What is doxxing?
Doxxing (also written as “doxing”) is an online threat to your privacy. Although this fad has been around in the hacker community since the 1990s, it is now become a major threat to anyone who uses the internet. Doxxing involves researching the details of people’s lives. The purpose of this practice is either to expose that person to legal prosecution, to embarrass the victim, to draw criticism towards that person, or to cause them physical harm.
People’s lives have been ruined by doxxing. Some doxxing attacks lead to a mass campaign of public shaming, the online equivalent of mobbing. The effects can cause people to lose their jobs, their families, and even their homes. Targets of major doxxing attacks have been forced into hiding and have had to delete all of their online accounts and change their identities.
So, let’s find out more about doxxing and how to avoid it.
The origins of doxxing
The term “doxxing” derives from a hacker word for “documents.” “Documents” became “docs” and then “dox.” When you “dox” someone, you are documenting their personal information. The important pieces of information you can find out are a person’s social security number, their address, telephone number, email address, social media profile names, place of work, details of relatives, partners and children, and so on.
The term first surfaced in the 1990s when hackers would dox a rival out of spite. In this case, the doxxing focused on identifying the hacker and his misdeeds and turning those details over to the authorities to get him arrested.
The purpose of doxxing
Doxxing is a weapon and it can be used for good or evil. However, it is mostly used as a method of attack. The Anonymous movement and its associates on the 4Chan message board are particularly keen on using doxxing as a way to punish enemies. 4Chan has millions of members, and a hate campaign launched against a celebrity or company leader on that site can be very destructive.
Mob attacks launched by 4chan include prank telephone calls, overwhelming amounts of abusive email, network-swamping quantities of text messages and even physical attacks on the individual.
Doxxing attacks
As doxxing is generally negative and often fuelled by the need for revenge, the victim doesn’t necessarily have to be a bad person. However, the attacker garners support by making false accusations against that person and publishing the contact details of the target. This was the case with Kyle Quinn, a biomedical engineer at the University of Arkansas. He was identified as taking part in a neo-nazi rally. However, it was simply a case of mistaken identity — the marcher looked a bit like him. Once doxxers got involved, however, his life, that of his family, friends, and colleagues became hell.
In Quinn’s case, he was fortunate that he had actually been in a public place on the night and had several colleagues from the University’s administration as witnesses to his innocence. The resources of the University helped him survive the attacks. Few people are that lucky.
Jessica Leonhardt of Florida launched a tirade on YouTube against 4Chan users back in 2010. For some reason, the 11-year-old had been accused on 4Chan of having sex with a member of the band, Blood on the Dancefloor. Thanks to doxxing, which revealed Jessica’s address and contact information, the young girl was overwhelmed with attacks both online, in person, and through email, phone and chat apps.
Her father got involved and posted a video in defense of his daughter to threaten those attackers to back down. The trolls had a field day. Within a year, Jessica’s father was dead of a stress-induced heart attack and the young girl was taken away to a mental institution.
The problem with doxxing
As the few cases above show, a stupid row or lack of correct information can lead to life-threatening mob attacks on individuals. An argument on social media can escalate to false accusations and a hate campaign. Doxxing adds teeth to these disputes, leading to psychological destruction or even physical attacks. Doxxing takes cyberbullying to the next level.
RELATED: Cyberbullying statistics
Without the research into personal information that doxxing involves, online disputes could be left online. However, knowing the address of enemies makes it possible to create a series of events that can kill.
SWATTING
Back in the day, if a prankster wanted revenge on someone, they would call up every pizza delivery place in the town, posing as the victim ordering pizzas. The target of this pizza delivery attack would soon have a front lawn full of angry pizza delivery boys demanding payment.
Now that doxxing can reveal the identity of an enemy on the other side of the world, prank attacks have intensified into seriously life-threatening situations. These attacks are known as SWATTING.
In a SWATTING attack, the perpetrator poses as the victim, but doesn’t call pizza parlors. He posts threats to shoot up the school and bomb football stadiums in a faked online account. The attacker makes sure to expose the discovered contact details of the victim to lead a trail to the target’s house. Alternatively, the attacker simply phones in an anonymous accusation to the local police claiming that the victim has a bomb and is plotting a terrorist attack.
A SWAT team or other police force then arrives on the front lawn, fully hyped up and armed. SWATTING is becoming an increasingly common form of revenge and could not be practiced without doxxing. A number of celebrities have been the targets of SWATTING. These include Taylor Swift, Chris Brown, Ashton Kutcher, Tom Cruise, and Miley Cyrus.
In a 2017 incident, two Call of Duty gamers falling out over a $1.50 bet resulted in a death thanks to SWATTING and flawed doxxing. Tyler Barriss of Los Angeles called the police in Wichita, Kansas, claiming to have shot someone and that he also held two hostages. The police SWAT team immediately went in force to the address. When Andrew Finch walked out of the house to find out what was going on, the SWAT team shot him dead.
