Managing third-party risks has become a crucial aspect of maintaining data security and regulatory compliance. Organizations increasingly rely on external vendors, contractors, and service providers to support various operations, but this dependency also introduces significant risks to their data and systems. Third-party risk management (TPRM) software is designed to help businesses assess, monitor, and mitigate risks arising from their third-party relationships.
Here is our list of the best third-party risk management software:
- OneTrust Third-Party Risk Exchange EDITOR’S CHOICE A risk management platform with completed assessments supplied by other clients. This system is constantly updated and includes assessments of more than 70,000 companies.
- SpyCloud Third Party Insight This service assesses account takeover risk and has a special module for third-party ATO risk.
- SureCloud A third-party risk management platform that is questionnaire-driven and is part of a compliance management package.
- Riskonnect Third-Party Risk Management A supplier vetting portal that imposes a risk management framework on third-party assessments.
You can read more about each of these options in the following sections.
These tools are vital for identifying vulnerabilities in supply chains, ensuring that vendors meet security requirements, and safeguarding sensitive data against potential breaches.
Third-party risk management software offers organizations a comprehensive solution to evaluate the security posture of their partners and vendors. These platforms allow businesses to assess and monitor vendor risk factors, such as cybersecurity, regulatory compliance, and operational performance, through questionnaires, audits, and continuous monitoring. By implementing TPRM software, organizations can proactively identify and address risks before they escalate into serious security incidents.
With the increasing complexity of the global supply chain and the growing threat of cyberattacks, having a robust third-party risk management strategy is critical for protecting valuable data and ensuring business continuity. TPRM software helps businesses assess potential risks at the outset of vendor relationships and continue monitoring those risks throughout the partnership.
Many of these tools also enable automated reporting, allowing organizations to stay up-to-date with any changes in their risk landscape and take necessary actions to remain compliant with industry regulations.
In this article, we will examine the best third-party risk management software available today, highlighting their key features, benefits, and how they can help businesses effectively mitigate the risks associated with third-party relationships.
The need for risk management in IT systems
The legal landscape faced by businesses has evolved rapidly in recent years. The General Data Protection Regulation (GDPR) and the ePrivacy Directive of the EU have been implemented as laws in every EU nation. These govern the use of PII and also specify the rights of individuals. Individuals have the right to request information on what data organizations hold on to. They also have the right to demand that mistakes are corrected or that data related to them be removed. GDPR also specifies that permission needs to be sought to send the PII of EU citizens outside of the EU.
GDPR enables individuals to seek compensation for the abuse of PII, which includes accidental disclosure of information. Governments can also fine businesses for such accidental disclosure. The Directive specifies a maximum fine of €20 million (about £17 million or $24.5 million) or 4% of annual global turnover. Those limits can be lower in the national legislation that implements GDPR.
Note that the fine can be up to 4 percent of turnover, not profit, and there is no free pass for businesses that have already been fined once in a financial year. Consumer compensation can be sought on top of those fines. Therefore, a data loss event can be ruinous. This gives businesses that want to trade within the EU a big incentive to take every measure possible to prevent data disclosure or inappropriate use of PII.
Since GDPR, other areas of the world have implemented their data protection legislation. These include the California Consumer Privacy Act (CCPA), Brazil’s Lei Geral de Proteção de Dados (LGPD), Canada’s Personal Information Protection and Electronic Documents Act (PIPEDA), and South Africa’s Protection of Personal Information Act (POPIA). In the USA, there are additional data protection rules for payment card details (PCI DSS) and protected health information (HIPAA).
The difference between third party risk management and vendor risk management
Vendor risk management is a type of third-party risk management. For many businesses, third-party assessment only needs to go as far as vendor risk management. For example, service providers need to assess risk in their systems and those of their suppliers but they don’t need to audit the systems of their clients.
Probably the biggest incidence of a third party that isn’t a supplier would be a franchisee. However, the franchisor can be seen as a supplier. In both cases, the franchisee and the franchisor are third parties to each other. Another example of companies that are associated without a traditional supplier-client relationship is a joint development partnership. Another mutual relationship between companies is formed during a takeover or a merger.
Implementing third-party risk assessment
The typical risk assessment process centers around a questionnaire. This form provides a standard assessment format, ensuring that all vendors are treated equally. The most common format for the assessment form is called the Standardized Information Gathering questionnaire, or SIG.
