Many people are familiar with Tor. Tor is an anonymous network overlaid on the public internet that allows its users to anonymously access the internet, and to use internal Tor websites that reside only within the Tor network. These types of anonymous networks are called dark webs because they are not searchable like the public internet, and users need special software to access them. Tor is the most well-known dark web, but the Invisible Internet Project (I2P) is arguably more anonymous, albeit much smaller.
RELATED: How to access the dark web
Contents [hide]
I2P vs Tor vs Freenet
The most common use of Tor is to access the public internet anonymously. Users connect to the Tor network and pass through it to the regular internet, called the clear web. When Tor is running, internet traffic is routed through the Tor network in such a way that it is difficult to to correlate a request entering the Tor network with the same request exiting the network. In addition, services can reside inside the Tor network meaning that the traffic never exits Tor to the clear web. I2P has limited support for clear net access, but has the same basic dark web function in that it supports sites that exist inside the I2P network.
RELATED: The ultimate guide to Tor
Garlic routing
The word Tor is derived from its routing technology named The Onion Router. Onion routing involves encrypting data packets in layers of encryption. Each node only decrypts the layer it needs to understand where to send the packet next. In that way, the layers of encryption are said to resemble the layers of an onion. I2P does not use onion routing. Rather, it uses garlic routing.
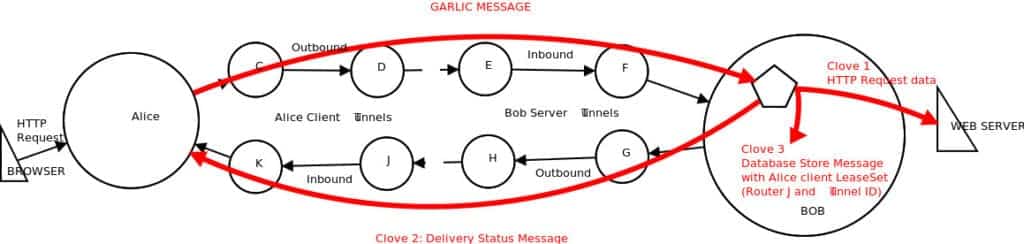
Garlic routing is a variation of onion routing that clumps messages together much like a garlic bulb has many cloves. The layered “onion” method of Tor means that a single packet is encrypted repeatedly but it is still a single message. This makes timing observations —- a method to correlate a Tor entry and exit node — easier. To reduce the risk of a single message being used by an observer in this way, I2P bundles messages together in a packet where each message is like a clove hanging off a garlic bulb Another important feature of garlic routing is that it is uni-directional. This means that data sent through I2P takes one path to get to the destination site and a different path to send data back to the requester. This make observation more difficult because it’s not possible to know what path the other half of the conversation is taking. Tor’s routing is bi-directional, meaning that traffic to and from the destination take the same path through Tor.
Eepsites
An I2P site is called an eepsite, which is analogous to a Tor onion service. An eepsite is just a normal website with the notable exception that it is only available to users who are connected to I2P. An eepsite is analogous to the more well-known Tor onion sites.
One use of Tor is to create an onion service, which is a website only accessible when connected to the Tor network. This type of Tor use has even greater anonymity because the traffic never leaves the Tor network, so it is difficult to even see the traffic, never mind spy on it.
Outproxies
I2P is a little different than Tor, although they both have the same aim. It is technically possible to set up an I2P exit node (called an outproxy in I2P parlance) but in practice I2P is not generally used that way. I2P is almost exclusively used to access eepsites sites instead of using it as an anonymous way to access the public internet.
Freenet
Freenet is another anonymity-based darknet. Unlike I2P or Tor, Freenet is not designed to be a proxy to the clear web, therefore there is no such concept as outproxies or exit nodes. Freenet is primarily concerned with the anonymous distribution and storage of content across the Freenet which can be retrieved by other Freenet users even after the publishing node goes offline. Internal Freenet sites are named freesites which is synonymous with Tor’s onion sites and I2P’s eepsites. Like other darknets, Freenet encrypts data in transit and at rest, and routes traffic through an arbitrary number of nodes to obfsucate the originator. No Freenet node knows whether the node it is forwarding data to is the final destination or just another node along the way. Upon receipt of a request, each node checks its local content cache to see if it has the requested content. If it does not, it sends the request to its next neighbor node. If it does have the content, the node sends it back along the same path, and the nodes along the way will cache that content to make future requests faster.
