managed by Atomicorp, which produces its own paid version. The company has created a hosted free improvement of OSSEC, which is called OSSEC+. As it is easier to use and is based on the efficient ELK stack, most new users will probably opt for that version.
Pros:
- Versatile Use: Functions across a diverse range of operating systems, from Linux to Mac.
- Dual Functionality: Serves both as a SIEM system and HIDS, offering extensive security coverage.
- Visual Customization: Allows for easy customization and a highly visual interface for better usability.
- Quick Start: Community templates enable administrators to quickly implement and utilize the system.
Cons:
- Analytical Tools Required: Needs additional tools like Graylog or Kibana for comprehensive analysis.
- Lacks Direct Support: The open-source version does not offer official paid support, potentially limiting assistance.
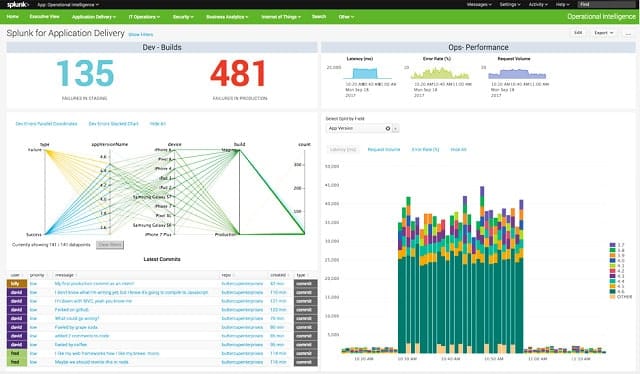
7. Splunk Enterprise
Splunk is a network traffic analyzer in free and paid versions. The higher versions, Splunk Enterprise, and Splunk Cloud include IPS capabilities. The lower editions are Splunk Free and Splunk Light. The detection procedures of the tool include network traffic monitoring and log file analysis. The detection method searches for anomalies, which are patterns of unexpected behavior.
Key Features:
- Anomaly Detection: Utilizes AI for advanced anomaly detection in network traffic and logs.
- Compliance Assistance: Includes features and reports for PCI DSS compliance, enhanced with the Enterprise Security add-on.
- Flexible Deployment: Available in both cloud and on-premises versions to suit various business needs.
- Integration Capabilities: Offers extensive integration options, including with Symantec for improved security posture.
Why do we recommend it?
Splunk Enterprise Security is a platform of security tools, which includes a SIEM. These systems are all important for businesses that need to comply with standards such as PCI DSS. The package also provides log management, which is another important requirement of PCI DSS. Offered in cloud and on-premises versions.
To get AI-based anomaly detection and strong automated prevention systems with Splunk, you need to supplement it with the Splunk Enterprise Security add-on, which is available on a seven-day free trial. Symantec chose to do a deal with Splunk in order to integrate Splunk Enterprise into its security products and gain PCI DSS compliance capabilities.
Who is it recommended for?
Splunk offers two pricing models, which work on the count of applications you want to monitor or on the amount of data that you put through the SIEM. The throughput pricing model, called Ingest Pricing, would appeal to small businesses. The platform is also appealing to very large organizations.
Pros:
- Advanced Threat Detection: Employs behavior analysis for uncovering hidden threats beyond conventional log monitoring.
- Intuitive Interface: Features a highly visual and customizable user interface, simplifying event management and analysis.
- Compliance Focus: Designed to help large organizations meet and stay ahead of compliance regulations effectively.
- Broad Compatibility: Supports both Linux and Windows platforms, offering flexibility for diverse IT environments.
Cons:
- Opaque Pricing: Requires potential users to contact for pricing, lacking transparency.
- Enterprise-Oriented: Best suited for larger organizations, possibly out of reach for smaller businesses.
- Learning Curve: Presents a steep learning curve, which may challenge new users.
Splunk Enterprise installs on Windows or Linux. You can get it on a 60-day free trial. If you prefer the Cloud edition, you can access that on a 15-day free trial.
Anti-malware systems
Malware threats to customer information and card transaction data held on your system focus on damaging or deleting data as much as stealing it. Spyware and Remote Access Trojans (RAT) help hackers to steal your data, while ransomware and destructive malware will delete or scramble your data to render it unusable. The installation of anti-malware on your system is Requirement 5 of PCI DSS.
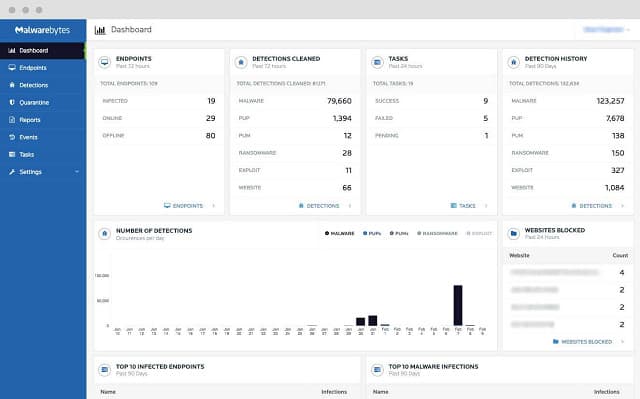
8. Malwarebytes Endpoint Protection and Response
Malwarebytes has been validated as providing PCI DSS Requirement 5 protection for data. The company doesn’t classify its product, Malwarebytes Endpoint Protection, as an antivirus system. Instead, it calls it an “antivirus replacement”. The system runs on Windows and operates in a very similar way to a network IPS, except its domain is a workstation. Rather than relying on a threat database like a traditional AV, the software searches for anomaly signatures in processes running on the computer. It then implements automated remediation procedures to remove the threat.
