SOC stands for Security Operations Center. That sounds like mission control, probably darkened, with a large screen all around and lots of serious people sitting at consoles full of buttons and dials.
Well, many years ago, that’s what a SOC looked like. Nowadays, thanks to advancements in task automation, the SOC is probably one person sitting at a PC.
Here is our list of the best SOC software tools:
- ManageEngine Log360 (FREE TRIAL) This large bundle of services includes a SIEM, a threat intelligence feed, UEBA, file integrity monitoring, AD auditing, log management, compliance reporting, and a SOAR service. Runs on Windows Server. Start a 30-day free trial.
- LogRhythm XDR Stack A combination of four layers of security that ranges from endpoint protection through to automated threat response. They are offered as a cloud service, as an appliance, or as software for Windows Server.
- Rapid7 Insight Platform A bundle of cloud-based automated security services with onsite agents, includes threat detection and automatic response.
- Heimdal Threat Hunting and Action Center This SaaS platform provides coordinated threat protection across all the endpoints of an enterprise with hybrid cloud/local threat detection.
- TrendMicro XDR A package of coordinating cybersecurity tools that include a SIEM, email security, and threat response. This is a cloud-based system.
- Exabeam A cloud-based next-generation SIEM that includes threat intelligence and automated threat response.
You can read more about each of these options in the following sections.
A Security Operations Center (SOC) is a dedicated facility or team within an organization responsible for continuously monitoring, detecting, analyzing, and responding to cybersecurity threats and incidents. The primary goal of a SOC is to safeguard an organization’s digital infrastructure, assets, and sensitive data by proactively managing and mitigating security risks. SOC teams use a combination of people, processes, and technologies to ensure rapid detection of security threats and efficient incident response.
The core tasks of a SOC include:
- Threat Monitoring: Continuously monitoring network traffic, endpoints, servers, and systems for suspicious activities or potential security breaches.
- Incident Detection: Identifying and analyzing security incidents, such as malware attacks, unauthorized access, or data breaches.
- Incident Response: Coordinating the response to security incidents, including containment, investigation, and remediation.
- Threat Intelligence: Collecting and analyzing threat intelligence to stay ahead of emerging cyber threats.
- Vulnerability Management: Identifying and addressing system vulnerabilities that could be exploited by attackers.
- Reporting and Compliance: Ensuring compliance with industry standards and regulations by generating security reports and maintaining audit trails.
While larger organizations typically operate an in-house SOC, outsourcing is also a viable option for many businesses, especially smaller or mid-sized ones that lack the resources for a full-scale internal team. Managed Security Service Providers (MSSPs) offer outsourced SOC services, providing round-the-clock monitoring and incident management at a lower cost. Outsourcing a SOC can offer expert-level security management without the need for maintaining an in-house team, making it an attractive option for many organizations.
SOC tools
The type of tools you need for your SOC depends on the size of your operations. The core systems a SOC needs are security monitoring systems. If you have a team working in the SOC, you will also need team management systems and incident management tools. If you run a small enterprise and leave security monitoring to automated software, then you should look for detection and response systems tied up in one bundle.
The tasks that you need to get software for are:
- Vulnerability management
- Penetration testing
- Access right management
- Endpoint protection
- Firewall and network security
- Security information and event management
- Incident response
- Privacy standards compliance
This is a long list of tasks. However, there are cybersecurity software bundles available that provide all of these services. A good indicator of a competent SOC package is the term “XDR.” This stands for “extended detection and response.” An XDR package could be bundled around an endpoint detection and response (EDR) system, which itself is an advancement on the original antimalware systems that formed the mainstay of IT security systems back in the day. Other XDR packages start around SIEM tools. SIEM has the added advantage of providing log management, which is essential for businesses working to a data privacy standard, such as PCI DSS or HIPAA.
The best SOC software tools
If you want to combine your security monitoring requirements with general system management, you are into SecOps territory. You should get a security package that will monitor everything without much human intervention. You need the system to issue an alert when problems are detected. Knowing that you will be notified tells you that everything is going OK if you don’t receive any notifications. Automated responses also take a lot of responsibility off your shoulders.
