What is a relay attack? It is similar to a man-in-the-middle or replay attack. All three attack types involve the interception of information with fraudulent intent as to their future use, e.g.:
- Radio signals or authentication messages between two devices (or people) may be hijacked
- An eavesdropping attacker may attempt to locate, intercept, and store a signal directly from a single device, e.g. a vehicle key fob, which constantly emits radio signals to check for the proximity of its owner’s vehicle
- A criminal may send a signal to a victim’s device in order to trick it into sending a response that they can then use to authenticate another device or application
To explain what a relay attack is, let’s look at two similar types of attacks, man-in-the-middle and replay attacks, and compare them to a relay attack.
These attacks are much alike, MITM being the most commonly used term, sometimes incorrectly. Each attack has elements of the other, depending on the scenario. Below are some subtle differences distinguishing each type of attack, sometimes only slightly, from the others. The name of each attack suggests its main technique or intent: intercepting and modifying information to manipulate a destination device; replaying stolen information to mimic or spoof a genuine device; or relaying stolen information to deceive a destination device.
- Man-in-the-middle attacks – Data is intercepted between two parties and can be viewed and modified before the attacker relays the (sometimes altered) data to the intended (or another) recipient. Classically, one of the genuine parties initiates the communication. For example, a thief could intercept a communication between your device and a server, and modify the message, e.g. block your access to the server. MITM attacks can control conversations between two parties, making them think they are talking to each other when each party is really talking to the go-between, the attacker. The SMB relay attack is a version of an MITM attack.
- Replay attack – Unlike man-in-the-middle attacks, in replay attacks the criminal steals the contents of a message (e.g. an authentication message) and sends it to the original, intended destination. For example, a thief could capture the signal from the remote you use to open your keyless front door, store it, and use it later to open the door while you are out, i.e. replay the message. Another example is where an attacker intercepts credentials sent from a network user to a host and reuses them to access a server, confusing the host enough to create a new session for the attacker.
In contrast, in a relay attack an attacker intercepts communication between two parties and then, without viewing or manipulating it, relays it to another device. For example, a thief could capture the radio signal from your vehicle’s key fob and relay it to an accomplice who could use it to open your car door. The main difference between a MITM and a relay attack is, in the latter, neither the sender nor the receiver need to have initiated any communication between the two. In some cases, an attacker may modify the message but usually only to the extent of amplifying the signal.
Three examples of relay attacks
- Vehicle relay theft
- SMB (Server Message Block) relay attack
- Contactless card attacks
1. Vehicle relay theft
When cars are the target, relay attacks are sometimes referred to as relay thefts, wireless key fob hacks, or SARAs (Signal Amplification Relay Attacks). In SARAs, thieves use signal boosters to:
- Extend the range of the radio signals being relayed between accomplices located a distance from each other, in this way allowing thieves greater maneuverability
- Fool cars into thinking their key fobs are in closer proximity than they actually are, as many, if not most, car models open automatically when their fobs are in range
Vehicle relay hacks are increasing
Although few statistics for this trending attack type are available, motor manufacturers and cybersecurity professionals say it is increasing, which suggests it is profitable and / or a relatively easy attack to execute.
Tracker, a UK vehicle tracking company, said, “80% of all vehicles stolen and recovered by the firm in 2017 were stolen without using the owner’s keys.” In the US, 765,484 cars were stolen in 2016 but how many were keyless cars is uncertain as makes and models are not recorded. Business Wire (paywall) estimates the car security market will be worth $10 billion between 2018 and 2023.
The potential for relay attacks on vehicles was reported at least as far back as 2011, when Swiss researchers announced they had successfully hacked into ten keyless cars. At the time, security experts thought the criminal threat was low risk as the equipment, in those days, was too expensive. Today, it requires very little capital expenditure. The devices to execute relay attacks are cheap and freely available on sites such as eBay and Amazon.
How do keyless cars work?
