Warning: This article contains profanity and depicts a crime that is sexual in nature.

“He begins by telling me he doesn’t want any drama or tears. Of course I was distraught at first but then I calmed myself and asked him what he wanted. He told me he knows the kind of person I am. He has seen all my photographs, read all my iMessages and WhatsApp chats. Seen x-rated photographs. He has access to a lot of my information that I would not want to be shared. He lectures me about how I’m a bad girl, that I have smoked weed and had sex. That if my parents knew what he did, they would be happy […] to know that their daughter is being punished for her ‘misdeeds’.”
This is the story of reddit user Zedevile, who spoke to Comparitech on condition of anonymity. She is a victim of spear phishing. Despite the disturbing and private nature of her encounter, Zedevile–Zed, for short–wrote about her episode with the criminal who blackmailed her, and posted the story on reddit. She says her intention is to reach as many people as possible so that what happened to her doesn’t repeat itself.
“He said I was a slut because of the number of relationships I have been in/people I have dated since I have had that phone. I asked him if he wanted money, anything of the sort. He said he could buy me with money, so I should drop that. So I asked him what he wanted from me.”
“He asked me to take my clothes off and touch myself in front of him on FaceTime. Satisfy him. Only then would he give my accounts back.”
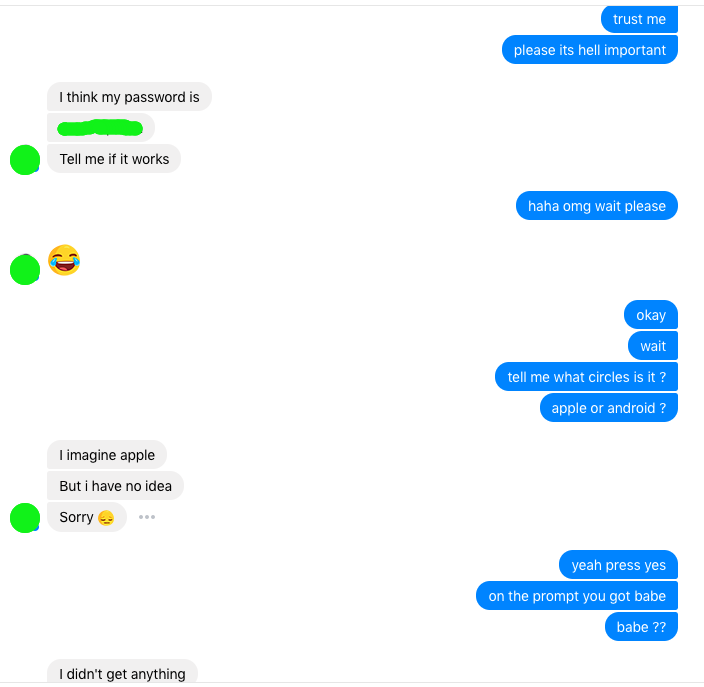
It began when a hacker posing as a familiar acquaintance contacted Zed on Facebook, asking her to vote in a modeling competition online. She handed over her Apple and Google IDs to be added to a group. Then things went sour. A bug in the system has somehow prevented Zed’s friend from adding anyone else to the group. She needed to remove Zed from the group to fix it, and to do that, a password was necessary.
“Her career was at stake for goodness sake, she begged. After going back and forth for a bit.. I fucked up. I trusted her. I thought there was no harm and I would just change the password right after. It was the password to a Gmail ID I never use anyway, except for signing up on random websites where I don’t want to get their spam mail but need to create an account, you know how we all have one of those.”
The moment Zed disclosed her password, the attack was a success.
Spear phishing
Phishing uses behavioral psychology to trick victims into trusting the attacker in order to obtain sensitive information. Anyone who regularly uses the internet has probably encountered phishing attempts. They appear as dodgy links in fake emails, forged financial websites that ask for login details, and suspicious phone calls from banks and hospitals to senior citizens. The bulk of phishing attempts target a massive audience–often thousands of people–and hope that a small handful will be tricked.
Spear phishing is less prevalent, but far more dangerous. Spear phishing targets an individual or small group of people. The attacker can gather personal information about their target to build a more believable persona. 95 percent of all successful attacks on enterprise networks are the result of spear phishing, according to a SANS Institute researcher. 91 percent of respondents in a Cloudmark survey said that they have experienced spear phishing attacks.
Spear phishers typically target high level executives and IT admin in charge of protecting sensitive databases. Cybercriminals spoof company email accounts to impersonate executives and trick employees in accounting or HR into wiring money or sending out confidential information. But Zed’s story shows how it can happen to anyone.
Comparitech reviewed multiple screenshots of Zed’s conversation with the hacker as well as several forwarded email threads of her conversations with customer support at Microsoft, Instagram, and Facebook to verify her story. We also also called one Microsoft customer advocate at the company’s Global Escalation Services at his personal number, supplied by Zed, to verify his identity.
The email password that Zed handed over to the imposter was not just a junk mail account. It was also the recovery email for her primary email account on Hotmail. Shortly after the exchange, she received emails about a sign in from Pakistan. Within minutes, the attacker signed her out of several accounts.
“Every account I have on the internet if it is important is linked to Hotmail. Bank accounts, Facebook, LinkedIn, Squarespace, Amazon, you name it. He changed the Hotmail password, recovery email and phone. My Hotmail was also my Apple ID.”
