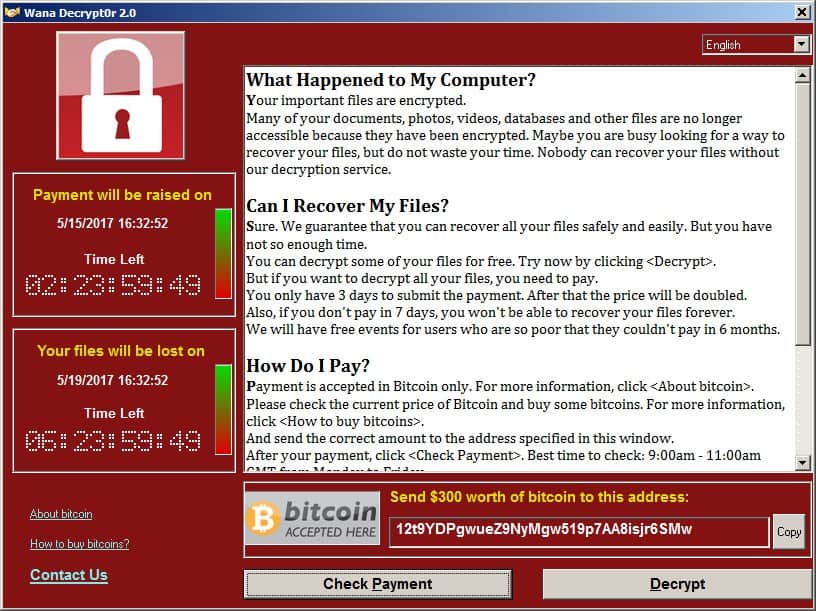
In May of 2017, Windows computers around the world began to lock themselves with a bright red screen that would later become immediately recognizable to security researchers. The now-unusable systems demanded Bitcoin in exchange for regaining access: the defining feature of a particular type of virus known as ransomware. So why does this matter, and why are we still talking about it today?
Well, what was particularly unusual was the speed with which this infection spread. In under 24 hours, it had compromised more than 75,000 computers around the world, and significantly undermined the operations of multi-million dollar organizations including FedEx, Renault, Telefonica, as well as critical parts of some countries’ infrastructure, such as the UK’s National Health Service. Simply, the scale of this attack was unprecedented and even now, WannaCry infections continue to be extremely common.
What is WannaCry?
In simple terms, WannaCry (also known as WannaCrypt, WCry, and WDecryptor) is ransomware: it locks your PC and only grants access after you’ve paid the attackers (usually around $300–600 in Bitcoin).
However, this software is extremely complex. It spreads itself using two exploits developed by the NSA, a backdoor implant tool named DoublePulsar, and a Windows exploit known as EternalBlue. Essentially, DoublePulsar allows hackers to run WannaCry on remote machines, and the EternalBlue exploit allows this ransomware to spread to other devices on the network.
There were three reasons that this approach was so effective. First, there was no easy way to tell if you were already infected by the DoublePulsar backdoor. Second, network security usually focuses on preventing outside attacks, not malware spreading internally. Finally, Windows had only patched the vulnerability that EternalBlue exploited a month earlier. In other words, unless your system was set to update automatically, you were likely still vulnerable.
How was WannaCry’s spread stopped in 2017?
The 2017 WannaCry ransomware campaign was stopped almost by a total fluke. Two security researchers, Marcus Hutchens and Jamie Hankins, discovered a web address in WannaCry’s code and, realizing that it was unregistered, quickly claimed it. This acted as a kill switch, shutting off the stream of malicious traffic and effectively preventing the ransomware from spreading even further.
Of course, this wasn’t the end. According to TechCrunch, the pair quickly found the situation spinning out of control, with both botnets and law enforcement trying to take the website offline (to resume and stop the attacks, respectively). Even now, if the site goes offline, the attack will start up again. Luckily, Cloudflare now hosts the site. As one of the biggest web infrastructure companies in the world, the worst case scenario is now extremely unlikely (though not impossible).
Who was behind the 2017 WannaCry attacks?
In September 2018, following a lengthy investigation, the US Department of Justice charged a programmer from North Korea named Park Jin Hyok with a spate of cybercrimes dating back to 2014. Notably, the indictment alleged he was part of a state-sponsored hacking collective named the Lazarus Group. The North Korean government, for their part, claims that this individual “does not exist.” The effort to identify the rest of the people involved with this particular WannaCry campaign is ongoing.
Is WannaCry still a threat?