What should you look for in a SOC tool?
We reviewed the market for SOC software and analyzed the options based on the following criteria:
- An automated system that covers all aspects of IT security
- Alerts and notifications for detected intrusions
- Network and endpoint protection
- Log management for standards compliance
- Vulnerability scanning and system hardening
- A free trial or a demo system for a no-risk assessment
- A valuable package of tools that combines all of the tools you need for system security
Getting a SOC software package saves you time in trialing many different systems for each security monitoring function and works out cheaper.
1. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 includes a lot of security monitoring and threat response services. The core of the threat detection service in this package is a SIEM tool. This is paired with its own log manager, which collects data from all endpoints plus third-party applications. The system also has a threat intelligence feed, which provides a blacklist of IP addresses and domains known to be used by attackers.
Key Features:
- Comprehensive SIEM Solution: Includes log management and threat detection.
- File Integrity Monitoring: Keeps track of important system files for security.
- Activity Logging: Provides detailed records of system and user activities.
Why do we recommend it?
ManageEngine Log360 examines user accounts and identifies misuse. Tools in this system include Active Directory auditing scanners that identify unauthorized changes and also assess weak account security, such as open-ended password validity or abandoned accounts. The system is able to track the activity of each user account and generate a baseline of regular activity.
The service also watches all behavior on endpoints and uses that for baselining. The system performs anomaly detection so any deviations from normal behavior raises an alarm. The tool will log unusual activity, particularly in relation to files because the system includes a file integrity monitor.
The package collects activity reports and logs from cloud platforms. Access to cloud services and the usage of cloud packages are governed by a cloud access security broker (CASB). A security orchestration, automation, and response (SOAR) module ties together all of the units in the bundle plus third-party security systems so that responses to detected threats are automatic and coordinated.
Who is it recommended for?
This package makes it onto our list because it is recommended for use by a Security Operations Center. It would also be a good choice for a managed security service provider (MSSP). This is a big bundle of tools that needs a team to manage. It isn’t suitable for small businesses.
Pros:
- Extensive Log Management: Covers a wide range of log sources and types.
- Integrated Threat Intelligence Feed: Enhances security awareness and response.
Cons:
- Complex Setup: May require significant time and resources to fully deploy.
ManageEngine Log360 provides compliance reporting for PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA. The software package for the bundle runs on Windows Server and you can access it with a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Log360 is our top pick for a SOC software tool because it provides a comprehensive SIEM service that is designed to help security teams monitor, detect, and respond to threats in real time. It integrates capabilities like log management, user behavior analytics, and event correlation, making it a strong candidate for use in Security Operations Centers (SOCs). One of its core strengths is centralized log management, allowing SOC analysts to collect and analyze logs from diverse sources such as servers, applications, firewalls, and cloud services. This aids in threat detection and compliance reporting. Log360’s real-time event correlation feature is particularly effective in detecting anomalies by linking disparate security events and generating actionable alerts. The tool also offers robust user behavior analytics (UBA), which helps identify insider threats or compromised accounts by monitoring deviations from normal user activity. Furthermore, its automated threat detection and response capabilities, including workflows for security incidents, enhance the SOC’s efficiency in mitigating potential breaches.
Download: Get a 30-day free trial
Official Site: https://www.manageengine.com/log-management/download.html
OS: Windows Server
2. LogRhythm XDR Stack
LogRhythm XDR is a SaaS package that is built around a SIEM. As the processing module of the SIEM is based in the cloud, the system needs onsite elements to gather log data and upload it. This configuration leads to the concept of a stack.
Key Features:
- Modular Security Platform: Offers customizable security components.
- Behavior Analytics: Employs advanced analytics for threat detection.
- Integrated SIEM: Provides comprehensive security event management.
Why do we recommend it?
LogRhythm XDR could be described as a SIEM. It is a cloud-based system that installs agents onto monitored systems and those units collect log files to upload to the threat-hunting module. Automated responses are implemented through SOAR, which means that the tool interacts with third-party products such as firewalls and access rights managers to block malicious activity.
