Data privacy has become one of the most critical concerns for organizations worldwide, as data breaches and privacy regulations continue to evolve. With growing threats to personal and sensitive information, businesses must take proactive steps to protect data and ensure compliance with various laws and regulations. The importance of data privacy management cannot be overstated in today’s digital landscape, where data is constantly collected, processed, and shared across multiple systems.
Here is our list of the best data privacy management tools:
- Ketch EDITOR’S CHOICE A no-code, AI-driven platform that automates consent management, data subject rights fulfillment, and real-time compliance monitoring to help businesses comply with global privacy regulations like GDPR and CCPA, reducing legal risks and enhancing customer trust through transparent data practices. Access a free trial.
- StandardFusion A cloud-based risk assessment and compliance auditing package with an automated compliance manager.
- ServiceNow Governance, Risk, and Compliance A cloud-based data privacy management system that ties into a service desk system and project management tools.
- N-able Risk Intelligence A cloud-based vulnerability assessment tool with a data discovery system and a permissions analyzer.
- ManageEngine DataSecurity Plus A package of data management services that include discovery and categorization procedures, a vulnerability scanner, and a file integrity manager. It runs on Windows Server.
- Spirion Sensitive Data Manager A data privacy manager with data discovery and classification processes and file protection services This a cloud-based service with on-site agents for Windows, macOS, and Linux.
- Azure Information Protection A cloud-based sensitive data manager that tracks access to files and manages their movements.
- Acronis Cyber Protect A package that includes a vulnerability scanner, a data backup system, and a data loss prevention module. It runs as a virtual appliance.
- SolarWinds Security Event Manager A log management and SIEM security service with automated risk management and compliance auditing. It runs on Windows Server.
This comprehensive guide to data privacy management provides essential insights into the key aspects of protecting personal and business information. It explores the various elements of data privacy, including the legal and regulatory frameworks that govern data protection, best practices for data governance, and the technologies available to help manage and safeguard data.
With legal requirements such as the GDPR, CCPA, and HIPAA, organizations must understand the nuances of compliance to avoid hefty fines and reputational damage.
The guide outlines practical strategies for implementing a data privacy program, including risk assessments, employee training, and establishing data access controls. It also highlights the tools and solutions available, such as Data Loss Prevention (DLP) systems, encryption technologies, and privacy management software, to help businesses ensure that their data privacy practices are up to industry standards.
Whether you’re a small business or a large enterprise, this guide serves as a valuable resource to help you navigate the complex world of data privacy management. By understanding the risks, regulations, and tools available, you can develop a data privacy strategy that ensures compliance, builds trust with customers, and protects your organization’s most valuable asset: its data.
Data privacy legislation
PCI DSS is the Payment Card Industry Data Security Standard. It only applies to businesses operating in the USA, and it is a required standard for any business that handles payments by credit or debit card. HIPAA is the Health Assurance Portability and Accountability Act. It covers the protection of “Protected Health Information” (PHI), which means data related to individuals processed within the health sector.
Members of the general public can be tracked by “Personally Identifiable Information” (PII). Leaks of PII can lead to compensation claims for all people who disclosed data related to – that can prove very costly to businesses.
The EU’s General Data Protection Regulation (GDPR) lays out a standard of expected protection for PII. GDPR stipulates that a company that fails to protect PII adequately can be fined an amount of up to 4 percent of its turnover. That’s per leak event. The GDPR laws also allow individuals to bands together and launch class-action suits against companies that leak their data.
Another legal recommendation of the EU bundled into GDPR laws in member states is the ePrivacy Directive. This is where the requirement for cookie consent comes from. Combined, GDPR and the ePrivacy Directive create a headache for businesses that hold PII in digital format – the data doesn’t have to be collected on the Web to be included in these laws.
These data privacy standards require companies to implement a Data Subject Access Request (DSAR) mechanism. This allows members of the public to request copies of all of the information held on a system about them. They have the right to ask that mistakes are corrected and demand that PII be removed.