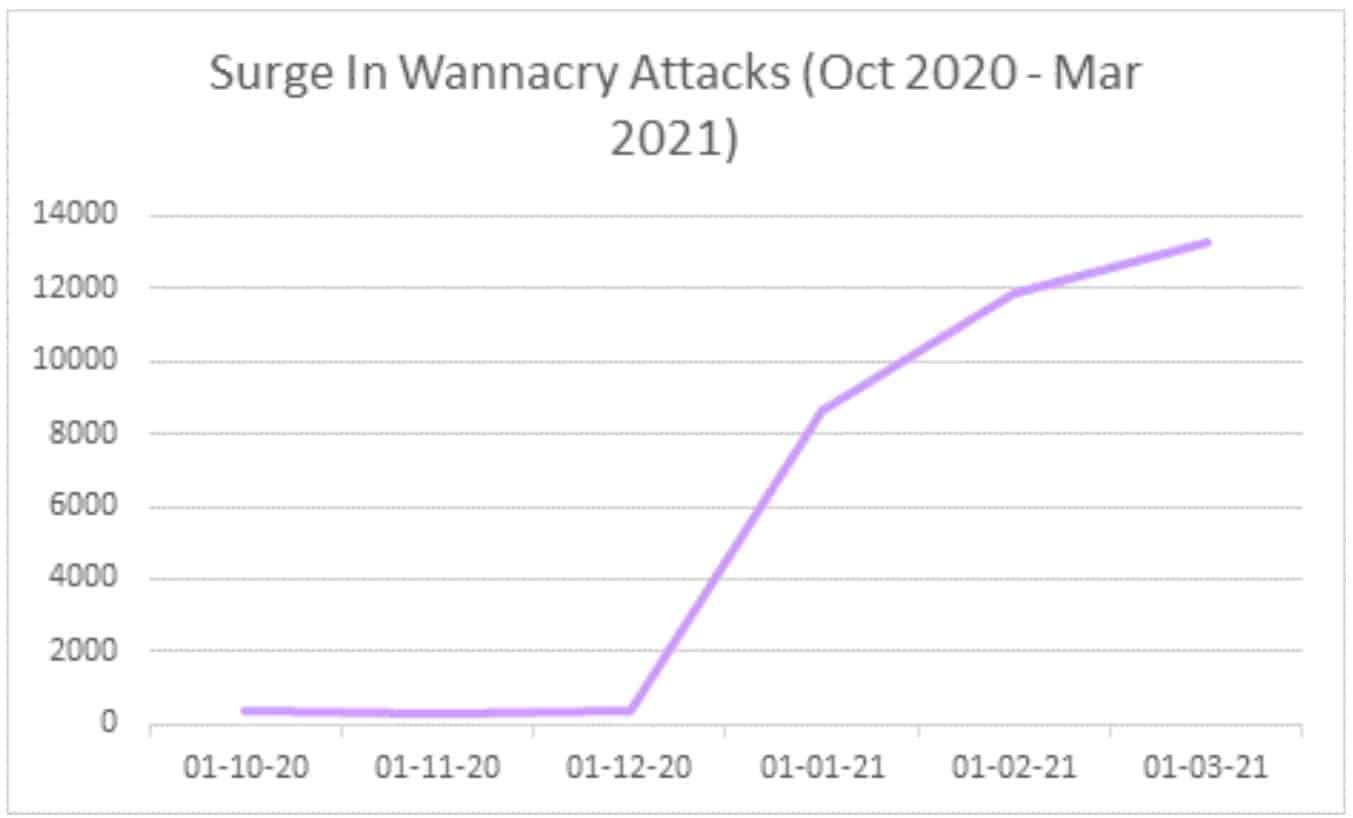
Absolutely. Although WannaCry attacks had remained fairly stable, there was a 53% surge in reported incidents between October 2020 and March 2021, bringing the number of impacted organizations to around 13,000. This represents a more than 4000% increase year on year, despite the fact that the patch preventing WannaCry has been out since 2017.
Does WannaCrypt affect Mac or Linux systems?
WannaCry relies on a vulnerability in Windows’ Server Message Block (SMB) protocol. Other operating systems like MacOS and Linux don’t use this technology, and as such, are not vulnerable to WannaCry ransomware.
What should I do if my PC is infected by WannaCry?
The general consensus between organizations including the NCSC, the FBI, and ACSC is that you should not pay the ransom. The entire threat is that you’ll lose access to your files, but there’s actually no guarantee that the malware will go away once you pay, and doing so could mark you as a lucrative victim for additional attacks in the future.
Instead, the first thing you should do is disconnect your device from the network by removing all Ethernet cables and wireless dongles. The next step is to consult with your organization’s tech team and see if there’s any hope of decrypting your files using the WannaKey or WanaKiwi tools. Note that these tools will only work if you haven’t rebooted the system yet.
Unfortunately, if you’re an individual and not a large organization, your best bet is to simply format your computer and start over or try using something like Norton’s Bootable Recovery Tool (though this won’t give you access to any encrypted files, even if it works).
How to prevent WannaCry attacks
The simplest, most obvious course of action is to install Microsoft’s security patch. However, there are a variety of different updates based on which version of Windows you’re using. Luckily, Malwarebytes has assembled a complete list for each affected operating system, making it quick and easy to see which one you should be applying.
