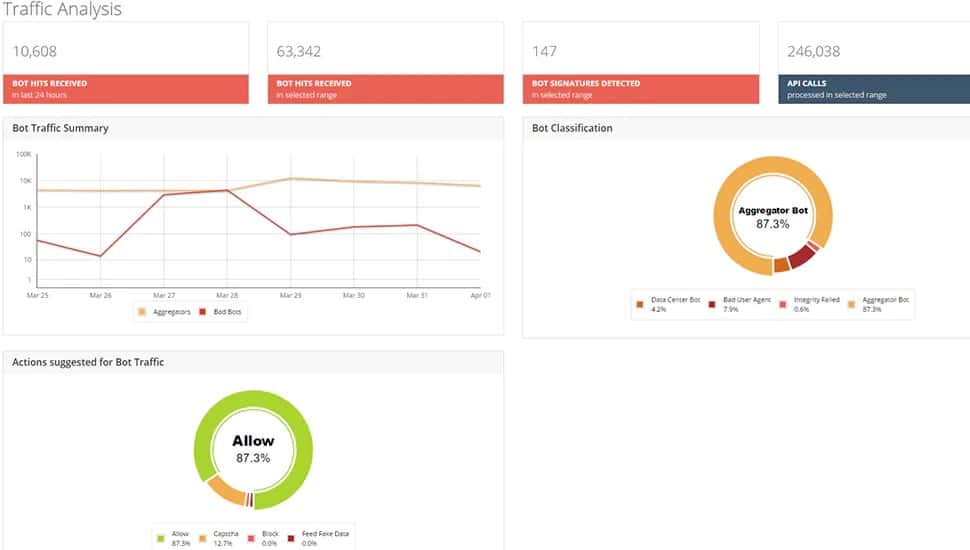
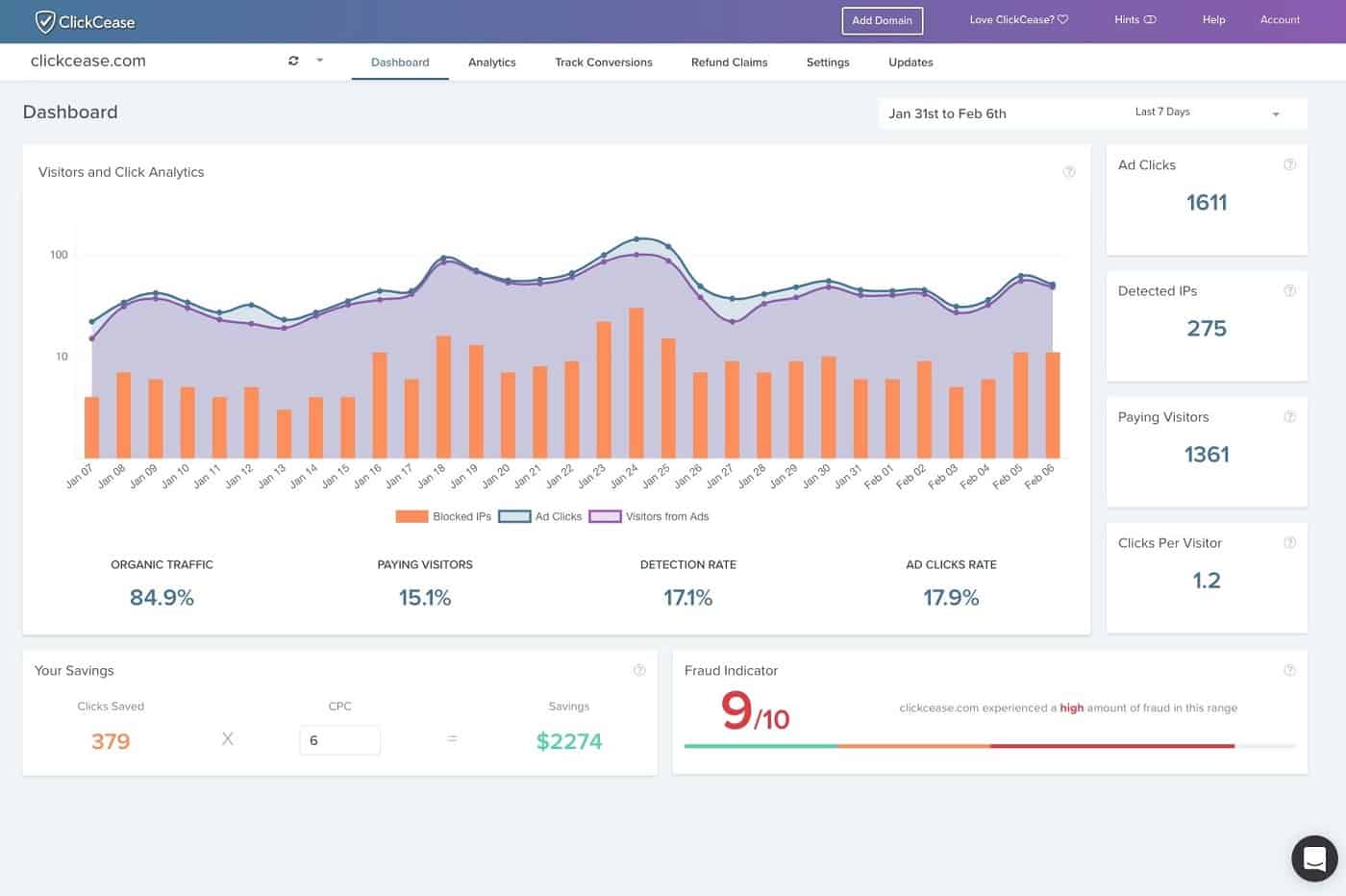
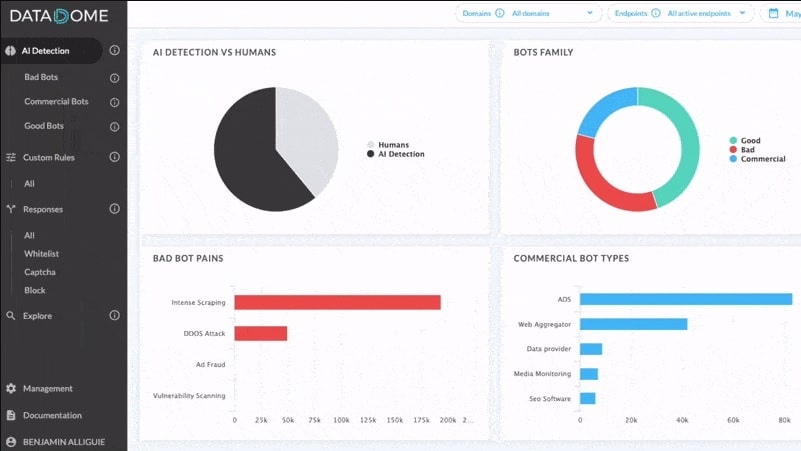
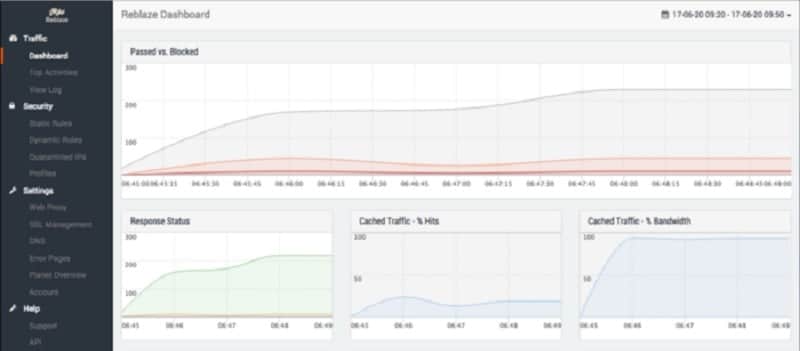
Botnets are networks of compromised devices controlled by cybercriminals, often without the device owners’ knowledge. These devices, referred to as “bots” or “zombies,” are used for various malicious purposes. A botnet operates under the control of a command-and-control (C&C) server, which sends instructions to infected devices. Common uses include launching distributed denial-of-service (DDoS) attacks to overwhelm servers, spreading malware, stealing data, and mining cryptocurrencies without authorization.
A particularly deceptive application of botnets is click fraud, a technique used to exploit pay-per-click (PPC) advertising models. In click fraud, botnets are directed to repeatedly click on advertisements, artificially inflating the number of clicks. Thus, the eCommerce entrepreneur gets an accurate report of the number of times an ad was clicked, without gaining any sales because those clicks were made by automated processes and not real potential customers.
Click fraud can also be used to deplete a competitor’s ad budget, disrupting their campaigns. Detecting and mitigating such botnet-driven schemes is crucial for digital businesses. In fact, the proliferation of botnets could render PPC pricing and site throughput data collection defunct unless automated clicks can be identified and factored out of statistics.
