Many sneaky malicious programs can find their way onto your computer over the internet, and a keylogger is one of the worst. Spyware is a type of malware that records your activities. A keylogger records every keystroke you make on your computer’s keyboard. With this information, a hacker can work out your username and password for a range of sites without even seeing what comes up on the screen.
For example, when you check your email, you might type in “mail.yahoo.com” or “gmail.com” in the address field of your browser. Predictably, your next step is to type in your username and password. Everything you type is sent to a hacker database over the internet, where the text is parsed through to pick out the sensitive parts, like your password.
In this guide, you will learn:
- What keyloggers do
- How keyloggers get onto your computer
- How to detect a keylogger
- How to get rid of a keylogger
What is a keylogger?
Keyloggers are also known as keystroke loggers. This is a program that runs all the time on your computer from the minute that you start it up. The keylogger will either record every keystroke you make or just those made in specific fields on websites.
Keyloggers don’t slow down your computer and you won’t even notice when one is in operation. Windows 11 even has a keylogger built into the operating system. Although there are some legitimate uses of keyloggers, such as in the workplace, or to track the internet activities of children, you are also at risk of these programs turning your computer into a spy for hackers.
Keyloggers can embed themselves into the operating system of your computer. These types of malware are called “rootkit” viruses.
There are types of keyloggers that can even work at a lower level than the operating system. These are known as “hypervisor malware.”
A keylogger may attach itself to your browser as a hidden extension and just report on all of the keystrokes that you make through that app. Other keyloggers manage to infect web pages, so everyone that visits those pages gets their data stolen.
Keyloggers can alter the memory access process of your browser and steal information at that point, or they can be triggered by the click of a web form “Submit” button.
In short, there are many operating scenarios for keyloggers and many different locations on your computer where the program might be running.
Rootkit and hypervisor keyloggers are particularly difficult to get rid of. Antimalware programs usually can’t get down to that level and so these keyloggers continue in operation unmolested. Keyloggers that masquerade as browser extensions also often evade detection from antimalware.
Hardware keyloggers
Not all keyloggers are software-based. Some operate as a piece of hardware. You are less likely to be subjected to one of these in your home.
However, industrial spies sometimes slip in one of these extra jacks in the back of a computer between the keyboard socket and the plug on the lead from the keyboard.
A number of other hardware-based keyloggers seem to come straight out of a spy movie. These include keyboard overlays, “acoustic keyloggers” that record the sound of a person tapping on a keyboard and work out the tiny difference in the sound that each key makes, and “electromagnetic emission” keyloggers that capture the electric pulses leaking into the air from a keyboard cable.
However, unless you are a spy, or you travel to places such as North Korea on business, the chances of you being hit by a hardware keylogger are slim. Those virus keyloggers that hackers put on the internet are what you need to be concerned about.
How keyloggers get onto your computer
The best chance you have of preventing a keylogger from operating on your computer is to block it before it gets installed. For this, you need very good antimalware software and also a skepticism toward downloading anything over the web.
The typical method of entry for a keylogger is as part of a Trojan. A Trojan is a piece of software that pretends to be a useful utility. When you download this free app and install it, either it won’t work, or the app really does work as promised but the installer program slips malware onto your computer as well.
Trojans often operate as bundles of software, with each element specializing in a different task. The initial Trojan may be loaded as a downloader, which enables the hacker to get more malware, including a keylogger, through the firewall and onto your computer. The keylogger will record your keystrokes in a file on your computer and then a separate program will send that information out over the internet.
That information is rarely sent directly to the hacker. This is because any malware analyst could then trap the message and trace the hacker. Instead, the data is encrypted and then sent to a public message board, where the hacker can download the information while hiding his true address.
As many legitimate programs use keylogging as part of their routines, this activity is often overlooked by antimalware and anti-spyware. This makes it very difficult to prevent keyloggers from getting onto your computer.
Those that sneak in as part of an update also frequently manage to get past antimalware programs. The only real defense you have is to resist the temptation to download and install free software from sources other than major, reputable software houses.
How to detect a keylogger
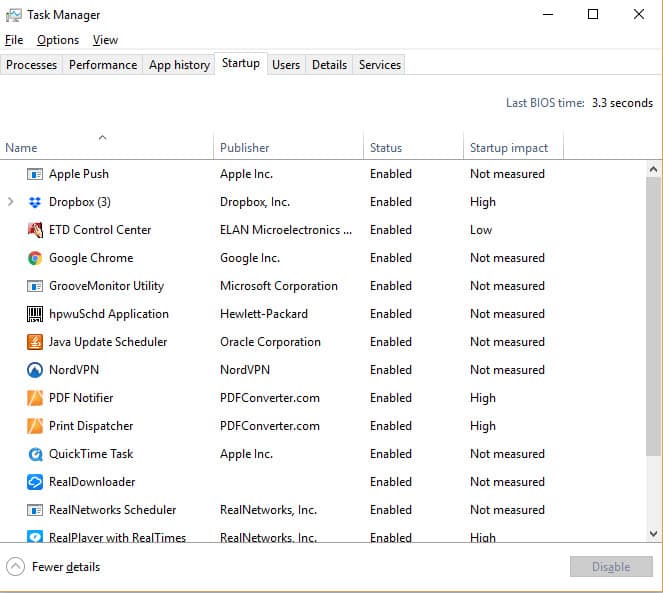
The most straightforward way to detect any undesirable software is to look in your Task Manager to check on the processes that are running.