Installing the I2P client
The IP2 project has applications for Windows, macOS, Linux, and Android. The only notable exception is iOS.
To get started, grab the version of the I2P client that fits your operating system from this page.
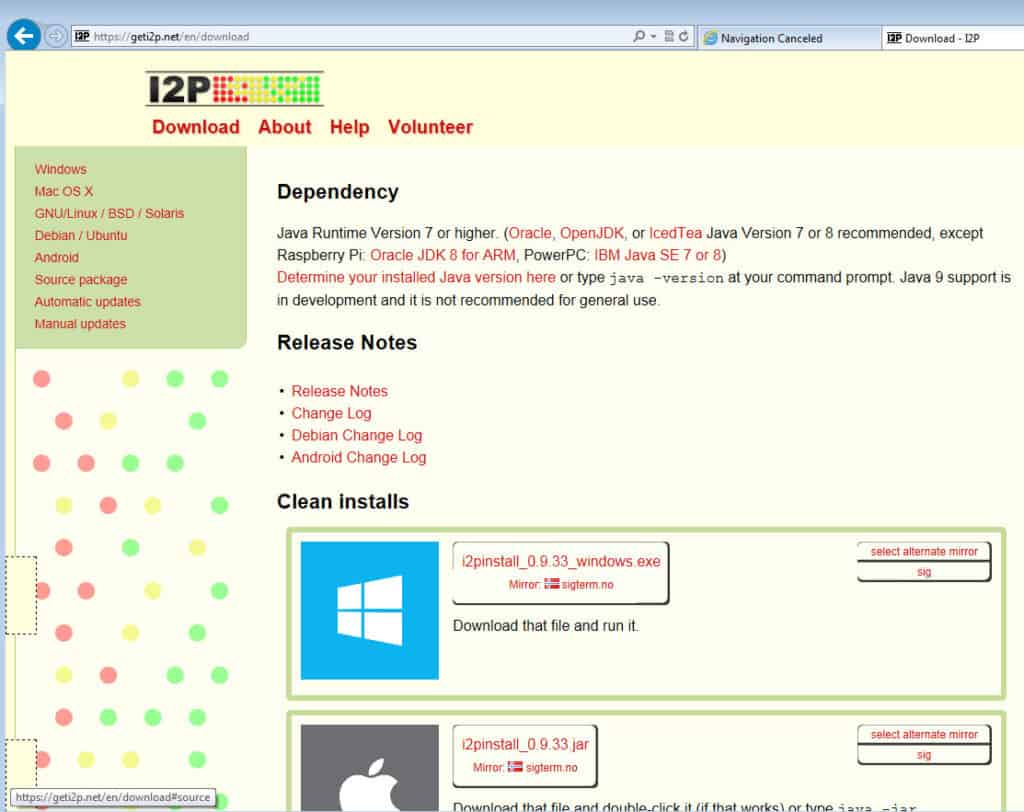
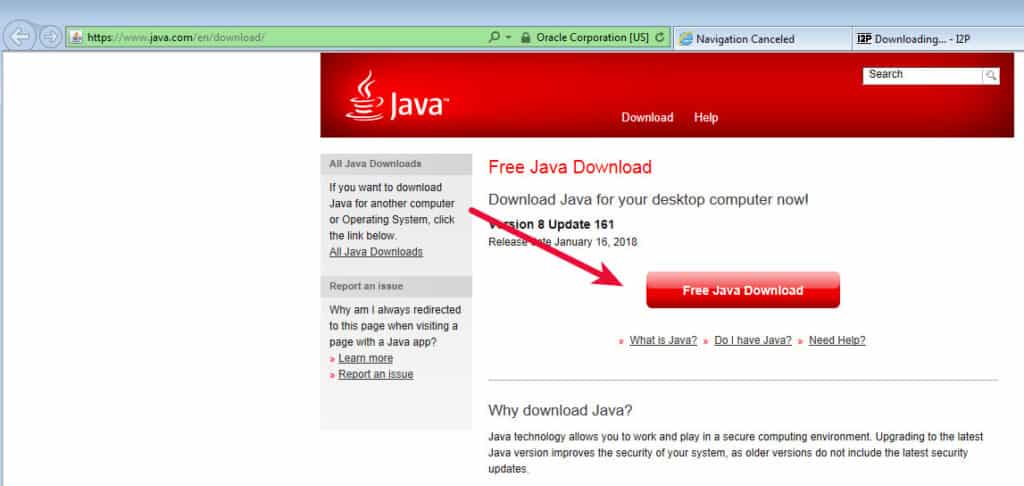
I2P requires Java. If you don’t have a suitable Java installation on your computer, the I2P installation will fail with a message to that effect. It will then bring you to the Java homepage to install Java so you can continue with the installation.
