A botnet is a group of computers controlled by a hacker. The method of control combines two key advantages for the hacker. First, it amplifies the damage they can do, and second, the attacks don’t originate from their own computer, which makes them nearly impossible to trace.
If your computer is infected by malware, this would not only make you a victim of cybercrime, but unwittingly, an accomplice as well. In this article you will find out how botnets are created, what they do, and how you can prevent your computer from being controlled by a hacker.
What do botnets do?
Botnets can be used for any type of hacker attack. However, they are mostly used in those attack strategies that require traffic volume. A botnet can contain anywhere from 100,000 to north of 5 million zombie computers.
The three main purposes of botnets are click fraud, spam email distribution, and DDoS attacks.
Click fraud
One ecommerce pricing model charges advertisers a tiny amount each time someone clicks on their advertisements on a web page. Some online publications charge per page impression, which is the number of times the page containing the advert is loaded into a browser.
These two methods of paying to display advertisement online are open to abuse. Even if third-party tracking systems can verify the reported number of clicks or impressions, there is no immediate way to evaluate the quality of those contacts. So, it is impossible to tell whether a web surfer clicked on a link because she was genuinely interested in learning more, or got tricked into clicking. Equally, it is impossible to tell whether that click was actually made by a mouse, or generated by a program.
The origin of each visitor can be checked because every computer that is connected to the internet has a unique address and the actions performed on a site from those addresses can be logged.
So, the statement of activity will show different source address for every event. However, in click fraud, those hundreds of thousands of visitors to a page were actually the zombie computers in a botnet directed by a hacker and not real consumers at all.
Spam email
Have you ever received replies from friends asking why you sent an email recommending a pre-approved credit card, or pills to heighten sexual prowess? Of course you didn’t send those emails — a hacker got into your account and sent out spam email to all of the people in your contacts list.
Botnets are used to gather login credentials through phishing emails. These emails look like they come from your webmail provider and tell you that you must follow a link and log in again. That link takes you to a copy of the login page, which is owned by the hacker. When you log in, you give the hacker your credentials to get into your email account.
The fake login request is called “phishing” and it also used to try to trick people into handing over login details for a wide range of online services, including eBay, PayPal, Amazon, and online banking.
Nowadays, these speculative emails are managed through botnets. The hacking of email accounts to deliver spam is also accomplished through botnets. In a phishing campaign, the botnet provides the hacker anonymity. When delivering spam, however, the attraction of a botnet is more one of volume. The identity of the sender could always be traced by tracking down who the advertiser paid to deliver the advertisement by email.
DDoS attacks
The “distributed denial of service,” or DDoS attack is the most common use of botnets. When you access a web page, your browser sends a request to the host server of the site. The browser will only wait so long. If no response is received within a matter of seconds, the browser will give you one of a range of error messages to inform you that request timed out or the page is not available.
In most cases, those error messages do not properly explain the situation. In fact, the host of that web page that you wanted could be under a DDoS attack.
Website hosts can only reply to so many requests at once. Sites that expect a lot of traffic put load balancers in front of their servers. These devices distribute traffic evenly over an array of servers. However, if demand for pages held by a host exceeds the capacity for the system to respond, arriving requests get put in a queue, or just get ignored if there is no queuing system in place.
The sheer quantity of requests that can be sent all at once through a botnet overwhelms even the largest host server arrays and queuing systems. Genuine requests get pushed so far to the back of the queue that your browser gives up waiting for a response and tells you that the page is unavailable.
DDoS attacks have now become so ambitious that they attract international headlines. A 2016 attack on an internet addressing system blocked off Amazon, Twitter, and Netflix. This attack was made by the Mirai botnet. The Russian government uses DDoS attacks frequently to destabilize democracies in its former satellite states. In 2016, the Bulgarian Electoral Commission’s website received 530 million page requests in one day, despite the fact that the country’s entire population is just 7.2 million.
Sony’s servers were blocked off through a DDoS attack in 2014, which locked out online gamers. According to cybersecurity firm Akamai, the online gaming and gambling sector is the biggest target of DDoS attacks. Many games’ servers are constantly under attack and DDoS attacks on individual players are becoming increasingly common.
Botnet industry
The owner of a botnet is called a botmaster or a bot herder.
The botmaster isn’t the only person who can use the botnet. Some botmasters never actually launch their own attacks. Instead, some botnets are just meant to be a service for hire. Even hackers who have agendas for their botnets will also rent out their spare hours as cybercrime infrastructure. Many botnet attacks are paid for and launched by people who don’t even run the botnet.
