Bluetooth is cheap and ubiquitous. Speakers and headsets, smart watches, game controllers, and IoT devices all rely on it to communicate. But a new wave of Bluetooth tools have hackers picking the protocols apart, and our own testing shows that the devices are insecure.
We looked at seven models of wireless speakers from different manufacturers and found them all vulnerable to the recently-disclosed Key Negotiation of Bluetooth (KNOB) attack. Hackers can gain complete control over a Bluetooth device without alerting the victim, or carry out more insidious attacks like monitoring a conversation over a Bluetooth headset.
Bluetooth security test results show a critical risk
We were able to test 7 models of Bluetooth speaker, and we found all 7 vulnerable to attack. The models we tested include 5 Harman Kardon and JBL speakers currently on store shelves, along with 2 older models. We tried to choose speakers from diverse price points.
For KNOB testing, we used a rooted Huawei Nexus 5 running Android Nougat, and to hijack the speaker we used a Raspberry Pi 3B+. Both devices were using a version of the KNOB proof-of-concept that patched ROM to force extremely low encryption. The only device we actively compromised was a Harman Kardan Onyx Studio 2, but all devices negotiated 1-byte entropy and are vulnerable.
| Manufacturer | Device | Bluetooth version | Affected |
|---|---|---|---|
| Harman Kardon | Onyx Studio 2 | 3.0 | Yes |
| Harman Kardon | Onyx Studio 3 | 4.1 | Yes |
| Harman Kardon | Onyx Studio 5 | 4.2 | Yes |
| Harman Kardon | Onyx Studio 6 | 4.2 | Yes |
| JBL | Flip 5 | 4.2 | Yes |
| JBL | Xtreme 2 | 4.2 | Yes |
| JBL | Charge 4 | 4.2 | Yes |
It’s no surprise that every speaker we tested was affected, since the KNOB exploit attacks the Bluetooth standard itself. Every device using chipsets manufactured prior to 2018 are reportedly vulnerable. We expect devices running Bluetooth 5.1 and above should not be vulnerable if they are compliant with the updated standard.
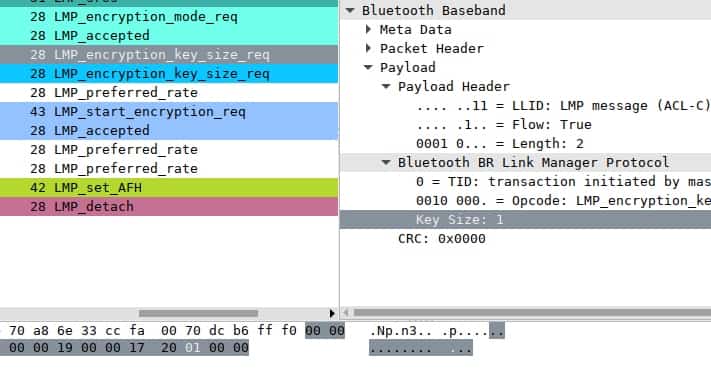
Still, it was jarring to see every test come back positive. We saw connection after connection accept 1-byte of entropy, using the published proof-of-concept and monitoring traffic in Wireshark.
Even the newest device, Harman Kardon’s Onyx Studio 6, is vulnerable, despite being manufactured after KNOB was reported. We believe manufacturers have chipset inventory that is still being used despite the security risk.
What’s the Bluetooth KNOB attack?
Bluetooth is a very polite standard. When two devices pair, they begin to negotiate. One of the things they agree upon is encryption. Bluetooth devices are able to request different levels of security for the link. In practice, this increases device compatibility and lifetime by ensuring that old devices can still communicate with new phones, and vice versa.
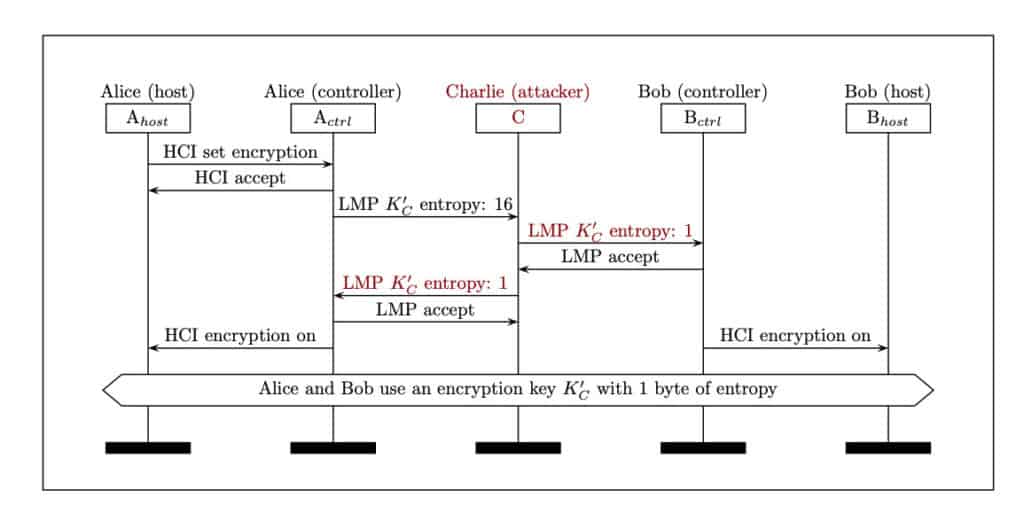
But the attack takes advantage of a flaw that allows an attacker to force two devices to use weak encryption. A successful KNOB attack reduces the entropy of the link key to 1-byte. The level of entropy dictates how much the encryption key changes over time, and it’s core to Bluetooth security. Since the key changes so slowly, malicious users are easily able to crack it.
