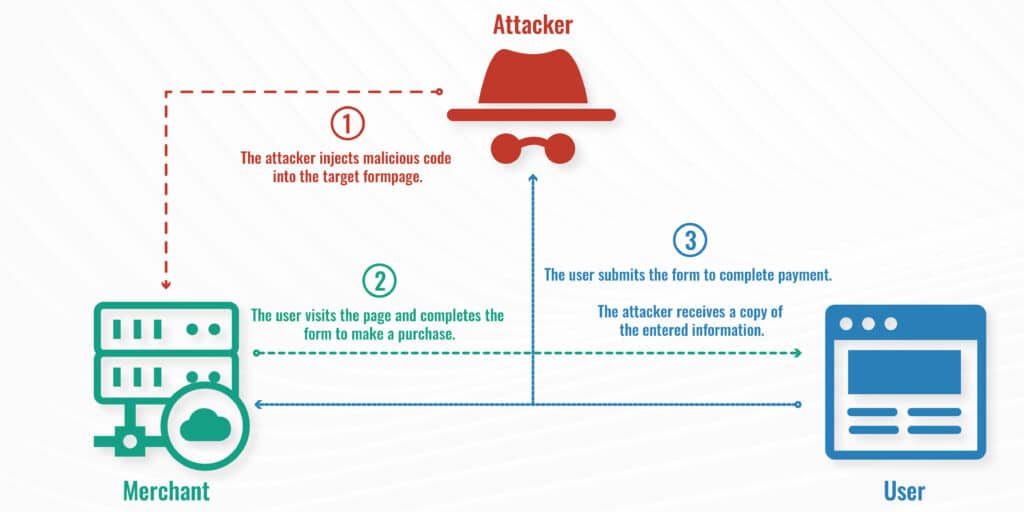
Formjacking involves the use of malicious JavaScript code to steal personal and financial information from website forms. Cybercriminals attack the form page itself, then each time someone fills out a form, a duplicate of the entered information is sent to the attacker.
This practice can affect any organization that accepts online payments from customers. It puts consumers at risk of credit card fraud, identity theft, and other types of fraud, and can be damaging for a company’s reputation. Formjacking is discreet and doesn’t require any user action, so it’s a very attractive option for cybercriminals looking to make some easy money.
In this article, we reveal more about how formjacking works, including some real-world examples, and how to prevent it.
See also: Best identity theft protection services
What is formjacking?
Formjacking can be thought of as new-age card-skimming. You’ve probably heard about the scenario in which a small device — known as a skimmer — is added by criminals to card readers at a point of sale. This device can read and store information from the card’s magnetic strip. Heavily targeted card readers include those at ATMs and gas pumps. These are easily accessible compared to, for example, a card reader located alongside an in-store cash register.
Formjacking follows a similar concept to card skimming but has been adapted to the online world. This makes the practice more far-reaching than skimming and easily accessible to cybercriminals across the globe. Formjacking is relatively simple to execute, another likely reason it’s becoming increasingly attractive to data thieves.
An attack begins when they insert JavaScript code into the target website. Note that it usually takes the form of a supply chain attack and targets code provided by a third party, not the website itself.
Once the malicious code is in place, when the user enters their information and sends the form to the website, all details are also sent to the attacker.
When the user hits “Submit” or the equivalent, the transaction goes through as normal so there’s no sign that anything is awry. This is why it’s difficult for either the user or the website owner to detect formjacking until it’s too late.
How concerned should we be about formjacking?
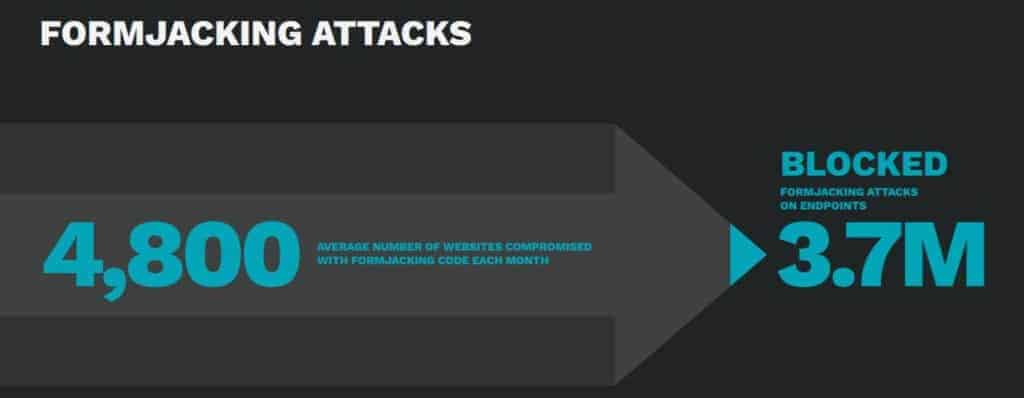
Formjacking has been on the rise in recent years. In its 2019 ISTR report, Symantec reported having identified an average of 4,800 websites each month that had been compromised using formjacking code. In 2018, Symantec blocked a whopping 37 million formjacking attempts.