Select the Windows Service option if you want I2P to run all the time beginning at Windows startup. If you want to easily toggle I2P on and off as you need it, leave that checkbox blank.
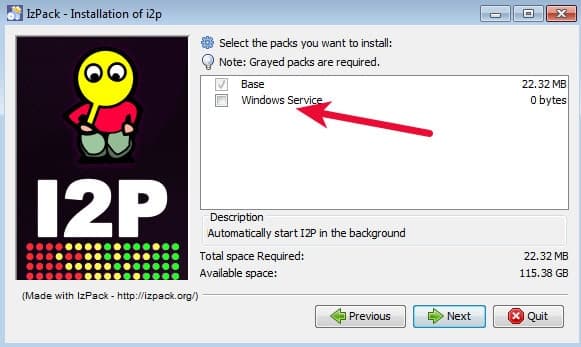
The rest of the installation is very straightforward. If you’ve left the default settings alone during installation you will see an I2P group in your Start Menu. Click one of the Start I2P options to get it running, and then click the I2P router console entry to view and configure the I2P router.
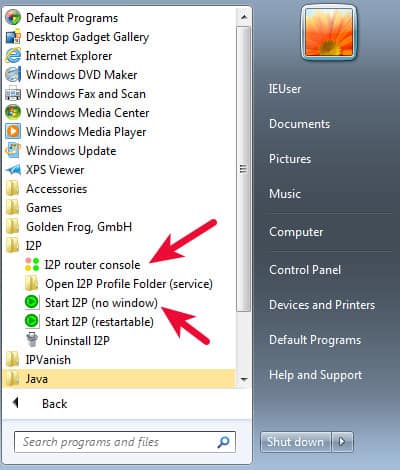
Using I2P
The I2P router console is the place to control everything about your I2P usage. The router application runs quietly in the background and you will interface with it via your web browser at 127.0.0.1:7657. Note that just because the router is running does not mean your applications are using it. The first thing you will likely want to do is configure your browser to use I2P. If you have not done this, your browser will not be able to resolve eepsites and will show some kind of DNS resolution error like this one from Internet Explorer.
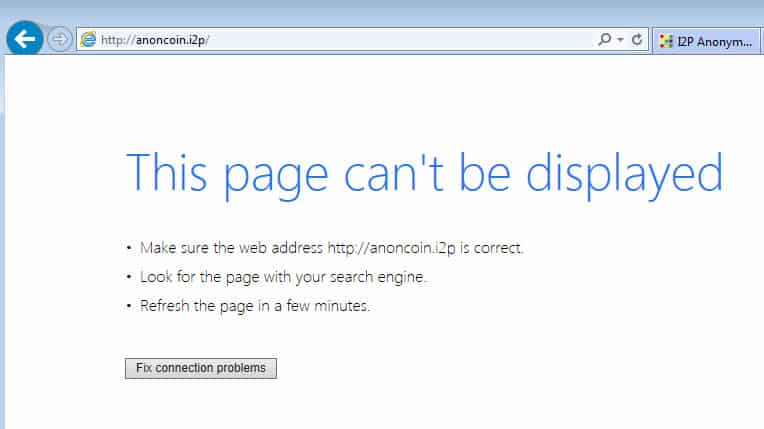
The cure for this is to tell your browser to use the I2P proxy that the router provides. The router home page states, “Also you can setup your browser to use the I2P proxy to reach eepsites. Just enter 127.0.0.1 (or localhost) port 4444 as a http proxy into your browser settings. Do not use SOCKS for this.” It contains directions on how to configure a proxy for most browsers on the clearnet I2P page here.