Botnets are also used to steal sensitive information, such as login credentials, by intercepting data from infected devices. They may target businesses and individuals, exploiting vulnerabilities in networks and software. Their scale and distributed nature make them especially difficult to detect, as traffic originating from botnets often mimics legitimate activity.
Modern botnet detection tools are essential in combating these threats. These tools analyze network traffic, detect unusual patterns, and block malicious communications with C&C servers. By identifying and neutralizing botnet activity early, organizations can protect their infrastructure and minimize risks to data privacy and security. As botnets evolve, incorporating techniques like machine learning and behavioral analysis is critical to staying ahead of attackers.
Here is our list of the best botnet detection software:
- ManageEngine Log360 EDITOR’S CHOICE This package deals with botnets by watching user and endpoint activity, referencing a blacklist of suspicious IP addresses and domains, and implementing automated responses to block suspicious activity. Runs on Windows Server. Start a 30-day free trial.
- ManageEngine NetFlow Analyzer (FREE TRIAL) This network traffic monitor identifies botnet attacks and zombie infections that turn your equipment on other networks. Available for Windows Server and Linux. Start a 30-day free trial.
- Cloudflare Bot Manager A threat intelligence service that reaps botnet identification from more than 25 million sites managed by Cloudflare. This enables you to sort out bots used for different purposes. This is a cloud-based service.
- Radware Bot Manager This service offers protection for Web applications, mobile devices, and APIs through a plug-in that assesses connection requests and signals whether they should be rejected. This is a cloud platform.
- SolarWinds Security Event Manager This on-premises package protects your network from botnet attacks that overwhelm or bypass firewall security. This will also stop your devices from being hijacked into a botnet. It runs as a virtual appliance.
- ClickCease This cloud-based service is powerful at rooting out click fraud, and the company also helps you with a range of other Google Ads-related services.
- DataDome This service doesn’t operate as a proxy. Still, it provides a SaaS AI process that generates a fast approval for all requests arriving at your Web server, preventing OWASP-listed attacks.
- Reblaze Bot Management Part of a cloud-based security platform, this service filters out bot actions before they reach your Web server.
Botnet detection software
You want to stop them from overloading your resources rather than just spotting botnets. There are several ways this can be done. Probably the most effective tactic is to get a vast capacity server to take the hit and just pass on the actual traffic to your Web server. There are other methods available, such as blacklists, honeypots, and black holes.
As there are several angles you can use to detect and block botnet activities, we have identified various solutions that include onsite options and edge services.
The best botnet detection software
Botnet detection requires network traffic analysis for incoming connection requests to Web servers and load balancers.
What should you look for in a botnet detection system?
We reviewed the market for botnet detection software and analyzed the options based on the following criteria:
- A system that can catch DDoS attacks before they block access to a Web server
- A software package that offers security services in addition to botnet detection
- A service that can take remediation action to reduce the effects of a botnet attack
- Threat intelligence that includes an IP address blacklist
- Quick detection and response
- A free trial or a money-back guarantee for a no-risk assessment period
- A good deal that provides valuable services for a reasonable price
As well as working to our selection criteria, we looked for a range of solutions that offer options for hosted and on-premises packages and include subscription services and software packages that can be bought outright.
1. ManageEngine Log360 (FREE TRIAL)
ManageEngine Log360 is a large package of system security tools that implement monitoring and automated responses. The service addresses botnets in a number of ways. The main threat hunting module in this package is a SIEM, which gathers log messages from all around your system and your cloud accounts. The SIEM gets a threat intelligence feed, which provides a blacklist of IP addresses and domains known to be used for malicious activities, such as botnet C&Cs.
Key Features:
- IP Blacklisting: Utilizes a threat intelligence feed for blacklisting malicious IP addresses and domains.
- Anomaly Detection: Identifies unusual behavior as potential security threats.
- Network Monitoring: Keeps an eye on network activity to detect anomalies.
- User Activity Tracking: Logs user account activities for security and compliance purposes.
Why do we recommend it?
ManageEngine Log360 provides a number of methods to detect and block botnet activity. This multi-layer approach means that deceptive programs that are written to dodge detection have a lot more traps to avoid. Combining log examination with network traffic scanning gives this choice opportunities to spot botnets.
A botnet operates as a background process and all running tasks get logged by the operating system. So, the SIEM will see if a program is communicating excessively over the internet. This activity would be flagged as anomalous behavior and shut down.
