A visa assistance website for travelers to India exposed more than 6,500 international visa applications on the web, according to Comparitech researchers.
The applications, which included scanned passports and photos, could be accessed by anyone through a simple Google search.
Travelers from the USA, Canada, UK, Sweden, Russia, Australia, and many other countries are affected.
Comparitech researchers led by cybersecurity expert Bob Diachenko discovered the unsecured data on April 27, 2021. As per our responsible disclosure policy, he immediately attempted to notify the website administrator so the data could be secured, but the company has not responded despite numerous attempts.
Because the data is still exposed and at risk, we have elected not to share the name or URL of the vulnerable site and continue our efforts to get this taken down.
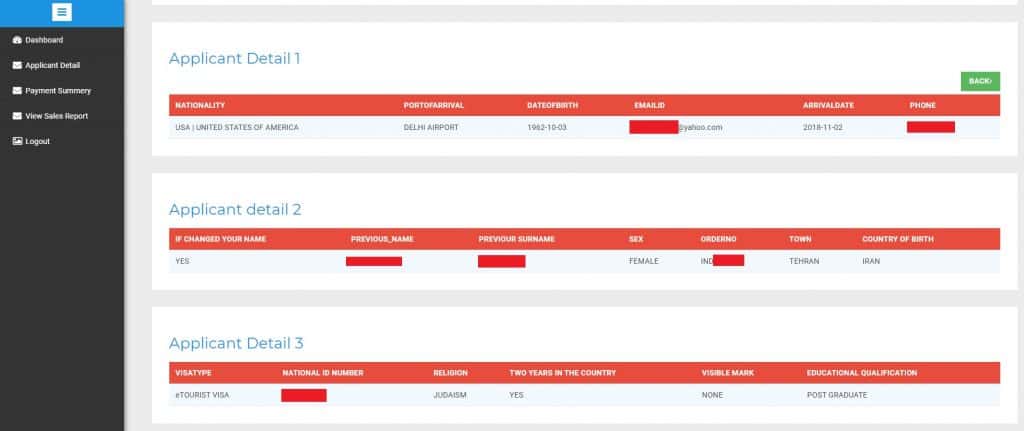
The website stores applications on its web server, which can be accessed through a public URL leading to a dashboard. The URL has a numbered variable at the end indicating the index of the application in the database. These indices are sequential, which means anyone can easily access visa applications by incrementing the number at the end of the URL by one.
This allowed Diachenko, and would allow any would-be attackers, to browse through applicant details. In total, 6,516 visa applications were exposed.
What can consumers do?
We’re reporting this incident because there is something consumers can do right now:
If you have applied for India’s electronic visa through a visa assistance website in the last three years, we recommend you perform a Google search for your name and passport number.
If you find your information has been exposed, you can then request Google to remove your personal data from search results using this link (non-EU citizens) or this link (EU citizens).
Timeline of the exposure
We do not know how long the data was exposed for before we came across it, but Google Search timestamps go back to 2018. Given how long the data was likely exposed for, applicants should assume the worst: their data may already in the hands of cybercriminals.
On April 27, 2021, Diachenko discovered the exposed data and immediately sent an email notification to the site owner. In the following days, Comparitech made repeated attempts to contact the company by phone and email, but did not receive a response.
The data is still exposed and we have received no communication from the agency as of time of publishing.
What data was exposed?
The visa applications were stored on a server in the Netherlands. They included a wealth of information about international travelers to India, including some or all of the following:
- Passport scan
- Passport-style headshot photo
- Name
- Age
- Email address
- Phone number
- Sex
- National ID number, including SSN or SIN
- Religion
- Education
- Type of visa applied for
- Place of birth
- Nationality
- Mailing address
- Billing address
- Payment status
- Marital status
- Occupation
- Immigration status
- Previous travel to India
- Applicant references including names, phone numbers, and addresses
- Port of arrival
- Arrival date
- Passport number
No credit card numbers or other payment information was included.
Dangers of exposed data
The information and images exposed in this incident pose a number of threats to visa applicants.
Fraudsters could use the information for identity theft. Particularly if a Social Security Number or some other national ID number is included, they could open bank accounts, take out loans, apply for visas, or get government benefits in the victim’s name.
Passport scans and photos are sometimes necessary to open online bank accounts. Many online banking services offer a signup reward for new customers. In a bank drop scam, criminals can open accounts in the victim’s name, collect the reward, then abandon the account.
Cybercriminals could also use the images to bypass logging into the victim’s accounts. Some websites allow users to reset lost passwords by submitting proof of identity. By posing as the victim and claiming they’ve lost their login credentials, criminals can hand over the passport scan to “prove” their identity and hijack accounts.
Victims should also be on the lookout for targeted phishing. Scammers can post as immigration authorities or a related organization and use the leaked information to tailor convincing messages. These messages may come over SMS or email, and they typically try to trick victims into clicking on a malicious link. That link either downloads malware or directs the victim to a fake site where they enter a password or payment information.
About the visa assistance company
The website offers visa application assistance to customers for a fee. Although applicants can apply directly through government websites, visa agencies often make the process more convenient by assisting with paperwork and going to an embassy or consulate on the applicant’s behalf. This service seems mainly focused on electronic visas rather than traditional printed ones.
Applicants can apply electronically and submit the necessary documents by uploading scans of passports, photos, and other ID to the website.
Why we reported on this data incident
Comparitech researchers routinely scan the web for vulnerable databases containing personal information. When we find exposed data, we immediately begin an investigation to determine the owner, what information is at risk, who is affected, and potential impact on people whose data was exposed.
Once we identify who is responsible for the data, we promptly alert the owner according to our responsible disclosure policy so the data can be secured as quickly as possible. In this instance, the company did not respond and the data is still vulnerable as of time of publishing, so we have elected not to share details about the company or website in order to protect end users.
By publishing reports like this one, we hope to raise awareness and curb harm to end users.
Previous data incident reports
Comparitech has published several data incident reports like this one:
- Utah COVID-19 testing service exposes 50,000 patients’ photo IDs, personal info
- Car dealer marketing service Friendemic exposes 2.7 million consumer records
- Gym chain Town Sports exposes 600,000 records of members and staff
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- UFO VPN exposes millions of logs including user passwords
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database
- Over 2.5 million CenturyLink customer records leaked