Browsers such as Internet Explorer and Firefox have their own internet connections settings. Within those settings it is possible to configure the browser to use the I2P proxy on port 4444 of your computer. For example, in Internet Explorer the path is Settings -> Internet Options -> Connections Tab -> LAN Settings button to get here:
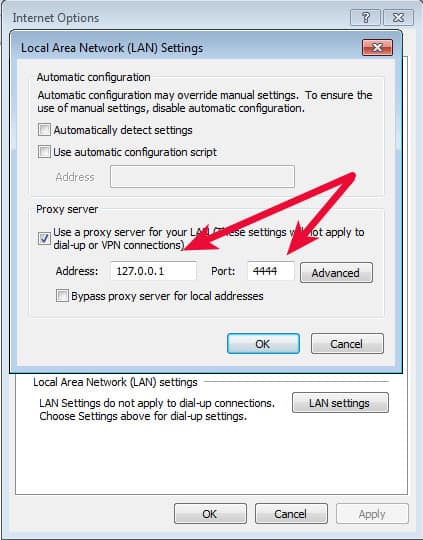
If you’ve set the proxy up correctly, you will be able to browse eepsites now such as the I2P dev forum at http://zzz.i2p (eepsite)
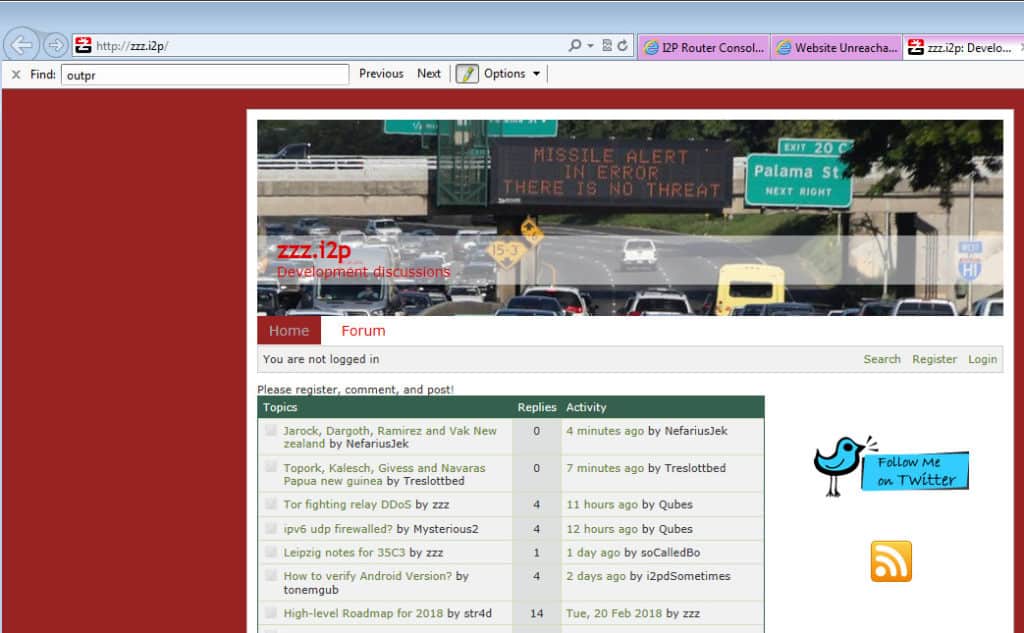
To resume browsing the internet you’ll need to remove those proxy settings. All this repeated configuration can be a pain and a much easier way to handle it is to use a proxy plugin such as FoxyProxy. FoxyProxy can automatically use the I2P proxy for eepsites and the regular internet for everything else with three simple steps.
