
Although the promise of flying cars has yet to materialize, futurists were at least mostly right when it comes to smart homes. Every electronic device in your home is either “smart” or can be made smart and operated remotely. Thankfully, that extends to home security. The smart home security market is practically bursting at the seams, making it easy for even a tech newcomer to set up a complete smart home security solution in just a few hours.
Still, as easy as it is to get started, there are numerous options to explore and some notable limitations anyone should know about before buying smart home security products.
Below, we’ll explore everything you need to know about smart home security. You’ll learn about:
- What you need to do before purchasing any smart home security products
- Common smart security products you may want to consider
- Trusted brands and product makers to consider
- Where to safely purchase smart home security products
- Smart home ecosystem and automation technologies
- Smart home security limitations
As this guide offers an extensive overview of smart home security, we recommend you use the table of contents on the right to quickly navigate between the topics you most need.
What is smart home security?
Certain devices under the wider umbrella of smart home technology protect the safety and security of your home and those inside of it. Popular smart home security devices include (but are not limited to):
- Security cameras (including video doorbells)
- Door locks
- Window and door sensors
- Indoor and outdoor lighting
- Hub devices
Smart home security can also include devices designed to protect your property from physical damage. Smart smoke detectors may help prevent extensive fire damage, while smart leak and freeze sensors provide early warnings about potential water damage to your home. There’s even an entire and emerging class of smart home products for elder care which can be used to monitor both physical and health concerns for senior citizens.
In this article, our primary focus is on the type of smart home security products that monitor your home for threats related to criminal activities, such as robberies, burglaries, vandalism, or home invasion.
What to consider before purchasing smart home security products
Before you purchase your weight in smart home security products, you’ll need to carefully consider all of the following factors:
- The size of your home
- The number of entrances in your home
- Your available internet speed/bandwidth
- The mobile device(s) you plan to use to manage your smart home security
- Whether you want a self-monitored or professionally-managed system
- Product installation requirements (particularly important for renters)
- Whether you can get insurance discounts for installing home security devices
- The type of products that exist for home security that you may want to use
- Whether your devices can be automated using IFTTT (pro-level!)
You may also want to take other factors into consideration, including what local and state laws exist on where you can place video and audio recording devices. Although rare, it’s possible to violate some state or local privacy laws if you install your security cameras in the wrong locations. (For example, video cameras in bedrooms or bathrooms that capture guests undressing could be a criminal offense.)
Step 1: Consider the size of your house or apartment
Before purchasing any smart home products, consider the size of your home or apartment. Your dwelling size is important to help determine how many products you’ll need if you want complete security coverage of your home.
For example, if you’re living in a one-level studio apartment, you probably don’t need multiple indoor security cameras. One multi-functional smart security camera may be able to monitor your apartment for potential threats.
Conversely, if you own a house, you’ll need more security equipment for full coverage. The average American home is now over 2,500 square feet. One security camera won’t effectively monitor both the interior and exterior of your home.
Step 2: Count the number of entrances (including windows) in your home
Every entrance to your home is a potential weak spot. One survey of 86 real burglars found most came in through either an unlocked front door or window.
Beyond the front door, other points of entry that can make it easy to get into your home include windows, back doors, side doors, garage doors, and even pet doors.
Make sure to account for the total number of entrances in your home that could be a security risk. That should include front, back and side doors, basement entrances, and first-floor windows. Second-floor windows are less of a concern unless they’re easily accessible due to the design of your home or surrounding features (such as trees).
Step 3: Assess your internet speed or available internet bandwidth
Some smart home security products are extremely data-hungry. Even one video camera monitoring constantly in HD-quality video will use around 1.5 to 2 Mbps of downstream internet bandwidth. Other smart home security products will use considerably less, but you’ll want to take all of this into account before setting up your smart home.
Importantly, you’re likely already using multiple devices in your home that also cause a drag on your available bandwidth. Streaming TV or music and online video gaming are the most common activities that require significant amounts of data.
Also, note that the speed your ISP advertises to you is not the amount you’ll receive. Internet speeds also tend to decline during peak usage hours of the day, and most ISPs will adjust available bandwidth from heavy users to ensure all users have adequate speeds.
One thing many new smart home users fail to account for is available upload speed. Although the median download speed in the US is 60 Mbps, the average upload speed is only 5 Mbps. Most consumers don’t use much of their upload bandwidth, but if you’re setting up a smart home, you may end up using more upload bandwidth than you’re used to, especially if you’re running security cameras. Make sure you have an internet plan that can handle both the upload and download demands of your combined household data usage.
Step 4: Make sure you have mobile devices that work with most smart security products
Before you purchase any smart home security products, double-check that the supporting apps work not only with your version of iOS or Android but that the apps work with your specific device, as well.
Limited device functionality is rarely a problem for Apple product users, but it will occasionally be a problem for Android device users. Even if your Android device has a version of Android the smart home product supports, there may still be limitations based on the specific Android phone or tablet you’re using. If there are device-specific limitations, the company offering the device may know about it and may have some information on its website knowledgebase.
Unfortunately, you may not find out about some Android device limitations until after you’ve purchased the product and attempted to use it. Most unknown device limitations occur for individuals using significantly lower-end and lower-cost Android device models, particularly those devices that lack Bluetooth Low Energy technology.
Step 5: Decide whether you want self-monitored (DIY) or professionally-monitored smart home security
Before diving into smart home security products, you’ll need to decide whether you’d prefer to manage your smart home security yourself, or outsource that management to a third party. This consideration is important and may ultimately determine where you purchase your smart home products.
What is self-monitored (DIY) smart home security?
A self-monitored smart home security system is one that you put together and monitor yourself. Also known as a DIY smart home security system, this avenue allows you full choice over which smart home security products and brands you use. You’ll also personally take on the management of those devices, which includes reviewing monitored and recorded events and troubleshooting the products when something goes wrong.