SIEM systems combine log file analysis with live network monitoring. The strategy aims to spot anomalous behavior either in network traffic or on endpoints. The endpoint agent that gathers logs and uploads them to the LogRhythm server is called UserXDR, and the network monitor is called Network XDR.
The SIEM is divided into a log consolidator, called AnalytiX, and a threat detection system called DetectX. The DetectX system uses AI-based UEBA and a threat intelligence feed to identify a possible intrusion. That threat intelligence is collated from shared experiences of other LogRhythm XDR clients. The threat response is provided by RespondX, which uses SOAR to interact with other services, such as Active Directory and firewalls, to shut down hacker activity.
Who is it recommended for?
LogRhythm XDR is an almost entirely cloud-based system. The package has almost no footprint on local systems – unlike Falcon, which has the Prevent module that can operate autonomously. The LogRhythm system could be disabled by malware that disconnects a target computer from the internet.
Pros:
- Cloud and On-Premises Flexibility: Supports various deployment options.
- Advanced Threat Detection: Utilizes modern technologies for security insights.
Cons:
- Requires External Security Tools Integration: Additional effort needed for complete protection.
LogRhythm XDR is available as IaaS (Infrastructure as a Service) on the cloud, as on-premises software for Windows Server, or as a network appliance. In any of these options, the package offered by LogRhythm will provide you with all of the SOC tools you need to keep your system secure.
3. Rapid7 Insight Platform
Rapid7 Insight provides a bundle of security systems that supply a complete set of SOC tools. The core of this package is a SIEM system called InsightIDR, which is delivered from the cloud. IDR stands for Incident Detection and Response. The system requires agents to be installed on-site to gather log messages and upload them to the Rapid7 server.
Key Features:
- Cloud-Based SIEM: Streamlines security event management.
- Automated Detection and Response: Enhances overall security posture.
- Integrated Security Services: Offers a range of complementary security tools.
Why do we recommend it?
Rapid7 Insight is almost identical to LogRhythm XDR in that local agents upload log files for threat hunting in the cloud and responses are implemented by SOAR. Both systems also use user and entity behavior analytics to spot anomalous behavior and detect zero-day attacks.
InsightIDR collects log messages and consolidates them into a standard format. It then applies UEBA to register normal patterns of behavior on the monitored system. Deviations from this norm raise alerts and trigger closer scrutiny of a user account, a device, or traffic from a particular IP address. The system also uses a database of known hacker attack strategies called Attack Behavior Analytics (ABA).
The attack response mechanism in the InsightIDR system is called Insight Connect. This uses SOAR methods to coordinate mitigation actions, such as blocking an IP address or suspending a user account.
Who is it recommended for?
Potential buyers of Rapid7 Insight should also consider Falcon Insight and LogRhythm XDR as three very similar products. Of these three, Falcon is probably a stronger candidate because it can continue to operate on endpoints that are cut off from the local network and the internet.
Pros:
- User-Friendly Interface: Simplifies security monitoring and management.
- Flexible Deployment Options: Adapts to different organizational needs.
Cons:
- Potentially Overwhelming for Small Teams: Extensive features may require dedicated resources.
The Insight platform also includes InsightVM, a vulnerability manager that scans all devices on a network and its endpoints, looking for weaknesses that hackers exploit. If you use cloud services, you would also subscribe to DivvyCloud, which protects cloud-based assets. Another SOC tool that could be of interest to you is Insight AppSec, which monitors DevOps environments.