The team behind KNOB, Daniele Antonioli, Nils Ole Tippenhauer, and Kasper Rasmussen, presented the exploit at USENIX over the summer. The implications of the vulnerability are stunning; billions of Bluetooth devices are likely vulnerable to key negotiation attacks.
In their whitepaper, the team says (emphasis mine), “The KNOB attack is a serious threat to the security and privacy of all Bluetooth users. We were surprised to discover such fundamental issues in a widely used and 20 years old standard.”
Escalating the attack
With KNOB opening the door, we decided to escalate the attack a step further. In a controlled environment, we were able to leverage our access to the decrypted link and hijack the Bluetooth session.
Setting up the Man in the Middle
We were able to escalate the attack by setting up a relay for MitM after using KNOB to crack the link encryption. Using publicly available tools, we cloned the target device and set up a MitM relay.
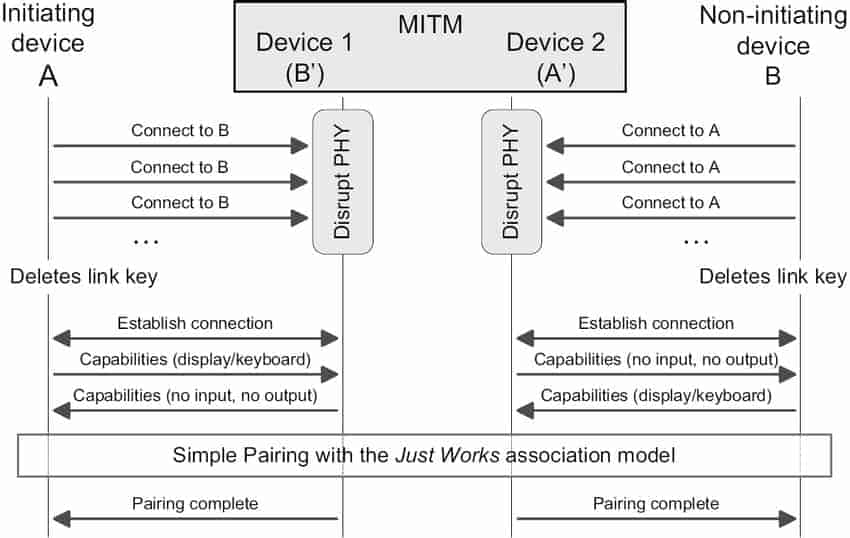
With the relay complete and Bluetooth packets visible, we were able to play the part of an attacker by intercepting and altering data heading to the speaker.
It should be noted that the device we attacked was the oldest we had access to, a Harman Kardon Onyx Studio 2 running Bluetooth 3.0 and A2DP 1.3. It’s possible that newer versions of the device implement packet other countermeasures to make an attack like this more difficult.
Hijacking the session
In order to complete the hijack, we wrote a Python script to alter the session running through our Man in the Middle (MitM) relay, then retransmit altered packets. In this case we replaced the audio stream being sent to the speaker.
In effect, we were able to take control of a speaker and change the song being played. The victim is not disconnected from the Bluetooth session. The link is still active, but it’s sending information to a relay device we control instead of the speaker.
As long as the attacker takes care to keep the relay datastream valid, there is no indication the session is under attack from the victim’s perspective, aside from the change in music.
What’s going on with Bluetooth security?
It’s no coincidence that a huge new Bluetooth vulnerability is emerging now. New tools have recently been released that give hackers a clear view of Bluetooth traffic as it travels over the air.
Some of these utilities are still rough around the edges, but they’re improving quickly. And, more importantly, they’ve eliminated the need for extremely expensive hardware that was, previously, the only option for Bluetooth hackers.
These utilities are opening up Bluetooth security research for the masses. Rather than an expensive all-in-one solution like the Ellisys Bluetooth Explorer, researchers are using cheap and readily available devices running in debug mode.
We believe this could be the beginning of a major sea change in the Bluetooth security segment, and users should be aware that more exploits are being developed using these toolchains.