A traditional car key is replaced by what is known as a fob or remote, although some people call it (confusingly) a key. Let us call it a key fob. The key fob acts as a transmitter, operating at a frequency of about 315 MHz, which sends and receives encrypted RFID radio signals. The transmission range varies between manufacturers but is usually 5-20 meters. Antennas in the car are also able to send and receive encrypted radio signals. Some vehicles use Bluetooth or NFC to relay signals from a cell phone to a car.
As explained in Wikipedia, a Remote Keyless System (RKS) “refers to a lock that uses an electronic remote control as a key which is activated by a handheld device or automatically by proximity.” Depending on the vehicle model, the key fob may be used to start the car (Remote Keyless Ignition system), but sometimes it will only open the car (Remote Keyless Entry system) and the driver will need to press an ignition button. Bear in mind, some attackers do not wish to steal the vehicle; they may just be after anything valuable inside, like a laptop on the back seat.
How is a relay attack executed on your car?
Key fobs are always listening out for signals broadcast from their car but the key fob needs to be quite close to the car so the car’s antenna can detect the signal and automatically unlock the car. Criminals can use radio amplification equipment to boost the signal of a fob that is out of range of the car (e.g. inside the owner’s home), intercept the signal, and transmit it to a device placed near to the car. This device then sends the “open sesame” message it received to the car to unlock it.
Types of vehicle relay attacks
The waiting game
According to the Daily Mail, their reporters purchased a radio device called the HackRF online and used it to open a luxury Range Rover in two minutes.
“Priced at £257, the device lets criminals intercept the radio signal from the key as a car owner unlocks the vehicle. It is downloaded to a laptop and the thieves then transmit the stolen signal to break in when the owner leaves it unattended.”
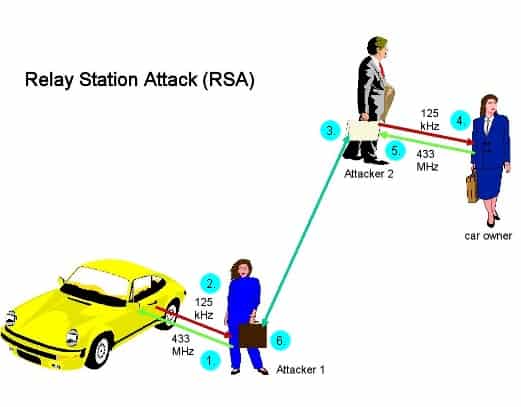
Relay Station Attack (RSA)
Key fobs are sometimes called proximity keys because they work when the car’s owner is within range of their car. Reported by Jalopnik, researchers at Chinese security company Qihoo 360 built two radio gadgets for a total of about $22, which together managed to spoof a car’s real key fob and trick a car into thinking the fob was close by.
In the Qihoo 360 experiment, researchers also managed to reverse engineer the radio signal. They did it by recording the signal, demodulating it, and then sending it out at a lower frequency, which enabled the researchers to extend its range, up to 1000 feet away.
Relay station attack (Source: slightly modified from Wikipedia)
In the above scenario:
- The first thief sends a signal to a car, impersonating a key fob
- The car replies with a request for authentication
- This signal is transmitted to the second thief, stationed near the real key fob, e.g. in a restaurant or mall
- The second thief relays this signal to the fob
- The fob replies with its credentials
- The second thief relays the authentication signal to the first thief who uses it to unlock the car
Remote interference
Attackers may block the signal when you lock your car remotely using a fob. If this happens, unless you physically check the doors, you may walk away leaving the car unlocked.
2. SMB (Server Message Block) relay attack
Windows transport protocol vulnerability
SMB is a transport protocol used for file and printer sharing, and to access remote services like mail from Windows machines. An SMB relay attack is a form of a man-in-the-middle attack that was used to exploit a (since partially patched) Windows vulnerability.