A proper assessment will require information from a third party, so it is better to get someone at that company to fill out the SIG for you. The sales team or contract department will be happy to do this because companies that are involved in providing IT systems are aware of the requirement for risk assessment in most data protection standards. They wouldn’t get much business if they didn’t already have all of the relevant information in hand for the SIG.
The third-party risk assessment platform provides an index for documents related to each company being audited. Each profile will also include slots for certification copes and audit assessment results. Some risk assessment systems include a method for SIG pooling, which allows many clients to benefit from the same effort to compile one SIG.
If you subscribe to a SIG sharing service, you need to ensure that the assessment is recent or recently updated. Some providers perform that assessment process for you and will keep an eye out for developments with each registered third party.
The best third-party risk management software
There are many choices in the risk assessment market for third-party risk management because this is becoming an essential service for a large number of companies.
What should you look for in a third-party risk management system?
We reviewed the market for third-party risk management software and analyzed the options based on the following criteria:
- A system that collects all necessary documentation for each assessed company in one profile
- A framework that is supported by a legal team
- An assessment format that can be adapted to specific standards
- An assessment system that is part of a wider governance and compliance platform
- Risk assessment that is constantly updated
- A free trial or another method for a risk-free assessment
- A service that is priced appropriately given the value of the modules it provides
As well as following the above selection criteria, we made sure to identify services that cater to all budgets.
1. OneTrust Third-Party Risk Exchange
OneTrust Third-Party Risk Exchange is a member-driven SIG database that gives access to assessments carried out by other companies and by OneTrust consultants.
Key Features:
- Global SIG Database: Offers access to a vast, member-driven database of Standardized Information Gathering (SIG) assessments, providing insights into third-party risks.
- Crowdsourced Information: Leverages assessments conducted by other companies and OneTrust consultants to compile comprehensive vendor risk profiles.
- Comprehensive Risk Records: Includes detailed records of data breaches, failed compliance audits, and rankings of company safety to inform risk assessment decisions.
Why do we recommend it?
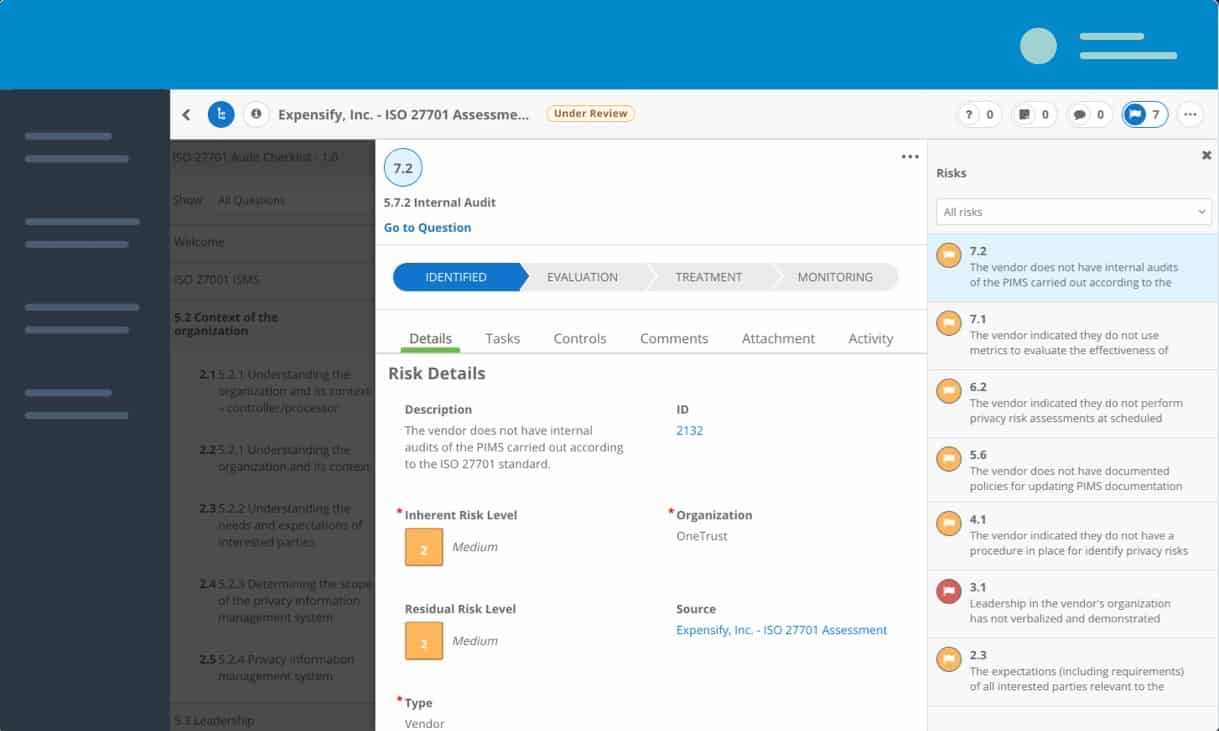
The OneTrust Third-Party Risk Exchange lets you read through a database of vendor risk scorings and also search through the records. The system can also transfer data directly into your own third-party risk management system. Each score rating is explained by detailed categories, relating to risk type.
