Data governance is a critical component of any organization’s data management strategy, ensuring that data is accurate, secure, and used in compliance with applicable regulations. With data becoming one of the most valuable assets for businesses, effective governance frameworks are essential for maximizing data’s potential while minimizing risks related to privacy breaches, non-compliance, and security vulnerabilities.
As organizations collect and manage vast amounts of sensitive and personal data, it’s crucial to implement proper data governance practices to maintain control over how data is handled throughout its lifecycle.\
We get into a lot of detail on data governance and the tools we include below, but in case you are short of time, here is our list of the best tools for data governance tools:
- ManageEngine ADAudit Plus EDITOR’S CHOICE Manages log files and produces standards compliance audits.
- Smartsheet Data governance project templates.
- SENF Locates sensitive data.
- N-able Cove Data Protection For data discovery, backup, and recovery.
- Blackberry Unified Endpoint Management Secures access to applications and data on all endpoints, including mobile devices.
- SolarWinds Access Rights Manager Controls document and resource access.
- OSSEC An intrusion prevention system.
- Symantec Data Loss Prevention Protects data from theft.
Our article provides a comprehensive overview of data governance principles, best practices, and the tools that organizations can use to ensure that data is properly managed, secure, and compliant. This guide serves as a valuable resource for businesses looking to strengthen their data governance framework, especially in light of evolving privacy laws such as the GDPR and CCPA, which require organizations to adhere to strict data handling and protection guidelines.
The guide covers the key elements of a strong data governance program, including data quality management, data security and privacy, data stewardship, and regulatory compliance. It emphasizes the importance of clearly defined roles and responsibilities for managing data across an organization, as well as the need for effective data governance policies and procedures to ensure consistency, accountability, and transparency.
In addition to the foundational concepts, the guide explores various data governance tools that can help organizations automate and streamline their data management efforts. These tools, including data catalogs, data lineage tools, and compliance management software, provide essential features for tracking data, ensuring data integrity, and maintaining compliance with privacy regulations.
As data governance becomes more complex due to increasing regulations and technological advancements, this guide offers valuable insights into how organizations can implement robust data governance practices and leverage tools to better manage their data assets while safeguarding privacy and meeting legal obligations.
There are three categories of threats to the data on your system:
- Outsider intrusion
- Insider theft
- Corruption or destruction
Data controls
Although your IT system is a very efficient automatic data processor, the way organizations store the information that feeds into it can be very haphazard. You will be surprised to learn that you probably do not know where all of your data is held.
When you move towards a data governance policy, you first need to locate all instances. You should decide whether to centralize all data or leave it in distributed locations. Either way, you need to back them up. You should create a backup strategy that decides the frequency of copying and whether those copies should be made available live, should be stored as versions of files, should be replacements of existing backups, and what recovery procedures you should implement. You should decide where those backups are kept and you need to ensure that they are secure.
Once you have gotten your data protection in place, you need to work out how data is going to be made available to employees, exactly who should be able to see it, who can change it, who can delete it, and who can copy it.
You also need to decide how long you should keep each category of data and how you should securely retire it.
Data loss protection vs data continuity vs data stewardship vs data governance
The section above outlines the tasks you need to perform in order to manage the data in your business. However, there are several terms that describe these responsibilities.
The protection of data from theft is called “data loss protection.” The backing up and recovery of data is called “business continuity.” “Data stewardship” is the practice of ensuring that no one is able to use the information that you store for purposes other than the explicit needs of your business. “Data governance” covers all of these data management processes.
A priority of data governance is to recognize the value of data. That is not just its value to you and your business, but also the value that it could have to others.
The value of data protection measures lies in the cost to the business of paying compensation to individuals should it be stolen and abused for malicious purposes. Another cost of data disclosure is the effect of legislation. Your business can be fined or shut down by the government if you don’t protect the data held about other businesses and private individuals. You and key employees could be imprisoned, and you could all be banned from holding positions of responsibility.
Loss of reputation is another potential cost of data loss and lack of correct data governance. Conversely, effective data governance assures trust in your brand, enhances your business’s reputation, and strengthens the enterprise’s money-making potential.