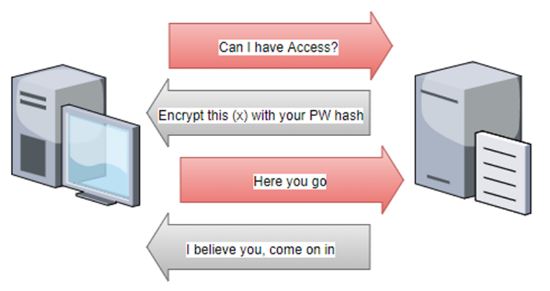
A Windows computer in an Active Directory domain may leak a user’s credentials when the user visits a web page or even opens an Outlook email. NT LAN Manager Authentication (the network authentication protocol) does not authenticate the server, only the client. In this scenario, Windows automatically sends a client’s credentials to the service they are trying to access. SMB attackers do not need to know a client’s password; they can simply hijack and relay these credentials to another server on the same network where the client has an account.
NTLM authentication (Source: Secure Ideas)
It is a bit like dating
Leon Johnson, Penetration Tester at Rapid 7, explains how it works with an amusing, real-world analogy. In this scenario, two guys are at a party and one spots a pretty girl. Being somewhat shy, the first chap, Joe, asks his friend, Martin, to go and chat to the girl, Delilah, and perhaps get her number. Martin says he is happy to oblige and confidently goes up to Delilah, asking her for a date. Delilah says she only dates BMW drivers. Martin gives himself a mental high-five and returns to Joe to ask him for his (BMW) car keys. He then goes back to Delilah with the proof he is the kind of guy she likes to date. Delilah and Martin set a date to meet up and then she leaves. Martin goes back to Joe, returns his keys, and tells him Delilah wasn’t interested in a date.
The principal is similar in a network attack: Joe (the victim with the credentials the target server called Delilah needs before allowing anyone access) wants to log in to Delilah (who the attacker wishes illegally to break into), and Martin is the man-in-the-middle (the attacker) who intercepts the credentials he needs to log into the Delilah target server.
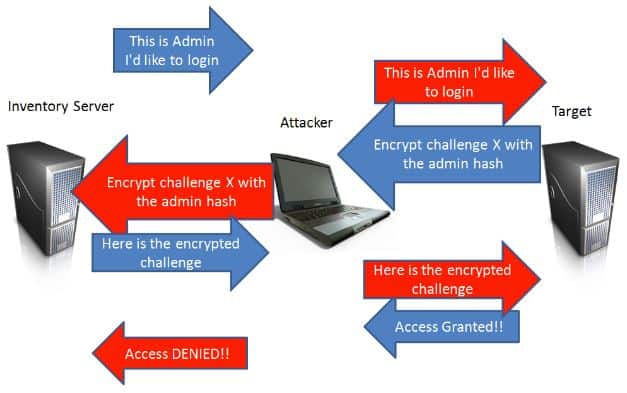
In the below diagram from SANS Penetration Testing, the Inventory Server is Joe, the Attacker is Martin, and the Target is Delilah. If you are an in-house ethical hacker, you might like to try this attack with Metasploit.
How an SMB Relay Attack works (Source: SANS Penetration Testing)
3. Contactless card attacks
A contactless smart card is a credit card-sized credential. It uses RFID to communicate with devices like PoS systems, ATMs, building access control systems, etc. Contactless smart cards are vulnerable to relay attacks because a PIN number is not required from a human to authenticate a transaction; the card only needs to be in relatively close proximity to a card reader. Welcome to Tap Technology.
Grand Master Chess problem
The Grand Master Chess problem is sometimes used to illustrate how a relay attack works. In an academic paper published by the Information Security Group, titled Practical Relay Attack on Contactless Transactions by Using NFC Mobile Phones, the authors explain: Imagine someone who doesn’t know how to play chess challenging two Grand Masters to a postal or digital game. In this scenario, the challenger could forward each Master’s move to the other Master, until one won. Neither Master would know they had been exchanging moves via a middleman and not directly between each other.