OneTrust is a leader in governance, risk management, and compliance. The company runs a consultancy that performs risk assessments for companies both to check their internal risks and their third-party risks. The innovation of storing these risk assessments in a database and making them available to subscribers creates very cost-effective re-use of OneTrust expertise.
The vendor assessments don’t stop at first-tier suppliers. Risk analysis reveals which providers rely on other companies to create their products, so it builds up a hierarchy of suppliers. Each supplier will have a SIG in the database, so subscribers get to see through the supply chain to fully understand dependencies and build up a full risk landscape.
SIGs that assess more than 70.000 vendors are registered in the Vendorpedia Third-Party Risk Exchange database. The service is cloud-based and the dashboard is accessed through any standard browser. The console includes data querying tools to help you locate records and you are then able to store collections of documents that create a profile for each of your suppliers and their suppliers. This package of analytical tools is called OneTrust DataGuidance and it provides the expertise you need to fully benefit from the Vendorpedia database.
The risk assessment document base that you create in the system will help you with proof of compliance to NIST, HIPAA, PCI DSS, GDPR, EBA, CCPA. Creating a profile for a company in your user account doesn’t copy over information and store it separately, Instead, you get a view on a shared document, so when a SIG gets updated, you instantly get the latest version.
OneTrust consultants moderate and check through the data held in the Vendorpedia database; it isn’t a complete free-for-all. So, you get verified and valid data on all suppliers, not just someone else’s opinion. The risk assessments in Vendorpedia relate to each product of a company, not just the company. This accounts for the fact that different products will be based on a different supply chain and so have different risk profiles.
Who is it recommended for?
This service is suitable for businesses of all sizes. The Exchange is an efficient way for businesses to share information and cut down the time it takes to perform third-party risk assessments, which usually involves sending suppliers questionnaires. You can create profiles for your vendors, which will trigger alerts if new information becomes available.
Pros:
- Efficient Risk Assessment: Streamlines the process of third-party risk assessment by offering pre-compiled, detailed evaluations of potential and current vendors.
- Depth of Supply Chain Insight: Reveals dependencies within supply chains by analyzing the risk profiles of both direct suppliers and their subcontractors.
- Real-Time Information Updating: Ensures the latest risk assessment data is always available, thanks to shared documents that update instantly when SIGs are revised.
- Compliance Support: Facilitates proof of compliance with various standards like NIST, HIPAA, PCI DSS, GDPR, EBA, and CCPA, enhancing regulatory adherence.
- Verified Data Quality: Maintains high-quality, reliable information through moderation and verification by OneTrust consultants, ensuring the validity of the data provided.
- Product-Specific Assessments: Recognizes that different products may have different risk profiles based on their unique supply chains, offering precise risk analysis.
Cons:
- Product-Specific Focus: Each assessment is tied to specific products and their supply chains rather than providing an overarching evaluation of the company, which may require additional research for a complete risk picture.
You can request a demo to get a full understanding of the Risk Exchange system.
EDITOR’S CHOICE
OneTrust Third-Party Risk Exchange is our top pick for third-party risk management because it leverages the expertise of OneTrust’s expertise and the assessments already performed for other companies. This is an excellent way to get risk assessments on your suppliers and their products without having to go through the time-consuming process of creating SIGs yourself. Guidance within the cloud-based console ensures that you get a full risk assessment without having to have years of experience in the field.
