
As remote work becomes increasingly common, ensuring secure access to company networks for home workers has become a top priority for businesses. One of the most effective ways to achieve this is by setting up a secure Virtual Private Network (VPN). A VPN creates an encrypted connection between remote workers and the company network, ensuring that sensitive data remains protected while it travels over the internet.
The need for secure remote access has never been more critical. Cyber threats such as data breaches, hacking attempts, and even insider attacks can easily compromise unprotected connections, especially when employees are using home Wi-Fi networks or public internet connections. A VPN provides a secure tunnel for data, making it much harder for cybercriminals to intercept or eavesdrop on communications.
This guide will walk you through the process of setting up a secure remote access VPN for home workers. We’ll cover everything from selecting the right VPN solution for your business needs, configuring VPN servers, and ensuring that encryption protocols are properly implemented, to managing user access and authentication. We will also discuss best practices for monitoring and maintaining your VPN to ensure that it continues to provide reliable and secure access over time.
By the end of this guide, you’ll have a clear understanding of how to establish a secure, reliable, and scalable remote access VPN solution that allows home workers to connect safely to your organization’s resources. Whether you’re an IT professional or a business owner, this guide will help you navigate the complexities of remote access security and protect your company’s digital assets.
How a VPN Works
A VPN allows you to create a secure virtual tunnel to your office network through the public network such as the Internet. It protects confidentiality (data remains secret via encapsulation) and integrity (data remains unaltered via encryption) of data as it travels over the public internet. You can liken VPN tunneling to the process of moving physical cash from one location to another using an armored transport van along public highways. The cash in this instance is your data, the public highway is the non-secure public network, and the armored van is the VPN tunnel. Encapsulation disguises the van so in most cases it won’t be recognized as a vehicle carrying cash, while encryption ensures that even if the van is recognized, no one can access the cash inside. The diagram in Figure 1.0 below helps you visualize the process.
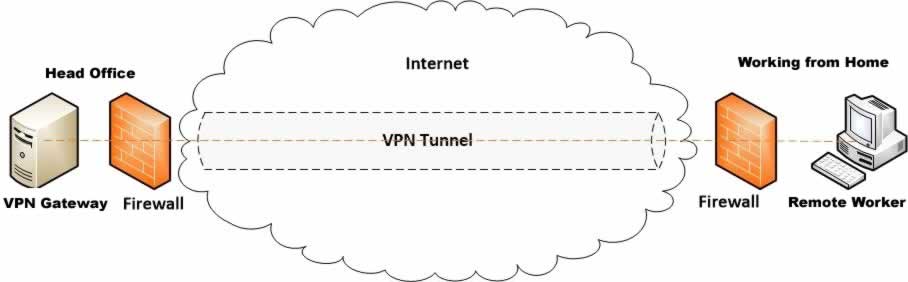
Establishing a secure VPN connection is relatively simple. The user first connects to the internet and then initiates a VPN connection via a locally installed client software or web browser to the VPN server located in the office. The VPN server based on your access level permission grants you access to internal company resources via the secure tunnel; thus, keeping data secure and private over the internet. Below are the different possible ways you can implement an office VPN so your employees can remotely access office resources without compromising security. We’ll go into each of these in more detail.
- Remote access VPN
- Cloud VPN
- SD-WAN VPN
Remote Access VPN
Remote-access VPNs just as the name implies, allow mobile employees or remote workers to access their company’s intranet from home or anywhere in the world using their personal computers or mobile phones. Users can access the resources on the office computers as if they were directly connected to the office network. The two most commonly used technologies in remote access VPNs are IPSec and SSL.
IPsec is the most widely used VPN technology. Because it provides protection at the IP level layer (Layer 3), it can be deployed to secure communication between the office network and a host computer used at home. A client application is required at the host computer in order to establish a connection. IPsec was designed to ensure data integrity and confidentiality, and offers enterprise-grade security features.
The greatest strength of SSL VPN comes from the fact that it is platform-independent. You do not have to depend on a third-party VPN client to initiate connections. Using any web browser, you can access resources remotely without worrying about the underlying operating system.
In order to setup an office VPN (IPsec or SSL VPN) to support working from home, you’ll need to purchase, install and configure a hardware device known as VPN Gateway in your office location. Some of the leading VPN hardware vendors/products include Cisco ASA firewall for SSL VPN and IPsec VPN, Check Point Next Generation Firewall, and Sophos XG Firewall, among others. Configuring the VPN itself is quite vendor-specific and would require the services of qualified personnel such as a Network Engineer or a third-party service provider, but some devices have a GUI user interface or a wizard-type configuration process.
The initial investment needed to set up a remote access VPN is minimal and they can easily be scaled as a company grows. This is especially true if a VPN service provider is used. Because remote access VPNs are affordable and secure, organizations can feel more comfortable deploying them and allowing their employees to work from home.
See also: IPSec vs SSL
Cloud VPN
A Cloud VPN, also known as VPN as a Service (VPNaaS) is a novel VPN technology that’s specifically designed for cloud-based applications and data. Many modern businesses have transitioned their local network environment, business applications and data into the cloud, and conventional VPNs such as those described above are no longer enough to ensure data security.