Stolen credentials
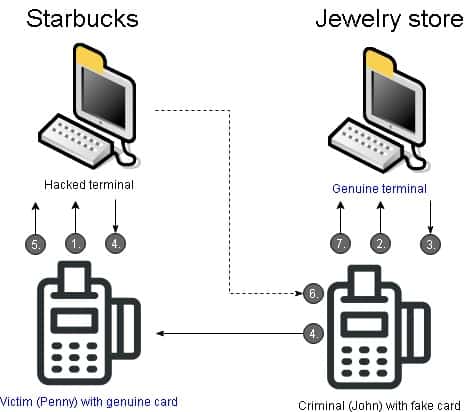
In terms of a relay attack, the Chess Problem shows how an attacker could satisfy a request for authentication from a genuine payment terminal by intercepting credentials from a genuine contactless card sent to a hacked terminal. In this example, the genuine terminal thinks it is communicating with the genuine card.
- The attack starts at a fake payment terminal or a genuine one that has been hacked, where an unsuspecting victim (Penny) uses their genuine contactless card to pay for an item.
- Meanwhile, a criminal (John) uses a fake card to pay for an item at a genuine payment terminal.
- The genuine terminal responds to the fake card by sending a request to John’s card for authentication.
- Pretty much at the same time, the hacked terminal sends a request to Penny’s card for authentication.
- Penny’s genuine card responds by sending its credentials to the hacked terminal.
- The hacked terminal sends Penny’s credentials to John’s card.
- John’s card relays these credentials to the genuine terminal.
Poor Penny will find out later on that memorable Sunday morning she bought a cup of coffee at Starbucks she also purchased an expensive diamond necklace she will never see.
Underlying network encryption protocols have no defense against this type of attack because the (stolen) credentials are coming from a legitimate source. The attacker does not need even to know what the request or response looks like, as it is simply a message relayed between two legitimate parties, a genuine card and genuine terminal.
How can you prevent relay attacks?
Distance bounding protocols for contactless card attacks
In 2007, Cambridge researchers Saar Drimer and Steven Murdoch demonstrated how a contactless card attack could work and suggested distance bounding (narrowing the window of opportunity) as one possible solution. In a research paper – Chip & PIN (EMV) relay attacks – the duo said the technique of distance bounding could prevent the risk of relay attacks on contactless cards by measuring how long a card takes to respond to a request from a terminal for identification.
“Since information cannot travel faster than the speed of light, the maximum distance between card and terminal can be calculated. By carefully designing the communication method cards use, this estimate can be made very accurate and ensure that relay attacks over even short distances (around 10m for our prototype) are detected.”
Banks are cagey about security, but distance bounding was apparently implemented by MasterCard in 2016.
According to researchers at Birmingham University, distance bounding is not a practical option for contactless card theft as incorporating new protocols into the existing infrastructure would be complex and costly. In addition:
“As contactless transactions can only be used for small amounts without a PIN, and the use of specialized equipment may raise suspicion (and so the chance of getting caught) such an attack offers a poor risk/reward ratio.”
How can you mitigate an SMB attack?
According to Fox IT, the only solution to SMB attacks is to disable NTLM completely and switch to Kerebos. If you can’t (perhaps you are running legacy software), the following configuration suggestions from Fox IT may help mitigate the risk of attack. The links provide step-by-step instructions about how to configure Microsoft workstations.
- Enabling SMB signing – All messages have to be signed by the client machine at the authentication stage. As attackers don’t have the session key/password, they will not be able to access the server even if they manage to relay the request.
- Enabling EPA (Enhanced Protection for Authentication) – This technique ensures the client and server use the same TLS connection and requires the client sign it
- Enabling LDAP (Lightweight Directory Access Protocol) signing – Similar to SMB signing, but this setting, according to Fox IT, “will not prevent relay attacks to LDAP over TLS.” This warning is echoed by Preempt: “…while LDAP signing protects from both Man-in-the-Middle (MitM) and credential forwarding, LDAPS protects from MitM (under certain circumstances) but does not protect from credential forwarding at all.” The solution, according to Preempt, is to download the Microsoft patch for this vulnerability.