Neither Barriss nor Finch were involved in the original Call of Duty dispute. Bayliss was acting on behalf of the disgruntled bet loser and acquired the wrong address for the target. That address was the home of Finch’s mother, whom he was visiting at the time.
Public sources of private information
Data brokers
Many places on the web hold your personal information. Businesses profit from storing and collating your information along with data about a lot of other people. Those businesses are called data brokers. They buy customer lists from other businesses. So, if you buy a flight, the airline may put you on a list that they sell to a data broker.
Everything you do is of interest to someone, particularly in the world of marketing. You might fill in a survey about your favorite soap, or enter a competition to win a cruise. The companies that entice you to give your opinion usually put in the small print that they have the right to store and/or sell the information that you put on the form. This gives them a second income stream that can help pay for the prize that they offer you as an incentive to take part. They sell your information to a data broker.
Data brokers generally don’t sell on information about individuals. However, hackers and doxxers sometimes work on large volumes of data, and once your information has been sold on, it can be automatically matched up with other information sourced from other lists. So, with a comparison of a few sources, doxxers can collate more precise details about a large number of people. This is a much quicker option than hacking the accounts of targets. However, the requirement to pay for this information makes it expensive.
You are able to demand that many data broker sites remove your information. However, this is a lengthy process, which is explained in more detail below.
WHOIS
If you run your own website, or you have a website for your business, the registration information that you filled in to get that domain name is made public to all the world through the WHOIS database. This data is accessible directly from the WHOIS site, or through a domain sales broker, such as GoDaddy.
You don’t have to give your personal information to get a website. Some domain brokers offer you the option of obscuring this information. However, you can get this privacy for free by entering a webmail email address, putting a fake telephone number in the form and giving a made up company name — they never actually call you or check on your name.
IP address
Every connection you make on the internet has to carry your internet address on it. This is called an IP address. Doxxers can use an IP logger to trace your online activities. An IP logger can track you and expose your identity when it is combined with searches on membership of certain sites. Your IP address is actually owned by your internet service provider. However, that information alone gives away details about you.
How to protect yourself against doxxing
The practice of doxxing is clearly escalating and the consequences are now fatal. So, you need to be cautious about the information that you make available online.
Social media
Unfortunately, most of us give away too much personal information on social media sites. You need to make sure that you only allow close friends to access your personal information. There are many that accept Friend requests from anyone. You may know people who have thousands of “friends” on Facebook. Don’t be one of those people. Only allow people that you know very well to be your friends on Facebook. Be cautious about “friending” colleagues from work — they could soon become rivals.
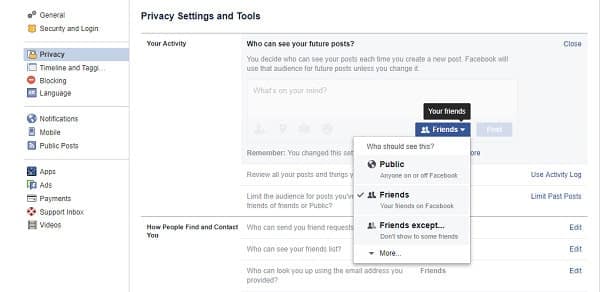
- In Facebook, click on the down arrow in the top menu bar and select Settings in the drop-down menu.
- Select Privacy in the left-hand menu and then click on Edit next to Who can see your future posts.
- In the next screen, select Friends from the drop-down list and then click on Close.
Avoid posting details about where you work and don’t write about where your children go to school. Although it is a great joy to share your favorite moments with friends on social media, it is safer to enforce a policy of not posting photos of your children and ask anyone else who takes pictures of them at events not to post them online.
Many sites allow you to log in with Facebook, Google Plus, or your Gmail account. Don’t take that option. This enables that site to access all of your personal details from the social media profile that you choose to log in with.
RELATED: How to improve your security and privacy on Facebook
Protect your internet communications
Hackers can read your internet data even if the content is encrypted. Every connection that you make on the internet has your internet address on it and that can be traced to a location. So, obscure your internet activity by installing a VPN.
Be cautious about using public wifi hotspots because these can be intercepted by fake hotspots put up by hackers. In this respect, a VPN can help you as well.
Protect the data on your computer
Doxware is a type of malware. This is another name for spyware, which will try to steal your personal information and passwords for online services.
Keep hackers away from this personal information by installing antimalware. Although some antimalware systems can seem to slow your computer down, don’t be tempted to turn it off. You should also make sure that you allow this software to check for updates and install them automatically.
Remove your personal data from your apps
Not everyone does this, but it is possible to write your identity into the settings of a lot of apps that you use. For example, you can put your name in the properties of your Microsoft Office apps. This means that every document you send out will have your name on it. If you have entered your name in the properties of any app, delete it.
Similarly, check out the settings on the gadgets that you own. Make sure that the operating system of your smartphone doesn’t have access to your email address or any other personal information. Check the settings of your camera, your webcam, your set top box and your games consoles and make sure that your name or any other personal information is not in there.
