Plenty of other articles out there compare and contrast IPSec vs SSL VPNs from the perspective of a network admin who has to set them up. This article, however, will examine how major commercial VPN providers utilize SSL and IPSec in their consumer services, which are intended to provide access to the web and not a corporate network.
VPN protocols that use IPSec encryption include L2TP, IKEv2, and SSTP. OpenVPN is the most popular protocol that uses SSL encryption, specifically the OpenSSL library. SSL is used in some browser-based VPNs as well.
This article compares and contrasts IPSec vs SSL encryption from the VPN end-user standpoint.
The basics of VPN encryption
VPN encryption scrambles the contents of your internet traffic in such a way that it can only be un-scrambled (decrypted) using the correct key. Outgoing data is encrypted before it leaves your device. It’s then sent to the VPN server, which decrypts the data with the appropriate key. From there, your data is sent on to its destination, such as a website. The encryption prevents anyone who happens to intercept the data between you and the VPN server—internet service providers, government agencies, wifi hackers, etc—from being able to decipher the contents.
Incoming traffic goes through the same process in reverse. If data is coming from a website, it first goes to the VPN server. The VPN server encrypts the data, then sends it to your device. Your device then decrypts the data so you can view the website normally.
All of this ensures that VPN users’ internet data remains private and out of the hands of any unauthorized parties.
The differences between varying types of encryption include:
- Encryption strength, or the method and degree to which your data is scrambled
- How the encryption keys are managed and exchanged
- What interfaces, protocols, and ports they use
- What OSI layers they run on
- Ease of deployment
- Performance (read: speed)
What is IPSec and what is SSL?
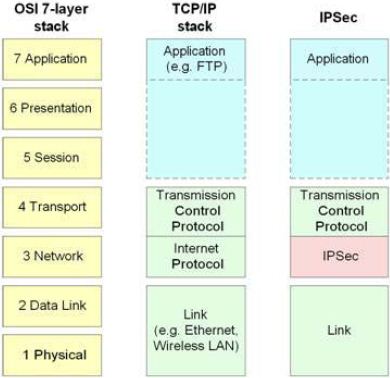
- SSL (Secure Sockets Layer) operates at the application layer of the OSI model. It encrypts the data exchanged between the user’s browser and the web server.
- IPsec (Internet Protocol Security) secures internet communication at the network layer. It is a suite of protocols for encrypting and authenticating network traffic.
For a more detailed explanation of the two protocols, check out our in-depth guide on common types of encryption.
Security
In short: Slight edge in favor of SSL.
IPSec connections require a pre-shared key to exist on both the client and the server in order to encrypt and send traffic to each other. A pre-shared key (PSK) is a is a piece of data — known only to the parties involved — that has previously been securely shared between two computers before it needs to be used.
The exchange of this key presents an opportunity for an attacker to crack or capture the pre-shared key. PSKs are vulnerable to Man-in-the-Middle (MitM) attacks, brute force and dictionary attacks.
SSL VPNs don’t have this problem because they use public key cryptography to negotiate a handshake and securely exchange encryption keys. Public key cryptography, also known as asymmetric cryptography, uses a pair of keys for secure communication: a public key and a private key. Unlike symmetric cryptography, where the same key is used for both encryption and decryption, public key cryptography uses two different but mathematically related keys.
SSL vulnerabilities
Despite this, TLS/SSL has a long list of its own vulnerabilities. These include Padding Oracle on Downgraded Legacy Encryption (POODLE), Browser Exploit Against SSL/TLS (BEAST), Browser Reconnaissance and Exfiltration via Adaptive Compression of Hypertext (BREACH), and Heartbleed.
Some SSL VPNs allow untrusted, self-signed certificates and don’t verify clients. This is particularly common in “clientless” SSL VPN browser extensions. These VPNs that allow anyone to connect from any machine are vulnerable to man-in-the-middle (MITM) attacks. However, this is not the case with most native OpenVPN clients.
SSL typically requires more frequent patches to keep up to date, for both the server and client.
The lack of open-source code for IPSec-based VPN protocols may be a concern for people wary of government spies and snoopers. Open-source code allows anyone to examine it for vulnerabilities and suggest fixes. Closed-source code is manipulated in-house and hidden from the end-user.
In 2013, Edward Snowden revealed the US National Security Agency’s Bullrun program actively tried to “insert vulnerabilities into commercial encryption systems, IT systems, networks, and endpoint communications devices used by targets.” The NSA allegedly targeted IPSec to add backdoors and side channels that could be exploited by hackers.
In the end, strong security is more likely the result of skilled and mindful network administrators rather than choice of protocol.
Firewall traversal
In short: SSL-based VPNs are generally better for bypassing firewalls.