The Log360 package includes a security orchestration, automation, and response (SOAR) system. This coordinates all of the units and also third-party tools and it can implement automated responses to detected threats. This unit makes the diverse tools in the Log360 package easier to manage.
Log360 isn’t just designed to deal with botnet activity. It also implements data loss prevention Active Directory protection and auditing, and insider threat protection. Many of the features in the Log360 package speed up the detection of threats, which could be software-based or manual. The package deploys user and entity behavior analytics (UEBA) to provide activity baselining and then performs anomaly detection, which is the best way to spot zero-day attacks.
Who is it recommended for?
The full system is very comprehensive and provides all of the tools needed by a Security Operations Center. The activity logging and system auditing features of the package are suitable for compliance reporting. Log360 is compatible with the requirements of PCI DSS, GDPR, FISMA, HIPAA, SOX, and GLBA.
Pros:
- Integrated Security Approach: Combines log analysis with network monitoring for comprehensive botnet detection.
- Automated Security Responses: Capable of executing coordinated, automated actions against detected threats.
- Enhanced User Protection: Offers robust user account security and active directory protection.
- Compliance Ready: Includes features that support compliance with major regulations like PCI DSS, GDPR, and HIPAA.
Cons:
- Management Complexity: Requires a dedicated team for effective utilization and management.
ManageEngine Log360 is an on-premises software package that installs on Windows Server. You can examine Log360 with a 30-day free trial.
EDITOR'S CHOICE
ManageEngine Log360 is our top pick for a botnet detection system because it offers a comprehensive, multi-layered approach to network security, enabling organizations to detect and mitigate botnet activity in real-time. Advanced log management and security analytics give Log360 the ability to effectively identify suspicious patterns and behaviors that are commonly associated with botnet attacks. The system uses machine learning algorithms and threat intelligence to analyze logs from various sources, helping to quickly spot abnormal traffic and unusual access patterns indicative of botnet infections. A notable feature of ManageEngine Log360 is its ability to correlate security events from different network components, including firewalls, routers, and endpoints, providing a holistic view of network activity. This unified approach allows administrators to detect even the most sophisticated botnet-related activities that might otherwise go unnoticed. Log360’s real-time alerting system ensures that teams are promptly notified of potential threats, enabling rapid response and reducing the time to mitigate an attack. Log360 also provides detailed forensic reports, allowing security teams to investigate past incidents and uncover the root cause of infections. The platform’s ease of use and scalability make it an excellent choice for businesses of all sizes looking to safeguard their networks against botnet threats.
Download: Get a 30-day FREE Trial
Official Site: https://www.manageengine.com/log-management/download.html
OS: Windows Server or SaaS
2. ManageEngine NetFlow Analyzer (FREE TRIAL)
ManageEngine NetFlow Analyzer is a network traffic monitor, and it includes a utility called the Advanced Security Analytics Module. This service is an intrusion detection system, and it also spots DDoS attacks and other types of botnet traffic.
Key Features:
- Anomaly Identification: Detects unusual traffic patterns indicative of botnets or DDoS attacks.
- Protocol Analysis: Breaks down traffic by protocol to identify suspicious activities.
- Intrusion Detection: Includes a system for recognizing potential security breaches.
- Cross-Platform: Compatible with both Windows and Linux operating systems.
Why do we recommend it?
ManageEngine NetFlow Analyzer is a traffic analysis package and as such, is able to spot bot activity and report it. The system operates from within a network, so it wouldn’t be able to divert, block, or absorb DDoS attacks. However, the tool will raise an alert and provide a retrospective analysis of each attack.
As with the SolarWinds option, this is a network resident solution. It can communicate with firewalls to push its detection capabilities right to the edge of the network. However, it is primarily a network defense system.
The dashboard for the NetFlow Analyzer includes attractive dials and graphs that show live traffic patterns. The system offers an overview of network activity, and it also provides traffic-shaping measures. These allow you to throttle certain types of traffic and prioritize or block specific applications. This tool could be used to shut down a botnet attack by closing off all services to connection requests temporarily. However, a more targeted approach would be to update the firewall table to block the IP addresses of the source of suspicious activity.
The ManageEngine NetFlow Analyzer allows you the flexibility to choose a strategy to deal with botnet activity. The dashboard of the service is customizable as well. This tool would save you money on your botnet detection strategy because it can help you with general network traffic management and squeeze value out of your existing network infrastructure.
Who is it recommended for?