The EU is not the only area in the world where data privacy issues have been codified into law. The primary standard that mirrors GDPR currently in operation is the California Consumer Privacy Act (CCPA). However, the USA has regulations about PHI and card information, thanks to HIPAA and PCI DSS. Other areas of PII usage weren’t regulated. CCPA fills in those gaps.
Brazil’s Lei Geral de Proteção de Dados (LGPD) stipulates a requirement for the protection of PII. In Canada, the Personal Information Protection and Electronic Documents Act (PIPEDA) is in effect as a GDPR-like system. South Africa’s version is called the Protection of Personal Information Act (POPIA).
Other places in the world are catching up on the issue of data privacy legislation. The subsequent law in the USA to be launched in this field is the Consumer Data Protection Act (CDPA) in Virginia, which will come into effect in 2023. Many other areas of the world are currently formulating their data privacy laws, notably India, Chile, and China.
Dealing with data privacy obligations
Although there are many different pieces of legislation either in effect or scheduled for launch, there are commonalities to all of them. The basis is that data should be protected from disclosure, loss, or misuse and that there should be a mechanism to inform the general public about how their data will be stored and used, plus a way for them to query their PII records.
A big problem with all of these different laws is that they don’t apply to the location of the data-holding business, they relate to the location of the person that the data is about. So, even if your company is based in an area with no local privacy law, such as Sri Lanka, you will need to comply with every law in the world if you have a website.
There is a way around all of these laws. That is to not hold data in electronic format about individuals. One other option is to decide not to do any business with consumers in those places with privacy laws. Given the global nature of the World Wide Web, you will get visitors from people in those companies if you have a website. Again, there is a way around this problem – just block access to physically located people in an area of the world where privacy law is in force. You could allow access to the site but block access to any data gathering function.
The problem with the decision to just withdraw from business in areas governed by privacy laws is that they tend to cover very lucrative markets.
Data privacy management tools
You don’t need to cut your business’s ties to its most lucrative markets. Fortunately, there are many similarities between all of the existing and emerging data privacy standards. It is possible to introduce a data privacy management solution and keep your company legally trading in all of those places that are covered by privacy laws. As more countries introduce data privacy legislation, a strategy of avoiding these obligations will continuously reduce your business’s areas of operation.
Data privacy management tools solve all of the requirements of laws and standards around the world. These keep you trading with the world while keeping it legal. There are several phases to data privacy management that you need to pay attention to. These tasks are grouped under the abbreviation “GRC.” This stands for governance, risk management, and compliance.
Governance refers to the auditing and access controls that you need to have in place to track all actions on sensitive data. Risk management describes the identification of data that needs to be protected and a classification process that grades different types of data according to whether the damage, loss, or disclosure of that data will have serious consequences.
Not all risk issues relate to data that is covered by data privacy laws and standards. Your company will have trade secrets, such as working practices that give it a competitive edge, research for new, innovative products, and price lists that only apply to specific customers. The disclosure of that information wouldn’t incur a fine, but it could seriously damage the business’s competitive advantages.
The compliance part of GRC refers to conformance to particular standards that apply to the types of data that the company holds. Compliance requirements include external auditing, which requires extensive log retention, access controls, data loss mitigation procedures, data usage reporting, and DSAR processes.
During ongoing operations, you will need data security and data management tools to restrict and track access to data stores and block malicious activity.
The best tools for data privacy management
Data privacy management involves a range of tools. Some providers manage to package together just about all of the tools that you will need to adequately protect data from loss or misuse while still making it available for legitimate business processes.
What should you look for in a data privacy management system?
We reviewed the market for data privacy management tools and analyzed the options based on the following criteria:
- A bundle that offers linked services that include many tools needed for data privacy management
- An easy-to-use dashboard that includes graphical data interpretation for rapid status recognition
- A system that includes automated monitoring processes
- Security tools that include file integrity management
- Data protection systems that have backup and restore functions
- An assessment opportunity provided by a free trial or money-back guarantee
- Value for money provided by as many of the tools necessary for data privacy management in one bundle
Taking these requirements into account, we assembled a list of practical systems that will help you manage data privacy easily.