Employees usually access these cloud applications and data from the office network; but with the COVID-19 pandemic, for example, employees were increasingly relying on their own home network, personal computers and mobile devices to access these applications. This raised a lot of security concerns. While cloud service providers offered the network infrastructure, it did not provide security for personal devices used by end-users.
The objective of cloud VPN is to give employees and remote workers secure access to cloud resources through a cloud-based VPN infrastructure over the public Internet from any location in the world without undermining security. Unlike traditional VPNs, which require some sort of on-premise VPN infrastructure, a Cloud VPN provides a globally accessible secure connection. For organizations whose business LAN environment or day-to-day business applications (such as ERP or Active Directory Services) have moved to the cloud, Cloud VPN offers the best alternative for cheap and secure access.
Cloud VPN services can be obtained from providers such as Check Point’s SASE and NordLayer can be configured in a matter of hours or minutes to establish a Site-To-Site IPSec VPN tunnel to your cloud servers. Most cloud service providers such as Google, Microsoft and Amazon also provide Cloud VPN services.
See also: Best Cloud VPNs for Business
SD-WAN VPN
For businesses that house both on-premise and cloud-based applications, neither Remote Access VPN nor Cloud VPN is adequate to ensure unified end-to-end data security. One technology that can adequately address this unique business requirement is Software-Defined WAN (SD-WAN) technology.
See also: Best SD-Wan Vendors
SD-WAN is a virtual wide area network (WAN) architecture that allows organizations to leverage any combination of network transport technologies such MPLS, 4G/LTE and broadband internet services to securely connect users to the office intranet and applications. SD-WAN is necessitated by the fact that organizations have become more geographically dispersed and utilize a growing number of cloud-based applications.
Traditional WAN approaches using conventional routers are not cloud-friendly. They were designed around on-premise applications. Today, deploying a mix of on-premise and cloud-based applications and connecting people and ‘things’ is the new norm. This shift is giving rise to an alternative VPN technology that is more dynamic – SD-WAN VPN. The SD-WAN model is designed to fully support secure remote access to critical enterprise applications hosted on-premise and in the cloud (such as Office365 for business, Dynamic 365 ERP, Salesforce, Service Now, Hosted Active Directory, etc.), while delivering the highest levels of application performance. This approach provides a consistent user experience as well as the cost benefits of internet-based VPNs with the performance and agility of MPLS VPNs regardless of location.
SD-WAN products can be physical appliances or virtual appliances and are placed in remote and branch offices, corporate data centers, and increasingly on cloud platforms. Most network appliance vendors such as Cisco, Juniper, and Aryaka, among others, also offer SD-WAN products. The Aryaka SmartACCESS SD-WAN solution, for example, delivers clientless SD-WAN VPN for the remote and mobile workforce. If you are considering deploying SD-WAN VPN for remote working, you will require the services of an SD-WAN managed service provider (SD-WAN as a Service) or a skilled Network Engineer. The network diagram in Figure 2.0 below helps visualize the SD-WAN setup.

For the transition to remote work and granting staff secure access to both on-premise and cloud-based applications, SD-WAN VPN promises to be the viable option. The SD-WAN approach of orchestrated, template-driven policies can be neatly applied to remote access, allowing access to be controlled in consistent ways. The table in Figure 3.0 below is a brief comparison of the various VPN technologies discussed above.
| Features | Remote Access VPN | Cloud VPN | SD-WAN VPN |
|---|---|---|---|
| Ideal For | Secure access to on-premise applications and data | Secure access to cloud applications and data | Secure access to on-premise and cloud applications and data |
| Target Consumer | Business | Business | Business |
| Deployment Skill Level | skilled labor | skilled labor | Highly skilled labor |
| Performance | Good | Good | Very Good |
| Pricing Model | One-time fee or subscription based | Subscription based | One-time fee or subscription based |
Remote access VPN FAQs
Can I work from home with a VPN?
A remote worker can become part of the office network by using a secure link that is protected with a VPN. While consumer VPN systems connect the user to a VPN server, which is based in the cloud, a remote access VPN needs to have an office server set up as the destination of the connection. Once established, the VPN connection persists and all of the traffic from the user’s computers travels down that tunnel. This means that the user is locked into the office network and can’t perform any other direct connections to the internet while the VPN session is live.
Does VPN work on all devices in a house?
A VPN can cover all devices in a house with one installation if the VPN client software is installed on the home router. For the remote access needed by work-from-home employees, placing the VPN on the home router is a bad idea. This is because the remote access jams all access to the internet other than through the company network. So, a router install would channel all of the traffic of your family to the company network as well. As corporate networks are set up to block internet access for leisure purposes, your family would be blocked from accessing video and games sites while you are logged into the office.
Do I need a VPN to work from home?
Whether or not you need a remote access VPN set up to get into the company network and work from home depends on your company’s network security policy. A new virtual network architecture is emerging, called secure access service edge (SASE), which is more appropriate for linking together sites, cloud platforms, and remote workers.


Very good article explaining secure remote access VPN for home users. A virtual private network (VPN) gives you online privacy and anonymity by creating a private network from a public internet connection. VPNs mask your internet protocol (IP) address so your online actions are virtually untraceable. Somme good VPN`s are express VPN, Logmein Hamachi, R-HUB remote support servers, Logmein, Teamviewer etc.