Add the FoxyProxy plugin
FoxyProxy is available for Chrome and Firefox. Keep in mind that any proxy plugin will necessarily see all of your internet traffic so you need to trust it.
Add the I2P proxy on locahost port 4444
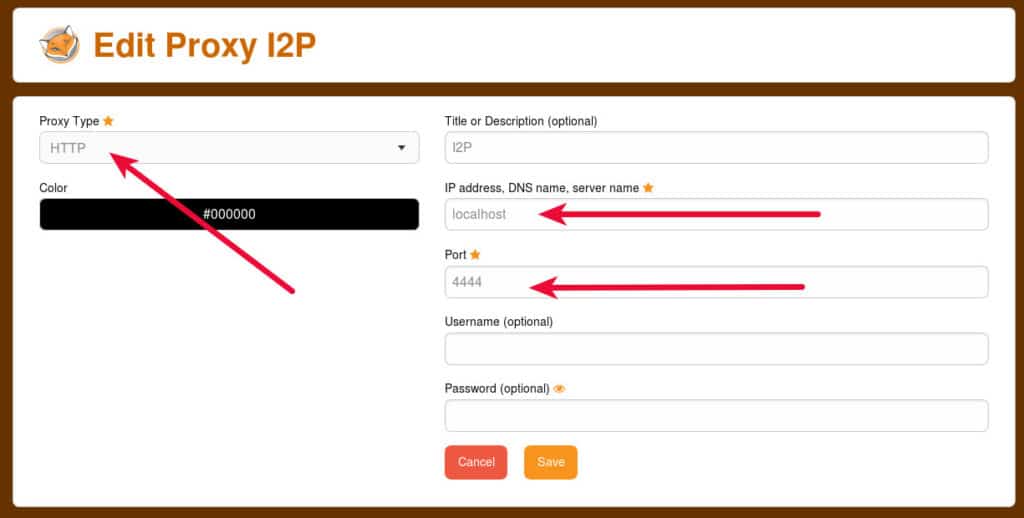
Add in a URL pattern so that FoxyProxy will only use that I2P setting for eepsites
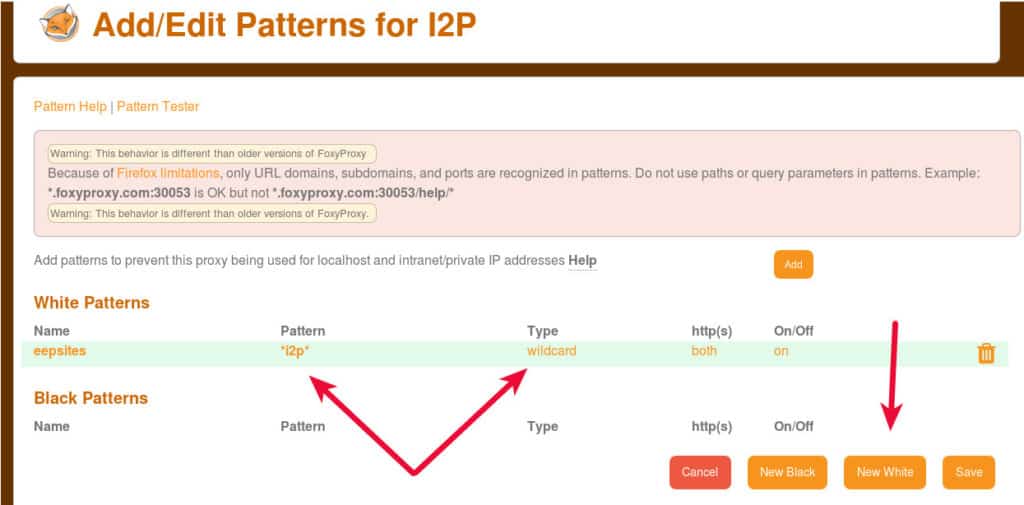
Warning: Setting Foxyproxy up like this will not route your regular internet traffic through I2P. It will use your regular internet connect for regular internet traffic and the I2P proxy for eepsites. There is more information in the next section about accessing websites within I2P.