Criminals typically use formjacking to target websites that collect payment information such as e-commerce sites. While personal details can be valuable to criminals, payment data is especially sought-after. Criminals can either use credit card and billing information directly in credit card fraud or they can sell the details to the highest bidder.
Formjacking can be highly lucrative. According to Symantec a set of credit card details can fetch up to $45 on the dark web. When you consider criminals can steal the details of thousands of cards from just one site, this quickly adds up.

As a consumer, there are a few ways you might find out that you’re a potential victim of a formjacking attack. You may be contacted by the company involved directly or find out from a news report or announcement. For example, British Airways took out ads in newspapers as part of its attempts to alert (and apologize to) users after a formjacking attack.
Alternatively, if your credit card details have been used, you may find out through your bank, either by noticing unusual activity on your card yourself or having your bank contact you directly.
Examples of formjacking
So what types of websites are under attack? To illustrate this growing problem, here are some real-world examples of formjacking attacks:
- Sixth June: In October 2019, it was discovered that the checkout page of this fashion retailer’s website had been formjacked. It’s unclear how many customers were affected but it was believed to have been in the thousands.
- Ticketmaster: Between September 2017 and June 2018, up to 40,000 Ticketmaster customers fell victim to a formjacking attack. The fault was laid on Inbenta, a chat support tool that had created code for Ticketmaster’s site. The attack was only discovered when an online banking platform, Monzo, discovered that some of its customers’ cards had been compromised.
- British Airways: In September 2018, British Airways apologized after 380,000 customers had their card details stolen in a formjacking attack. The attack took place over two weeks and the thieves stole all the information they needed to make an online purchase with the credit card details, including names, addresses, card numbers, expiry dates, and security codes.
- Newegg: Online retailer Newegg was the subject of a month-long formjacking attack in August and September 2018. The attack appeared to be almost identical to the British Airways and Ticketmaster cases.
Many attacks appear to have involved a cybercriminal operation dubbed Magecart. This is a consortium of hacking groups that target online checkout systems. They usually target the Magento system, hence the name Magecart.
The formjacking attacks affecting British Airways, Ticketmaster, and Newegg were all attributed to the Magecart group.
How consumers can prevent formjacking
Many of us complete online transactions on a daily basis without a second thought, assuming the websites we’re using are secure and have our backs when it comes to protecting our information.
Thankfully, there are a couple of ways we can have a bit more control over the security of our payment information.
One is to consider using a masked credit card. These cards, offered by certain financial institutions, provide you with a set of card details for one-time use, either online or in a store. Once the details have been used, they are no longer valid for future purchases. Masked credit cards are often misleadingly referred to as “fake” credit cards, but they are legitimate forms of payment.
Another option is to look into payment methods that use tokenization. This is another way to add an extra layer of security to credit card payments and is used by systems like Apple Pay and Google Pay. The concept is similar to a masked credit card and a “token” is used to replace the real credit card number.
How consumers can detect and deal with formjacking
Formjacking is often difficult to detect, but there are some steps you can take to find out sooner rather than later and mitigate the resulting damage.
- Check your credit card account: If you suspect you’re the victim of formjacking, assuming you use online banking, you should be able to check for yourself if your card has been used. If not, call your bank to go over recent transactions in case there are any you don’t recognize.
- Cancel your card: If you believe a card may have been affected, call your bank immediately so they can cancel the card and send you a new one.
- Monitor your accounts on an ongoing basis: Even if you haven’t been notified of a formjacking attack, it’s important to always keep a close eye on all of your bank statements to check for account and credit card fraud.
- Check your credit score regularly: Some criminals won’t use your card directly but will instead use your personal information to set up a new account. Since you don’t know the account exists, this type of identity fraud can go undetected for a long time. A change in your credit score can be a telltale sign that someone has used your details to borrow money.
- Purchase identity theft protection: You might prefer to have peace of mind that someone is monitoring your accounts and credit score on your behalf. In this case, you can sign up with an identity theft protection service such as those offered by IdentityForce or LifeLock.
How businesses can prevent formjacking
Do you run a website that accepts online payments? Although our real-world examples above include some ecommerce giants, there have been reports of businesses of all shapes and sizes coming under attack. There are some steps you can take to avoid this nasty attack happening on your site.
- Use a solid antivirus software: A reputable antivirus software can help protect against some (but not all) formjacking attacks.
- Run penetration tests and vulnerability scans: These can help identity software vulnerabilities so you can patch them before a hacker finds them.
- Rigorously test updates: It’s important to test new updates for any odd behavior. The most prominent formjacking attacks have been software supply chain attacks, so it’s crucial to have strict testing in place for any third-party software.
- Monitor for behavioral pattern changes: Proper monitoring of a system may help you spot suspicious patterns and block offending applications before more damage is done.
Even with all of these measures in place, it can still be extremely tough to spot formjacking until it’s too late. As such, you need to ensure you have protocols in place for swiftly alerting customers in case of an attack.
See also: