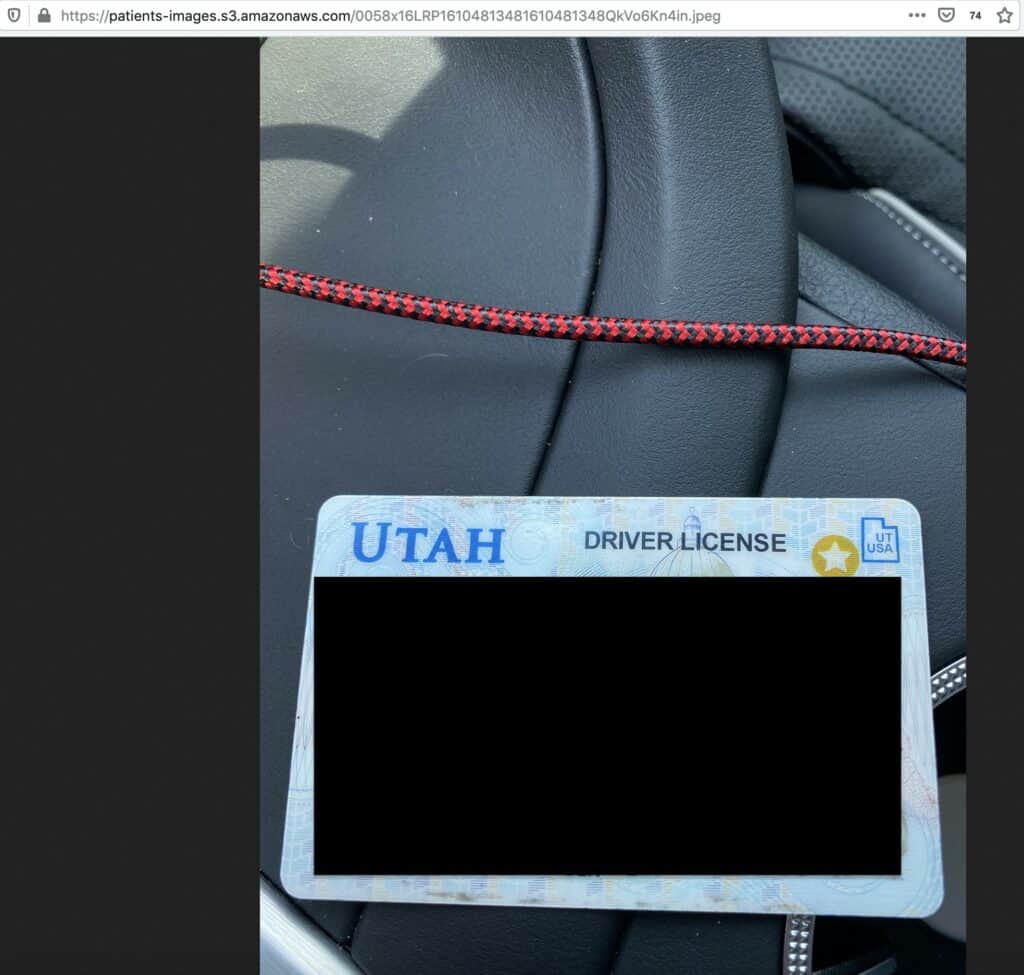
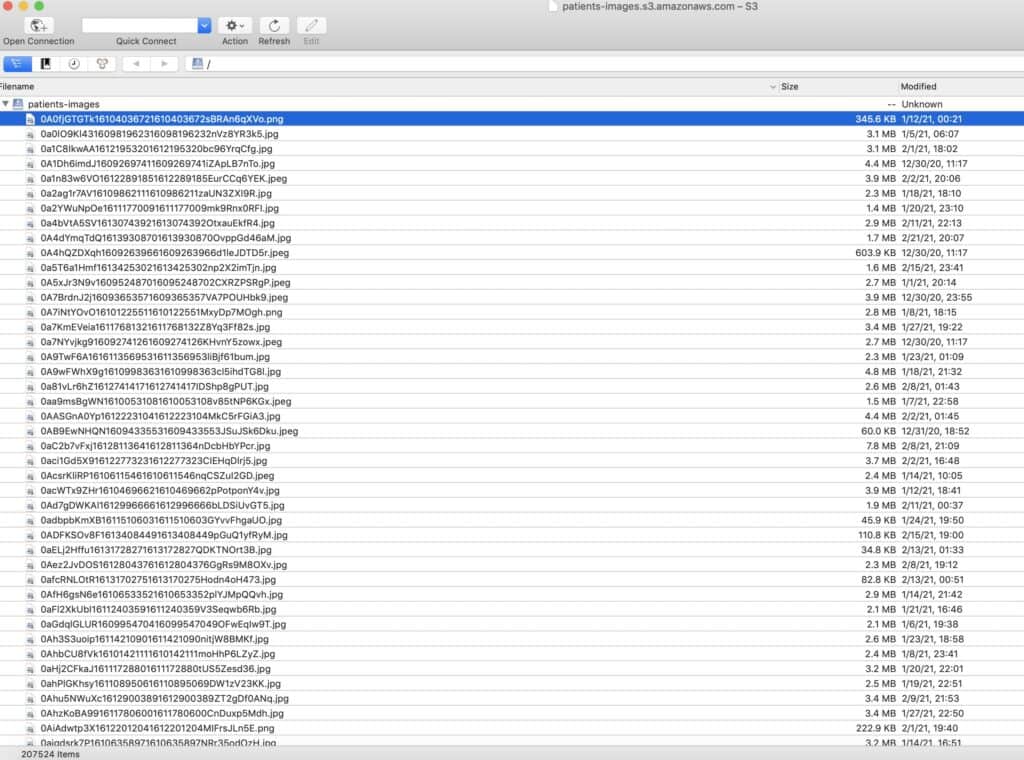
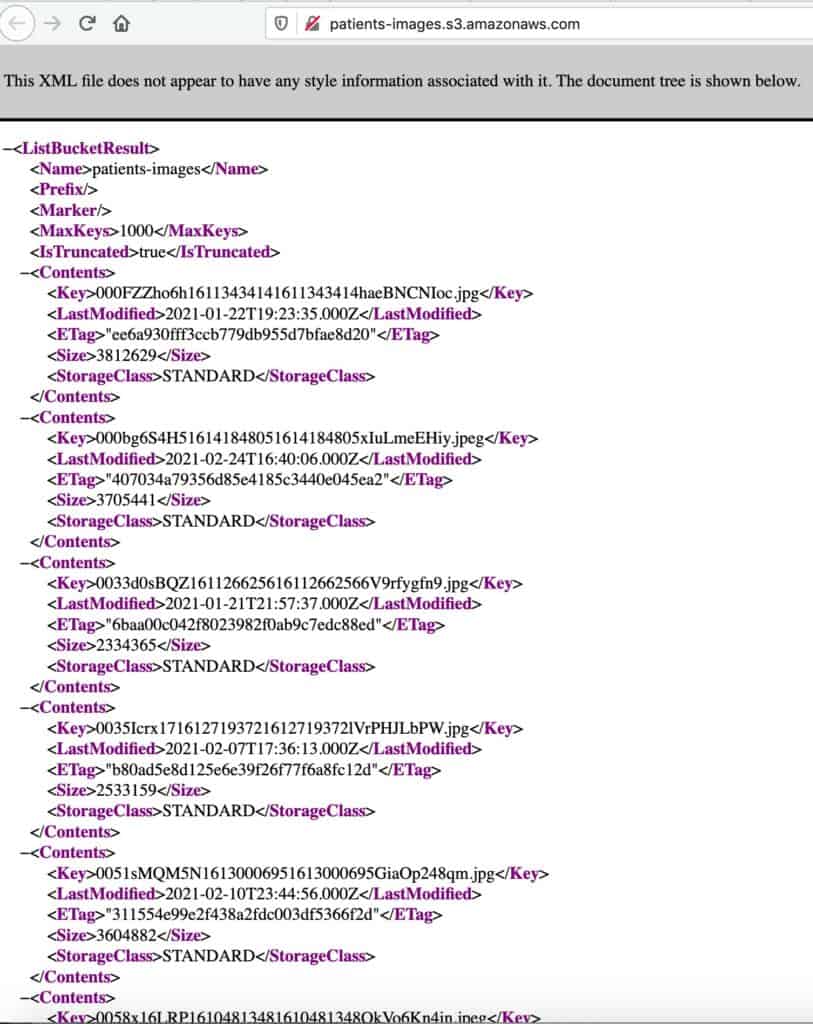
Utah-based COVID-19 testing service Premier Diagnostics has exposed thousands of ID scans, including driver’s licenses, medical insurance cards, passports, and other IDs, on the web without a password or any other authentication required to access it, according to Comparitech researchers.