Request a demo: onetrust.com/products/third-party-risk-exchange
Operating system: Cloud-based
2. SpyCloud Third Party Insight
The SpyCloud risk assessor is a little different from the others on this list. The SpyCloud service focuses on Account Takeover Risk (ATO). The ATO problem damages your company’s data protection standing through the malicious actions of insiders or user carelessness with login credentials. Just as this service can assess the risks within your own company, it can assess those risks within the providers of your essential software and services.
Key Features:
- Focus on Account Takeover Risk (ATO): Specifically addresses risks related to account takeovers, assessing both internal and third-party vulnerabilities to unauthorized access.
- Risk of Data Theft Assessment: Evaluates the potential risk of data theft within your company and your third-party vendors, focusing on security practices around login credentials.
- Vendor Security Success Assessment: Analyzes the effectiveness of security measures implemented by software and hardware providers, offering insights into their ability to protect against ATO.
Why do we recommend it?
SpyCloud Third Party Insight works on hacker community inquiries rather than shared risk assessments. The company suggests that once they notify you of a breach at a supplier you will need to tell that company about the problem as well. This extends the ATO detection operating in your own business.
Many executives are reluctant to work with outsourcing and cloud services because they worry about losing control over system security while still having to bear the responsibility for data loss events. SpyCloud solves that problem. You can at least assure the board that the companies that your IT department deals with are protected against account takeover.
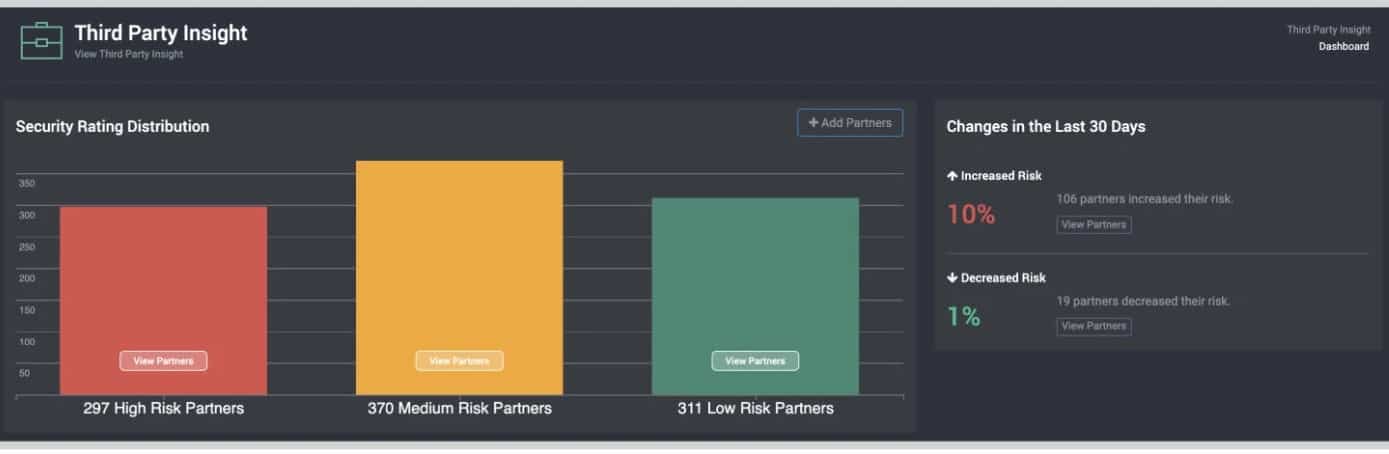
SpyCloud Third Party Insight scans information sources for reports of data breaches at your list of associated businesses and suppliers. Essentially, this is a data breach news feed that is collated into a presentable format through the SpyCloud dashboard. This entire system is hosted in the cloud.
Who is it recommended for?
This is a good choice for businesses that rely on cloud services. The platform focuses on account takeovers, which are particular problems for IT businesses and so your SaaS systems and virtual server providers are particularly vulnerable to such a risk. The platform also provides protection for your own company.
Pros:
- Specialized Risk Analysis: Uniquely concentrates on the significant issue of account takeover, offering targeted insights that other general risk assessment tools might overlook.
- Actionable Intelligence: Provides detailed information on data breaches and security lapses at associated businesses and suppliers, enabling proactive security measures.
- Cloud-Based Dashboard: Offers a centralized, cloud-hosted platform for monitoring and managing third-party account takeover risks, enhancing accessibility and usability.
- Trial Access: Allows users to conduct a free search, giving businesses an opportunity to evaluate the service’s effectiveness before making a financial commitment.