Self-monitored smart home security systems sometimes operate through a hub device. Some also come as a kit that includes multiple products. You can create your own system using a mixture of devices that each have their own apps or a central app from which you can control and monitor all or most of them.
You can also purchase all-in-one security devices that have multiple security features, or a device kit that includes several security products operated through either a central app or a central device hub.
Importantly, all self-monitored smart home security devices will send you alerts (known as push notifications) when activity occurs. You’ll receive those alerts on any device you have set to receive them.
What is professionally-monitored smart home security?
If you’re not comfortable with taking full responsibility for your smart home security, you may want to choose a managed smart home security approach. Several well-known home security companies, such as ADT, Vivint, and SimpliSafe, now offer smart home security systems.
In most cases, these companies can even send a technician to your home to help set up the smart home security devices for you. Alternatively, if you want to save some money, you can opt for a self-installation kit, which most security companies now sell. Most self-install kits also let you pick and choose between which types of security devices you want, and often include a base station (hub) to help monitor the whole system.
As you might expect, professionally-monitored smart home security systems are more expensive than self-monitored systems or devices. But it may come in handy if you don’t have the time, skillset, or patience to monitor your own system.
Another downside to professionally-monitored systems is that they tend to limit which devices you can use. Most managed home security companies sell a limited line of products from a select few product makers. It’s uncommon for them to let you add your own devices to their monitoring services, so you’ll need to personally monitor any devices you purchase outside of what the security company sells and maintains.
Step 6: Review your device installation limitations
Every smart home security product you purchase will come with installation instructions. Some devices are easier to install than others, and most don’t require any alteration of your physical property. However, some do either require that you drill or make holes in your walls, or provide you the option to do so for certain placements.
Physical property alterations for installation are often a necessity or a preferred method for outdoor home security cameras, smart locks, and window or door break sensors.
Before you purchase any smart home security product, read the required installation instructions, or look up installation videos or product reviews.
If you’re a renter, check with your landlord or property owner
Do you rent or lease your home? Review your rental or lease agreement before trying to make any physical alterations to the property, or contact your landlord, property owner or rental company for more details about what you can and cannot do. Most rental contracts include notations about whether or not you can make physical alterations to the property, and of what kind you can make.
For example, if you live in an apartment that doesn’t allow you to put holes in the wall, you will likely need to limit yourself to devices that don’t require any form of drilling. You may be able to get around some installation limitations by using strong adhesive pads to mount devices to walls or horizontal surfaces.
If you own your home, think about the long-term impact
You’re far more likely to be OK with drilling and running wires through your walls for indoor and outdoor security cameras if you own your home. However, you’ll need to consider the long-term consequences of doing so, as well. If you plan to sell your home, for example, what impact will that have on the future value of your home? If you plan to do the work yourself, make sure you’re using the right tools for the job, or have a skilled family member or friend perform the work. Make sure you’re drilling in the proper locations so as to avoid any unwanted mishaps.
Most managed security companies can install home security devices for you, for a fee.
Step 7: Research insurance discounts for smart home products
You may be able to get home insurance discounts if you install home security products. In fact, some home insurance companies have partnered with device makers to offer products that are approved for use in your home.