Key Features:
- Anomaly-Based Detection: Identifies threats by analyzing unusual behavior, offering a modern approach to endpoint security.
- Automated Remediation: Executes automatic actions to mitigate detected threats, ensuring quick response to incidents.
- Ransomware Protection: Includes capabilities to backup and restore files to defend against ransomware attacks.
Why do we recommend it?
Malwarebytes Endpoint Protection and Response scans devices running Windows and macOS for threats. The package operates an anomaly detection strategy that looks for unusual behavior rather than trying to identify malware by file signatures. The strategy also catches insider threats and intrusion. This system is validated as PCI DSS compliant.
The software is capable of detecting irregular activity performed by authorized users – a sign of stolen credentials. It protects against ransomware by saving backups of changed files so all can be restored if they are maliciously encrypted.
Who is it recommended for?
All companies need to protect their endpoints against malware and this is a candidate for that task. An advantage of the Malwarebytes system is that it also spots damaging human activity. The package is charged on a subscription per device per month for at least 10 devices.
Pros:
- Efficient Protection: Delivers comprehensive endpoint security with minimal impact on system performance.
- Broad Threat Coverage: Capable of detecting a wide range of threats, from adware to more serious malware.
- Compliance Support: Provides features that support PCI DSS compliance requirements, enhancing regulatory adherence.
Cons:
- Limited Local Control: Some users may desire more autonomy in adjusting settings on individual machines.
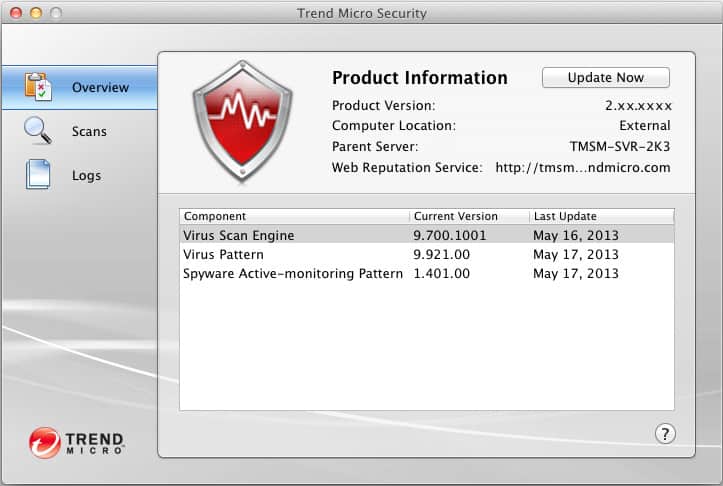
9. Trend Micro Security for Mac
Trend Micro is the company that owns OSSEC. It classifies Security for Mac as a product for home users. However, the system is fully compliant for PCI DSS Requirement 5, so it is also a good choice for businesses.
Key Features:
- AI-Based Detection: Employs artificial intelligence to detect new and emerging threats on Mac devices.
- Comprehensive Security: Offers a full suite of protections including web, camera, microphone, and email security.
- User-Friendly: Designed with a focus on ease of use, suitable for non-technical users.
Why do we recommend it?
Trend Micro Security for Mac is an alternative to the Malwarebytes system for small businesses that only use Macs and Macbooks. This package is designated by Trend Micro as a service for home use, and the company provides unified endpoint management (UEM) and XDR products for business use. This is an on-device system.
As well as blocking viruses, it protects your browser from a range of internet attacks and prevents intruder software from getting control of your Mac’s camera and microphone. The detection system is AI-based, which means it is able to block new viruses. It also includes email protection and password management.
Who is it recommended for?
This system is suitable for home offices and small businesses. Each device needs to have the software installed on it and that scenario isn’t feasible in a big business environment. The package includes protection against infected websites and will block botnet C&C communications as well.
Pros:
- Mac-Specific Compliance: Ensures PCI DSS compliance with a solution tailored for Mac OS environments.
- Simplified Operation: Provides an intuitive interface that’s easy to navigate for users of all skill levels.
- Integrated Ransomware Defense: Comes with built-in features to protect against ransomware attacks.
Cons:
- Bypassable Site Blocking: The system’s website blocking feature can be circumvented, reducing its effectiveness in certain scenarios.
As the name suggests, this software runs on Macs. However, a higher security product, called Maximum Security is available for Windows, Mac OS, iOS, and Android. This package can be bought with a 10-device license.
Cardholder Data Environment protection
Requirement 1 of PCI DSS expects you to define your Cardholder Data Environment. This means all of the equipment and processes that deal with cardholder data and the IT elements that support that infrastructure. You are expected to draw a Cardholder Data Environment Diagram of this system.
One tip for tracking down all of these details is to start with the location where cardholder data is stored and then track all of the software that put it there. You then need to look at the services and hardware that supported the process that put the data there. Here are two tools that you could use to trace cardholder data.