The NetFlow Analyzer is an impressive tool but it is probably a bit too comprehensive for small businesses. There is a Free edition available, but that is limited to monitoring two interfaces, which wouldn’t be enough for home use, so that still doesn’t make the package attractive to small enterprises. Mid-sized businesses would get a lot of use out of this traffic analyzer and the top edition provides multi-site monitoring capabilities for large organizations.
Pros:
- Dynamic Botnet Detection: Capable of identifying and mitigating botnet and DDoS threats through network traffic analysis.
- User-Friendly Dashboards: Features intuitive dashboards for real-time traffic monitoring and management.
- Automatic Outlier Highlighting: Efficiently identifies and displays network anomalies, including bandwidth overuse.
- Enterprise Scalability: Designed to accommodate the complex needs of large network environments.
- Detailed Traffic Insight: Provides in-depth traffic analysis on a per-hop basis for comprehensive network oversight.
Cons:
- Not Suitable for Small Networks: Geared towards enterprise networks, making it less applicable for small or home network setups.
NetFlow Analyzer is available in three editions: Free, Professional, and Enterprise. The Free edition is limited to monitoring only two devices. The Professional edition is limited to monitoring a single network, and the enterprise edition can monitor multiple sites. The Enterprise edition also adds NBAR and CBQoS management capabilities. The Advanced Security Analytics Module is only available in the Enterprise edition. You can get a 30-day free trial of the Enterprise plan. It is offered in versions for Windows Server and Linux.
3. Cloudflare Bot Manager
Cloudflare is one of the world’s leading DDoS protection services. The system’s DDoS service detects botnet traffic to filter out fake connection requests and pass on good traffic. The Cloudflare system is an edge service. It acts as a proxy, acquiring the publicly known IP address of the protected network and allocating a secret address to that system. The Cloudflare service assumes the client’s identity, receives all of its traffic, and passes legitimate traffic to its final destination over a VPN.
Key Features:
- CDN Integration: Works alongside a content delivery network to enhance site performance and security.
- Traffic Management: Effectively absorbs and manages large volumes of traffic.
- SSL Security: Includes an SSL certificate to secure website communications.
Why do we recommend it?
Cloudflare Bot Manager is a reliable service from the leader in DDoS protection. This tool can be integrated into a package of edge services that all protect and enhance websites. The Bot Manager is able to spot a range of automated attacks that derive from bots and the attempts that they launch against your site or Web assets are all blocked and logged. The online console for Cloudflare lets you see how many bot actions it blocked.
The Bot Manager offered by Cloudflare is a more sophisticated botnet detection system for those who want a broader botnet control service. DDoS is just one of the tricks that botnets can perform, and the Bot Manager covers every inconvenience and vicious action they can be used for. This list of services includes detection and blocking bots used for account takeover and credential stuffing. It also identifies bots that hijack email accounts to spread spam.
The system protects your content by identifying and stopping bots engaged in scraping. The bot detector can also spot fake credit card transaction attempts to damage your ability to process credit cards by repeatedly canceling charges. It also detects inventory hoarding, making stock unavailable for sale by loading carts and never checking out.
Cloudflare is a reliable and reputable company, and its rapid growth has been achieved through competently providing essential services for Web traffic problems. Cloudflare bundles all of its services into plans. There are four editions, and all of them include some degree of botnet detection. However, the full Bot manager is only included in the top plan, which is called Enterprise. The lowest plan is Free, and that includes DDoS protection – as do all editions.
Who is it recommended for?
Cloudflare Bot Manager is particularly good at blocking Web assets. Many private or small business craters of websites will encounter an offer for this service when first signing up for a Web hosting package. The base tier of the Bot Manager and other Cloudflare services, such as SSL certificate management and a content delivery network, is free. This means that it is a service that small businesses in particular will find it hard to resist … or avoid.
Pros:
- Comprehensive Bot Protection: Identifies and blocks a wide array of bot-driven attacks, including DDoS, account takeovers, and credential stuffing.
- Global Threat Intelligence: Leverages Cloudflare’s vast network to accurately detect and mitigate threats.
- Versatile Defense Mechanisms: Prevents data scraping, inventory hoarding, and fraudulent transactions to protect web assets.
Cons:
- Geared Toward Web Assets: Best suited for online assets, potentially less effective for non-web-based network protection.
4. Radware Bot Manager
Radware Bot Manager is offered as an API or plug-in with a range of integration options. The add-on can be integrated into your cloud server service, into a CDN, or into your Web server. The system is also available as a virtual appliance, which you can put on your gateway to pre-filter traffic.