While we do not recommend you make potential discounts your primary reason for getting home security products, you’ll still want to explore whether any discounts are available to you. Potential home insurance discounts are a fringe benefit of setting up a home security system.
In general, you may be able to get discounts from your home insurance provider if you’ve installed have security cameras, window and door break sensors, flood or leak sensors, or smart fire and smoke detectors. Insurance companies see these as a highly positive form of risk mitigation. Home insurance companies view almost every risk mitigation effort favorably.
Major home insurance companies that offer discounts for smart home security installations include:
- American Family Insurance
- Amica Mutual
- Allstate
- Farmers Insurance
- Geico
- Liberty Mutual
- Nationwide
- Progressive
- The Hartford
You can learn more through ValuePenguin’s detailed breakdown of smart home insurance discounts, and what potential savings you might see for different types of smart home security products.
Step 8: Pick the type of smart home security products you want or need
Although the number of devices available may seem overwhelming, there are only a few broad categories you’ll need to consider as you get started. Before buying any products, decide whether you want or need:
- One or more smart security cameras (indoor and/or outdoor)
- One or more smart locks
- Window or door break sensors
- Smart outdoor lighting
- Motion sensors
- A video doorbell
- A smart home hub device
- A controller/keypad
This is the biggest step in the process, so you’ll want to take some time to understand each of the most common smart home security product categories and what you should consider before you make a purchase.
As mentioned under the DIY vs. professionally-monitored section, some products come as an inclusive, multi-product kit, while others are sold individually. If you want to ensure your products work well together and save yourself a bit of money, purchase a smart home security kit. Some options, like the Ring Alarm 5-Piece Kit, are a good starting point for newcomers.

Below, you’ll find more detailed information about popular smart home security products.
Smart home security cameras
Smart security cameras are a common go-to for smart home security. These products also come with a multitude of functions, depending on the device, which makes them good standalone options for home security or a good choice to cover multiple security needs housed in one device.

There are two broad types of smart home security cameras: indoor and outdoor. There are multiple camera designs to choose from, to include bullet and dome cameras, and unclassed cameras that don’t fit into a defined category (such as the Wyze Cam pictured just above). You can also choose between wireless IP cameras or wired cameras. Additionally, some cameras may come with solar panels, while others are battery-powered and/or hardwired.
Outdoor security cameras
An outdoor smart security camera is any camera that can work outside of your home. Such cameras can be installed onto the exterior of your home, either through adhesive pads, screws, a magnetic base, or a combination of these. These cameras can also be hardwired, battery-operated, or powered through a solar panel. Most outdoor smart security cameras now use a wireless IP connection, but some offer both wired and wireless connectivity options.
Common outdoor cameras include more traditional bullet or dome cameras, as well as video doorbells such as those sold by Ring and Remo.

There are now dozens of outdoor smart home security cameras on the market. Some have unique features, but most incorporate variations of different features you’ll find desirable and necessary for smart security cameras.
Key features to consider when purchasing outdoor security cameras include:
- Push notifications
- Motion detection
- Sensor range
- Facial recognition
- Person alerts
- Geofencing (also known as Activity Zones)
- Two-way audio communication
- Night vision
- Wide-angle lens
- Continuous video recording
- Arm/disarm
- Live video streaming option
- Account sharing
- Local and cloud storage
- HD-quality video
- Digital pan and zoom functions
- Functional in low- and high-temperature ranges
- Weatherproofed and water-resistant
This list is long, but also not exhaustive. Companies in the smart home security market continue to push the limits and invent or innovate new functions, including new ways to incorporate artificial intelligence and machine learning.
Key advantages to outdoor cameras include:
- An effective deterrent against burglars and home invaders
- Uniquely designed to survive a range of weather conditions
Outdoor security cameras can be more expensive than indoor cameras, depending on the make and model. You’ll also find that outdoor cameras with motion sensors are far more likely to send notifications from false positives as they may pick up more background noise and activity. Thankfully, many smart security cameras allow you to adjust the sensitivity level of the motion sensor.
How much do smart outdoor security cameras cost?
How much you pay for a smart outdoor security camera will depend on the brand and the features. The better-known the brand and the more packed it is with features, the more expensive it will be.
Prices can range from under $25 (or even less) for low-end devices like the URJD WIFI IP Camera to over $200 or more for top-end options from well-known brands like Google’s Nest Cam Outdoor.
Indoor security cameras
You’ll find indoor and outdoor security cameras operate similarly. On a technical level, the key difference between most indoor and outdoor cameras is in the waterproofing (or lack thereof for indoor cameras).