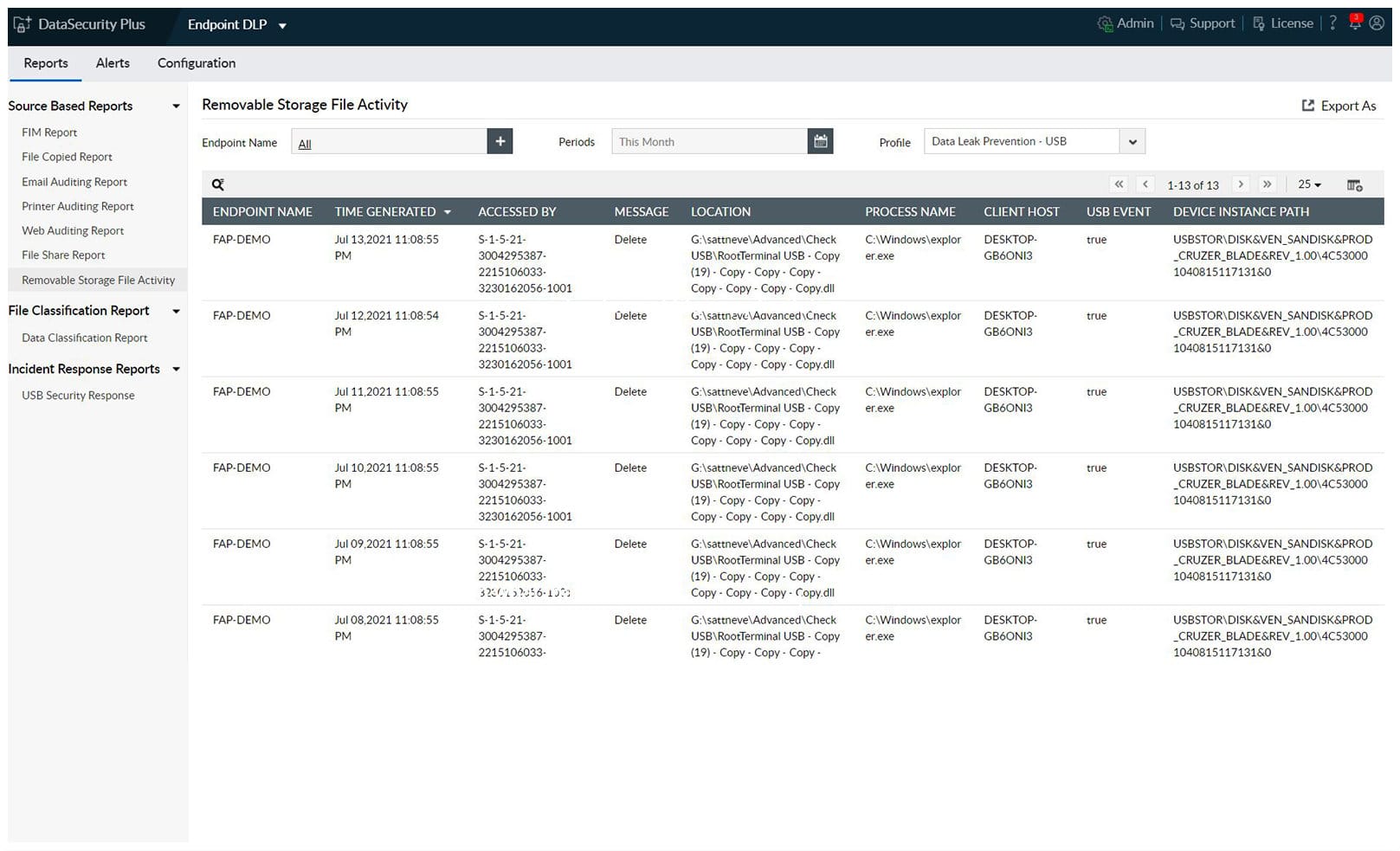
10. ManageEngine Endpoint DLP Plus (FREE TRIAL)
ManageEngine Endpoint DLP Plus is a policy enforcement system for data protection. It searches endpoints for sensitive data and then categorizes those instances. The service can be tailored to meet specific requirements, such as those for PCI DSS. This is implemented by selecting a policy template. The DLP system then tracks user activities on those data stores and controls the movements of the files that contain them.
Key Features:
- Data Categorization: Identifies and categorizes sensitive data across endpoints to ensure protection.
- Policy Templates: Offers customizable policy templates for compliance with standards like PCI DSS.
- User Activity Monitoring: Tracks user interactions with sensitive data to prevent unauthorized access or leaks.
Why do we recommend it?
ManageEngine Endpoint DLP Plus is a package of data protection systems that is ideal for the enforcement of PCI DSS requirements. The system includes a data discovery and classification process, which locates all instances of sensitive data. That process can be tailored to a specific standard by applying a template.
Who is it recommended for?
The ManageEngine system is adaptable according to which standard it is required to apply. PCI DSS is one of the standards that this system will implement. There is a Free edition that will protect 25 endpoints and the Professional edition can be expanded to cover multiple sites and cloud platforms.
Pros:
- Comprehensive Data Protection: Provides robust mechanisms for identifying and safeguarding sensitive information.
- Insider Threat Mitigation: Equips organizations with tools to detect and prevent potential insider threats.
- Flexible Data Access Controls: Implements stringent controls over data access, enhancing security measures.
Cons:
- Lacks Cloud Support: Does not offer a cloud-based edition, limiting its applicability for cloud-focused environments.
ManageEngine Endpoint DLP Plus is offered in a Free edition that is limited to monitoring 25 devices. The paid version is called the Professional edition and it can track all computers on a network – can also monitor multiple sites in one console. The software runs on Windows Server and you can assess it on a 30-day free trial.
11. SENF
SENF is the Sensitive Number Finder. It was developed by the University of Texas at Austin’s Information Security Office and it is free to use. The software is written in Java and it runs on Windows, Linux, Mac OS, and Unix. It will search through the entire device for sensitive numbers stored there, including credit card numbers and social security numbers. The software was available from a GitHub repository but has been removed since this article was first published.