- Enabling SPN (Service Principal Name) target name validation – Validates the target name against which it is authenticating with the server name
- Only use HTTPS – When internal websites are visited over HTTP, authentication is virtually impossible and the chance of a relay attack increased
- Disabling automatic intranet detection – Only allowing connections to whitelisted sites
- Disabling WPAD ( Windows Proxy Auto Detection) – The Microsoft MS16-077 patch addresses most WPAD vulnerabilities but disabling this feature is recommended
- Disabling LLMNR/NBNS – These are insecure name resolution protocols which may allow attacks more easily to spoof genuine URLs
Visit Microsoft for more suggestions on how to restrict and manage NTLM usage at your organization.
Preventing a relay attack on your car
- Keep the fob’s software updated
- An attacker will try to clone your remote’s frequency. Keeping your remote in a protective RFID pocket will block the frequency from attackers listening out for its signal.
- Never leave an unlocked key near a window or on the hall table. Thieves are constantly driving around neighborhoods looking for a radio signal. A low-tech option to shield your remote is to wrap it in silver foil, or put it in a metal tin or even your microwave. Warning: if you accidentally microwave your key, you could damage the microwave and the key.
- If you can, switch your remote off
- Use added protection, e.g. keep your car in a locked garage, or use a low-tech steering lock or wheel clamp. The latter suggestion is quite comical, suggest users in community forums: “Yes, I want keyless entry. So handy and trendy. just need to lug this 10Kg object around as well.“
- Buy a Faraday cage, box, pouch, wallet, or case from Amazon (yes, those are the same guys from whom criminals can buy the equipment to hack into your car)
- Install an OBD (On-Board Diagnostic) port lock. Thieves can potentially break into OBD ports, which manage various data in your car and can diagnose faults and malfunctions, and, at worst, take control of some car components.
- When it comes to vehicle break-ins, it may be a case of back to the future: prevent theft simply by ensuring valuables are out of sight. Reported by The Daily Standard, thieves are often more likely to target the contents of a vehicle than the vehicle itself. Many are happy enough to score a few dollars towards a drug habit. At around $22, a relay theft device is a relatively small investment.
- Tesla has a mobile app which links to a car via Bluetooth on a smartphone to open it. Later models have the option to enable the need for a PIN before the car starts. You can turn PIN activation on by disabling passive entry.
- Check your car doors are locked and criminals haven’t blocked the lock command you issued with the remote when you left the car.
Cybersecurity is like a ping pong game
New technologies are embraced by criminals, upon whose shoulders is not the onerous task of deploying patches every time a new vulnerability is found, or configuring new ways to circumvent security holes. To someone keeping up with cybersecurity news, the score between cybersecurity professionals and criminals is currently 1:1:
- Once Captcha was smart enough to tell if a website visitor was human or not. Today, criminals are relaying Captcha images and puzzles to Captcha sweat shops where humans solve the puzzles and send the results back to an attacker’s bots. Sweat shop jobs are advertised on freelance websites and commission is based on how many Captchas a freelancer can solve in a certain period of time.
- Once used only for short distance communications, according to RFID Journal, these days an RFID reader (also known as an interrogator) “using a beam-steerable phased-array antenna can interrogate passive tags at a distance of 600 feet or more.”
- Once hacking equipment was expensive. Today, manufacturers of hacking equipment like car-theft kits flaunt their wares legally online; these devices are legal to buy but illegal to use fraudulently. Thieves don’t care.
- Once exploit toolkits were purchased on the Deep Web, making cybercrime easy but requiring a small capital outlay. Today, open source software on the internet, like Metasploit, used by white hat pentesters to test for vulnerabilities in their systems, is a free and welcome addition to a hacker’s toolkit.
- As far back as 2014, an Info World article claimed, “encryption is (almost) dead.” While encryption lives on and is a major deterrent in most cybercrimes, it is irrelevant to criminals executing relay attacks.
To keep up with cybercrime, more cybersecurity professionals are needed. According to CSO, the number of unfilled cybersecurity jobs will reach 3.5 million by 2021. By that time, new types of attacks will probably have superseded relay attacks in headline news.
Related:
100+ Terrifying Cybercrime and Cybersecurity Statistics & Trends
Finding your first job in cybersecurity
Image for Betaalpas en logo contactloos betalen by nieuws via Flickr. Licensed under CC BY 2.0