Attack duration
The emergence and evolution of the botnet industry might explain the changing characteristics of attacks. Akamai’s research highlights some interesting details. Although the volume of traffic in attacks keeps increasing, the average attack length seems to be decreasing. This is probably due to a new market for the industry: attacks on individuals rather than corporations.
Originally, botnet-for-rent services were available in blocks of 24 hours. However, a direct-to-public approach has created the availability of attacks that last just one hour, 20 minutes, or even five minutes.
Short bursts of attacks are just what gamers and poker players need to knock out a key opponent and win the game. These DDoS-for-hire services are becoming widely available on well-known sales platforms. This new development in the industry might also account for Akamai’s discovery that the majority of attacks are directed towards online gaming and individual gamers.
A short attack can now be bought for $5, which brings the price of renting an attack within the budget of vengeful teenagers.
Botnet types
Botnets are not the only method that hackers can use to launch an attack. Cloud storage services are also useful sources of attack clones and hitting a DNS, time, or mail server with spoofed source addresses can increase the volume of traffic directed at a target computer by a factor of 20.
Cloud-based and reflector attacks are more complicated and more likely to be used in bespoke attacks rather than by a rental service. Botnets take time to assemble, and once those zombie computers have been infected, the hacker has little more to do other than issue attack commands.
This means that the cost of maintaining a botnet is marginal and the bot herder is unlikely to walk away from it while there is extra money to be squeezed out of their system. This is why the cost of a DDoS-for-hire attack keeps falling. Short, cheap attacks make DDoS accessible to a consumer market and help hackers find new sources of income in an increasingly crowded supplier pool.
Trojans and zombies
You probably know what a computer virus is. It is a piece of malware that gets onto your computer over the internet or on an infected USB stick or DVD. Firewalls block incoming connection requests, which was the original way that viruses snuck onto your computer over the internet. However, firewalls don’t block incoming messages if they are in response to an outgoing request.
Hackers developed Trojans so that they could open up a connection from behind a firewall and let any other program onto the computer. All the major software producers release updates for their apps. Their programs periodically check in with their home servers and look for instructions. If there is an update available, that program will be downloaded onto your computer. Trojans use the same operating methods. Once a hacker has a Trojan on your computer, he can put more malware on his server, which the Trojan will download and install automatically.
The initial Trojan only needs to be a very small program. Its task is just to initiate downloads. The bigger, more complicated, and damaging programs come later. One of those newer programs may make your computer a “zombie.” Zombie computers are the members of the botnet. So, a botnet is a group of zombie computers.
The zombie goes one stage further than a Trojan. It not only spies on your activities and sends your private data to its controller, but it will also launch attacks on other computers on command. Essentially your computer becomes a relay station for the attack. The gall of this strategy is that if anyone ever traces the source of the attack, you will get blamed and not the hacker.
Zombie detection
It is difficult to detect whether your computer has been co-opted into a botnet. Although an attack generates very large volumes of traffic, the contribution of each zombie is not very taxing. In each attack, the individual zombie may only be commanded to send one message. It is the coordinated flood of fake request messages from hundreds of thousands of sources that makes DDoS attacks so effective, so you may not notice any performance impairment on your computer.
Another factor that makes your computer’s participation in a botnet difficult to detect is the obscurity of process names used by your computer. You can look at the active processes in your Task Manager, but only find non-specific task names such as “Service Host” or “System.” The frequency with which legitimate software looks for updates, downloads, and installs them can also account for high volumes of activity on your computer when it should be idle.
Fortunately, a few services will help you identify botnet activity on your computer. These three online botnet detection services are free to access:
Kaspersky’s Simda Botnet IP Scanner
This site does a quick check against the Kaspersky database of infected IP addresses. The anti-virus company scans the internet for botnet traffic and logs the addresses of those computers found to be participating in DDoS attacks. So, as soon as you connect to the page, you will be able to see whether your computer has taken part in an attack. If you are not on the list, you can be more confident that your computer is not part of a botnet.
Sonicwall’s Botnet IP Lookup

Sonicwall’s utility works on the same logic as the Kaspersky checker by looking up addresses in a list of zombies. There is one small difference with this facility, though: it does not automatically detect your IP address. You can find your own IP address simply by Googling, “What’s my IP?” However, you also get the opportunity to check the status of addresses other than your own.
RUBotted
This botnet detection is the product of the reputable cybersecurity company Trend Micro. Curiously, you can’t get the standalone detection utility from the company’s own website, but you can get it from Cnet. Trend Micro has integrated the functionality of the RUBotted detection system into its free botnet software removal tool, which is called HouseCall (see below).This tool launches on system start up and keeps operating as a background process to alert you to potential botnet zombification.