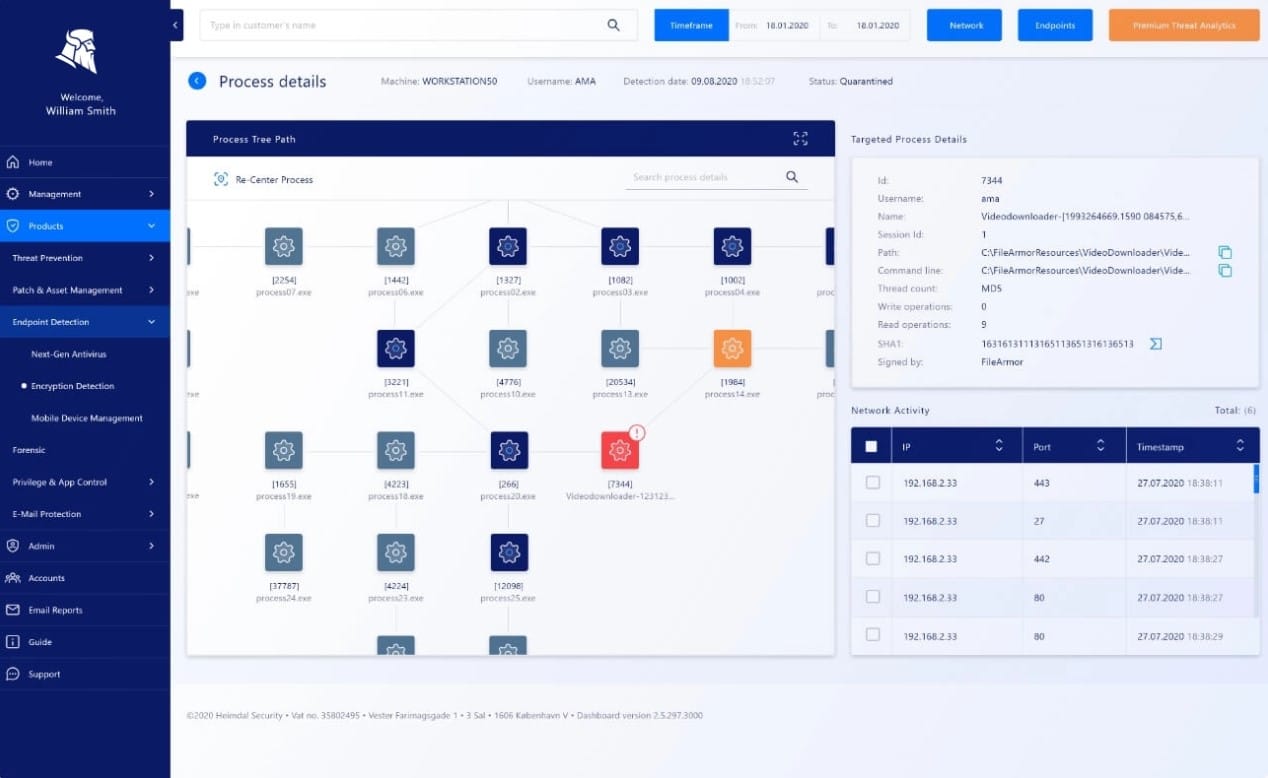
4. Heimdal Threat Hunting and Action Center
Heimdal Threat Hunting and Action Center operates from a cloud server but installs agents on monitored endpoints. These agents are available for Windows, macOS, and Linux.
Key Features:
- Anomaly Detection: Identifies unusual patterns indicating potential threats.
- Automated Responses: Quickly reacts to identified security issues.
- Security Consultancy Advice: Offers expert insights for security enhancement.
Why do we recommend it?
There are three layers to the Heimdal Threat Hunting and Action Center solution. The agent is the first of these – it uploads local event data to the cloud server for threat hunting. That cloud server is the second element and it sends response instructions to the endpoint agents when a threat is detected. The third element is the security consultancy team, who will advise you on ways to fine tune your automated security policies.
The cloud server standardizes all of the log messages that device agents send so that they are in a common format. It then performs its threat hunting on this standardized data. The package will indicate a threat with an alert and optionally send instructions to endpoint agents to block the threat.
The server identifies each user account, external source, and endpoint and records a pattern of regular activity in each dimension. If a user suddenly does something different or if an endpoint shows unusual activity, the Heimdal system registers a security event. This strategy is called user and entity behavior analytics (UEBA).
The Heimdal system is able to coordinate with third-party security tools such as access rights managers and firewalls. This interfacing is used both to gather event data and also to shut down threats.
Who is it recommended for?