Unfortunately, many of those background processes have obscure names. However, you can search on the internet for the names of the programs you discover running on your computer and hopefully, someone will have already written a warning about keylogger processes that match some of the names you found.
In Windows, right-click on the Windows icon and select Task Manager from the context menu.
The programs listed as Apps are those that appear in windows on your screen, so you won’t find a keylogger listed there. It will most likely be listed under Background processes.
Another good place to look for keyloggers is under the Startup tab. Keyloggers get set up to run all the time on a computer and in order to do that, they need to be started up with the operating system.
It is a good idea to get rid of anything you see in the Startup list that you don’t remember installing.
If you want to get rid of one of these programs, click on the line for it and then press the Disable button at the bottom of the window.
One more place to look for suspicious activity is in the report of internet usage on your computer. On Windows, press the Windows button and “I” together.
This will get you to the settings screen. Select Network & Internet and then select the Data usage option. You’ll be presented with a list of all the programs on your computer that are using the internet. Do a web search on any of the names you don’t recognize to see if they are keyloggers.
Perform similar checks on your browser extensions. Look through the extensions and disable any that you don’t remember installing or that you never use.
To get to extensions:
- In Chrome: type chrome://extensions into the address field
- In Firefox: type about:addons in the address field
- In Opera: select Extensions from the menu then click Manage Extensions
- In Safari: Select Preferences from the Safari menu and then click on Extensions
- In Internet Explorer: click on Manage add-ons in the Tools menu
- In Microsoft Edge: click on Extensions in the browser menu
How to get rid of a keylogger
Anti-keylogger software gives you a better chance of getting rid of keyloggers than general anti-malware or even anti-spyware utilities.
A comprehensive anti-keylogger needs to audit all of the processes running on your computer, from the BIOS to the operating system to the background services and apps running on your computer, on through to the network settings, plug-ins, and browser settings.
It may take some time for you to get rid of the keylogger, and ultimately, you might have to reinstall your operating system to completely wipe it away.
Many keyloggers are rootkit viruses, so, apart from a specialized anti-keylogger system, an anti-rootkit program could rid you of your problem. Some antivirus software — such as that from Bitdefender — includes the ability to detect rootkit viruses.
Here is a list of the best software to help you remove keyloggers.
SpyShelter
SpyShelter has several lines of attack against keyloggers. Once you install this software, you should let it run all the time, it will detect keyloggers when they try to install on your computer and it will block that installation. There are new keyloggers produced all the time and it takes a while for information about them to proliferate throughout the antimalware industry.
You may already have a keylogger on your system by the time you install SpyShelter. As explained above, some keyloggers are really difficult to shift and you may be reluctant to reinstall your operating system. The SpyShelter second line of attack is to scan the operations on your computer for suspicious keylogger-type activities. When it identifies this malware, SpyShelter will try to remove it. As a final defense for your computer, SpyShelter will scramble and encrypt all of your keystrokes to make them meaningless to keyloggers.
SpyShelter is only available for computers running the Windows operating system.
Zemana
Zemana produces an antimalware suite, but its anti-logger system is what we are looking at today. This doesn’t perform quite as well as SpyShelter in spotting all of the different strains of keyloggers out there, but it does pretty well. The anti-logger also includes an encryption enforcer for secure web transmissions, an ad blocker, a malware scanner, and ransomware protection.
This system works constantly in the background, monitoring activity and scanning downloads and installers for malicious content. It will also perform periodic system scans in the manner used by antivirus programs.
Zemana Antilogger is only available for Windows.
Malwarebytes Anti-Rootkit
If specialist keyloggers can’t help you, go for a rootkit removal program. The Malwarebytes anti-rootkit is an excellent performer and the fact that it is free makes it a top pick. This software will get right down into the operating system of your computer and scan for a range of rootkit viruses, not just keyloggers.
This program will perform system scans on demand rather than running constantly. A full scan involves a system reboot. If a clean up operation doesn’t solve all of your problems, you can use a fixdamage tool to get your internet working properly and fine tune your firewall.
Malwarebytes Anti-Rootkit is only available for Windows.