Botnet program removal
Getting clean and staying that way is a three stage process. You need to detect whether your computer is already part of a botnet, remove the controlling program, and then install blockers that keep the malware off your device. Some utilities will perform all of these functions.
HouseCall
This is Trend Micro’s cleanup program that originally complimented RUBotted. However, now the utility includes detection methods, which means that if you install HouseCall, you won’t need RUBotted as well. This free service also clobbers viruses, worms, Trojans, and other forms of malware.
Norton Power Eraser

This is a free Norton tool from Symantec’s consumer brand. This cleaner goes beyond the usual procedures of your typical malware removal tool. You will need to reboot during the cleaning operation. The company admits this utility is a little overzealous, sometimes identifying legitimate programs as malware. However, it is better to be safe than sorry.
Quick Heal Zombie Removal Tool
This free botnet cleaner was developed at the behest of India’s Ministry of Electronics and IT. This is just one example of how governments in advanced and developing economies are encouraging tech enterprises to develop botnet blocking software and distribute it for free.
Zombie protection
Fortunately, most operating system and browser companies are aware of botnet malware and they constantly shut down security weaknesses to make it harder for all types of malware to get on your computer and create havoc. So, the first strategy you need to deploy in order to protect your computer or mobile device from infection is to make sure you always upgrade to the latest versions of software.
Most software updates are free of charge, so it is worth allowing well-known apps to update automatically. However, major new versions of these systems are sometimes released as separate products, which means that you have to buy it again.
Worse, still, some older versions of software become “desupported” and older computers may not be capable of running the latest operating system version. In these cases, it is better to just buy a new computer.
Beyond keeping your computer and software up to date, here are some other strategies to deploy.
Protect your wifi
Fake wifi hotspots and open hotspots can give hackers access to your mobile device or laptop
This will allow them to download botnet and Trojan programs. If you like to go to a café or bar that has free wifi, be careful about which network you connect to. There may be more than one. Any device with a wireless network card can create a wifi hotspot. That includes other computers and phones, not just routers.
You may notice that when you open the list of available networks, several devices are listed
These usually have names that give you an idea of whether they are hotspots created by nearby phones or laptops. However, anyone can easily change the network name (SSID) to appear as though it is an official service supplied by the premises.
By giving a fake hotspot a similar name to the business (e.g. “Starbucks Wifi”) and using the same password as the official hotspot, the hacker can trick you into connecting.
The initial phase of connection involves the exchange of security keys, which will protect the transmission of data between you and the hotspot from snoopers. However, the hotspot controls that process, so if the hacker designates the key that your device will use for the session, then he can intercept and read all data sent and received through the network. This enables the introduction of malware, which could include botnet software.
Open hotspots do not require you to enter a password
Your laptop or mobile device will keep searching for wifi signals even when it is in sleep mode. It will always try to connect whenever it can.
To prevent this scenario, turn off wifi on your mobile device or laptop before you leave the house. Turn it on again when you reach your destination and have access to a trusted hotspot.
Install a VPN with automatic wifi protection.
The software creates an encrypted tunnel that only the client program on your device and its home server can decrypt. This means that even if you end up running your connection over a hacker hotspot, no botnet or Trojan program can invade your computer, phone, or tablet.
Mobile devices are the current fad among hackers looking for botnet zombies. Towards the end of 2017, the WireX virus made botnet zombies of 150,000 Android devices in a matter of weeks.
Enable firewall and antivirus
Install a firewall,get an antivirus program and keep them turned on
Although free anti-virus is usually no good, the producer of your operating system likely has integrated firewall and anti-virus options that cost nothing to use.
At times, you may be frustrated by your firewall blocking access to certain utilities and preventing you from downloading cool free software. However, pay attention to these recommendations because they are aimed at keeping your computer free of Trojans and zombie control programs.
Get DDoS protection
VPNs provide privacy on the internet
Some VPN providers have expanded their services to add on DDoS protection. NordVPN, ExpressVPN, VyprVPN, PureVPN, and TorGuard are just some companies able to absorb very large volumes of DDoS attacks.
This service would be ideal for gamers and gamblers who frequently fall prey to attacks at crucial moments of a game. In this scenario, you are represented by an internet address provided by the VPN company. All traffic headed for you goes first to the VPN server, which has the capacity to absorb superfluous requests. The genuine requests get passed on to you down an encrypted tunnel.