Comparitech cybersecurity expert Bob Diachenko discovered the publicly accessible data on February 22, 2021. Affected persons are mostly from Utah, Nevada, and Colorado, based on samples of the data obtained by Comparitech. In total, over 200,000 images of ID scans were exposed.
After initial difficulties in identifying and contacting the owner of the data, Premier Diagnostics acknowledged the incident and secured the data on March 1, 2021.
Timeline of the exposure
We do not know how long the data was publicly accessible for prior to Comparitech’s discovery of it. Here’s what we know happened:
- January 25, 2021 – The first of the two databases was indexed by a search engine.
- February 22, 2021 – Diachenko discovered the exposed data and began his investigation to identify the owner
- February 24, 2021 – Unable to identify the owner, Diachenko sent an alert to the Amazon Web Services security team. He received a response that the owner would be informed via internal channels.
- February 25, 2021 – After further examination of exposed data, Diachenko identified Premier Diagnostics as the likely owner, and sent a disclosure accordingly.
- March 1, 2021 – After several days with no response, Comparitech’s editorial team was able to make contact with Premier Diagnostics. The data was secured later in the day.
- March 5, 2021 – Premier Diagnostics requested additional time for security experts to review their infrastructure.
In total, the data was exposed for at least a week, if not longer. We do not know if any unauthorized parties accessed the data in that time. Our research shows it takes just a few hours for attackers to find and steal publicly exposed data.
What data was exposed?
The exposed data was stored in two large Amazon S3 buckets. One bucket named patient-images contained 207,524 images of patients’ photo ID scans:
- Driver’s licenses
- Medical insurance cards
- Passports
- Other forms of ID
Premier Diagnostics tells Comparitech that each patient is associated with four images: the front and back of a medical insurance card, and the front and back of a second ID such as a driver’s license or passport. That means roughly 52,000 patients are affected.
These forms of identification contain detailed personal information about their owners, including name, age, address, photo, gender, ID numbers, and more.
A second bucket called paper-records contained a database of names, dates of birth, and test sample IDs from patients who underwent COVID-19 tests. Each of the 3,645 items in the bucket is a scanned table with dozens of patients.
Correction: An earlier version of this article stated the data contained COVID-19 test results. It did not.
Dangers of exposed data
Patients whose data was exposed could be at risk of health insurance fraud, identity theft, and phishing.
Medical insurance cards can be used by fraudsters to obtain prescription medication in the victim’s name.
ID scans and the information therein could be used for identity theft, though we didn’t find any payment data or Social Security numbers. Still, cryptocurrency exchanges and online financial services often require ID scans to set up accounts. An attacker could use the ID scans to set up an account in someone else’s name, then collect the signup bonus or use the account as a mule.
ID scans can also be used by attackers to bypass two-factor authentication measures. If you are unable to log into an account armed with two-factor authentication, the service in question might require you to submit an ID scan to prove your identity and access your account. Attackers can use an ID scan to pose as the victim and bypass login security.
Lastly, victims should be on the lookout for targeted phishing and scam messages. Scammers posing as Premier Diagnostics or a related company will message victims by SMS or email, using personal details from the exposed data to make their messages more convincing. Do not click on links or attachments in unsolicited emails and always verify the sender’s identity before responding.
About Premier Diagnostics
Premier Diagnostics provides COVID-19 testing for individual patients, clinics, schools, and businesses, according to its website. It was established at the beginning of the COVID-19 pandemic and primarily serves residents of Utah.
PremierDX operates drive-through testing facilities and has tested “hundreds of thousands of patients.” Its available tests include saliva-based RT-PCR tests, rapid antigen tests, and antibody tests.
Why we reported this data incident
Comparitech researchers regularly scan the internet for unsecured databases containing private and personal information. When we come across unprotected data, we immediately launch an investigation to find out who is the owner, what information is at risk, who is affected, and the potential impact on data subjects.
Once we’ve identified whomever is responsible for an exposed database, we immediately alert the owner so the data can be secured as fast as possible, according to our responsible disclosure policy.
After the data has been secured and our investigation completed, we publish an article like this one to raise awareness about the exposure.
Previous data incident reports
Comparitech has discovered and reported on several data incidents like this one, including:
- Car dealer marketing service Friendemic exposes 2.7 million consumer records
- Gym chain Town Sports exposes 600,000 records of members and staff
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- UFO VPN exposes millions of logs including user passwords
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database
- Over 2.5 million CenturyLink customer records leaked