Key features to consider when purchasing an indoor security camera include:
- Push notifications
- HD-quality video
- Facial recognition and person alerts
- Works with Google Assistant or Amazon Alexa
- Night vision
- Geofencing (less important for indoors, but still an option)
- Continuous recording
- Live video streaming
- Arm/disarm
- Local and cloud storage
- Two-way audio
- Wide-angle lens
- Digital pan and zoom
Key advantages of indoor cameras include:
- Often less expensive than outdoor cameras
- Less likely to experience wireless signal interruption
- Will capture criminal activity before they can be tampered with
Indoor cameras are mostly limited in how much you’re willing to pay. Cheap cameras will come with fewer features or diminished reliability (or both) and may have more features and software limitations, as well.
How much do indoor smart security cameras cost?
Indoor security cameras don’t need to be weatherproofed, which can help to reduce the price by a small amount. Still, you’ll find the price range is similar to outdoor security cameras. Low-cost options such as the $25 Wyze Cam exist. A good number of popular and well-regarded devices sit in the $100-$200 range, as well. At around $150, the Arlo Q is a good example of the upper-bound for widely-tested devices that cost a bit more.
Indoor/outdoor smart security cameras
You may come across some security cameras labeled as “indoor/outdoor”. An indoor/outdoor security camera is one you can use either indoors or outdoors without making any changes to the device, making the class highly versatile.
Indoor/outdoor cameras mostly differ in that they offer various base setups that make them easy to install either indoors or outdoors. However, since they’re all designed to work outdoors, indoor/outdoor cameras are in effect outdoor cameras that can also be installed inside your house with an aesthetic that makes them look less out-of-place inside your home.

The Arlo Pro line of cameras are among the most well-known indoor/outdoor options, but there are others within different price ranges.
Key advantages of indoor/outdoor cameras include:
- More versatility
- Typically designed with both form and function in mind
How much do indoor/outdoor cameras cost?
You’ll find indoor/outdoor cameras tend to be more expensive than their solely indoor or outdoor counterparts. An indoor/outdoor camera is best if you plan to move your camera around between the inside and outside of your home. Otherwise, opt for a solely indoor or solely outdoor camera.
Bullet security cameras
Bullet cameras tend to be “bullet” shaped with a cylindrical housing. They’re what many consumers think about when security cameras come to mind. Sizes and even the overall shape of bullet cameras can vary.

Key advantages of bullet cameras include:
- Easily mounted
- Cheaper than dome cameras
The primary disadvantage of bullet cameras is their field-of-view (FOV). Most bullet cameras cannot swivel without manually changing the angle. The FOV is usually around 70-100 degrees.
How much do bullet security cameras cost?
Prices for bullet cameras can range from under $20 to well over $200, depending on the brand and the features.
Dome security cameras
Dome cameras get their name from the characteristic “dome” covering the top of the camera. These cameras differ from bullet cameras primarily in the exterior design.
Key advantages of dome cameras include:
- Weatherproof casing
- More conspicuous or aesthetically pleasing
- More tamper-proof
- Difficult to determine the position of the camera
Dome cameras have the same key limitation as bullet cameras, with a field-of-view around 70-100 degrees. However, the design of a dome camera makes it more difficult to determine where the camera is pointing.
How much do dome security cameras cost?
Dome security cameras are slightly more expensive than bullet cameras. The key design feature (the dome) adds a slight premium to the pricing in some cases. Dome cameras are available under $20, but you’ll be better off purchasing a camera in the $30 or above range.
Point-Tilt-Zoom (PTZ) security cameras
PTZ security cameras can point in any direction and zoom in and out of a location, giving them a wider FOV than most other types of cameras.
Key advantages of a PTZ camera include:
- Widest view angle among other cameras
- Can see further with higher optical zoom options
PTZ cameras work well outdoors, but can also be mounted indoors. You can mount these cameras the same way you would for bullet cameras.
How much do PTZ cameras cost?
These are among the most expensive design types. You can easily spend $50 to well over $200 for a good quality PTZ camera.
Wired vs. wireless IP cameras
Smart security cameras must all connect to the internet. They do so using either an Ethernet cable (wired) or a WiFi connection (wireless). Some cameras allow for both. There are notable limitations to cameras that only allow for one or the other, however.
Wired (Ethernet) cameras
Cameras that can only be wired tend to have a more complicated setup process. You’ll likely need to drill holes and run wires behind walls if you want to keep a clean look to them. For some users, such disadvantages may be outweighed by the permanence offered by an Ethernet connection, which can include better bandwidth and no signal interruptions.
WiFi (or wireless IP) cameras
WiFi cameras can be placed anywhere within reach of your home’s WiFi signal. Alongside a limited range based on the strength of your WiFi signal, you may have to deal with interrupted WiFi signals or the reduced bandwidth that can occur through many WiFi routers.
Wireless IP security cameras are usually a better option if you’re renting a house or apartment, and tend to work best for smaller homes.
How much do wired and wireless IP cameras cost?
There’s no real cost difference between wireless and wired IP cameras. Even cameras that offer both a wired and wireless option can range in price between $20 to several hundred dollars.
Hardwired vs. battery vs. solar-powered cameras
All smart security cameras require a power source. There are three options that exist for this: hardwired (usually via an A/C adapter), battery-powered, and solar-powered. Each has benefits and limitations.
Hardwired cameras
Some hardwired security cameras have the same limitations as IP cameras that require an Ethernet connection. You’ll find they can be placed in fewer locations, and they may require additional setup and some tampering with your walls to get them installed. Once they’re in place, it’s difficult to move them, as you’ll need to go through the time-consuming installation process again.
However, many hardwired cameras also provide WiFi connectivity. This makes some of them more versatile and makes it easier to place them in more unconventional locations, so long as they’re within reach of an outlet or an extension cord.
The SmartThings Indoor Security Camera is an example of a camera in this category.