Key Features:
- Flexible Integration: Compatible with web application firewalls (WAF) and content delivery networks (CDN) for comprehensive protection.
- Proactive Defense: Offers a unique fightback option against bots.
- Comprehensive Fraud Protection: Safeguards against various forms of online fraud.
Why do we recommend it?
Radware Bot Manager is a very similar package to the Cloudflare system. This tool is part of a platform of edge services and it is particularly strong at protecting Web assets. This system, like Cloudflare, can be bundled together with a Web application firewall or content delivery network (CDN). One advantage that Radware has over Cloudflare is that it gives an option for you to host the package yourself as a virtual appliance.
Used on your premises, the Radware system won’t be able to offload DDoS attacks. However, Radware also offers a WAF, an edge service, to filter traffic before getting to your network and Web servers. Radware Bot Manager can be taken as an add-on option with the WAF.
The system sorts through incoming traffic and creates a profile for each IP address to track users and spot bots. Remember, botnets aren’t only used for DDoS attacks. After a quick reference to the Radware server, the API returns an allow/reject message to the server.
By tracking activities on your website, the Radware system identifies bots and gives you a range of automated actions, which your select when setting up an account. The service can feed fake data to a bot, duping the end-user of the data that the bot collects. It can also challenge incoming users with potential bot profiles with a reCAPTCHA or block access to users that have been definitively identified as fake.
Who is it recommended for?
The cloud version of Radware is suitable for any business and the self-hosted version would appeal to large businesses. However, the DDoS service of Radware is not quite as good as the Cloudflare system and there is no Free tier, so Cloudflare wins in the small business market.
Pros:
- User-Friendly Interface: Features an intuitive dashboard for easy management and monitoring.
- Granular Traffic Filtering: Acts as or integrates with a WAF for detailed traffic analysis and control.
- Automated Response Options: Allows for custom automated actions upon bot detection, including data feeding and user challenges.
Cons:
- Limited DDoS Mitigation: While effective against bots, its DDoS protection capabilities are not as extensive as some competitors.
- Trial Period: A longer trial period would be beneficial for in-depth evaluation.
You can get a 15-day free trial of Radware Bot Manager.
5. SolarWinds Security Event Manager
SolarWinds Security Event Manager is a protection system for networks. The service operates on your site as a virtual appliance, installed on top of either VMWare or Hyper-V. This isolates the system from any potential threats circulating on the network, making it hard to tamper with.
Key Features:
- Comprehensive Detection: Identifies a wide range of network and endpoint threats.
- SIEM Functionality: Acts as a Security Information and Event Management system.
- Log Analysis: Searches and analyzes log files for security insights.
- Activity Insights: Collects data on network activity for thorough monitoring.
- On-Site Implementation: Designed specifically for Windows Server environments.
Why do we recommend it?
SolarWinds Security Event Manager is a SIEM that includes a log message collection service. After consolidating and sorting those log messages, the tool performs threat hunting as a SIEM service. This can detect bot activity as well as other malicious actions. You can set up instructions for automated responses, such as account suspension or IP address blocking.
The botnet detection systems and defense strategies in the Security Event Manager are focused on protecting the network – as it operates within the network, it cannot intercept traffic before it arrives on site. However, it able to block traffic as soon as it arrives.
SolarWinds supplies all installations of the Security Event Manager with a feed of community-sourced IP addresses found to be the sources of malicious activity. This blacklist saves time examining packet contents – if the address is on the list, that packet just isn’t getting in.
The Security Event Manager updates firewall tables with its blacklist, putting botnet blockers right on the network’s boundary. Any action the firewall takes to block traffic gets logged, and those logs are all picked up by the Security Event Manager. The security system is a SIEM. It collects and consolidates log messages. The threat hunter then scours through log messages, which will spot the block on a request. This then gets reported in the dashboard. The notification from the firewall gets passed through to a log file and stored.
The logs that the Security Event Manager saves are all preserved and made available for standards compliance auditing. This log management function makes the Security Event Manager a good choice for businesses that need to follow PCI DSS, GLBA, SOX, NERC CIP, HIPAA. The log manager includes a file integrity monitor that protects log files from tampering.
Who is it recommended for?
This package offers good value for money because it isn’t limited to bot detection – it identifies a whole range of threats. You also get a log manager included for free and this provides compliance auditing and reporting features. Small businesses would find that this package is too big for their needs but all mid-sied and large organizations will benefit from its use. The software runs on Windows Server.