Key Features:
- Cross-Platform Compatibility: Runs on multiple operating systems, including Windows, Linux, Mac OS, and Unix.
- Lightweight Tool: Designed for efficient scanning without significantly impacting system resources.
Why do we recommend it?
SENF is a small, free utility that will scour the servers and workstations of an enterprise for specific patterns of data. The service looks for formats such as social security numbers and bank account numbers. Use this tool in conjunction with data protection systems that do not provide data discovery.
Who is it recommended for?
This is a lightweight tool that has been a little overtaken by more sophisticated tools recently. However, a small business that uses a DLP package that doesn’t have a sensitive data discovery tool included in it would benefit from this program. The tool can be run on all of the major operating systems.
Pros:
- Broad OS Support: Facilitates sensitive data discovery across a wide range of operating systems.
- Resource Efficiency: Operates smoothly without overburdening system resources, ensuring uninterrupted workflow.
Cons:
- Limited Functionality: Offers basic capabilities, which may not suffice for advanced data protection needs.
- Obsolescence: Falls short in comparison to modern tools in terms of functionality and proactive data protection.
- Availability Issues: Its removal from GitHub complicates access to the software, posing challenges for users.
12. PowerGREP
PowerGREP searches through files on a computer for specified data formats. You could use this feature to search for credit card numbers and establish all of the locations where cardholder data is held. The tool can search through all types of files including text, binary files, and compressed files.
Key Features:
- Versatile Data Search: Capable of searching through various file types, including text, binary, and compressed files.
- Customizable Scanning: Allows for detailed and tailor-made scanning methods to identify specific data patterns.
Why do we recommend it?
PowerGREP is a Windows-based tool that is similar to the SENF service. As the name suggests, this tool operates in a similar way to the Unic Grep command, which searches a file for instances of a given text. As with Grep, this tool is able to look for patterns of data rather than just exact text matches.
Who is it recommended for?
This tool is useful for administrators who are used to the concept of Grep but need to search through PCs instead of Linux, macOS, or Unix computers. The tool isn’t just designed for seeking out sensitive data finances but can be put to many uses. PowerGREP is a paid tool.
Pros:
- Advanced Search Capabilities: Provides extensive options for conducting in-depth searches for sensitive information.
- False Positive Management: Enables preview of discovered data, allowing for quick verification and reduction of false positives.
- Comprehensive File Support: Parses through an array of file types, enhancing the scope of data discovery.
Cons:
- Complex Regex Use: Utilization of regex for filtering can be challenging for those unfamiliar with it.
- Cluttered Interface: The user interface may appear overwhelming, making navigation and feature utilization difficult.
PowerGREP is a paid tool, but the vendors offer a three-month money back guarantee.
Wireless security monitoring
13. OpenWIPS-NG
OpenWIPS-NG is made by the same people who produced Aircrack-NG, which is a famous hacker tool. This is a free wireless IPS for Linux. The system has three modules; a sensor, a server, and an interface. The sensor is a packet sniffer that passes network traffic to the server, which is where traffic analysis is performed.
Key Features:
- Packet Sniffer Sensor: Captures network traffic for analysis and detection of intrusion attempts.
- Automated Response: Capable of injecting traffic or modifying wireless data upon detecting intrusion, with options for manual control.
- User Interface: Provides access to data streams and insights through a dedicated interface.
Why do we recommend it?
OpenWIPS-NG is a penetration testing tool for wireless networks. The tool can be used to test a network’s security or it can be left running to detect intrusion. You have to be careful how you run the tool, though because its packet capture function can use up a lot of storage space if you pipe to a file.
The sensor is also able to inject traffic into channels or modify passing wireless traffic. That action can be commanded automatically when the server detects intrusion. It can also be launched manually. The user accesses data streams through the third element in the package, which is the interface.
Who is it recommended for?
This is a free tool for Linux and is more appropriate for use in penetration testing rather than for ongoing security monitoring. The tool is a little old now but it has almost no competition in its specialized field, which guarantees its endurance.
Pros:
- Cost-Effective Solution: Being a free tool, OpenWIPS-NG offers an accessible option for wireless intrusion detection and penetration testing.
- Live Traffic Analysis: Performs real-time analysis of network traffic, allowing for immediate detection and response to potential threats.
- Informative Dashboard: Offers informative insights through default dashboard configurations, aiding in monitoring and threat assessment.
Cons:
- Linux Compatibility Only: Limited to Linux operating systems, restricting its use for organizations operating on other platforms.
- Steep Learning Curve: Requires a significant learning curve compared to other tools, potentially posing challenges for new users.
14. Aruba RFProtect
Aruba RFProtect is a wireless IPS. The Aruba company is a division of Hewlett Packard and it produces networking equipment, including wireless access points. Aruba RFProtect operates from within the AP. The program scans all channels for anomalous transmissions and also prevents unauthorized changes to the configuration of the AP.
Key Features:
- Integrated Wireless IPS: Embedded within Aruba wireless access points, providing comprehensive wireless intrusion prevention capabilities.
- Automatic Anomaly Detection: Scans all channels for unusual transmissions and prevents unauthorized configuration changes to access points.
- Auditing and Reporting: Includes auditing and reporting functionalities compliant with PCI DSS and other regulatory requirements.
Why do we recommend it?
Aruba RFProtect is one of the few alternatives to OpenWIPS-NG. It is a paid tool, which gives it advantages and disadvantages when compared to its free rival. Small businesses might balk at paying for the tool but its development budget provides a more sophisticated system that is easy to use.