Battery-powered cameras
Many smart home security cameras run off of battery power. Some cameras use replaceable batteries, while others utilize an internal battery that can be recharged. In either case, battery-powered cameras are the most flexible variety as you can place them anywhere. Many will also continue to record motion-activated events to an internal hard drive should the power go out, and can still communicate with your mobile phone via a Bluetooth connection, as well.
Most battery-powered cameras use internal, rechargeable batteries that can last anywhere from 6 to 12 months to a charge. They come with charging cables that allow you to recharge the device indoors. Some devices require changeable batteries. You’ll need to check manufacturer specifications for the type of batteries to be used in those cases. As someone who’s tested home security products for several years, I’ve seen everything from AA to D batteries required.
The Canary Flex is an example of a camera in this category.

Solar-powered cameras
Somewhat of a subclass of hardwired cameras, solar-powered cameras are outdoor security devices powered via an included solar panel. They have similar limitations to other purely hardwired cameras, but by design, they offer internal batteries that allow them to continue working in low-light conditions, such as at night or on cloudy days. The market for outdoor solar-powered cameras is still small, but it’s growing as solar panels become more effective and cheaper.
The Lynx Solar Outdoor Camera from Tend Insights is an example of a camera in this category.

How much do hardwired, wireless, and solar-powered cameras cost?
Hardwired and wireless come in the standard $20 to $200 or more price range. Solar-powered cameras, however, have a much higher starting point given the additional solar panel included with the device. Expect to pay closer to $100 or more for a trustworthy solar-powered camera.
Smart security locks
Smart security locks are internet-connected locks that feature one or more keyless entry methods. Most also have keypads that allow you to enter a code should the digital communication methods fail, while all of them still have a slot for a traditional key in case the battery dies.

These types of locks are particularly popular among homeowners operating vacation rental properties or bed and breakfast operations, such as through vRBO or Airbnb.
Key features to look for when purchasing smart locks include:
- Long battery life
- Tamper-proof design
- Multiple unlock options (keycode, physical key, Bluetooth auto-unlock)
- Guest access
- Compatibility with multiple door types, sizes, and configurations
- Smart home ecosystem compatibility
Several of these features are essential to check into before purchasing a smart lock. For example, if the lock doesn’t fit your door properly, you’ll be out of luck unless you go to the extreme of purchasing a new door that it does fit. Make sure to check your door’s measurements and the measurements of the lock before purchasing installing a smart door lock. Additionally, check the layout and measurements of the lock bores and faceplate slots on your door to ensure any lock you install will fit. Most doors will work, however.
Battery life is also extremely important, as all smart locks are battery-powered. You’ll need a back-up entry option for when the battery fails (e.g., a keyed entry). Most smart locks include back-up options, but you may want to review the features of the smart lock you’re purchasing to ensure such options are indeed available.
How much do smart locks cost?
Smart locks are not something you want to buy on the cheap end. You might be able to locate options under $100, but we wouldn’t recommend it. The best and most secure smart locks range between $150 to $250 or more. At $229, the popular August Smart Lock Pro (pictured above) falls into that category.
Very expensive models run in the $300 to $500 range and often include particularly advanced biometric features, such as fingerprint or face recognition unlocking.
Smart door and window sensors
Door and window sensors are simple tools that let you know if someone opens your door or windows without your permission or knowledge. You may see these listed under a few other names, including “contact sensors” or “entry sensors”.