The VPN solution is also a good option for small businesses that run their own web servers
In this case, you would need to buy a dedicated IP address service from the VPN. That IP address gets registered as the host of your website. You need to maintain a permanent connection to the VPN server that your IP address is allocated to.
When DDoS attacks on your website occur, they pass first through the VPN server, which filters out the fake requests, while passing on genuine web page requests to your server down an encrypted tunnel.
The encryption protection between you and the VPN server is an essential part of DDoS protection. You don’t want hackers to discover your real IP address because then they could bypass the VPN server and attack your host server directly.
More sophisticated solutions for larger businesses are offered by Cloudflare, Akamai, and Incapsula
These companies also employ VPN connections between their servers and their clients. Again, as with the VPN DDoS protection, a second IP address is acquired for the client and that points to the protecting server.
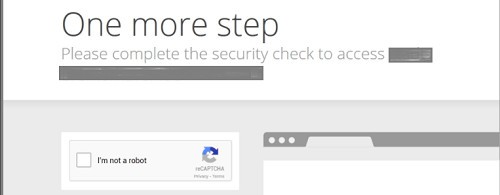
Cloudflare is notable for its challenge pages. When you see a pre-screen on a website that expects you to declare “I am not a robot,” that’s Cloudflare in action.
There are many different types of DDoS attacks and when traffic volume rises to dangerous levels on an IP address protected by one of these DDoS mitigation services, the companies kick in a diversion of all traffic to “scrubbers.” These servers examine incoming requests for the characteristics of botnet activity and drop any suspicious requests, while passing on genuine traffic to the client.
Download torrents with caution
Be very careful about what you download
Torrenters usually don’t deploy necessary skepticism and will download anything. Be particularly careful about torrent sites that require you to install a downloader utility before it will allow you to get access to files.
Never download files that do not have recognizable file extensions
Executable programs don’t only end in “.exe.”
Avoid compressed files that require a specific unzipper in order to get access
Even standard zip files that your operating system already knows how to access can hide programs. If you look into a downloaded zip file and see file extensions that you don’t recognize, delete the whole zip file and look for another source.
Be wary of app installers
Learn to look a gift horse in the mouth
This is a particularly relevant piece of advice in the case of software because Trojans were named after a trick employed in Ancient Greece. A besieged city discovered a wonderful and enormous wooden statue of a horse outside their gates one morning and took it inside to admire it. During the night, enemy soldiers hidden inside the structure slipped out and murdered all the townsfolk in their beds. This was the Trojan horse, and Trojan malware copies its success.
You may see a useful utility that is available for free. You download the file, open the installer and then click through the install wizard until you have that app ready to use. The app may be a genuinely useful tool and it may work very well. However, the automatic install process could also have slipped a Trojan onto your computer that will invite in botnet programs without your knowledge.
Some genuine software producers also use this method to get irritating toolbars onto your computer,modify your settings to show adverts in your browser, and alter your default search engine.
These install wizards will often ask you whether you want to make these changes or install the extra software. Many people just click through these install screens and so actually agree to have pesky extras, spyware, and malware installed.
Make sure you only install apps from the website of the software producers
Check out reviews of the program before you install to make sure that it isn’t a scam or a Trojan before you hit the download button.
Ebook downloads can contain infected PDFs
You may visit a site that has a lot of information and see an offer of a free ebook that will enable you to read up on a complicated topic offline on your daily commute. This is a common marketing tool and is designed as an incentive for you to give your contact details. However, be careful about downloading PDFs.
The structure of a PDF can hide programs
This is particularly risky if your system is set up to open PDFs in your browser. Close down that option for starters. Also, make sure that you disable JavaScript in your PDF viewer.
Before you download an ebook, make sure that you don’t have to download a special reader program
Be suspicious of files that require non-standard readers from the same site in order to open them. Avoid zipped files that require a proprietary decompression utility.
Check online for information about the website that the PDF comes from and see whether anyone else has reported problems after downloading the file.
Email attachments can contain malware
Don’t download any files attached to speculative emails that come from people who you don’t know
If a friend or colleague sends you an unusual file, speak to that person first before downloading and opening it. The email that contains the attachment might not actually have been sent by that person. It may be the product of a botnet that got into your friend’s email account and sent out the email under their name.
Phishing scams are not the only way that hackers can get your login information for your email account and other online services
A secret program called a “keylogger” can record everything you type in and send your username and password to the hacker’s database without your knowledge. Keyloggers can be installed by Trojan programs masquerading as email attachments.