You can read more about each of these data privacy management solutions in the following sections.
1. Ketch (FREE TRIAL)
Ketch is designed to help businesses comply with global regulations like GDPR, CCPA, and CPRA. It provides tools for consent management, data subject rights fulfillment, and privacy policy enforcement, all through a unified, no-code interface. Ketch’s AI-driven automation simplifies compliance workflows, reducing manual effort while ensuring accuracy. By integrating with existing tech stacks, Ketch enables organizations to build trust with customers through transparent data practices while avoiding costly fines for non-compliance.
Key Features:
- Automated consent management
- Data Subject Request (DSR) fulfillment
- Real-time compliance monitoring
- No-code policy configuration
Why do we recommend it?
Ketch stands out for its automation, ease of use, and reliable compliance features. It reduces legal risks while improving customer trust. The platform’s adaptability to changing regulations and easy integrations make it a future-proof solution for businesses prioritizing privacy.
The platform goes beyond basic compliance by offering granular control over data collection and usage, empowering businesses to align privacy policies with customer expectations. Ketch’s real-time monitoring and reporting capabilities provide visibility into data flows, helping organizations identify and mitigate risks proactively. Its scalable architecture makes it suitable for enterprises and SMBs alike, offering flexibility to adapt to evolving privacy laws.
Who is it recommended for?
Ketch is ideal for compliance teams, legal departments, and marketing teams handling customer data. Enterprises, mid-sized businesses, and startups facing complex privacy regulations will benefit from its scalable, no-code approach.
Pros:
- Reduces compliance workload with automation
- Adapts to multiple privacy laws globally
- Enhances customer trust through transparency
- Integrates easily with existing tech stacks
Cons:
- Pricing may be prohibitive for very small businesses
You can examine Ketch by accessing a free trial.
2. StandardFusion
StandardFusion is a data privacy management service aimed at standards compliance. The standards this package implements include GDPR, HIPAA, PCI-DSS, ISO, SOC2, NIST, CCPA, and FedRAMP. The service helps you adapt your IT system and working practices for standards compliance through a series of questionnaires.
Key Features:
- Questionnaire based
- Change management
- Risk management
- Auditing function
Why do we recommend it?
StandardFusion is a GRC risk management platform that is designed to enable businesses to assess their operations to get them aligned with a specific data protection standard and then monitor day-to-day activities and data storage conditions to keep them in compliance. The tool gives you compliance reporting as well as auditing and enforcement.
The automated processes in the plan perform a risk analysis that highlights changes that need to be made to make the IT system compliant. It reassesses each change until the system reaches an appropriate state. The StandardFusion package includes data discovery and classification service. It then monitors file access in sensitive data stores, creates logs, and protects log files from tampering.
Who is it recommended for?
The StandardFusion system is offered in four plans and all of them are priced so that they are only accessible for large organizations. The platforms are designed to be used by an in-house GRC team and there is an onboarding fee to pay as well as a monthly subscription rate.
Pros:
- Adapts to GDPR, HIPAA, PCI-DSS, ISO, SOC2, NIST, CCPA, and FedRAMP
- Includes third-party
- Collates evidence
- Centralizes compliance documentation
Cons:
- Hosted service with no on-premises option
The system integrates with Jira, Confluence, Slack, OpenID, DUO, and Google Authenticator. This is a hosted service, and it is available for a 14-day free trial.
3. ServiceNow Governance, Risk, and Compliance
ServiceNow is a service desk system, and its GRC package can be integrated into that system management tool. The primary tool in this package is risk assessment related to the protection of sensitive data. Risk assessment also extends to the evaluation of third parties and decision support for new projects.
