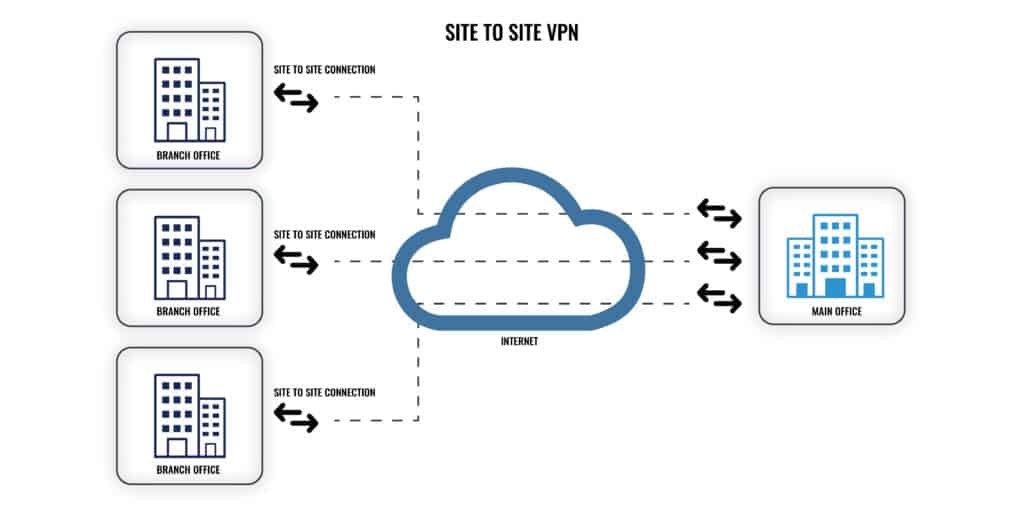
A VPN, or Virtual Private Network, allows you to securely access remote resources over the internet from a remote location. A common example is an employee working from home who uses a VPN to securely access company-only apps and documents from their employer’s office. A site-to-site VPN works similarly, except instead of connecting an end-user device to a company network, it connects two entire networks.
If you’re just looking for a quick recommendation, here’s a summary of our favorite site-to-site VPN services:
- Perimeter 81 Our top choice. Business-centric VPN that allows for network segmentation and traffic monitoring.
- Twingate A ZTNA that’s easy to deploy and supports single sign on.
- NordLayer Easily scalable solution that can manage all VPN users from a single dashboard.
Site-to-site VPNs can be used to securely connect the local networks of two or more offices in different locations. This allows employees in both locations to securely share resources and collaborate without exposing communication and files when they’re sent over the internet.
A site-to-site VPN can also connect a group of offices in different places to a central data center.
Unlike remote access VPNs installed on end user devices, which should be disconnected when not in use, site-to-site VPN connections usually remain in place indefinitely.
Best site-to-site VPNs
If you’re looking for a tested, ready-to-deploy site-to-site VPN service, we’ve listed some of the best services based on the following criteria:
- Ready to deploy with minimal configuration
- Can deploy on-premises and cloud-based servers
- Strong security and access control
- Scalable
- Dashboard management
- Supports single sign on (SSO)
1. Perimeter 81
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.perimeter81.com
Money-back guarantee: 30 DAYS
Perimeter 81 specializes in VPNs for businesses. You can easily deploy private VPN servers and manage network activity from an online dashboard. It doesn’t require much technical expertise and allows businesses to set up either site-to-site or cloud VPN servers. Further, you can easily scale your network up as your business grows. Public servers are also available in 36 locations around the world.
Key Features:
- Site-to-site and site-to-cloud
- User account administration
- Access rights management
- Application protection
- Single sign-on environment
Security features include network segmentation, traffic monitoring, and 256-bit AES encryption.
Apps are available for Windows, MacOS, Linux, iOS, Android, and Chrome.
Pros:
- Can deploy cloud and site-to-site VPN servers
- Useful security features and access control
- Novice friendly
- Includes public servers
- Caters specifically to businesses
Cons:
- Expensive
TOP CHOICE - EASY TO DEPLOY:Perimeter 81 allows you to easily deploy site-to-site VPN servers and customize them to your needs. Comes with a 30-day risk-free guarantee.