The tool contains defense measures to lock out transmissions from IPs that seem to be engaged in malicious activities. It includes an auditing and reporting module that complies with PCI DSS requirements and can also be tailored towards HIPAA, DoD 8100.2, and GLBA compliance reporting requirements.
Who is it recommended for?
Aruba RFProtect blocks a range of hacker attacks that can be implemented on wireless networks. The audience for this tool is limited, however, because it will only operate on networks that are run by Aruba Networks wireless systems.
Pros:
- Automated Threat Detection: Automatically identifies and blocks suspicious activities, such as rogue access points and deauthorization attacks.
- Compliance Capabilities: Offers preconfigured auditing and reporting scans to ensure compliance with industry standards like PCI DSS.
- Effective Defense Mechanisms: Implements measures to block malicious IP addresses and safeguard wireless networks against various hacker attacks.
Cons:
- Opaque Pricing Structure: Lack of transparent pricing requires contacting sales teams, potentially leading to uncertainty for prospective buyers.
Password protection lockers
If you want to qualify as PCI DSS compliant, password managers are not an option – they are a requirement of the standard. Creating long passwords composed of random characters and storing them for reuse because they are impossible to remember creates extra security for the network. For one thing, users are not able to disclose passwords that can’t be remembered and password manager access procedures place an extra barrier between the outside world and your resources. Here are two password protection systems that we recommend:
15. KeePass Password Safe
KeePass Password Safe has a GUI interface that lists all of the passwords stored in its internal database. The database is locked by AES or Twofish encryption, and you need to create one password in order to access the interface. Once started, the program will run in the background and fill in all passwords in screens on the computer for you. It also has a strong password generator.
Key Features:
- Secure Password Storage: Utilizes AES or Twofish encryption to safeguard stored passwords within a locked database.
- Password Generation: Includes a strong password generator to create complex and secure passwords for enhanced protection.
- Cross-Platform Compatibility: While primarily for Windows, KeePass can run on Linux, Unix, and macOS through Wine.
Why do we recommend it?
KeePass Password Safe is a free, open-source software package for Windows but you can run it on Linux, Unix, and macOS over Wine. This package needs to be installed on each device but you can manage a central password database and distribute it across the network with a managed file transfer script.
Who is it recommended for?
This system is suitable for home use and for small businesses. The tool protects the password vault with strong AES encryption. This is not a networked solution and so it wouldn’t be suitable for large organizations or managed service providers. Another detection for large businesses is that it doesn’t come with professional support.
Pros:
- Free and Open-Source: Offers a cost-effective solution for password management, suitable for both personal and small business use.
- Strong Encryption: Protects password vaults with robust encryption methods, ensuring resistance against brute force attacks.
- Portable Usage: Can be run from a USB stick, allowing for convenient access to passwords on various devices.
Cons:
- Dated Interface: User interface may feel outdated and cluttered, especially when managing a large number of credentials.
- Lacks Networked Solution: Not designed for large organizations or managed service providers due to the absence of networked features and professional support.
This is a free password protection system for Windows, Linux, Mac OS, and Unix. There is also a version that can be run from a USB stick.
16. Password Gorilla
Password Gorilla distributes passwords via the clipboard, so you will have to paste passwords into each site and application that you visit. Passwords are protected by SHA256 and the entire database is encrypted by Twofish. The program includes a password generator that provides impossible to remember random strings for each password.
Key Features:
- Clipboard Password Distribution: Passwords are distributed via clipboard, requiring manual pasting into applications and websites.
- Encryption: Utilizes SHA256 and Twofish encryption to protect stored passwords and the entire database.
- Password Generator: Includes a password generator for creating complex and secure password strings.
Why do we recommend it?
Password Gorilla is a simple free password vault system that will run on Windows, Linux, macOS, and Unix. It distributes stored passwords by copying them into the clipboard. This is an efficient solution but it also means that this service is an on-device system and can’t be effectively networked.
Who is it recommended for?
This tool rivals KeePass Password Safe because it is a free on-device password vault. Thus, it is suitable for home use and small businesses. The methodology of Password Gorilla makes it impossible to distribute a password file, so even the distribution workaround that can be implemented for Keepass isn’t possible with this tool.
Pros:
- Cross-Platform Compatibility: Available for Windows, Linux, macOS, and Unix, providing flexibility across different operating systems.
- Secure Password Generation: Offers a secure password generator for creating strong and unique passwords, enhancing security.
- Customizable Password Policy: Allows users to specify password policies for generating credentials, ensuring adherence to security standards.
Cons:
- Manual Password Pasting: Requires manual pasting of passwords, lacking autofill functionality found in newer password managers.
- Limited Interface: Interface may feel limited compared to more feature-rich password managers, potentially impacting user experience.
Password Gorilla is another free password manager that is available for Windows, Linux, Mac OS, and Unix. There is also a standalone version that will run from a USB stick.
Network monitoring systems
Although network monitoring systems are not specifically demanded by the requirements of PCI DSS, the security of a system can only be guaranteed by stability. You will need to keep an eye on the performance of the network because partial failure can reduce the effectiveness of the security systems that are detailed above. Here are two network monitoring systems that we recommend.
17. SolarWinds Network Performance Monitor (FREE TRIAL)
The SolarWinds Network Performance Monitor is a leading network monitor that uses SNMP procedures to keep a constant check on the statuses of network devices. Monitored equipment is able to send an alert message to the monitor when emergency conditions arise. The monitor is able to guard wireless systems and virtualizations as well as standard LANs. The tool discovers all network devices automatically and generates a network topology map.