Key Features:
- GRC for service desk
- Data privacy
- Working practice guidance
Why do we recommend it?
ServiceNow Governance, Risk, and Compliance is a GRC service that adds on to a Service Desk system. The advantage of this strategy is that the based package of ServiceNow will have already mapped your data management asset and channeled all of your business’s IT asset management procedures – GRC just needs to tweak that.
The tool’s governance sections help you establish safe working practices and create a data privacy management policy together with the risk assessment system. Compliance features help you track data protection goals.
Who is it recommended for?
This is an accessible package for any business that is able to afford the ServiceNow IT Operations Management system. This is a cloud-based package, so you don’t need to worry about making server space for it. The platform can be expanded by a range of modules.
Pros:
- Risk assessment module
- Third-party risk assessment
- Continuous monitoring
Cons:
- No free trial
ServiceNow Governance, Risk, and Compliance are available for a demo.
4. N-able Risk Intelligence
N-able Risk Intelligence is a vulnerability scanner for all endpoints on a network that runs Windows and macOS. The vulnerability scanner references the Common Vulnerability Scoring System (CVSS) to identify system risks. The scanner examines access rights and file permissions and remembers weak system settings.
Key Features:
- Vulnerability scanning
- Endpoint assessment
- Data discovery
Why do we recommend it?
N-able Risk Intelligence is an add-on to the N-able stable of remote monitoring and management tools. This is a cloud platform that reaches out to endpoints through the installation of agents. The Risk Intelligence service provides a sensitive data scanner that locates and reports on data that need to be protected.
The service also scans for sensitive data, categorizes it, and maps its locations. The sensitive data discovery tool searches for email addresses, license plate numbers, bank accounts, social security numbers, ACH data, and credit card numbers. It generates a risk report for each type of PII that it discovers.
Who is it recommended for?
This tool is designed for use by managed service providers and IT departments. It is particularly useful for serving multiple clients in one account or multiple sites, in the case of corporate use. The dashboard for the service is based in the cloud. It only scans endpoints running Windows or Windows Server.
Pros:
- Part of a platform of tools for managed service providers
- Creates a risk report for each sensitive data type discovered
- Good for PCI DSS, GDPR, and CCPA
Cons:
- Mainly for use by managed service providers to assess the systems of their clients
N-able Risk Intelligence is hosted as a SaaS system and is suitable for compliance with PCI DSS, GDPR, and CCPA. Other utilities in the package include a vulnerability scanner and security issues surrounding the email system. You can assess N-able Risk Intelligence on a 14-day free trial.
5. ManageEngine DataSecurity Plus
ManageEngine DataSecurity Plus performs File Server Auditing, Data Leak Prevention, and Data Risk Assessment. Each of these modules is also available individually.
Key Features:
- Data leak prevention
- Risk assessment
- Sensitive data discovery
Why do we recommend it?
ManageEngine DataSecurity Plus is a very large package that is divided into four modules. Data privacy management is at the heart of all four of these services but you don’t have to buy all of them together, you can treat the platform as a menu rather than a package.
Features in the package include a sensitive data discovery tool that assigns a vulnerability ranking to each discovered piece of data. The package examines file permissions and access rights to devices and folders to assist in tightening data security. DataSecurity Plus also includes File Integrity Management (FIM), which records changes to files that hold sensitive data. The service controls USB sockets and prevents file transfers. It also examines attachments to emails.
Who is it recommended for?
As it is very large, the full package is also expensive. However, you can cut the cost by examining the functions of each of its four modules and only buying the services that you need. There isn’t a permanently free edition for this package but there is a 30-day free trial.
Pros:
- Discover and categorize PII, PHI, and PCI
- File copy blocking
- Works for PCI DSS, GDPR, and HIPAA
Cons:
- No version for Linux
ManageEngine DataSecurity Plus installs on Windows Server. You can assess it on a 30-day free trial.
6. Spirion Sensitive Data Manager
Spirion Sensitive Data Manager is a cloud-based service that tracks data on all of your sites plus cloud platforms.
