About 30 million new websites were registered between November 1 and November 20 this year. Comparitech’s cybersecurity research team scanned new sites created in the weeks prior to Black Friday for probable signs of phishing and scams.
First, we filtered by website domains by keyword to narrow our search. About 268,000 of the new site domains contained a word or phrase on our list of holiday shopping-related keywords. We scanned domains names for keywords like “black friday”, “cyber monday”, as well as several popular stores, brands, and websites:
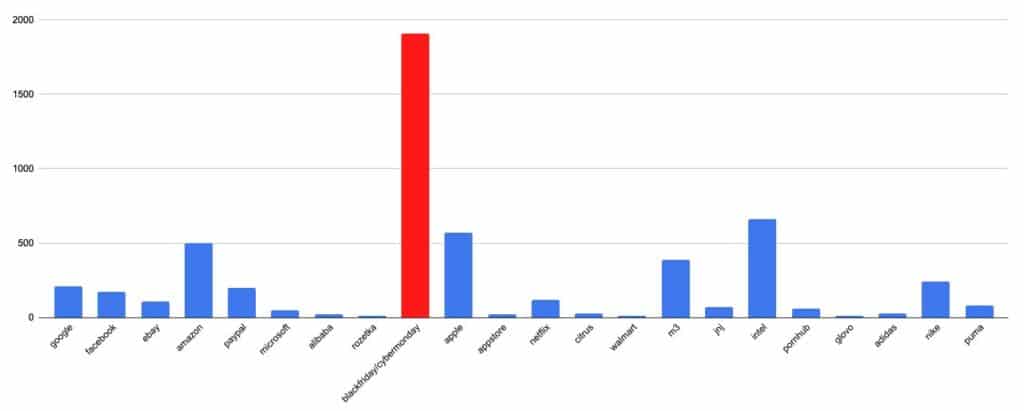
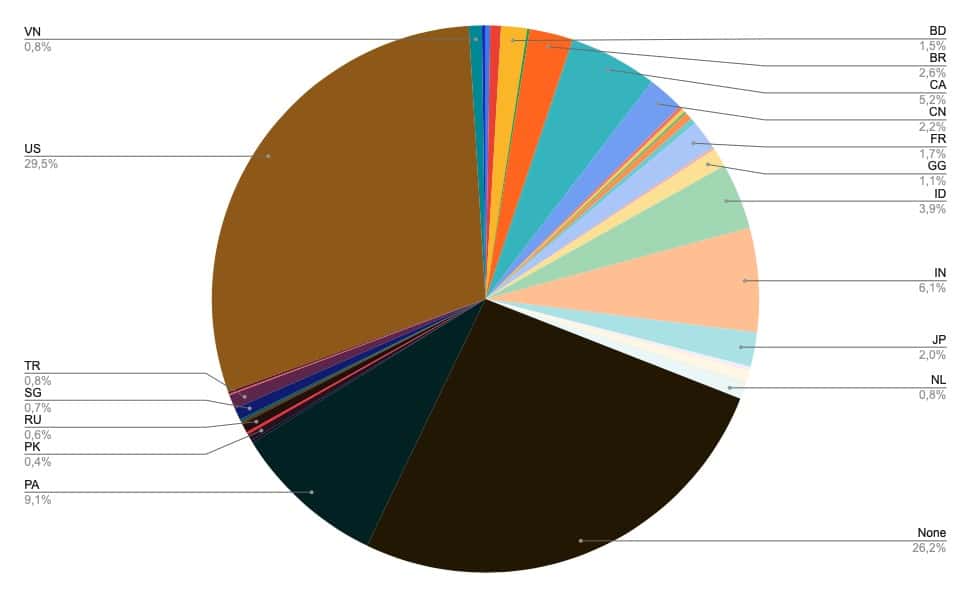
“Black Friday” and “Cyber Monday” were the most frequent keywords from our list found in newly-registered domains. The United States was the most common place to register a new site.
Of the 267,807 new domains containing a Black Friday-related keyword, 5,466 probably scam and phishing sites were identified. Remember these sites were all registered between November 1 and November 20.
Researchers analyzed newly created websites’ certificates, availability, registration date, and domain names for signs of phishing and scams. The sites were checked against phishing databases of known scam sites. The research team also searched for links to phishing and scam sites on social media.
Phishing sites often imitate well-known sites such as the login page for PayPal, but during the holiday shopping season, cybercriminals set up original scam websites with tempting deals and rewards. In this analysis, we focused on those original scam and phishing websites.