Attack of the Things
Pretty much any consumer product with the word “smart” in front of its name has a computer chip in it and can connect to the internet. Smart equipment can communicate with the manufacturing company for updates to firmware and performance monitoring. These internet-activated products include TVs, fridges, electricity meters, security cameras, and even cars.
Plug ‘n Play equipment includes printers, routers, games consoles, set-top boxes, watches, toys, drones, and kitchen equipment. These devices operate network discovery procedures the first time you turn them on. They will detect nearby compatible equipment and configure themselves appropriately.
Any product that can be updated over the internet or can communicate with other devices in your home via your wifi router is part of what is known as the “Internet of Things.” IoT devices can be hacked.
The Mirai botnet that attacked Sony in 2016 wasn’t made up of zombie computers, it was made up of smart devices — particularly security cameras and DVR players. An Incapsula analysis of one Mirai attack revealed that less than 50,000 devices participated, and yet this botnet and its imitators could cause global damage to the web.
Sloppy procedures implemented by the creators of these products made hacker access possible. Often, manufacturers use the same default account name and password for these gadgets to make their maintenance access easier. Once hackers discover the password for one piece of equipment, every copy of that model can be accessed all over the world, creating a very large and easily-directed botnet.
Wifi routers ship with a standard admin account, which buyers seldom alter. You can protect your router from being hijacked by hackers by navigating to the user account section on your router and changing the password. If the router is not fresh out of the box, it may already be infected with malware. Restore it to its factory settings to wipe out all software modifications before you change the administrator password and connect devices.
The firmware on smart devices is much more difficult to protect because it is often inaccessible and doesn’t have an admin console. Manufacturers don’t always want you to change the access credentials to these gadgets because they don’t have procedures within their maintenance contact routines to account for user-initiated privacy. In these cases, you have to rely on the manufacturer being smart enough to create access credentials that can’t be hacked. If you don’t have the confidence that your potential purchase can be immunized, browse other models. The manufacturers of shunned products will either get with the plan or go out of business.
If all else fails, try out Trend Micro’s IoT version of its HouseCall anti-malware utility. This is free to use, so you won’t be wasting your money. The realm of IoT is new to cybersecurity. You should expect, over time, more anti-botnet utilities will be produced to help protect your internet-connected and discovery-enabled home appliances and gadgets.
Cryptocurrency botnets
Cryptocurrencies are a hot investment topic at the moment. By the beginning of 2018 there were 1,384 different cryptocurrencies in existence. You can buy a cryptocurrency, but a neat way to make money out of the system is to mine. Cryptocurrencies rely on a formula called “blockchain.” This algorithm allows for the expansion of the virtual money supply and currency mining machines perform that task.
You can make money mining currencies, but the computers that you need to create them cost a lot to buy and they burn a lot of electricity. It takes a long time for your investment to start paying off.
Botnet herders have a better solution that considerably shortens the payback period of cryptocurrency mining equipment — they use other people’s resources instead of buying their own.
Not all cryptocurrencies can be mined by a botnet. However, the Monero digital currency is ideally suited for botnet activity. In January 2018, it was discovered that Smominru had enslaved 526,000 zombie computers and used their processing capacity to generate $3.6 million worth of Monero.
Ordinarily the owners of botnet zombies experience little performance impairment. However, the heavy processing required for cryptocurrency mining would be noticeable. Smominru is just the latest in a string of cryptocurrency mining botnets. Given that the cost of running mining computers has reached the point where the profitability of the pursuit is eroded, you can expect this scam to become a much larger hacking activity.
Conclusion
The good news emerging from the hacker world is that zombie computers are becoming a thing of the past. The bad news is that mobile devices are currently big targets and your home appliances are now more likely to become enslaved into a botnet.
Protecting all of your internet-enabled devices is important. Although you might be more interested in protecting yourself from attack rather than removing your equipment from a botnet, both of these activities are two aspects of the same issue. If everyone in the world made their computers, smart electronics, and mobile devices less vulnerable to remote control, you would be less likely to be attacked.
The ease with which botnets can be assembled creates an over-supplied market that forces hackers to explore new marketing strategies and cut prices. This results in DDoS attacks becoming more accessible, and therefore more prevalent. If acquiring zombies gets harder and the income generated by botnets reduces to the point where hacker effort is not sufficiently rewarded, then DDoS attacks will become less frequent.
If you want to maintain open access to your favorite websites and guard against being booted out of an online game at a critical moment, you need to take action to be part of the solution. Who knows, the next time you lose access to the internet, it could well be that you just got attacked by your own fridge.