2. Twingate
Apps Available:
- Mac
- IOS
- Android
- Linux
Website: www.twingate.com
Twingate is technically a ZTNA, or zero-trust network access solution, and not a VPN. We’ll discuss more about ZTNAs below, but for now, suffice to say that they are arguably more secure and easier to deploy. Twingate can be deployed without changing your network’s infrastructure and it can be scaled up without any restrictions.
Key Features:
- Protects links to sites and cloud platforms
- Private virtual network
- Application access control
Twingate supports single sign on (SSO). The zero-trust model allows IT admins to restrict access to apps and resources on the network with a level of granularity not usually possible with VPNs. You can also split tunnel traffic so that it only sucks up local network resources if necessary. More bandwidth-intensive activities can use a direct connection.
Twingate doesn’t use apps like a normal VPN. Instead, authorization happens on a per-app basis any time you access the network.
Pros:
- Zero-trust network access
- Easily deployed
- Supports split tunneling
- Uses single-sign on
Cons:
- Not a VPN
ZERO TRUST:Twingate is a ZTNA that allows businesses to manage remote access to apps and other resources. It comes with a 30-day money-back guarantee.
3. NordLayer
Apps Available:
- PC
- Mac
- IOS
- Android
- Linux
Website: www.nordlayer.com
Money-back guarantee: 14 DAYS
NordLayer caters to small and medium-sized businesses. With it, you can build dedicated gateways that enable secure access to your company’s local network. Users can be managed from a centralized dashboard. Scaling up and adding more users is easy.
Key Features:
- VPN app is an application menu
- Equal treatment for on-site and remote users
- Site and cloud protection
- Cloud-based firewall option
NordLayer supports third-party authentication via GSuite, OneLogin, Azure, and Okta. The apps come with a built-in kill switch and strong encryption. NordVPNLayer guarantees assistance in less than three hours for customers who request support.
Apps are available for Windows, MacOS, iOS, Android, and Linux.
Pros:
- Deploy cloud and site-to-site VPN servers
- Easily manage users from a single dashboard
- Strong encryption and leak protection
- Fast and reliable connections
Cons:
- Collects unique advertising IDs on mobile
EASY TO MANAGE:NordLayer our first choice and simple product for SMBs. It comes with a 30-day money-back guarantee.
How does a site-to-site VPN work?
Each “site” must have a VPN gateway connected to the internet, such as a router, firewall, or security appliance. Data sent from one site is first encrypted by the gateway before being sent over the public internet. When that data arrives at the other site, the receiving gateway decrypts the data and forwards it to the intended recipients.
If anyone intercepts data being transmitted between the two sites, it will be encrypted and thus unusable. That’s why we sometimes refer to VPNs as “encrypted tunnels”.
What are site-to-site VPNs used for?
Site-to-site VPNs are used to securely connect the local networks of two or more geographically dispersed offices, allowing employees to safely collaborate and share files. Here are a few examples:
- VoIP. Set up secure voice and video conference calls between offices
- Collaboration. Staff in different locations can securely work together on documents, spreadsheets, and code. Collaboration tools like Office 365 can be hosted on the network
- Email. If you don’t want staff to access email from outside your company network, you can restrict access to VPN users
- File storage and sharing. Securely store, access, and send files over the VPN so they are never exposed on the public web
- Remote desktop. TeamViewer and RDP connections can be better secured through the VPN
Advantages: Why use a site-to-site VPN?
Here are a few key advantages to using a site-to-site VPN:
- Security. Site-to-site VPNs use end-to-end encryption that prevents any plain text data from being intercepted. Any data that is intercepted cannot be read or used
- No individual client apps. Everyone who connects to either network can use the VPN without any configuration or third party apps necessary on individual devices
- Scalability. Because individual devices don’t need to be configured, adding new ones is as simple as connecting them to the network. New locations can be added fairly easily
- Can be deployed internally or by a third-party service provider
- Complete control over WAN routing
Disadvantages: Why NOT use a site-to-site VPN?
Here are a few key disadvantages of site-to-site VPNs:
- Difficult to set up, maintain, and scale. Public key infrastructure (PKI) must be carefully managed. Although adding more locations isn’t all that difficult, adding mesh connectivity (all locations connect to each other, not just to a central network) is more complex
- Requires hosting an on-premises server and well-managed local network
- Doesn’t allow for remote access from outside the office
- Centralized setup can cause hub servers to slow down under heavy load
- After connecting to the VPN, there are few security features like access control, quality of service (QoS), and content regulation
- Each site-to-site VPN operates independently, which makes monitoring and managing them more difficult
How much does a site-to-site VPN cost?