These sensors work via a magnetic contact that creates a closed circuit. When the magnetic contact is “broken”, the system sounds an alarm or alerts the user via an app or other notification methods.
Some window sensors are also known as “glass break” sensors. These sensors attach the glass pane of a window and are triggered by acoustic sounds or vibrations.
Key features to consider when purchasing door and window sensors include:
- Long battery life
- Tamper-proof design
- Arm/disarm feature
- Audible alarm
- Push notifications
- Smart home ecosystem compatibility
How much do smart door and window sensors cost?
Most smart door and window sensors are sold as part of a smart home security kit and are sold through professional-managed home security companies. However, you can purchase door sensors, glass break sensors, or multi-purpose separately for around $15 to upwards of $25-$30 or more.
Smart lights
Smart lighting is among the simplest types of smart home security products you can purchase. Outdoor lighting can reduce crimes against your property by 20 percent. You’ll find smart lighting works similarly to non-smart outdoor lights that use sensors. The technology in smart lighting is notably more advanced, however, making it possible to turn the lights on or off via a mobile device, smart hub, or smart speaker. Many smart lights can also be paired with a larger smart home system and be scheduled to turn on or off in conjunction with other activities.
There are a variety of ways to achieve smart outdoor lighting. You can purchase smart bulbs that work with pre-existing fixtures, install a smart fixture that works with any light bulb, or install a smart switch that operates existing light fixtures.
Smart bulbs have the advantage of being relatively cheap compared to installing a new fixture, but you may see higher costs in the long run. Meanwhile, installing a smart fixture or a smart switch can be costly as well as time-consuming. If you rent your home or apartment, a smart bulb may be the better option as you won’t need to mess around with wires and electricity (or you may be unable to if you’re renting).
Key features to consider when purchasing smart lights include:
- Available installation methods
- Light dimmers/scene-setting
- Auto on/off sensor (motion and/or light sensors)
- Sensor range and angles
- Long battery life (if wireless)
- Weatherproofing (especially for smart lightbulbs)
- Smart home ecosystem compatibility, especially whether or not a bridge or hub device is required
How much do smart lights cost?
Note that smart indoor lights are not a smart home security feature, although you can purchase smart lights for inside use. You can get smart outdoor lightbulbs with simple light-detecting sensors for under $20. More advanced smart lightbulbs can be pricey, with individual bulbs reaching over $30 or $40 for some brands.
If you’re looking for light fixtures, expect to pay over $80 for most good-quality options, like the Ring Smart Lighting fixture, and closer to $150 or more for top-of-the-line and fully-featured fixtures.
Those who opt to go the smart light switch route can find some for $15-$20. However, make sure any smart switch you get actually works with the sensor system on a normal outdoor light, or works within a smart home ecosystem so that it can be triggered by another device that does have a sensor, such as an outdoor camera.
Smart home security hub devices