Windows doesn’t normally update its older versions, but the scale of the WannaCry problem was so large that there wasn’t really an alternative. There’s no guarantee it will do the same the next time a major vulnerability is found, though. As such, we recommend upgrading to a more modern operating system as soon as possible.
You may have read that anyone using Windows Vista, Windows 8, Windows 10, or a modern Windows Server release is not vulnerable to WannaCry. This is true, but only if you have automatic updates turned on. Otherwise, you’ll have to manually tell your system to install the latest security updates. To do this, just press the Windows key, type “Update”, and hit Enter. Now, click on Check for updates and install any that appear.
Finally, you should turn on Windows Defender if it isn’t already active or install a reputable antivirus program. This will help keep malicious scripts from running in the first place, preventing the initial DoublePulsar infection entirely.
How to Protect a Network from Ransomware
When it comes to protecting your network you may want consider tools that can defend against attacks at the endpoint level.
CrowdStrike Falcon Prevent
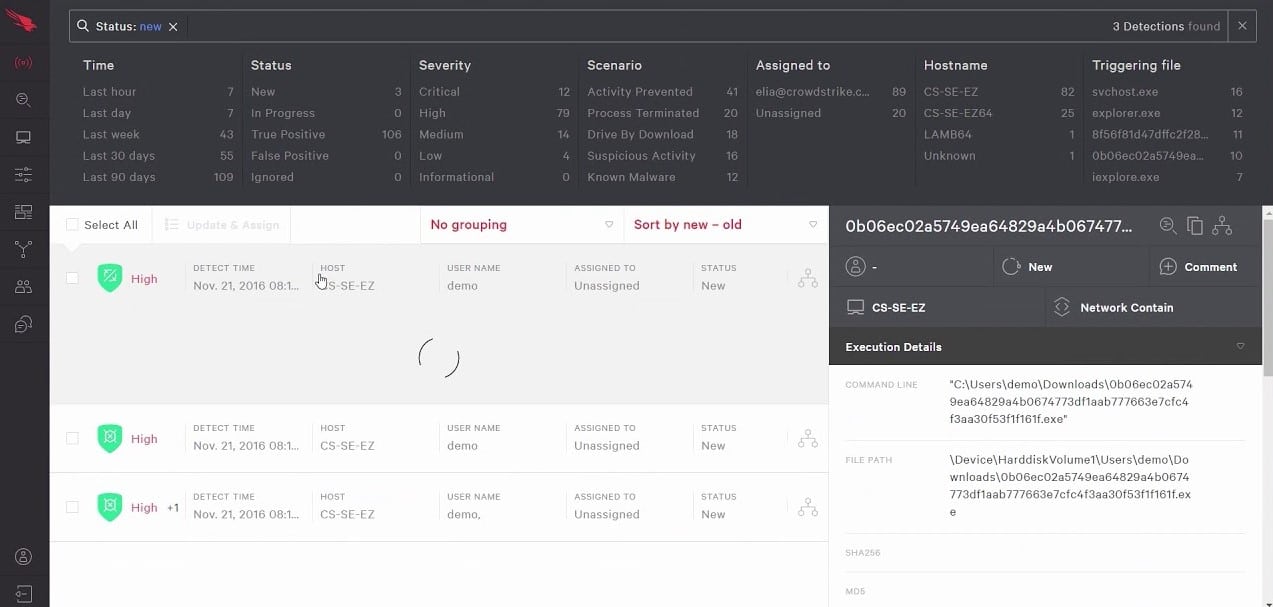
Anti-virus systems block a variety of malware, including ransomware. However, traditional AVs rely on a signature database that is defined by a central research team and then distributed to all implementations of the software package. This strategy means that many of the users will be hit by the malware before a solution is provided. This is a Russian Roulette solution that businesses can’t afford to risk when it comes to ransomware like WannaCry.
CrowdStrike Falcon Prevent provides a better solution because it is a next-generation AV. It uses anomaly detection instead of a signature-based approach. With this strategy, rather than relying on a list of files to look out for, the Falcon Prevent system establishes a baseline of normal activity on the endpoint and then looks for unusual behavior.
As soon as the Falcon Prevent system spots suspicious activity, it kills the processes involved and isolates the programs that ran them so that they can’t run again or trigger defense mechanisms. This means that you don’t have to wait for other businesses to get attacked by the ransomware before a solution is defined.
Falcon Prevent is just one of the modules that make up the Falcon platform — itself available in several tiers of plan. Just some of the other modules included with the basic Falcon Go platform include identity protection, USB device control, firewall management, and threat intelligence. You can assess the Falcon platform with a 15-day free trial.
Image used: 황승환, CC BY-SA 4.0 <https://creativecommons.org/licenses/by-sa/4.0>, via Wikimedia Commons