The price of operating a site-to-site VPN can vary quite a bit depending on a few factors:
- How many sites need to be connected
- Minimum bandwidth requirements
- Resource sharing and app hosting requirements
- Which solution you choose. If you have the technical know-how, you could use SoftEther or OpenVPN to set up a site-to-site VPN for free. But most of us don’t have that expertise, so you might opt for a more expensive but easier to deploy solution.
Site-to-site VPN alternatives
Site-to-site VPNs have fallen out of vogue in the past few years, largely thanks to widespread adoption of the cloud for hosting files and applications. Most businesses no longer host their own on-premises servers, which has made site-to-site VPNs less useful.
If you decide that a site-to-site VPN isn’t right for you, here are some alternative technologies:
MPLS
Site-to-site VPNs and MPLS VPNs are often used interchangeably, but there is a slight difference. Site-to-site VPNs usually send encrypted data across the public internet. That means it’s vulnerable to all the downsides of the internet, like congestion and snoopers.
MPLS stands for multi-protocol label switching. Instead of public IP addresses, MPLS routes data using labels. MPLS is better suited to organizations with three or more endpoints. It makes traffic prioritization possible, is less vulnerable to insecure IP lookups, and generally suffers less latency than a site-to-site VPN.
On the downside, MPLS is more expensive and does require some specific equipment to set up.
ZTNA
VPNs assume that anyone who is authorized to access the network can be trusted. There are very few restrictions once the user has connected. ZTNA, or zero-trust network access, takes the opposite approach. No device or user is trusted until they’re properly authenticated.
ZTNA solutions work on the application layer and, unlike VPNs, are independent of the network. Instead, users are connected directly to applications based on user verification and device posture. Applications are hidden from the internet, which reduces attack surface.
Cloud VPN, SD-WAN, and SASE
SD-WAN stands for software-defined wide area networking. It’s a cloud-based approach to connecting offices in multiple locations that allows administrators to separate traffic based on security level, authorization, and quality of service (QoS) settings.
Compared to a VPN, SD-WAN offers lower latency and has some security failovers that VPNs do not.
Most experts agree that SD-WAN requires less maintenance and expertise than a VPN, and is easier to scale up. These characteristics also mean that SD-WAN is better for work-from-home employees. Connections can be made over LTE, 4G, and MPLS, among others.
By default, SD-WAN doesn’t come with any security or access control, which means enterprises in the past needed to set up their own, unwieldy network of gateways and firewalls. Enter SASE.
SASE, or Secure Access Service Edge, is a model for implementing SD-WAN that gives enterprises a single, centralized view of the entire network, allowing for easy management. If you decide to go with an SD-WAN network, be sure to secure it with a SASE solution.
Leased circuit (dedicated connection)
A private circuit, or leased line, is a private, permanent, and dedicated connection between two or more locations. This solution is expensive and is usually only necessary for very large enterprises. Enterprises must pay recurring lease fees based on the number of locations and necessary bandwidth. They cannot carry any third-party communications, which means leased circuits are free from the congestion and latency of the internet.
Site-to-site VPN FAQs
What is difference between VPN and site-to-site VPN?
The VPN that most consumers know about connects a device, such as a computer or a phone to a cloud server and protects that link, keeping the true destination of the connection secret. A site-to-site VPN is set up between gateway routers on two sites and creates an enduring, protected tunnel through which all business traffic can pass in secret.
What is site-to-site VPN vs IPSec?
When people talk about a site-to-site VPN, they are referring to architecture. IPSec is a VPN protocol and its name stands for Internet Protocol Security. A VPN protocol is a set of instructions that explain how the VPN can be constructed. IPSec operates at the network level, so it isn’t able to maintain a session or manage the exchange of session establishment conditions. This shortfall is resolved by partnering IPSec with a higher-level protocol, which is usually Layer 2 Tunneling Protocol (L2TP) or Internet Key Exchange (IKEv2).
Is OpenVPN a site to site VPN?
OpenVPN can be used for a site-to-site VPN connection. In this format, one site has to be defined as the server and the other as the client. This is because OpenVPN isn’t a peer-to-peer system, it requires one site to request a connection and the other side to host it. The connections are forged between the internet gateways of the two sites.