Key Features:
- SNMP Monitoring: Utilizes SNMP procedures to monitor the status of network devices, including wireless systems and virtualizations.
- Alerting: Raises alerts for emergency conditions, ensuring prompt response to network issues and failures.
- Automatic Device Discovery: Discovers and maps network devices automatically, providing comprehensive visibility into network topology.
Why do we recommend it?
SolarWinds Network Performance Monitor provides a method to ensure the constant availability of protection systems, such as VPNs. this is a necessary requirement of any system that needs to prove compliance with data protection standards. Such as PCI DSS. The monitor will raise an alert if any element on the network ceases to respond.
Who is it recommended for?
This tool has a number of security benefits as well as performance monitoring. For example, it can spot rogue devices connected to the network and it also ensures the correct operations of wireless networks as well as LANs. The service is suitable for use by large organizations with many network devices.
Pros:
- Enterprise Scalability: Built to scale and support thousands of devices across multiple LANs, making it suitable for large organizations.
- Intuitive Dashboards: Offers intuitive dashboards for at-a-glance health reports and granular performance metrics, enhancing monitoring efficiency.
- WAN and VPN Support: Supports WAN environments and multiple VPN configurations, ensuring comprehensive network monitoring capabilities.
Cons:
- Enterprise Focus: Tailored for enterprise use, may not be suitable for home networks or small LANs due to complexity and scale.
The SolarWinds Network Performance Monitor installs on Windows Server and you can get a 30-day free trial of this software.
You can extend network monitoring by also implementing traffic monitoring with the SolarWinds NetFlow Traffic Analyzer. That service provides the ability to extract traffic throughput data from switches routers, and hardware firewalls. This system also runs on Windows Server. The Network Performance Monitor and the NetFlow Traffic Analyzer slot together in a common console and you can buy them both together with the Network Bandwidth Analyzer Pack, which is offered on a 30-day free trial.
18. Paessler PRTG Network Monitor
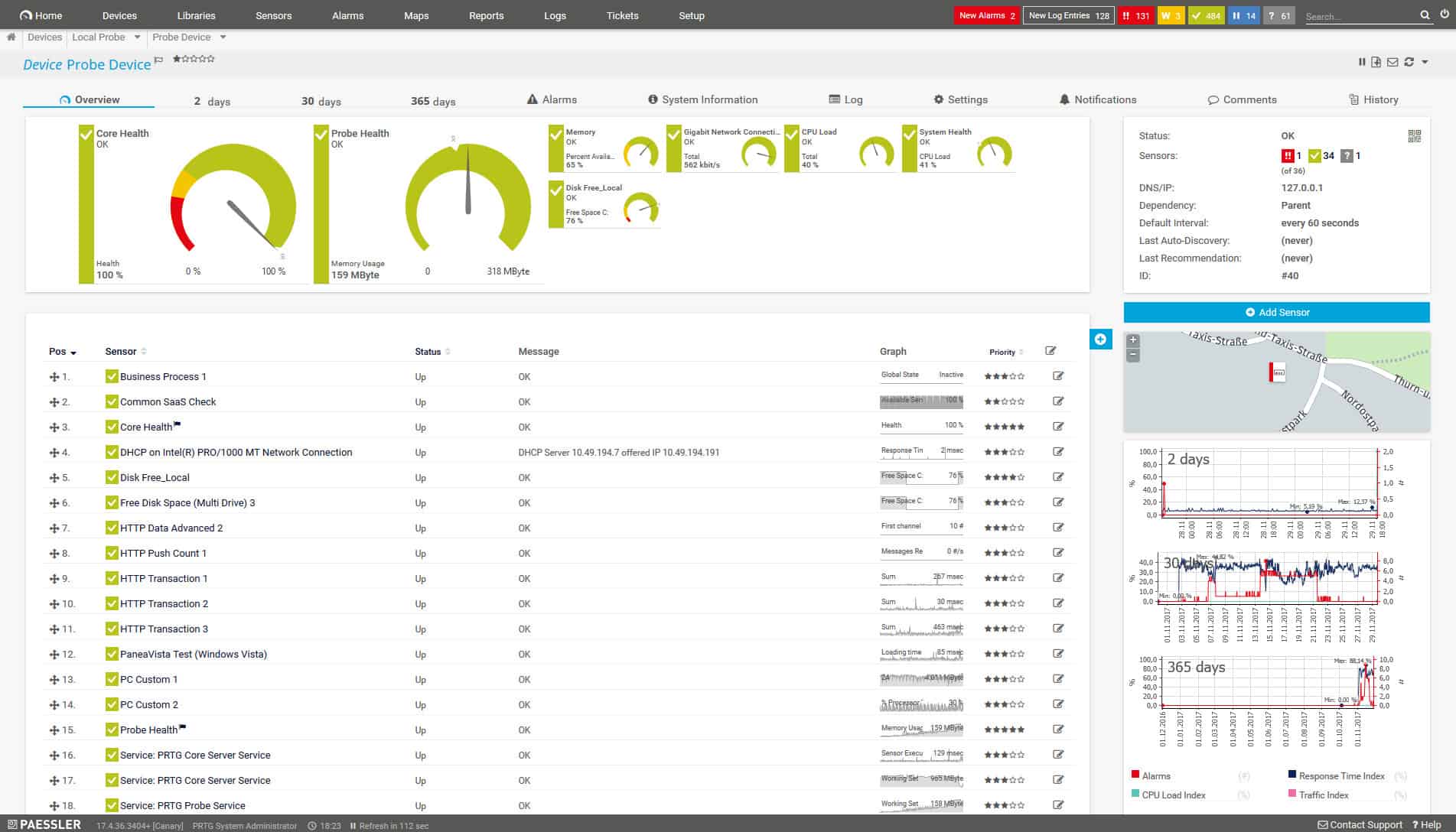
Paessler’s PRTG Network Monitor is a unified network, server, and application monitor that contains a large collection of “sensors”. Each sensor is an individual monitor and you choose which of the large library of sensors you want to activate. The system installs on Windows Server and is free to use if you only activate up to 100 sensors. The monitor uses SNMP procedures to monitor LANs, wireless networks, and virtualizations.