Protect your email identity
Create a second, “burner” webmail account to use for those sites that require an email address from you when you register. There are a lot of exciting new websites out there and you may be keen to join. However, some of those are doxxing harvesting sites and you need an escape hatch to make sure you can bail on those sites without leaving real personal information out there.
Email is a very insecure form of communication. Although many email services encrypt mail in transit, all emails are stored at an intermediate server in plain text before they arrive at the Inbox of the recipient. Check out secure email systems to improve your privacy. Check out email systems with built-in encryption, such as Mailinator.
Vary usernames and passwords
If you like to visit porn sites, or sites with strong political aims, create a separate persona for them. Don’t create the same username on these sites and always vary your password.
Many people use the same password for every site that they subscribe to. However, the danger of this strategy of convenience is that if you hit on a fake website, the hacker that created that site will have that one password that you use everywhere. Use a password locker to create different passwords for each site that you sign up for.
Get your information removed in the EU
In the EU, you have the right to be forgotten. This legislation particularly relates to search engine results. If you get search engines to delist information on you, doxxers will have a lot more difficulty tracking your data.
You can fill out a form at Google to get them to remove search results that relate to you. Bing also has a privacy removal request form. You can also request that Yahoo removes information about you from its search engine results.
The situation on holding personal information is getting tighter in Europe. In May 2018 a new EU directive on the privacy of data, called the General Data Protection Regulation, will come into force. This will make it much harder for companies to hold information on you. However, there is no clear procedure for demanding that your data is removed and there will be no central registry.
The GDPR will make it possible for class action lawsuits to be launched against companies that do not sufficiently protect the personal data that they hold, if they transfer that data outside of the EU, or if they fail to notify individuals of the information that they have on file about them.
Self-doxxing in the USA
Tracing the information that is held about you is not a doxxing issue as long as that information does not get leaked. The process of protecting yourself from information leakage is called “self-doxxing.” This refers to researching the information that is available on the web rather than uncovering the information that companies hold about you in secret.
You can get a quick rundown on where hackers can find you at have i been pwned?. AccessNow has more information on how you can self-dox.
In the USA, you can ask Google to remove information about you from their search engine results pages and other Google services.
After that, visit and ask these sites to remove your data. Here is a list of where to start, but this is not exhaustive:
- BeenVerified: https://www.beenverified.com/faq/opt-out/
- CheckPeople: https://checkpeople.com/do-not-sell-info
- Instant Checkmate: https://www.instantcheckmate.com/opt-out/
- Intelius: https://www.intelius.com/opt-out/
- Nuwber: https://nuwber.com/removal/link
- PeekYou: http://www.peekyou.com/about/contact/optout/index.php
- PeopleFinders: http://www.peoplefinders.com/opt-out
- PeopleSmart: See BeenVerified
- Pipl: https://pipl.com/personal-information-removal-request
- Radaris: http://radaris.com/page/how-to-remove
- Spokeo: http://www.spokeo.com/opt_out/new
- TruthFinder.com: https://www.truthfinder.com/opt-out/
Check out the services of AccountKiller, OneRep, DeSeat.Me, and DeleteMe, who will help identify information about you in the USA and get it removed so you don’t have to go to every site yourself.
Avoid doxxing
Unfortunately, although the World Wide Web gives you the freedom to express yourself, it also gives other the freedom to access all of the information that you put out there. So, if you feel you may be vulnerable to identity theft or profiling, be cautious about what you write on the web.
Although it is not fair to blame the victim, the example of Jessica Leonhardt show that you can provoke doxxing. If you intend to be controversial, you should take extra steps to prevent your identity for being discovered. Make sure you only use pseudonyms when you post comments online and try not to show identifying details if you post a video — such as your location and your face.
Doxxing can ruin your life, so be careful about the information that you make available on the web.
If I report a doxxing attack to law enforcement, will they know what I’m talking about?
If you’re worried about reporting a doxxing attack to the police, don’t be. They should know what you’re talking about. Doxxing, which is when someone shares your personal info without your okay, is a big problem these days, especially with social media everywhere. Law enforcement are dealing with this kind of stuff more and more, so they should be able to help you out.
When you report it, ensure you’ve got evidence, like screenshots or downloads of the webpage where it happened. This will help the police act quickly and effectively. How serious the doxxing is and the kind of threats you’ve received will affect how much the law enforcement can do. In some cases, doxxing is a crime, and the person who did it could be banned, suspended, or even prosecuted.
If you need more clarification about the laws in your area, it’s a good idea to talk to a lawyer. They can give you the most current info and advice.
Image from: Socialmediahacked via Pixabay by TheDigitalArtist, licensed under CC0




Doxing has been a problem for many years now, why isn’t anything being done about it, like new laws or Congressional action? Seems like Congress actually supports this behaviour behind the scenes.