Smart hub devices are designed to connect to, monitor, and control multiple other smart home devices at once. Hubs make it possible to turn your smart devices on or off at once, for example, or make triggers that will initiate your security device’s various functions and features.
Hub devices typically come in two flavors. They’re either a general-purpose product that works with other brands’ devices, or they operate as part of one brand maker’s smart home kit and only work with that brand’s devices.
The Google Home, Amazon’s Alexa line of devices, Apple HomePod, and Samsung SmartThings Hub are all examples of general-purpose hubs. Independent devices, such as cameras, locks, and sensors, may connect to and be operated through your Google Home, Alexa-enable devices, or HomePod, so long as they are part of the “Works With” program that company offers.
Alternatively, managed smart home security companies usually sell kits that work with an included hub device, but only for that device family. SimpleSafe is an example of a company that sells a kit with its own base/hub station.
Most hub devices use your home internet and WiFi as the chief connection method. However, some can utilize specialized radio frequencies designed for smart products, specifically, Zigbee, Z-wave and Bluetooth (more on these later).
Key features to look for in security hub devices include:
- Offers a list of compatible devices
- Provides long long battery life (if applicable)
- Can be connected via WiFi or Ethernet
- Can be operated via a central app
- Offers voice controls
- Provides scene-setting and rule-setting features
- Sends push notifications for connected devices
- Optional: Has a touchscreen
- Optional: Works with Google Assistant, Amazon Alexa, and/or Apple HomeKit
How much do security hub devices cost?
You can get a smart hub for as little as $20. The Amazon Echo Dot 2nd Generation, for example, sells for $19.99. Any smart device that works with Alexa can be connected to and controlled through your Echo Dot or the Alexa app. The Google Home Mini ($50) and the Apple HomePod ($300) work similarly.
But if you want a more dedicated smart home hub device that focuses only on that purpose, for the Samsung SmartThings hub is a popular option at just under $70.
Smart home automation and communication technologies
Automation is one of the primary benefits of setting up a “smart” home security system versus a traditional one. With a smart system in place, your devices can all communicate with each other and everything can be automated using either a hub device or using an automation tool that communicates with your devices through the cloud.
The important thing here is communication. There are a few communication methods you should familiarize yourself with, and a few automation tools you may want to explore once you have everything setup.
WiFi and Ethernet connections
Even the most casual users likely know what these mean. WiFi covers wireless connection to the internet, while Ethernet connections are hardwired connections to the internet. Every smart home device will have either a WiFi connection or an Ethernet connection. Some have both, but few only use Ethernet. If you find a device that one has one connection method, it’s likely going to be through WiFi.
The limitation for WiFi is that it’s an energy hog. If a device is battery powered and uses WiFi, its battery will drain far faster than if it’s using other communication methods.
Bluetooth
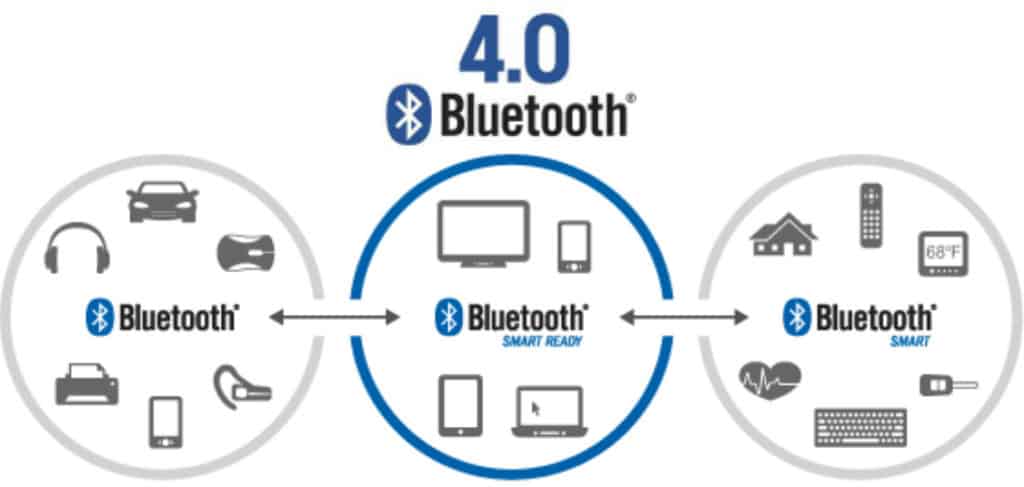
Some smart devices can communicate with your mobile device or smart home hub devices using Bluetooth. Bluetooth is great for longer battery life (especially since Bluetooth Low Energy came to market). However, Bluetooth has a short range, making it more difficult to use at times, especially if you have a large home. As well, some Bluetooth devices can only connect to one other device at a time, so you may find yourself needing a hub or an automation tool to run multiple Bluetooth-enabled smart home security devices.
Zigbee

Zigbee is a communication technology that operates on a high MHz radio frequency. Zigbee products are fairly interoperable, even across newer and older devices. Importantly, each Zigbee device acts as a repeater. Signals can bounce from device to device, up to 30 times. You can have a large network of Zigbee devices in this manner, making Zigbee great for larger homes with a hub device.
If buying Zigbee devices, note that this technology does not exist in smartphones. So you’ll still need a hub device. Few Zigbee devices are designed to operate as standalone security devices, but most will still have WiFi and/or Bluetooth radios for communication.
Z-Wave