Key Features:
- Discovery of PII, PHI, and PCI
- Vulnerability assessments
- Data protection
Why do we recommend it?
Spirion Sensitive Data Manager is a data discovery and classification that observes daySpir-to-day data creation and instantly records and categorizes new instances. The interesting feature of this package is that it will automatically reclassify all data if data protection sensitive data definitions change. It covers many data protection standards.
It includes a data discovery tool called AnyFind that identifies intellectual property, PII, PHI, and credit card information. A module called Watcher implements data classification for sensitivity. This facility also examines vulnerability levels of data. Spyglass’s module applies security measures to sensitive data stores, such as FIM and data loss prevention.
Who is it recommended for?
This tool is able to scan endpoints running Windows, macOS, and Linux. The company advertises the package as a system that has deployment options on the cloud or on-premises. In fact, the server runs on the cloud and is a hosted service while agents, which are also called “clients” need to be installed on endpoints or on cloud platform.
Pros:
- File integrity protection
- Classifies risk
- Good for GDPR, CCPA, HIPAA, and PCI DSS
Cons:
- No self-hosting option
Spirion Sensitive Data Manager will help you achieve compliance with GDPR, CCPA, HIPAA, and PCI DSS. Spirion offers a demo of the package.
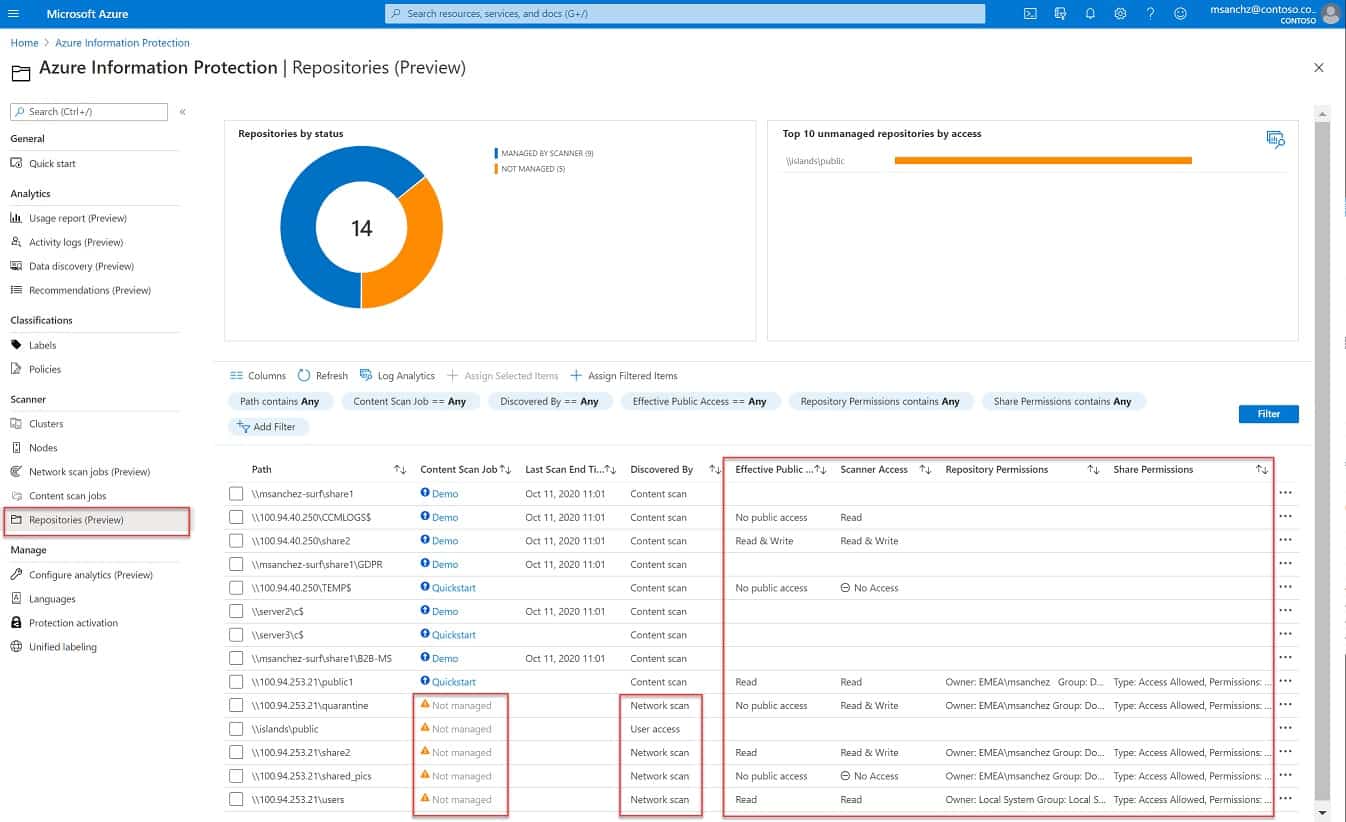
7. Azure Information Protection
Azure Information Protection searches for sensitive data on your sites or any of your cloud services. It then monitors for emails, document access, and data stores.
Key Features:
- Part of the Azure platform
- Data discovery and classification