A modern Bluetooth hacker’s toolkit
As part of our research into Bluetooth security, we’ve set up a modern testing lab. We’ve been using the following software packages, along with a Raspberry Pi 3B+ and a rooted Nexus 5 smartphone, to carry out research.
internalblue is testbed that gives researchers low-level access to Bluetooth devices. According to the researchers involved, it was key to developing the KNOB attack. Internalblue can log traffic, dump memory, send packets, push assembly instructions, set breakpoints, and more.
gatttool is a utility for exploring Bluetooth Low Energy (BLE) devices, a newer offshoot of the Bluetooth core standard with certain power-saving features. Researchers are interested in the BLE standard because it allows unpaired users to poll devices for information.
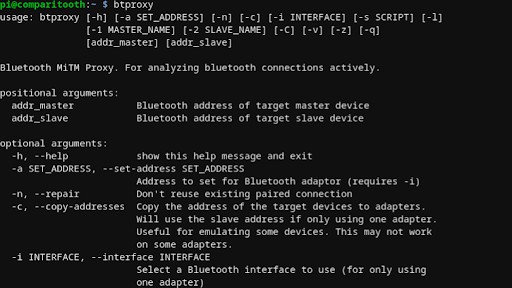
btproxy helps researchers create a MitM relay for analyzing traffic between two devices. Attackers use this software to eavesdrop on Bluetooth devices and inject their own data into the connection.
These utilities, along with a handful of specialized tools, are a huge asset to researchers, and they’re exposing critical flaws in Bluetooth security.
Channel hopping is Bluetooth’s saving grace
If there is one factor keeping these exploits from becoming an everyday nuisance, it’s Bluetooth’s resilience. In order to execute KNOB, the attacker has to be present for the moment of pairing. Otherwise, an attacker has to attempt to force the devices to re-pair while they’re present.
These re-pairing attacks are difficult to carry out. In some cases, they involve exploiting a hardware vulnerability, but the only guaranteed way to force devices to connect and pair again is to interrupt their connection by blasting the spectrum with noise.
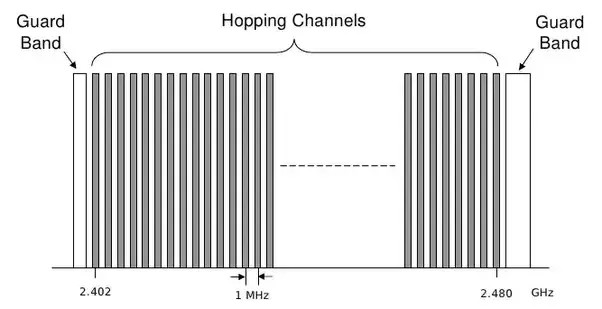
Fortunately, Bluetooth has robust systems in place to prevent re-pairing attacks. Bluetooth spectrum is split into 79 separate 1MHz bands. Devices hop across these bands 1,600 times per second, at random. In order to generate enough noise to guarantee an interruption, the attacker has to expose themselves by using a high-power multi-channel frequency jammer.
These devices are illegal. They’re routinely found by law enforcement using triangulation and other methods, and using them is a major risk. For our testing, we did not carry out any re-pairing attacks. Instead, we stipulated that a sufficiently motivated attacker could carry out such an attack.
The worrying implications of KNOB
Our attack against these speakers highlights one harmless way hackers can exploit their control of Bluetooth, but make no mistake: The door has been left wide open. In their paper, the authors of the KNOB attack shared their concerns that the vulnerability could be leveraged in very serious ways.
For instance, it may be possible to attack a Bluetooth internet adapter and sniff traffic. Or attack a Bluetooth headset being used to issue commands to a virtual assistant, then either inject malicious commands or monitor the responses.

We are also concerned about the growing use of Bluetooth as an authentication mechanism. For instance, some electric scooters rented out by rideshare apps use Bluetooth to pair a user account with the scooter. Attacks against those authentication mechanisms may enable theft or fraud.
The implications of this vulnerability are extremely worrying. Everyone should assume their Bluetooth connection is insecure.
What can consumers do about Bluetooth security flaws?
It’s very important that individuals stop purchasing and using older Bluetooth hardware. It’s unlikely that manufacturers will ever be able to patch a significant number of affected devices. Bluetooth devices tend to be difficult to update, and in some cases it’s impossible to patch the firmware at all.
Where possible, try to connect to older Bluetooth devices using the manufacturer’s official app and run an update. If updates aren’t available, be aware of the risks and try to follow some common-sense guidelines:
- Don’t have sensitive conversations over a Bluetooth device
- Disable Bluetooth on your phone and computer when it isn’t in use
- Don’t rely on Bluetooth for site access control
- Look for devices using Bluetooth 5.1 and above
- Don’t use Bluetooth devices to communicate with virtual assistants
- Avoid using Bluetooth internet adapters
As flaws in Bluetooth security are exposed, consumers need to stay aware of the risks associated with these devices. KNOB is only the first of many emerging threats, and the fact it affects the standard itself is a bad sign for the state of Bluetooth security in general.