Implementing data governance
Data governance is implemented by tools. You should put in place automated procedures to manage your data and secure it rather than expecting a technician to implement the strategy manually. However, there are many variables within each task that need to be set. So, you will need to make a lot of decisions upfront about how you implement your data governance policy.
The key deliverable for data governance is a policy document. This should outline all of the requirements of the data management system that will be put into place. You will decide on the goals and time horizons for each area of management.
Examples of the type of decisions that you need to make include the number of “days data” that your company could afford to lose. This will dictate the frequency of backups. You should write out a policy for each category of the data that your company holds:
- Financial data
- Operational transaction data
- Business reference information (contracts and plans)
- Personally identifiable information
Your obligations for each type of data are different. You should also identify the data security standards that are relevant to your industry and domicile.
Data governance policy
The actual document that you will produce in your strategy phase is the data governance policy. A key point in this document is the definition of user roles for each category of data. First, you need to nominate a Chief Information Officer (CIO) and the technicians and administrators who will be in charge of implementing the data governance policy. This team is called the Data Governance Board and will carry out the work to create, refine, and implement the data governance policy.
Identify the job types that need to have data access. Each should have access rights to see, create, amend, or delete data. Keep in mind that sensitive data will be held in documents and database. The usage of each should be guided by applications, such as document management systems and data access screens – ensuring that no one gets direct access to data and that all actions that operate on your data stores are logged.
The exact steps that you need to implement data governance depend greatly on the type of data that your business handles. Create a project library for your governance policy, start off with an overview definition, and work down to more and more details. The Data Governance Institute proposes the following project framework:
Rules and Rules of Engagement
- Mission and Vision
- Goals, Governance Metrics and Success Measures, and Funding Strategies
- Data Rules and Definitions
- Decision Rights
- Accountabilities
- Controls
People and Organizational Bodies
- Data Stakeholders
- A Data Governance Office
- Data Stewards
Processes
- Proactive, Reactive, and Ongoing Data Governance Processes
Data governance implementation
The implementation of a data governance policy is called “data management.” The strategy needs to be integrated into day-to-day working practices and should be a specific process. The Data Governance Board will continue to monitor the effectiveness of the policy and make adjustments accordingly.
Your data management task will fall into the following categories:
- Data discovery
- Access rights management
- Access logging and log management
- Intrusion prevention
- Standards compliance auditing
- Data backup strategy
- Data recovery strategy
For each of these tasks, you will need an automated tool. You are unlikely to find a single data management tool that you like and that effectively performs all of the processes that you will need to implement. Look for a blend of separate tools that you can organize into your own data management suite.
Data management tools
Our methodology for selecting a data governance tool
We reviewed the market for services that enable you to supervise data privacy compliance and analyzed options based on the following criteria:
- Activity logging
- Sensitive data management
- User account management
- Log auditing facilities
- Compliance reporting automation
- A free trial or a demo package that provides a try-before-you-buy opportunity
- Good value for money that provides GRC functions and can be integrated into system monitoring tools
With these selection criteria in mind, we identified a shortlist of governance tools that can be tailored to track compliance with specific standards.
You can read more about these tools in the following sections.
1. ManageEngine ADAudit Plus (FREE TRIAL)
ManageEngine ADAudit Plus is a useful tool for implementing SOX, HIPAA, PCI DSS, FISMA, GDPR, and GLBA compliance. The “AD” in the name of the tool explains that this security system focuses on Active Directory. The tool monitors your AD implementation, logging any access to the permission database and backing up changes so that they can be reversed.
Key Features:
- Prevent unauthorized AD changed
- Permissions assessment
- Access rights tightening
- File integrity monitoring
Why do we recommend it?
ManageEngine ADAudit Plus provides user activity tracking and uses Active Directory as a user account reference. The service is an insider threat detection system and it also guards against account takeovers. The tool also protects AD domains from unauthorized changes and logs alterations to make them reversible.
The dashboard for the tool displays alerts every time permissions are changed or user records are added or deleted. ADAudit Plus logs can be archived and stored for three years, making them available to the tool’s reporting and auditing utility.
Who is it recommended for?
You would need to be using Active Directory or Azure AD as your access rights manager to use this tool. The service is particularly useful for compliance with GDPR, GLBA, FISMA, PCI DSS, or HIPAA. You will need to be running at least two domains to justify purchasing this system.