- Protection for hybrid systems
Why do we recommend it?
Azure Information Protection is a very interesting service because ut us extensive and affordable and although it is based on the Azure platform, it isn’t limited to scanning data held on Azure. In fact, you can use this package even if you don’t run any other Azure accounts.
According to the standards that need to be followed, the actions of the Information Protection service are adaptable. Accordingly, the service will protect different types of data. It is possible to block the movement, copying, or printing of sensitive data with this tool.
Who is it recommended for?
You can’t download this package and host it on your own server. The system will implement data discovery and classifications across your on-premises system from its hosted location. The service can be tailored to the requirements of a specific standard and it will track data usage and movement in emails as well as on endpoints.
Pros:
- Tracks data movements and optionally blocks it
- Permits file sharing
- File integrity monitoring
Cons:
- Only available on Azure
The service also offers an encryption system to protect files both at rest and in transit.
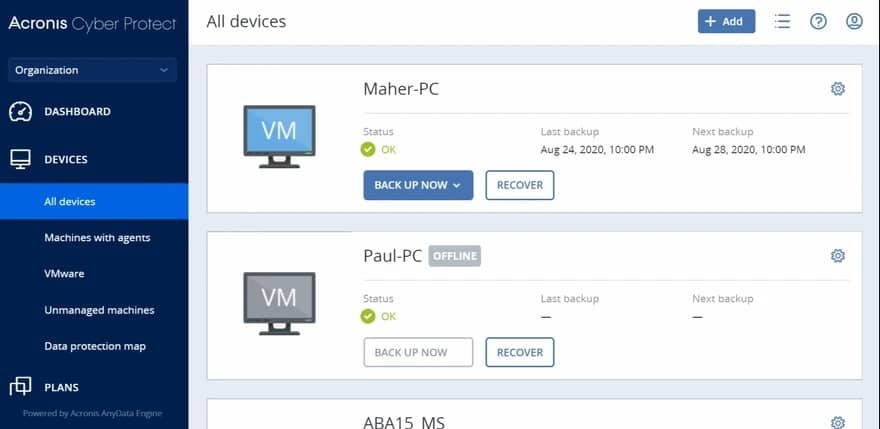
8. Acronis Cyber Protect
Acronis Cyber Protect includes a backup system, a vulnerability scanner, and a threat-protection system.
Key Features:
- Antivirus and anti-ransom
- Data backup
- Vulnerability scanner
Why do we recommend it?
Acronis Cyber Protect is a data protection service rather than a data privacy management system. It will protect all of your data against malware, damage, and destruction through its malware scanning and backup service. It operates on all data, regardless of whether a particular standard deems it to be sensitive.