Z-Wave is very similar to Zigbee, with a few minor exceptions. It operates on a slightly different radio frequency. And while each Z-Wave device can operate as a repeater, similar to Zigbee, the signal can’t travel as far (only four device bounces before the latency gets too poor to function). That said, Z-Wave devices are known to have better interoperability than most other smart home devices, even across years of production.
Similar to Zigbee, you’ll still need a hub device or will need to make sure any Zigbee devices you purchase have Bluetooth or WiFi connections that you can use to pair them with your smartphone.
IFTTT (If This, Then That)
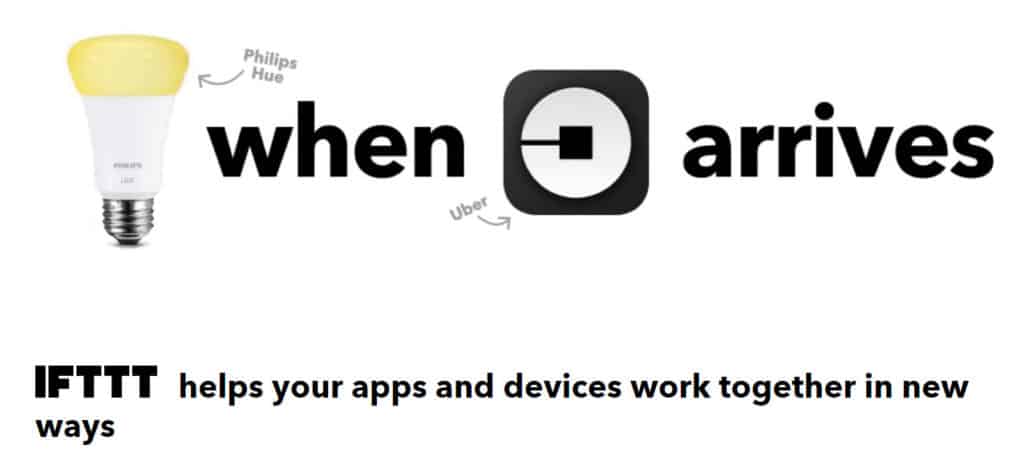
IFTTT is an automation tool that lets you create different protocols for your smart home using “if this, then that” statements. After signing up on the IFTTT website, you can connect to your smart home hub, or forgo a hub altogether and run all of your devices using IFTTT.
The good thing about IFTTT is that it can trigger your devices under far more conditions than any smart home hub will provide (which is why SmartThings heavily supports the use of IFTTT with its hub). You can use IFTTT’s triggers (known as Applets, or rules) to do almost anything your devices are capable of.
For example, if you have a Ring Video Doorbell with person detection and a coffee maker connected to a WeMo smart plug, you could create a rule that says “After 5 PM, if Ring Video Doorbell detects Sam, turn on WeMo coffee maker”. That’s a pretty high-level Applet, however. Most users will opt for more common smart home security triggers, like turning on certain lights depending on who’s detected, or automatically dialing 911 if a window or door break sensor goes off when nobody’s home.
Additional smart home security tips
Even with all the knowledge in the world, you’ll likely run into some problems setting up and operating your smart home. Here are a few tips to help smooth the process.
1. If you plan to use a hub device, buy the hub first
Don’t waste time and money purchasing products for your smart home that don’t integrate well into a cohesive system. If you’re going the DIY route, buy the hub device first. Then, investigate which smart home security devices, (e.g., cameras, locks, lights, etc.) work with your hub. Most hub device makers have a “Works With” program and a list of devices that work with their hubs.
To save you some time, here are a few top Works With product pages:
Once you know which hub device you’d prefer, check out the smart home devices that work with it. Some devices work with multiple hubs, some only work with one. Some devices don’t work with any hubs, which is why it’s important to buy the hub device before you purchase your security products.
2. If you plan to use Zigbee or Z-Wave devices, buy a hub
While Zigbee and Z-Wave devices can work without a hub, they’re not as effective if you go that route. Zigbee and Z-wave devices are best paired with a smart home hub to get the most out of them.
3. If you’re struggling with bandwidth, check your router
Loading your home with smart devices brings a lot of new users face-to-face with the limitations of their current home router. If you have a cheap or older router, you may not be getting the full benefit of the internet speed you’re paying for. All routers experience some bandwidth loss compared to a wired connection, but older and cheaper routers are notoriously slow.
If you suspect your router may be suffering, do the following:
- Perform an internet speed test using an Ethernet-connected computer
- Perform a second internet speed test on the same device, but using the WiFi router connection
If there’s a dramatic difference in speed, your router is most likely the issue. There are a few tricks you can employ that might help boost your internet speed, but there’s only so much you can do with faulty hardware. You ultimately may need to upgrade to a better router. I personally use and love the Netgear Nighthawk, but there are many on the market of equivalent effectiveness.
4. If you’re concerned about security, use a firewall device
Every device on your WiFi network is a vulnerability. If you’re setting up a smart home, you’re also making yourself more vulnerable to hacking. You can significantly reduce that risk by taking some of the standard precautions, such as using a unique WiFi name and a strong password. There are also a growing number of devices designed to add an extra layer of firewall protection to prevent hacking of your network.
We’ve written about the Bitdefender Box as one potential option for this. You may also want to consider some other devices, RATtrap, Roqos Core, and Bullguard Dojo.
See also: Best free firewalls
Image credit: Smart Home Gerd Altmann, Pixabay.