- Comprehensive Data Collection: Gathers risk information from a wide array of sources, ensuring a broad perspective on third-party risks related to account security.
Cons:
- Notification Responsibility: Indicates that users may need to inform their suppliers about breaches, adding an extra step to the risk management process.
- Potential Delay in Consultant-Provided Searches: While offering a depth of analysis, the turnaround time for detailed, consultant-driven searches can extend, potentially impacting timely decision-making.
You can get a demo of SpyCloud Third Party Insight to scope the service for yourself.
3. SureCloud
SureCloud is a cloud platform that offers a package of governance, risk management, and compliance functions. These services include a third-party risk management module.
Key Features:
- Guided Risk Assessment Workflows: Streamlines the process of conducting in-depth investigations into third-party vendors with structured workflows and checklists.
- Questionnaire-Based Data Collection: Utilizes customizable questionnaires to systematically gather necessary information directly from suppliers.
- Comprehensive GRC Integration: Part of a broader suite of governance, risk management, and compliance tools, facilitating a unified approach to enterprise risk.
Why do we recommend it?
The Third Party Risk Management service of SureCloud is part of a wider platform of GRC tools this is a questionnaire-based data-gathering system that relies on the cooperation of your suppliers to provide answers. As such, it operates as a digitized repository of your vendor risk inquiries.
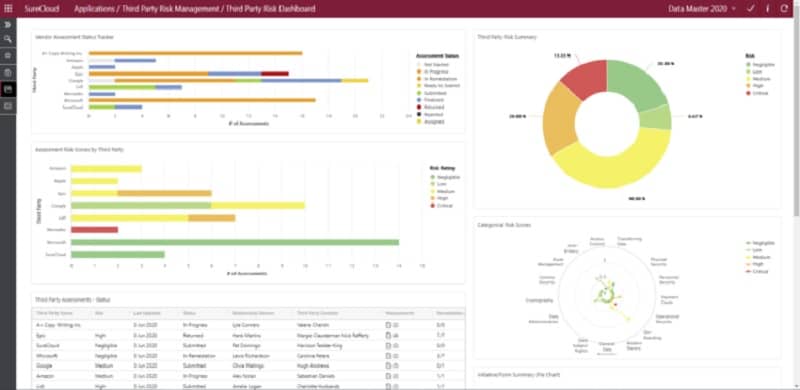
The Third-Party Risk Management software system in SureCloud creates a central interface to your vendor assessment and risk management documentation. The dashboard includes questionnaire templates that guide how to collect relevant data on suppliers and their products, plus the other businesses that contribute to the production of those products.
The SureCloud system is available in three plans. The lower edition, called Standard, is better suited to businesses that have in-house risk assessment expertise. Although this plan provides a structure that helps you organize your risk assessments, it doesn’t have much process automation in it. The guided workflows for risk assessment and third-party risk management are only available in the two higher plans, which are Business and Premium.
Like most third-party risk management systems, the SureCloud system is based around SIG questionnaires. These give you a strategy to work to, making sure that you research and check all of the relevant data that you will need to verify your suppliers and ensure that you minimize risk.
SureCloud Third-Party Risk Management system also offers the option of an add-on service, called BitSight for an additional fee. BitSight is a database of risk assessment data on many companies and cuts short the research process that you have to go through by providing all of the necessary data.
Who is it recommended for?
This service is suitable for businesses that have a GRC team on staff. The service requires human involvement because it is more of a guide and a document store than an automated data-gathering system or an intelligence feed. The service provides reporting formats for progress and goal measurement.
Pros:
- Structured Vendor Assessment: Provides a coherent framework for organizing and conducting third-party risk assessments, enhancing the efficiency and thoroughness of the process.
- Template-Driven Approach: Offers questionnaire templates that standardize the data collection process, ensuring all relevant aspects of vendor risk are covered.
- Flexible Plan Options: Available in three distinct plans (Standard, Business, and Premium), catering to varying levels of automation and support needs.
- BitSight Integration: Offers the option to integrate with BitSight for enriched risk data, streamlining the research phase by accessing pre-compiled vendor risk profiles.
Cons:
- Requires Active Supplier Participation: Relies on the willingness and responsiveness of suppliers to fill out questionnaires, which could delay the assessment process.
- Additional Cost for Database Access: The valuable integration with BitSight and access to a comprehensive database of SIGs incurs extra fees, potentially elevating the overall cost.