Pros:
- Detailed reporting, can generate compliance reports for all major standards (PCI, HIPAA, etc)
- Supports multiple domains, great for large enterprises
- Supports delegation for NOC or helpdesk teams
- Allows you to visually view share permissions and the details of security groups
Cons:
- Has a steeper learning curve than similar tools
This tool installs on Windows and is available in both free and paid editions. You can get a 30-day free trial of the Professional edition.
EDITOR'S CHOICE
ManageEngine is our top pick for a data governance tool because of its comprehensive features, user-friendly interface, and scalability for organizations of all sizes. It excels in managing and safeguarding sensitive data across various platforms, ensuring compliance with industry standards such as GDPR, HIPAA, and CCPA. The package’s Data Security & Privacy Management allows businesses to control access to sensitive data, ensuring only authorized users can view or modify it. This helps mitigate risks associated with data breaches and unauthorized access, offering a high level of security. Audit and reporting capabilities enable businesses to track and log user activities and data access. This feature is crucial for compliance audits and understanding how data is used and shared across an organization. Its Data Classification capabilities automatically tag and categorize sensitive data based on predefined policies, making it easier to enforce governance rules. Data Masking and Encryption further enhance data security, ensuring sensitive information is protected both in transit and at rest. ManageEngine’s ease of use, security, and compliance features make it a top-tier data governance tool for any organization.
Download: Get a 30-day FREE Trial
Official Site: https://www.manageengine.com/products/active-directory-audit/download.html
OS: Windows Server, AWS, and Azure
2. Smartsheet
Smartsheet is a team project library application. The tool includes template forms that are specifically written for data governance. You set a project mission and then follow through many layers of forms, assigning tasks with deadlines to different team members or groups.
Key Features:
- Adaptable online forms
- Library for compliance checklists
- Assignable tasks
Why do we recommend it?
Smartsheet is a flexible tool that can be used for workflow automation, task tracking, and request management. The system can be adapted by applying a template and there are templates available for data governance tasks. Data retention controls prevent the system from leaving data related to completed projects on the system.
The environment also includes planning utilities, such as critical path analysis and timeline estimates.
Who is it recommended for?
This package is primarily designed to schedule tasks and sequence together different processes, allocating responsibility for each to different people. The service can be adapted to so many uses that it is suitable for use by any type or size of business.
Pros:
- Designed specifically for data governance
- Offers many customization options
- Features solid team collaboration tools
- Dual-purpose, can use for managing other projects
Cons:
- Very manual process, would like to see more examples and templates for new users
- Can be tough to use without planning or guidance
Smartsheet isn’t just a data governance planning tool. You can use it to manage any project that your company takes on once the data governance project has been settled. It can even be used as a Help Desk management system. You can get a 30-day free trial of Smartsheet that will give you the opportunity to see the different business functions that it could support.
3. SENF
When you implement your data governance policy, your first task will be to locate all of the data on your system. If you hold personally-identifiable information, you will find SENF useful.
Key Features:
- Sensitive data locator
- Pattern searches
- Easy to manage
Why do we recommend it?
SENF is a free data scanner that can look for specific data patterns in the contents of files and databases. The system is intended for use as a sensitive data discovery service. For example, it can look for credit card numbers or social security numbers.
The program performs a system search for data format patterns, such as credit card numbers and social security numbers. The results report gives you the locations of these data instances.
Who is it recommended for?
The Sensitive Number Finder (SENF) is a searching tool but it doesn’t do much else. Therefore, you would need to pair it up with a data loss prevention service or a file integrity monitor in order to get full value out of this free tool. The program will run on Windows, macOS, and Linux.
Pros:
- Free to use
- Supports cross-platform functionality across Windows, Linux, and Mac OS
- Is easy to launch and doesn’t stress systems resources
Cons:
- Fairly limited in what it can do proactively
- Compared to newer tools, SENF is outdated in terms of functionality
- Was removed from GitHub, can be hard to find
“SENF” stands for “Sensitive Number Finder.” It is a free tool that was developed by the University of Texas at Austin’s Information Security Office – they still maintain and develop the program. SENF runs on Windows, Linux, Mac OS, and Unix. The software has been available on a GitHub repository but has been removed since this article was first published.