Heimdal Threat Hunting and Action Center is a flexible package that is finalized through a consultation. The involvement of the Heimdal technicians can be increased according to the client’s requirements. Therefore if you have your own technicians on the payroll who have good system administration skills but weak cybersecurity knowledge, this plan would be a good fit.
Pros:
- Cross-Platform Agents: Compatible with Windows, macOS, and Linux.
- Cloud-Based Operations: Enhances accessibility and data management.
Cons:
- No On-Premises Server Option: May not suit organizations with specific on-premises requirements.
Heimdal Security provides a platform of tools and the Threat Hunting and Action Center is not the company’s only product. The typical way to identify your business’s exact requirements is to start with a consultation with Heimdal Security experts. You can access a free demo.
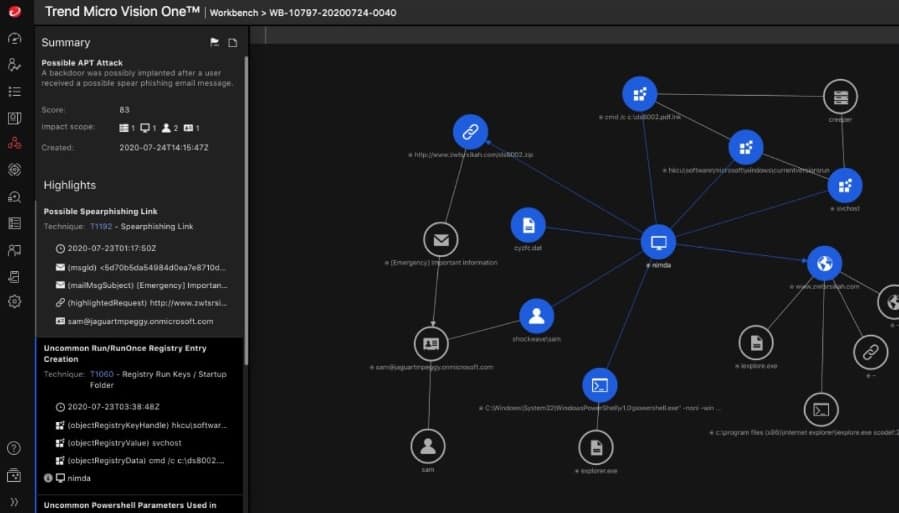
5. TrendMicro XDR
TrendMicro offers a package of SOC tools that are centered on a SIEM system. The SIEM operates from the cloud but includes onsite modules that collect data and upload them. Those on-site agents also implement response activities. If you use cloud services, there is also a module of TrendMicro XDR that installs on your cloud server account and protects those systems.
Key Features:
- Advanced SIEM Capabilities: Provides thorough security event analysis.
- Hybrid Environment Support: Protects both on-premises and cloud assets.
- Customizable Detection Rules: Tailors security to specific organizational needs.
Why do we recommend it?
TrendMicro XDR is a little different from the XDR systems above because while the LogRhythm, CrowdStrike, and Rapid7 systems (and Exabeam, below) focus heavily on user activity, the TrendMicro system is much more interested in devices. This makes TrendMicro XDR a very good choice for protecting IoT devices, although it can also be applied to regular business networks.
Whether operating on your site or in your cloud account, the data-gathering agent collects log messages and compiles its statistics on system activity. These information feeds are uploaded to the TrendMicro server and consolidated to provide a data source for the SIEM.
The SIEM operates a threat detection system, which looks for indicators of compromise. A typical indicator would involve a sequence of suspicious events. So, one action doesn’t automatically trigger an alert. Instead, the SIEM will pay extra attention to the activities of the user account involved in that action to see whether a follow-on action occurs that is expected from a hacker attack. If enough related actions occur that match a known chain of attack, the system triggers a response.
The threat response is communicated from the SIEM to the monitoring modules, which then either perform their actions or communicate with an access rights manager and firewalls to block hacker activity.
Who is it recommended for?
As already observed, the TrendMicro XDR is a good choice for protecting IoT devices. This includes sensor networks and security cameras, which can be targets for inclusion in botnets for use in DDoS attacks.