Pros:
- Advanced Threat Detection: Capable of detecting bot activity and a variety of other threats, enhancing network security.
- Automated Defense Mechanisms: Can autonomously block attacks based on predefined criteria, such as IP addresses.
- Broad OS Monitoring: Compatible with multiple operating systems, including Windows, Linux, Unix, and Mac.
- Instant Security Insights: Comes with over 700 pre-configured alerts and detection templates for immediate threat identification.
- Intelligent Reporting: Utilizes smart reporting to minimize false positives, making threat response more accurate.
Cons:
- Complex Interface: The extensive features require time and effort to fully utilize and understand.
SolarWinds offers the Security Event Manager for a 30-day free trial.
6. ClickCease
ClickCease detects bots that are used for excessive, unattended ad clicks, which is called click fraud. Bots can click on pay-per-click ads, thus jacking up the bill for the advertiser. This technique can be used by the advertising agency or by rivals who hope to exhaust the target’s advertising credits before any real people see the ad. This system is mainly geared towards click fraud used on Google Ads.
Key Features:
- Cloud-Based: Operates entirely online for seamless integration and management.
- Fraud Prevention: Specifically targets and blocks click fraud activities.
- Competitor Insight: Offers capabilities to identify and mitigate actions by competitors.
Why do we recommend it?
ClickCease has found a niche in the bot detection market, which is protection against click fraud. This is a useful tool that helps you dispute pay-per-click bills. It can also protect your Google Ads account to prevent malicious rivals from bumping up your Google bill out of spite. It will block the IP addresses of known click farms from accessing your site.
Several other types of people want to waste your ad budget, such as woke canceling activists and industrial-scale click farms. Whoever wants to drain your account can do it at a rate through bots.
The ClickCease system works as a javascript insert that you put into the code for your site. This can gather information on users that clicked on your ads and arrived at your location. The system builds up a profile for each visitor from an ad and identifies those who are not real people or manually perform click fraud. When malicious activity is determined, the ClickCease service automatically enters the source IP address in the exclude list of your Google Ads account.
The ClickCease service includes other utilities, such as how to get around the Google Ads exclusion list limit of 500 IP addresses.
Who is it recommended for?
This tool is specifically designed to protect websites. It integrates into a site through the addition of a line of code. Even if you have no idea how to do that, this service is still accessible because the signup screens give detailed instructions on the task.
Pros:
- Specialized Click Fraud Detection: Excellently identifies and prevents fraudulent ad clicks, saving advertising budgets.
- Automated IP Blocking: Integrates a system to automatically exclude malicious IP addresses from interacting with ads.
- User-Friendly Implementation: Simplifies setup with a straightforward JavaScript insertion for website integration.
Cons:
- Limited Scope: Focuses exclusively on click fraud, lacking broader network or DDoS protections.
- Trial Limitations: A more extended trial period would be beneficial for comprehensive evaluation.
ClickCease is available in two plans, Standard for a single domain and Pro for unlimited domains. You can assess the service on a 7-day free trial.
7. DataDome
DataDome supplements its botnet detection strategy with scans for the OWASP top ten threats. This system is a list of the most significant current vulnerabilities that an IT can have. So this is a vulnerability scanner as well as a botnet blocker.
Key Features:
- Comprehensive Protection: Cloud-based solution that scans for botnet activities and payment fraud.
- Advanced Fraud Detection: Identifies scalping, inventory hoarding, and other malicious bot behaviors.
- OWASP Awareness: Enhances security by scanning for vulnerabilities from the OWASP top ten list.
Why do we recommend it?
DataDome protects mobile apps from bot activity as well as websites. What’s even better is that, unlike Radware, DataDome publishes its prices, so it is very easy to see where this service’s target market is. The service’s plans each handle connection requests in the order of hundreds of millions per month.
The bot activity that the DataDome system detects includes DDoS attacks, scaping, account takeover, and click fraud. DataDome also operates a threat intelligence feed that pools the attack experience of all of its customers.
This SaaS solution integrates into your sites, mobile apps, and services with a plugin. The collected data from those agents is available for threat analysis in the cloud-based console.
Who is it recommended for?
DataDome is very expensive. Its starting price is $2,990 per month if paid annually upfront. That is considerably more than the $0 that Cloudflare charges for its base package. So, DataDome is aimed at very large organizations with big budgets.