NAT firewalls often exist on wifi routers and other network hardware. To protect against threats, they throw out any internet traffic that isn’t recognized, which includes data packets without port numbers. Encrypted IPSec packets (ESP packets) have no port numbers assigned by default, which means they can get caught in NAT firewalls. This can prevent IPSec VPNs from working.

To get around this, many IPSec VPNs encapsulate ESP packets inside UDP packets, so that the data is assigned a UDP port number, usually UDP 4500. While this solves the NAT traversal problem, your network firewall may not allow packets on that port. Network administrators at hotels, airports, and other places may only allow traffic on a few required protocols, and UDP 4500 may not be among them.
SSL traffic can travel over port 443, which most devices recognize as the port used for secure HTTPS traffic. Almost all networks allow HTTPS traffic on port 443, so we can assume it’s open. OpenVPN uses port 1194 by default for UDP traffic, but it can be forwarded through either UDP or TCP ports, including TCP port 443. This makes SSL more useful for bypassing firewalls and other forms of censorship that block traffic based on ports.
Speed and reliability
In short: Both are reasonably fast, but IKEv2/IPSec negotiates connections the fastest.
Most IPSec-based VPN protocols take longer to negotiate a connection than SSL-based protocols, but this isn’t the case with IKEv2/IPSec.
IKEv2 is an IPSec-based VPN protocol that’s been around for over a decade, but it’s now trending among VPN providers. Driving its deployment is its ability to quickly and reliably reconnect whenever the VPN connection is interrupted. This makes it especially useful for mobile iOS and Android clients that don’t have reliable connections or those that frequently switch between mobile data and wifi.
As for actual throughput, it’s a toss-up. We’ve seen arguments from both sides. In a blog post, NordVPN states that IKEv2/IPSec can offer faster throughput than rivals like OpenVPN. Both protocols typically use either the 128-bit or 256-bit AES cipher.
The extra UDP layer that many providers put on IPSec traffic to help it traverse firewalls adds extra overhead, which means it requires more resources to process. But most people won’t notice a difference.
On most consumer VPNs, throughput is determined largely by server and network congestion rather than the VPN protocol.
See also: Fastest VPNs
Ease of use
In short: IPSec is more universal, but most users who use VPN providers’ apps won’t notice a huge difference.
IKEv2, SSTP, and L2TP are built-in IPSec-based VPN protocols on most major operating systems, which means it doesn’t necessarily require an extra application to get up and running. Most users of consumer VPNs will still use the provider’s app to get connected, though.
SSL works by default in most web browsers, but a third-party application is usually necessary to use OpenVPN. Again, this is usually taken care of by the VPN provider’s app.
In our experience, IKEv2 tends to offer a more seamless experience than OpenVPN from an end-user standpoint. This is largely due to the fact that IKEv2 connects and handles interruptions quickly. That being said, OpenVPN tends to be more versatile and may be better suited to users who can’t accomplish what they want with IKEv2.
When it comes to corporate VPNs that provide access to a company network rather than the internet, the general consensus is that IPSec is preferable for site-to-site VPNs, and SSL is better for remote access. The reason is that IPSec operates at the Network Layer of the OSI model, which gives the user full access to the corporate network regardless of application. It is more difficult to restrict access to specific resources. SSL VPNs, on the other hand, enable enterprises to control remote access at a granular level to specific applications.
Network administrators who operate VPNs tend to find client management a lot easier and less time-consuming with SSL than with IPSec.
IPSec vs SSL VPNs: Conclusion
All in all, for VPN users who have both options, we recommend going for IKEv2/IPSec first, then turning to OpenVPN/SSL should any issues crop up. The speed at which IKEv2 is able to negotiate and establish connections will offer a more tangible quality-of-life improvement for the average, everyday VPN user, while offering comparable security and speed — but it may not work under all circumstances.
OpenVPN/SSL was until quite recently considered the best VPN combination for most users of consumer VPNs. OpenVPN, which uses the OpenSSL library for encryption and authentication, is reasonably fast, very secure, open source, and can traverse NAT firewalls. It can support either the UDP or TCP protocol.
IKEv2/IPSec presents a new challenger to OpenVPN, improving on L2TP and other IPSec-based protocols with faster connections, more stability, and built-in support on most newer consumer devices.
SSL and IPSec both boast strong security pedigrees with comparable throughput speed, security, and ease of use for most customers of commercial VPN services.
Image credit: “IPsec in de netwerklaag” by Soufiane Hamdaoui licensed under CC BY-SA 3.0
IPSec vs SSL VPNs FAQs
Do SSL VPNs hide IP addresses?
SSL VPNs can provide anonymity by hiding IP addresses, but they can also be configured to reveal IP addresses. It all depends on how the SSL VPN is configured. If you want complete anonymity, you’ll need to make sure that the SSL VPN is configured properly to avoid activities leaking to your ISP.