Pros:
- Focus on Device Security: Ideal for IoT and endpoint protection.
- Comprehensive Cloud Protection: Safeguards cloud-based assets effectively.
Cons:
- Device-Centric Approach: May overlook some user-based security aspects.
TrendMicro’s SOC support system is available in two formats. The first is called Vision One, which is a cloud-based system coordinator for TrendMicro endpoint protection systems. The system is also known as a managed service, called Managed XDR. This completely outsources your SOC, so you don’t need any onsite administrator staff to run your security services.
6. Exabeam
Exabeam offers a SOC software package that is built around a cloud-based SIEM. As with other SOC packages on this list that operate on the SIEM model, this bundle includes off-site processing with onsite data gathering. The Exabeam system processes log messages, so it is also a log manager that helps data privacy standard compliance reporting by laying down an audit trail. An optional extra service offered by Exabeam is a log archiving system that manages the large volumes of log data that your system will generate.
Key Features:
- Cloud-Based SIEM Solution: Offers a centralized approach to security.
- Compliance Reporting: Assists in meeting various regulatory standards.
- Log Management: Keeps detailed records for analysis and reporting.
Why do we recommend it?
Exabeam describes its solution as a SIEM. However, it is very similar to the XDR products on this list. This demonstrates the blurred line in the definition of these two categories of cybersecurity services. Like CrowdStrike, Rapid7, and LogRythm, the package installs agents on endpoints and they upload log files to a cloud-based threat hunter. The Exabeam also deploys UEBA for fine-tuned baselining.
All of the information that the on-site modules upload to the Exabeam server is called the Exabeam Data Lake. The Data Lake provides the source material for the Exabeam Advanced Analytics module. This is the threat hunting element of the SIEM. It deploys UEBA to watch for abnormal behavior. The Exabeam Data Lake is also available for manual examination through an analysis module in the Exabeam system console. This allows you to sort, group, and filter records for your assessments.
The console for Exabeam can be accessed through any standard browser. It displays live statistics and indicators as new log messages arrive. The console includes a settings system that allows you to specify the degree of response automation you are comfortable with. It is possible to set specific events to trigger automated responses while others generate notifications to give you the option of dealing with those situations manually.
The Exabeam Incident Responder implements automated responses. Fine-tuning the actions of the Incident Responder gives you control over your own business’s SOC strategy. The system works on a method that involves “playbooks.” Several pre-written playbooks are built into the Exabeam service, but you can create your own or decide which of those provided playbooks to activate. A playbook is a workflow that links triggers and actions. Typically, a response involves SOAR strategies that interact with other parts of your on-site system to block hacker activity.
Who is it recommended for?
Businesses that are interested in a cloud-based threat hunter should consider Exabeam alongside LogRhythm, Rapid7, and CrowdStrike for the protection of office networks from attack and particularly to root out advanced persistent threats.
Pros:
- Advanced UEBA: Utilizes behavior analytics for sophisticated threat detection.
- Log Archiving: Manages large volumes of log data effectively.
Cons:
- May Require Extensive Customization: To fully leverage all features.
Exabeam is available for a free trial.
SOC software tools FAQs
What is a SOC tool?
A Security Operations Center requires tools that collect system activity intelligence, search for malicious activity, and provide automated responses or advice for manual intervention. The types of security packages that achieve these goals include SIEMs, vulnerability managers, intrusion detection systems, and compliance reporting services.
Is SOC same as Siem?
A Security Operations Center (SOC) is an IT asset protection service that should be built into the tasks performed by your IT department. This service requires the collection and examination of system data to identify threats and a SIEM tool performs these actions. Therefore, a SOC isn’t the same as a SIEM, but it needs a SIEM.
Can you have a SOC without a SIEM?
A Security Operations Center (SOC) needs to gather system activity data and search it for signs of intrusion or malware movements. These actions are exactly the services performed by a SIEM. Therefore, a SOC can exist without a SIEM but it will need a suite of replacement tools to perform those data gathering and searching functions.