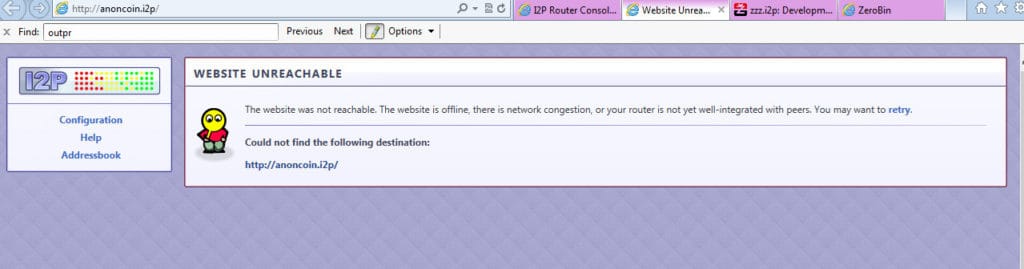
Keep in mind that I2P is a small and bumpy network. Eepsites are usually hosted on individual users’ computers and as such can have varying degrees of uptime. It is not at all unusual to come across dead eepsites which come back at some later time. If you see a page like this, it does not mean you’ve done anything incorrect. I2P is working, you just can’t get to that site right now.
Using I2P to access websites
If you’re not using the FoxyProxy method, you’ll notice that once you’ve activated the proxy settings you will lose connection to the clear net. This is because I2P does not provide outproxies by default. In I2P parlance, an outproxy is an I2P node that connects to the clear web and allows internal I2P traffic out onto the regular internet. In Tor language, this is called an exit node. I2P is a much more reclusive network and is not normally used as a proxy to the clear net. The I2P FAQ has this to say about outproxies:
How do I access IRC, BitTorrent, or other services on the regular Internet?
Unless an outproxy has been set up for the service you want to connect to, this is not possible. There are only three types of outproxies running right now: HTTP, HTTPS, and email. Note that there is currently no publicly listed SOCKS outproxy. If this type of service is required, try Tor.
At this time, there are three outproxy plugins (eepsite) listed in the IP2 plugin repository. Two no longer exist and the remaining one points to an I2P developer forum containing instructions on how to hack together a testing setup from 2016. I wasn’t able to get that working so it does not appear there is any publically available way to use I2P as an anonymous internet proxy at this time.
While browsing I2P dark web eepsites, you may sometimes be unable to load a site and instead be presented with a page like this.
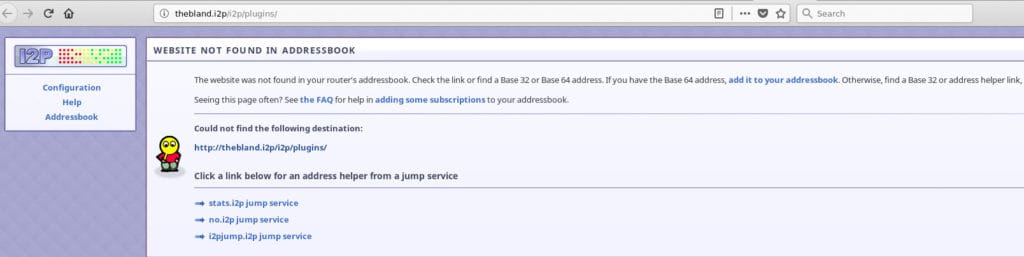
This means that your I2P router doesn’t know where that site is, but that does not necessarily mean the site does not exist; other routers may know where it is. To find out, click one or all of the jump links presented. Those links will consult well-informed I2P routers to see if the site can be found. In many cases, it works.