Pros:
- OWASP Top Ten Scans: Regularly updated to detect threats based on prevalent vulnerabilities.
- Broad Activity Coverage: Capable of defending against a wide range of bot-driven attacks including DDoS, scraping, and account takeovers.
- Intuitive Management Interface: Offers a user-friendly web interface for easy configuration and monitoring.
Cons:
- Pricing: Geared towards larger organizations with significant budgets, potentially inaccessible for smaller businesses.
The DataDome service is a subscription system, and it is expensive. There are three editions, and the cheapest, called Starter, is priced at $1,590 per month. This price comes down to $1,190 per month if you pay for a year’s service upfront. The two higher plans are Business and Corporate. That top plan covers mobile apps and APIs and websites – the two lower plans only monitor websites. The Corporate plan is charged at $7,790 per month or $5,990 per month if paid annually.
8. Reblaze Bot Management
Reblaze Bot Management operates as a proxy server. It receives your web traffic and filters it, passing on only legitimate users. The processing of each connection request takes only 0.5 milliseconds.
Key Features:
- Integrated Security: Combines with a web application firewall (WAF) and content delivery network (CDN) for comprehensive web protection.
- High-Speed Processing: Analyzes and filters web traffic in just 0.5 milliseconds.
- Extensive Blacklisting: Utilizes a vast database of known malicious sources to prevent scams and traffic floods.
Why do we recommend it?
Reblaze Bot Management is a traffic assessment service that has a vast blacklist of known sources for scams and traffic floods. Like Cloudflare, this protection service is a proxy that filters traffic before it reaches your Web assets. The Bot Management service is integrated into a bundle that includes a CDN and DDoS mitigation. The key selling point of Reblaze is that its traffic assessment system involves many layers of processing but does not slow down site response times.
The full service of Reblaze includes a web application firewall and a content delivery network. This is a package of edge services that keeps your website running and servicing customers. The botnet detection system passes through several phases very quickly.
The system uses a profiling strategy to spot the same automated bot system, whether it switches IP address or flows through many different zombie devices. The Reblaze technique looks for a list of indicators of suspicious identity to quickly home in on candidate bots. This is the key to the speed of Reblaze.
Who is it recommended for?
Reblaze is a strong rival to Cloudflare, but it doesn’t publish its prices, so there might be some nasty surprises in store for those who enter the buyer’s journey with the 30-day free trial.
Pros:
- Efficient Traffic Filtration: Ensures quick and accurate differentiation between legitimate users and bots, maintaining optimal site performance.
- Comprehensive Web Protection: Offers an all-in-one security solution that includes bot management, DDoS mitigation, and content delivery acceleration.
- Advanced Bot Detection: Employs behavioral profiling to accurately identify and block sophisticated botnet attacks.
Cons:
- Cloud-Only Availability: Limits deployment options to cloud environments, potentially restricting flexibility for some organizations.
The Reblaze platform is delivered from the cloud. Its console includes activity reports and provides historical analysis support. You can try the Reblaze system on a 30-day free trial.
Botnet Detection Software FAQs
How can botnets be detected?
Although a botnet uses many zombie computers to launch an attack, botnet traffic has a typical pattern. The botnet’s main purpose is usually a DDoS attack and these have standard formats. Some DDoS attack strategies, such as reflection attacks are not found in botnet activity because the traffic volume created by the zombie computers is enough to disable a Web server’s ability to serve legitimate requests without the need for an external third-party service. So, botnet detection systems look at traffic patterns and packet structures rather than the source addresses of that traffic.
What is bot detection software?
Bot detection software typically operates in a firewall, so if you buy in a botnet detection package, you should load it onto your gateway router or place it on a server that operates a filtering service, such as a cloud-based Firewall-as-a-Service. Bots typically operate from outside the network and direct traffic at the gateway or a Web server. This means that bot detection services operate at the boundary of the network. Nowadays, firewalls and proxy services typically already include botnet protection.
How does Cloudflare detect bots?
Cloudflare has the advantage of offering the largest DDoS protection services in the world. This means that it is worthwhile for them to note down the sources of botnet traffic. Typically, an individual zombie device in a botnet is rarely reused for attacks on the same target, so a botnet protection system would be wasting time and space maintaining a reference database of IP addresses to block. A list of infected IP addresses can extend to millions of entries that would take too long to scan through, so rather than listing IP addresses, Cloudflare uses a system of fingerprinting. This implements selective challenges to filter out potential threats while allowing through the majority of traffic.