The backup service can replicate servers, so you don’t have to restore to the same server. It will backup servers running Windows Server and Linux, and it can also protect virtual servers.
Who is it recommended for?
The Acronis Cyber Protect system is a family of products, each of which is tailored to a particular size of business. The services of this system are necessary for any business because it includes a backup service. However, it won’t protect your data against theft by authorized users.
Pros:
- Combines cybersecurity and data protection
- Integration for Microsoft 365
- Cloud storage available
Cons:
- Rate per endpoint
The vulnerability scanner tightens up your system to prevent data loss and the threat protection service further shields data from intruders. Acronis Cyber Protect is available for a 30-day free trial.
9. SolarWinds Security Event Manager
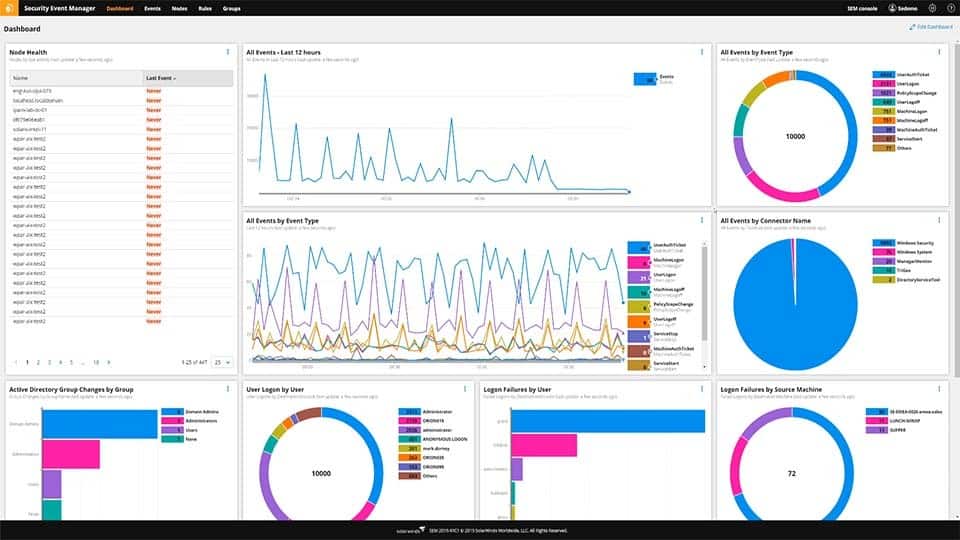
SolarWinds Security Event Manager is a log management and system security package that will help with compliance with PCI DSS, GLBA, SOX, NERC CIP, HIPAA, and other data privacy standards.
Key Features:
- Log collection and consolidation
- Log message filing and archiving
- SIEM tool
- Intrusion detection
- Compliance reporting
Why do we recommend it?
SolarWinds Security Event Manager is a log manager and SIEM system that includes compliance reporting. This is an on-premises package but it can also collect logs for cloud platforms. The service is able to process very large volumes of data but its efficiency relies on the capacity of server that you provide to host it.
This service is a SIEM system. It searches through log files for suspicious activities and organizes those logs so that they can be queried for compliance auditing. All log files are protected from tampering.
The package also includes a vulnerability scanner for risk assessment plus automated remediation mechanisms should a data loss event occur.
Who is it recommended for?
This is a solution for large businesses. The cost of hosting the software has to be added to the cost of acquiring the software – the package runs on Windows Server. The service can be tailored for compliance reporting for HIPAA, PCI DSS, SOX, FISMA, and GLBA, plus others.
Pros:
- Tailored for PCI DSS, GLBA, SOX, NERC CIP, and HIPAA
- Supports compliance auditing
- Anomaly detection
- Automated remediation
- Vulnerability scanner for risk assessment
Cons:
- No SaaS version
The Security Event Manager runs on Windows Server, and it is available for a 30-day free trial.