Using I2P to send and receive email
At this time there are two common ways to send and receive email between I2P and regular internet email addresses. SusiMail comes bundled with your I2P router and there is also a plugin named I2P Bote. Both can be used to send email within I2P, but at this time only SusiMail can be used to send email to and from regular internet addresses.
To get started with SusiMail, click the Email icon on your I2P router page.

SusiMail will prompt you to create an account on the I2P Postman site before you can use it. From there, you will recognize a fairly standard webmail interface and should be able to send and receive email to both I2P addresses and regular internet email addresses.
Note: It can take literally hours for I2P emails to arrive at regular internet addresses. This is actually a benefit as it makes timing correlation observations more difficult. If a known I2P user sends and email and then is observed leaving her house, and a few moments later an email arrives from an I2P email address, that can compromise her anonymity. Having emails arrive much later eliminates this correlation possibility.
When I set up my I2P email account, it took the form of user@mail.i2p. Emails sent within the I2P network will retain that email address. However, since the .i2p top-level domain is not resolvable on the public internet, it is modified for emails sent outside the I2P network to use a .i2pmail.org top-level domain. Because .org is resolvable, internet emails are sent back to that getway before being forwarded through I2P to my particular SusiMail instance.
Unlike SusiMail, I2P Bote views account creation as option, and does not require an account to send anonymous email. If you wish to be able to receive email, then you will need to go through the account creation process.
The I2P Bote project is working on implementing Internet <-> I2P email gateway but it is not functional at this time.
I2P Bote setup requires a little more work. The installation steps can be found on the I2PBote installation page(eepsite).
- Go to the plugin install form in your router console: http://127.0.0.1:7657/configclients#plugin
- Paste in the URL http://bote.i2p/i2pbote.su3
- Click Install Plugin.
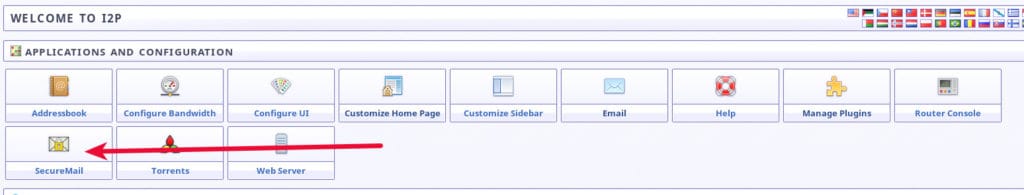
- Once installed, click SecureMail in the routerconsole sidebar or homepage, or go to http://127.0.0.1:7657/i2pbote/
It can take a long time for the installation process to complete and there is no progress bar to let you know what is happening. After about five minutes, I refreshed my I2P router home page and was rewarded with a new Bote SecureMail icon.
In true dark web fashion, there is no need to create any type of account or identity to send email with Bote. You can click the + icon at the bottom right of the screen, type up an email, and send it off with complete anonymity. However, you will not be able to receive email since you’re completely anonymous. If you want to be able to receive email, you will need to create an identity.

How to set up your own eepsite (I2P site)
Your I2P router comes with an eeepsite ready to go, you just need to add content.