4. N-able Cove Data Protection
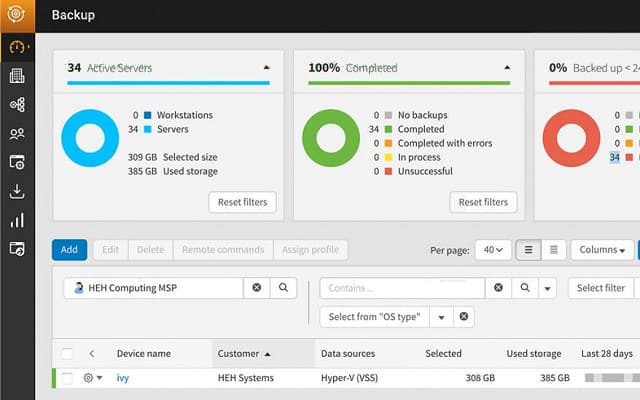
The N-able Cove Data Protection service combines backup management software and the storage space – the company operates data centers around the globe.
Key Features:
- Data backup system
- Cloud storage
- Made for managed service providers
Why do we recommend it?
N-able Cove Data Protection provides backup, archiving, and business continuity services. The package is a SaaS system that will back up on-premises data and also data held in Microsoft 365. The subscription includes storage space on the N-able cloud servers. Storage space is encrypted and mirrored for assurance.
Cloud storage is the best solution for backup – keeping copies on your own site risks both the original and backup being destroyed by environmental events.
Who is it recommended for?
The N-able brand provides products for use by managed service providers. The Cove Datra Protection system is intended for use by MSPs to back up the endpoints of their clients. One account can be divided into subaccounts, with each of those divisions holding the data of one client.
Pros:
- The interface is simple and easy to learn
- Designed with MSPs in mind, with multi-tenant features and reporting capabilities
- Scales well as a cloud-based application
- Can back up data from other cloud providers like OneDrive
Cons:
- N-able Cove Data Protection is a highly detailed tool designed for IT professionals and may take time to fully explore all features available
Data transfers are made quicker through compression. Data is protected by AES encryption, both in transit and in the cloud storage. Only your account has access to the decryption key, so even the data center staff is unable to read your records. The dashboard enables you to command data recovery to your site or to a different site. N-able offers a 30-day free trial of the Cove Data Protection service.
5. BlackBerry Unified Endpoint Management
Available for installation on site or as a Cloud service, this system manages mobile devices with Windows, macOS, iOS, Android, Windows Phone, and BlackBerry and also wearable devices and IoT equipment. You can configure devices en masse by device type or user function and create secure areas for corporate use on user-owned devices.
Key Features:
- Deployment options
- Endpoint configuration control
- Mobile device tracking
Different plans include different levels of functions. You can include mobile application management and mobile content management, which will protect the documents and data accessed from mobile devices. Other options include secure email, messaging, and collaboration software.
Pros:
- Sleek highly customizable interface
- Cross-platform support with Windows, Mac OS, Linux, Android, and iOS
- Available on-premise and as a cloud service
Cons:
- Would like to see more options for mobile security
- Message sync can delay emails
- Implementation is fairly complex when compared to similar solutions
Blackberry UEM can be assessed with a free trial.
6. SolarWinds Access Rights Manager
SolarWinds Access Rights Manager will give you a report of your current user community and the permissions granted to each person.
Key Features:
- Data loss prevention
- Active Directory auditing
- Reset security settings
- Access permissions controls
- Compliance reporting
Why do we recommend it?
SolarWinds Access Rights Manager is an on-premises package that provides a front end for Active Directory. This system lets you manage multiple domains from one dashboard and highlights problem accounts that weaken security. The package has a library of compliance reports for GDPR, PCI DSS, and HIPAA.
This is your starting point for the user management aspect of the data governance strategy. Once you have defined clear user groups, assigned individual accounts to groups, and set the permissions for each, you can implement that new policy through the Access Rights Manager.
Who is it recommended for?