Key Features:
- Unified Monitoring: Monitors networks, servers, cloud platforms, services, and applications with a collection of customizable sensors.
- Flexible Sensor Activation: Users can activate sensors based on their monitoring needs, allowing for tailored monitoring configurations.
- Network Discovery: Constantly repeats network discovery to identify and manage devices, including rogue devices.
Why do we recommend it?
Paessler PRTG Network Monitor is a system-wide monitoring package for networks, servers, cloud platforms, services, and applications. The software is a bundle of monitoring tools, called “sensors”, and the buyer decides which to activate. The core of the system is a network discovery service, which repeats constantly and can help you to discover rogue devices.
Who is it recommended for?
PRTG doesn’t have any sensors that are specifically dedicated to PCI DSS enforcement. It is a system monitoring tool. You can opt to get the package for installation on Windows Server or sign up for the cloud-based SaaS version. PRTG is free forever if you only activate 100 sensors.
Pros:
- Multi-Network Monitoring: Supports both LAN and WAN monitoring across multiple networks, providing comprehensive network visibility.
- Application SLA Monitoring: Configurable sensors for specific application SLAs help enforce compliance and performance standards.
- Visualizations: Utilizes various visualizations to keep teams and administrators informed on network performance and status.
Cons:
- Learning Curve: Offers numerous features and customization options, requiring time to fully explore and utilize all capabilities.
You can get a 30-day free trial of thisPaessler’s PRTG Network Monitor.
Configuration management
Intruders can get wider access to your network if they are able to alter the settings on your network devices, namely your switches and routers. Creating a standard configuration for your devices, backing them up and installing them on new devices helps you be compliant to PCI DSS Requirement 6. Here are our two recommendations.
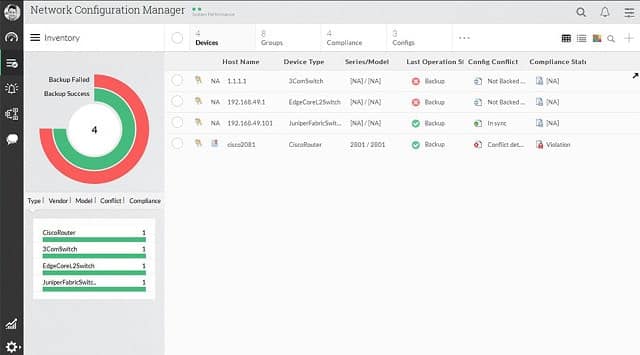
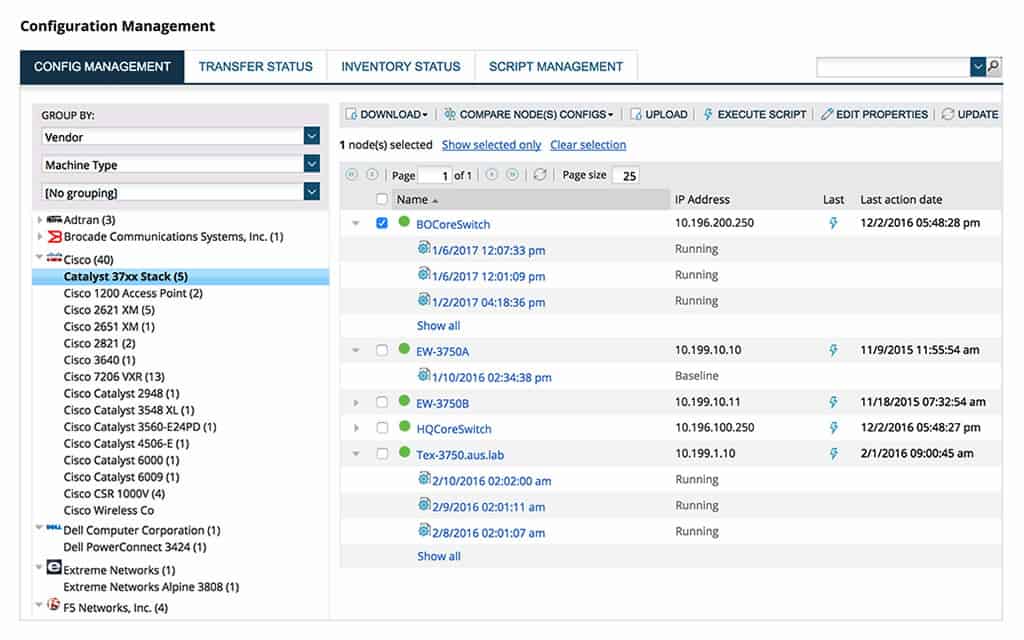
19. ManageEngine Network Configuration Manager
The Network Configuration Manager is able to manage configurations for switches, routers, and firewalls. The service backs up the configuration and then monitors for any changes to the set up of your devices, reinstalling the original image if unauthorized changes occur. The system logs all changes and actions and produces audit reports to help PCI DSS compliance.