How do victims end up on Black Friday and Cyber Monday phishing sites?
Scammers lure victims to their sites using email and social media. We’ve all seen phishing emails where scammers pose as a business or authority figure to trick victims into clicking on malicious links. Social media posts and pages direct users to the scam page and promise rewards for liking, following, reposting, and registering a new account.
One such site, promoblackfriday.online, requires users earn 100 points to get a free iPhone, laptop, or smart TV. Users get 30 points by taking a quiz, then must acquire the remaining 70 points by sharing the scam on social media. Ten points per share.
Some of the sites are just used to collect email addresses where phishing messages are later sent. Such a site is probably less likely to get flagged by web browsers this way. Others actually steal login and payment information during the registration and checkout phases.
Copycat domains
Just like legitimate sites, scammers often buy several domains at once with similar spelling. They all lead to identical scam websites. Here’s an example of some phishing domains advertising NBA and NHL jerseys:
- www.blackfridaynbajerseyforsale.com
- www.blackfridaynbajerseyonline.com
- www.blackfridaynbajerseyonlineoutlet.com
- www.blackfridaynbajerseyonlinesale.com
- www.blackfridaynbajerseyonlineshop.com
- www.blackfridaynbajerseyonlinestore.com
- www.blackfridaynbajerseyonsale.com
- www.blackfridaynbajerseyoutletsale.com
- www.blackfridaynbajerseyshop.com
- www.blackfridayncaajersey.com
- www.blackfridayncaajerseyfans.com
- www.blackfridaynhljerseys.com
- www.blackfridaynhljerseysfans.com
- www.blackfridaynhljerseysforsale.com
- www.blackfridaynhljerseysonline.com
- www.blackfridaynhljerseysonlineoutlet.com
- www.blackfridaynhljerseysonlinesale.com
- www.blackfridaynhljerseysonlineshop.com
All of these sites were created at the same time and registered in the same country, Turkey, just before November 15, 2020. They have since been taken down.
Cybercriminals also frequently engage in typosquatting, in which they buy domains with similar spelling to a legitimate domain so as to trick victims into thinking they’re on the genuine site.
Common indicators of a phishing site
During our analysis of phishing sites, we spotted a few common patterns:
- There is little to no information listed about the company, including contact details
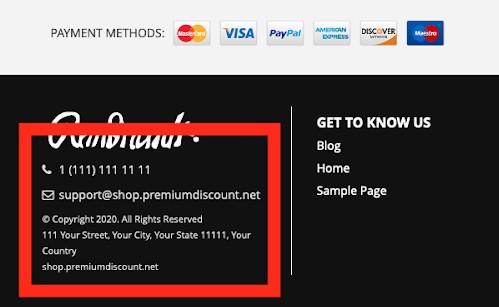
- Whois data, which includes information about the site’s registration, is missing or hidden
- WordPress was the most common CMS used to set up phishing sites. They often use basic, free templates.
- Social media links don’t go to the company’s profile

- HTTPS is not an indicator of a legitimate site
How we found holiday shopping phishing and scam sites
Researchers used a range of tools and techniques to analyze and identify probably phishing sites:
- Analyst Arsenal: an open-source intelligence (OSINT) tool suite
- Domain-check-2: get information about domains including registrar, status, and expiration date
- Opensquat: identify cyber squatting threats to specific companies or domains
- Phishing catcher: catch possible phishing domains in near real time by looking for suspicious TLS certificate issuances reported to the Certificate Transparency Log (CTL). Sites are scored and those who meet a certain threshold (75%) are likely to be scam or phishing sites.
- PhishTank: a collaborative clearing house for data and information about phishing on the internet.
- Phishing.Database: a testing repository for phishing domains, websites, and threat, updated hourly.
- ImmuniWeb: an application security company that offers free tests for website and SSL security, among others.
Ultimately, phishing catcher and ImmuniWeb proved to be the most performant in identifying new phishing sites.
How to shop safely this Black Friday and Cyber Monday
Although fraudsters are especially active this time of year, you can protect yourself from phishing and scams with a few simple guidelines:
- Never click on links or attachments in unsolicited emails and messages
- Shopping websites must have HTTPS, but note that many phishing sites have HTTPS as well
- Check the spelling of website URLs and email domains for typos
- Only buy from reputable vendors and marketplaces
- A lack of contact information or terms of use is a strong sign that a site is a scam
- Avoid clicking on shopping ads and posts on social media
- Run a Whois search for the website. If it was registered very recently, it’s more likely to be a scam.
- If a deal seems too good to be true, it probably is.