- Designed for GRC Teams: Best suited for organizations with dedicated governance, risk, and compliance personnel, as it necessitates significant user involvement for effective management.
You can request a demo to see the SureCloud Third-Party Risk Management system for yourself.
4. Riskonnect Third-Party Risk Management
Riskonnect Third-Party Risk Management is a cloud system that gives you a console for managing all risk-related issues when dealing with suppliers and other third parties. This can be seen as a mediation platform because it lets you communicate with potential suppliers in a standardized format that imposes a framework and a workflow for completing assessments.
Key Features:
- Cloud-Based Management Console: Facilitates centralized management of third-party risks, accessible from anywhere.
- Comprehensive Risk Assessment Guidance: Offers structured workflows and frameworks for thorough evaluation of potential and current suppliers.
- SLA and Contract Management: Integrates functionalities for tracking and managing service level agreements and contracts to ensure compliance and performance standards are met.
Why do we recommend it?
Riskonnect Third-Party Risk Management is a module on the Riskonnect GRC platform. The service is intended for use as an assessor for potential suppliers as well as a risk scoring system for current vendors. The platform includes options to manage ESG compliance as well as data protection risk.
The Riskonnect system doesn’t stop as supplier assessments. It also manages the formulation of contracts and SLAs so that your business can be reassured that the risks of taking on a product or service have been minimized.
Fortunately, most suppliers in the field of data processing are well aware of standards requirements and have certification gained through regular compliance auditing. The documentary evidence of this status goes a long way to removing risk. However, assessments have to be reimplemented periodically and the Riskonnect service includes a calendar that will alert you when it is time to recontact suppliers for confirmation of their ongoing compliance status.
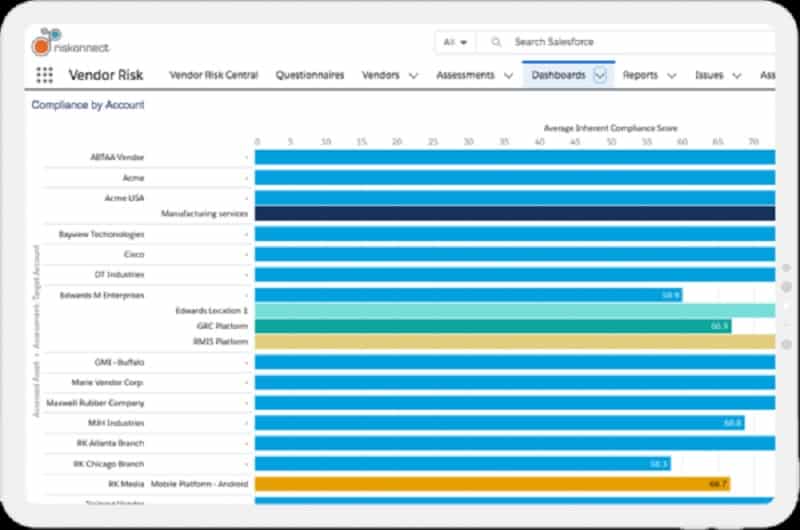
Riskconnect calculates a risk ranking for each of the companies that you enter into the system. Analytical tools in the system let you categorize the products that you use and their providers so you can focus scrutiny on those businesses that would impact your standard compliance.
Who is it recommended for?
This is a big system for large companies. The system manages the request for information from third parties through a digital form and stores the results in a database. So, it is suitable for use by companies that have a GRC team in place. The Riskonnect platform is evolving more into its ESG management services.
Pros:
- Holistic Supplier Evaluation: Enables businesses to assess not just the immediate compliance and risk posture of suppliers but also to consider broader ESG compliance impacts.
- Automated Reassessment Notifications: Features a calendar system that alerts users to the need for periodic reassessment of suppliers, ensuring continuous compliance.
- Risk Ranking System: Assigns risk scores to each third party in the system, providing clear visibility into which relationships pose the greatest risk to the organization.
- Versatile GRC Integration: As part of the broader Riskonnect GRC platform, it allows for a unified approach to governance, risk management, and compliance, enhancing overall risk posture.
Cons:
- Designed for Larger Enterprises: The scope and scale of the platform are best suited for large companies with specific GRC teams, potentially making it less accessible for smaller businesses.
You can request a demo of the Riskonnect system to assess it for yourself.