Key Features:
- Configuration Management: Manages configurations for switches, routers, and firewalls, including backup and restoration of configurations.
- Change Monitoring: Monitors for any changes to device configurations and reinstates original configurations if unauthorized changes occur.
- Audit Reporting: Logs all changes and actions, producing audit reports to facilitate PCI DSS compliance.
Why do we recommend it?
ManageEngine Network Configuration Manager helps you to manage the settings of your network devices. Create a standard profile for one device, store an image, and then apply it to all other devices of the same type. The tools will watch all devices and restore the standard configuration if an unauthorized change is detected.
Who is it recommended for?
This package is suitable for use by all sizes and types of businesses. The system will also scan device firmware and identify when updates are available. The software for the Network Configuration Manager can be run on Windows Server, Linux, or AWS. The Free edition is limited to monitoring only two devices.
Pros:
- Multi-Platform Support: Available for Windows, Mac, and Linux systems, ensuring compatibility across different operating environments.
- Autodiscovery: Continuously discovers assets through autodiscovery, providing comprehensive network visibility.
- Real-time Alerts: Immediately alerts when configuration changes are detected, enabling prompt response to security incidents.
- Infrastructure Organization: Neatly organizes networks, devices, and infrastructure to support multi-site use, enhancing management efficiency.
Cons:
- Learning Curve: As a full-service monitoring platform, it may take time to fully explore all available options and features.
You can get a 30-day trial of the ManageEngine Network Configuration Manager.
20. SolarWinds Network Configuration Manager (FREE TRIAL)
The SolarWinds Network Configuration Manager integrates with the SolarWinds Network Performance Monitor. Its reporting module contributes towards PCI DSS compliance. On installation, the tool scans the network, logs all switches, routers, and firewalls and backs up their configurations. Subsequent configuration changes need to be made through the manager’s interface because it will overwrite any direct changes with its stored image.
Key Features:
- Integration: Integrates with the SolarWinds Network Performance Monitor and contributes towards PCI DSS compliance.
- Automated Backup: Scans and logs switches, routers, and firewalls, backing up configurations and enforcing changes through the manager’s interface.
- Vulnerability Database Checks: Regularly checks the Cisco National Vulnerability Database and updates firmware accordingly.
Why do we recommend it?
SolarWinds Network Configuration Manager is a rival to the ManageEngine system and provides identical services. This is an on-premises package and it can be bought in conjunction with the Network Performance Monitor in the Network Automation Manager. This system works for compliance with PCI DSS, HIPAA, and SOX.
The tool makes regular checks with the Cisco National Vulnerability Database and updates firmware whenever necessary. It also has strong capabilities when interfacing with the Cisco Adaptive Security Appliance firewall.
Who is it recommended for?
The Network Configuration Manager has a great deal of capacity and provides its best service to large organizations. The tool performs automated device monitoring and will block attempts by intruders or malware to weaken security settings on network devices. This software package runs on Windows Server.
Pros:
- Comprehensive Reporting: Reporting module aids in fixing compliance issues and provides immediate insights through templated health reports.
- Automated Device Discovery: Automatically discovers new devices on the network and provides health reports upon installation, enhancing visibility.
- Configuration Management: Offers configuration management, allowing quick backup and restoration of changes that impact performance.
- Security Monitoring: Monitors settings for unauthorized changes and blocks attempts by intruders or malware to weaken security settings.
- Customizable Dashboard: Offers a customizable dashboard with various options for visualizing network performance, improving usability.
Cons:
- Enterprise Focus: Not designed for home networks, tailored for enterprise use by system administrators and network technicians.
The tool installs on Windows Server and you can get it on a 30-day free trial.
The Network Configuration Manager is just one of the tools that you will need to monitor and manage your network and SolarWinds produces many others. You can buy all of the SolarWinds network systems together in a bundle, called the Network Automation Manager. The components of this pack can all be bought individually. However, you save time buying the bundle. All of the components fit together in one common console. Those units are:
- Network Performance Monitor (NPM)
- Netflow Traffic Analyzer (NTA)
- User Device Tracker (UDT)
- VoIP & Network Quality Manager (VNQM)
- Network Configuration Manager (NCM)
- IP Address Manager (IPAM)
- SolarWinds High Availability
SolarWinds provides the Network Automation Manager on a 30-day free trial.
PCI DSS Compliance FAQs
What is PCI DSS compliance?
PCI DSS stands for Payment Card Industry Data Security Standard. This is a set of guidelines that any business needs to follow if it handles payments by credit or debit card. The rules only apply within the USA. However, the global nature of the eCommerce means that websites run by businesses in other countries could need to comply with PCI DSS. The main thrust of the rules is that personally identifiable information (PII), bank account details, and card data should be protected as much as possible against theft, misuse, or alteration.
Is PCI DSS compliance mandatory?
PCI DSS is an industry standard and not a law. Compliance is a commercial imperative and is usually written into service contracts by banks and payment clearance systems. Failure to comply would get a merchant account suspended and that trader would find it impossible to accept payments by card.
Who must comply with PCI DSS?
If you are unsure whether your business needs to comply with PCI DSS, look at the contracts you have with your payment processing service. This is where PCI DSS is relevant and if the agreement mentions the standard, you could lose your account if you don’t take steps to protect PII and customer banking data.