Norton Power Eraser
Like the Malwarebytes Anti-Rootkit, Norton Power Eraser goes deeper into your computer than standard antivirus programs. Antivirus programs often overlook keyloggers because some legitimate programs use the same technology. Whereas antivirus programs err on the side of caution, Norton Power Eraser deletes programs and asks questions later. You may risk losing some favorite apps with this take-no-prisoners approach. Check the program’s logs and restore or reinstall any genuine utilities that you didn’t want to lose.
The Power Eraser is an on-demand tool rather than a background process. It is only available for Windows.
aswMBR Rootkit Scanner
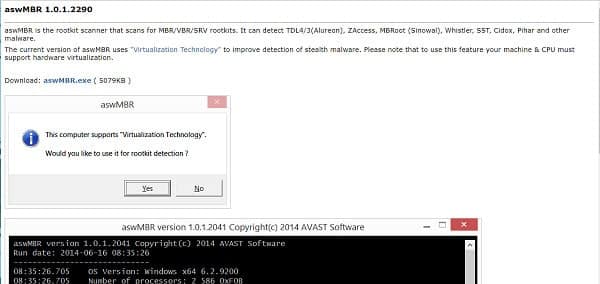
This rootkit searcher is a product of antivirus giant Avast. The user interface is not so hot, though, as you can use this system sweep for free, it’s worth a shot. This utility is only available for Windows.
GMER
GMER specialises in detecting and removing rootkits. The program scans for hidden processes, registry keys, threads, Alternate Data Streams, modules, services, files, and disk sectors. In addition, it looks for inline hooks and drivers hooking SSDT, IDT, and IRP calls.
GMER is free, though it will only work on Windows XP/ VISTA/ 7/ 8/ 10. It’s a good alternative to aswMBR.
Sophos is well-respected in the antimalware industry. Its free Scan & Clean program is designed to rescue computers that have become infected with rootkits, zero-day malware, Trojans, spyware, and other threats “capable of evading real-time protection from up-to-date antivirus software.”
Specifically, Sophos says that its proprietary “Cloud-Assisted Miniport Hook Bypass technology” allows it to defeat rootkit and bootkit hooks for any hard disk driver. Because it uses the cloud, the program automatically keeps itself updated. The only downside is that it’s currently only available for Windows.
Keylogger information
Keyloggers were originally invented as a method for employers to track what workers were doing on the company computers. They then became useful for hackers. Now web marketers are using them.
The Olympic Vision keylogger is an example of a hacker attack. This was discovered in March 2016 and managed to track the actions of computer users in 18 countries. This email-based hack used a zip file attachment to emails in order to gain entry to victims’ computers. The attack was specifically aimed at business, with the email text referring to an invoice or a quote that the receiver should download. This keylogger scam seems to have originated in South Africa.
In late 2022, the company behind the LastPass password manager disclosed a breach in which hackers stole encrypted and plaintext passwords for more than 25 million users.
LastPass said that attackers initially gained access by implanting keylogger malware on one of its developers’ home computers. This, it says, was achieved by “exploiting a vulnerable third-party media software package, which enabled remote code execution capability.” The implanted keylogger captured the employee’s master password and gave attackers access to the engineers LastPass corporate vault.
Keyloggers have also become acceptable tools for digital marketers. In November 2017, the BBC reported that more than 480 commercial websites included keylogging functions to monitor the activities of visitors.
Using keyloggers to gather behavioral information for the purposes of market research is just as much an invasion of privacy as the hacker use of this technology to steal passwords. The discovery of keyloggers by marketers seems to have given keylogging new respectability.
The BBC report was based on research carried out at Princeton University. The study reported that:
Collection of page content by third-party replay scripts may cause sensitive information such as medical conditions, credit card details and other personal information displayed on a page to leak to the third party as part of the recording. This may expose users to identity theft, online scams, and other unwanted behaviour.
Although digital marketers may declare that their intentions are not criminal, their actions are because none of the websites that now employ keylogging technology for marketing purposes inform their visitors of this feature. As the collection and storage of this information is kept a secret, the theft of recorded information would not need to be reported. This means that you now have to guard against apparently legitimate websites become conduits for the theft of your personal information.
It is very difficult to get rid of keyloggers once they get onto your computer. Therefore, you should be vigilant about the programs you’re downloading onto your computer. Be choosy about the free apps that you install.
It is also very important to keep all of your software updated. This is particularly the case with your operating system and your browsers. Big software providers constantly look for security weaknesses in their products and re-code them in order to block off these exploits. So keeping up to date with the latest versions of everything running on your computer is a key protection against all forms of malware.
Image: Finger auf Tastatur by Christoph Scholz via Flickr, licensed under CC BY-NC-SA 2.0











great
Thanks for sharing this information. I learnt alot. Thanks