This software package runs on Windows Server, which is ideal for coordinating with Active Directory. It is also able to administer Azure AD and other AD-dependent systems, such as Microsoft 365. The service is ideal for businesses that need to comply with GDPR, PCI DSS, and HIPAA.
Pros:
- Provides a clear look into permission and file structures through automatic mapping and visualizations
- Preconfigured reports make it easy to demonstrate compliance
- Any compliance issues are outlined after the scan and paired with remediation actions
- Sysadmins can customize access rights and control in Windows and other applications
Cons:
- SolarWinds Access Rights Manager is an in-depth platform designed for sysadmin which may take time to fully learn
The tool monitors Active Directory, Microsoft Exchange, Windows File Share, and SharePoint. The reporting module includes auditing for GDPR, HIPAA, and PCI DSS compliance. The software installs on Windows Server and you can get it on a 30-day free trial.
7. OSSEC
This open-source, free intrusion prevention system is owned by cybersecurity company, Trend Micro. The tool checks on details in log files and automatically takes action to block user accounts and transmission source IP addresses.
Key Features:
- Intrusion prevention system
- Detects malicious activity
- Community tips
The connection between a detected event and a remediation action is called a “policy.” It is possible to write these rules yourself. However, the active user community for the tool is a good source for pre-written policies. The community provides tips and tricks for OSSEC and you can buy a support package as an addition from Trend Micro.
OSSEC can be downloaded from GitHub and it runs on Unix, Linux, Mac OS, and Windows. There is no front end for this tool, but you can interface it with Kibana, Splunk, or Graylog.
Pros:
- Can be used on a wide range of operating systems, Linux, Windows, Unix, and Mac
- Can function as a combination SIEM and HIDS
- Interface is easy to customize and highly visual
- Community-built templates allow administrators to get started quickly
Cons:
- Requires secondary tools like Graylog and Kibana for further analysis
- Open-source version lacks paid support
8. Symantec Data Loss Prevention
Symantec Data Loss Prevention scans your system for sensitive data on installation. The software is driven by policies, which dictate the actions that the service will take on detection of unacceptable actions. These actions are all logged, which makes the auditing capabilities of the tool good for HIPAA, GDPR, and PCI DSS standards compliance.
Key Features:
- Spots malicious behavior
- Controls data access
- File copy tracking
Sensitive documents are encrypted and access to them is controlled by authentication. Copying, movement, and emailing of these files can be banned and you can fingerprint every copy when files are distributed, making it easy to detect the source of leaks. The system is also able, on command, to destroy files completely, leaving no traces on the device. The tool includes user tracking, which is useful if you need to investigate an account that has triggered an alert through suspicious activity.
Pros:
- Combines DLP with user activity tracking, giving it additional functionality
- Automatic scanning can map out sensitive locations where data is stored
- Offers pre-built temples and works flow for major compliance standards, offering good out-of-box functionality
- Supports file integrity monitoring through a fingerprinting system
Cons:
- Could integrate better with other Symantec tools
- Need better Mac functionality
Data governance FAQs
What are data governance tools?
A data governance tool is a system that enables the creation and enforcement of data security and privacy policies. These tools track events that occur on data and record them for data privacy auditing as well as control access.
What is data governance?
Data governance applies security and privacy rules to data access events. For example, your business might operate in the health care sector and need to comply with HIPAA in order to attract business. In this case, you would need to ensure that the HIPAA requirements are enforced throughout your organization. Another example comes from businesses that accept credit card payments. In this case, the business would set its data governance policy so that it enforces compliance with the PCI DSS standard.
What is data governance in ETL?
Extract, transform, load (ETL) involves moving or copying data from one location to another and also altering the format or context of that data in the process. This can be problematic for compliance with data privacy standards because you have to maintain the integrity of data. The meaning of the data’s original context has to be preserved in order to keep a proper and truthful record. Your data governance standard should ensure that the meaning of the data isn’t altered by changing its context during ETL processes.
What is a data governance solution?
A data governance solution is a software package that contributes towards the enforcement of data protection standards within a business. A service does not need to be a complete, closed-loop system in order to qualify as a data governance solution. It can make a partial contribution to the overall data governance enforcement strategy of the business and still be regarded as a data governance solution.