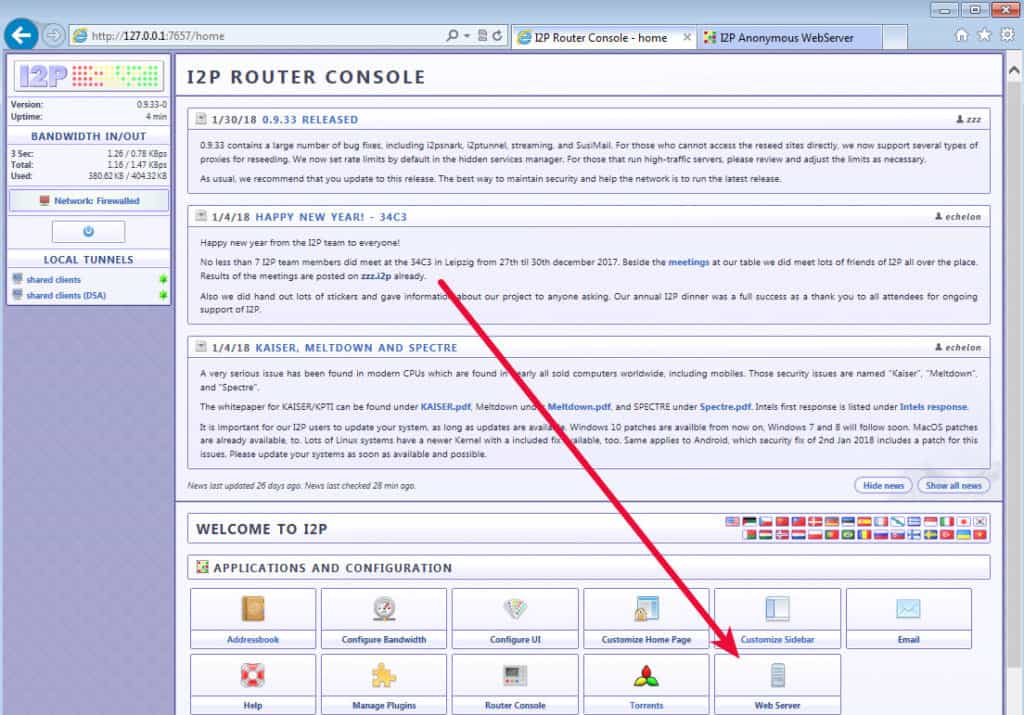
To view the instructions on how to get it set up properly, click the Web Server button or paste this into your I2P router address bar: http://127.0.0.1:7658/help/
Adding functionality to your I2P console
I2P comes with the basic toolset most dark web users are looking for bundled right in. The main I2P router page has tools for IRC, file transfer, email, and web servers, as well as many others. That functionality can be extended with I2P’s plugin framework, although there are very few plugins available.
To manage your plugins, navigate to the configplugins page http://127.0.0.1:7657/configplugins and you will see options to install plugins in two ways. If you have a plugin in an xpi2p and su3 file, you can upload it to your router. Another way is to provide the URL to one of those types of files.
The I2P plugin repository is on the I2P eepsite (eepsite). It seems very likely that an attacker or observer would have a lot to gain from tricking an I2P user into installing a surveillance plugin, so be sure to get your plugins from this official repository and not from untrusted third-party sources.
Finding content on I2P
Unlike the clear web, dark webs aren’t exactly into promoting their sites. There’s no Google for the dark web and even if there was, many dark web sites are up and down due to their unorthodox hosting set ups. Having said that, there are a few places where you can find I2P services if you have no particular destination in mind
The I2P Planet – The latest around the world of I2P
The I2P Planet (eepsite) is an aggregate site of activity around the I2P network. It mostly contains torrent links, but also has some news interspersed regarding the project’s support tickets and application news.
The I2P FAQ
There are a lot of misconceptions about I2P; what it is and why it isn’t Tor. Many of those questions are addressed on the I2P FAQ page (eepsite).
The I2P Bug Tracker
Think you’ve found a bug? Wondering if anyone knows about it, or if there is a patch available for it? The I2P bug tracker is the place to find that information. Community projects like I2P need fresh eyes and different systems to uncover bugs that may exist in the software. Do your part and report new bugs you find on the I2P Bug Tracker (eepsite).
Final words on using I2P and anonymity
I2P is not a replacement for Tor. While Tor certainly has its security problems, it is also much more mature and its advanced functionality makes it infinitely more useful for most people. If your intent is to gain anonymity on the internet by using a proxy, then Tor is the better choice. I2P only grudgingly incorporates the ability to connect to the clear net at all, and its ability to do so is unreliable. However, if you’re looking to run a full-on dark web site that remains as hidden as possible, I2P may be the better choice. If your intended user base is already using I2P, or is technically savvy enough to set it up, I2P’s garlic routing provides a better defence against the tactics that can be used on Tor to break anonymity.