Once the attacker had gained control of Zed’s Hotmail account, he had everything.
He changed her recovery phone number, email, birthday, and security questions for her Apple ID. Zed did not have two-step verification enabled, which requires a secondary form of verification typically via text message when logging in from a new device, set up on her accounts.
“I wasn’t able to verify my identity because my answers were incorrect, the lady on the phone couldn’t let me in.”
The attacker took control of Zed’s Facebook account. Using her boyfriend as a proxy, Zed set up a call on Facebook Messenger with him. That’s when the blackmail began. The attacker wasn’t interested in money.
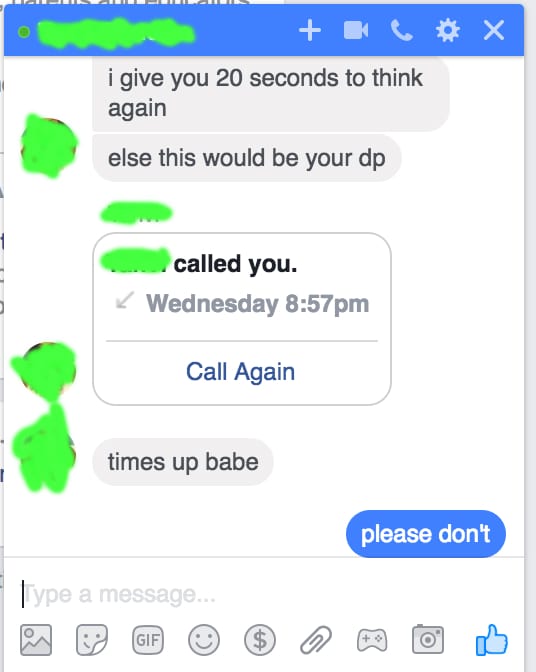
He told her that if she didn’t give in to his request, he would post compromising photographs from her iCloud on Facebook as her profile picture. He said he didn’t care if she reported him to law enforcement.
Zed refused.
“[…] I began to get upset during this call, and telling him he had no right to morally police me and that I could be in as many relationships as I want and sleep with whomever I want and it is none of his business. This made him angry. He said, ‘check your [display picture] in two minutes’.”
The attacker followed through on his threat. He posted the photo. Zed’s boyfriend had amassed a team of friends to monitor her account and flag the photo on Facebook as soon as it appeared.
“I was in tears. Within a couple of minutes, a random friend whom I hardly speak to called my phone and asked me if I knew what was on my Facebook. She heard me crying and I said I couldn’t talk. My friends were reporting, reporting, reporting. I saw my profile change. It was fucked up.”
Her profile was deactivated in less than 10 minutes, but it was enough to do some damage.
“I think at least 15 people must have seen it. At least 5-7 reached out to me immediately, through some method or the other.”
Recovery
Zed spent the next month piecing her online life back together.
The attacker had used her Facebook account to message 20 to 25 of Zed’s female friends on Facebook. He successfully tricked one of them, who also lost everything. “He actually called her by phone, but her boyfriend spoke to him and they had some sort of shouting match, at the end of which he seemed to give up,” Zed says.
The police told Zed that there was little they could do. The criminal was supposedly in Pakistan and her case “wasn’t important enough for a cyber crime investigation.”
Zed notes that Apple, Facebook, Instagram, and Google all had reasonable and responsive customer service to help her recover her accounts. Microsoft–which owns Hotmail–and Snapchat had “terrible” support, and she was unable to recover those accounts.
Zed’s story not only highlights that spear phishing can target anyone, but that it is probably more common than most people realize. Zed was courageous not only because she did not give in, but because she chose to share her story on reddit and with Comparitech as a cautionary tale to others. She is an exception to the norm, though. It’s very likely that these sorts of personal attacks often go unreported, both to law enforcement and to the media.
How to protect yourself
Zed wraps up her reddit post with a simple piece of solid advice: “Things are better now, but remember kids: DO NOT EVER give your personal info away, even to a close friend or loved one.”
Passwords
Passwords, especially, need to be closely guarded. If you insist on sharing an account with someone, such as a family Netflix account, enter the password yourself on their behalf. Don’t write them down on your computer, smartphone, or even a notebook. Don’t tell someone your password over the phone or in a text message. These mediums are often not encrypted and you never really know who is on the receiving end.
Passwords also need to be strong and varied. Creating a strong password means using a random combination of letters, numbers, and symbols that’s at least 12 characters long. You can read more about how to build strong passwords here.
Never use the same password for multiple accounts. If you have trouble remembering your passwords, use a password manager. Password managers encrypt and store all your passwords in an app or browser extension so you only need to memorize one master password to access all of your accounts.
“I have been looking into a password manager like Keepass or LastPass since they were recommended by other Redditors on the thread, but I haven’t yet installed any,” Zed says. “Still want to do some research before going into that.”
Finally, change your passwords when appropriate. Older security guidelines suggested changing passwords every 30 to 180 days based on how long it took to brute force a password–to guess every possible combination of characters–but the best advice now is to change them any time a data breach has affected a company with which you have an account. Again, password managers can come in handy here. Some not only help you store passwords, but can also generate random unique passwords on your behalf.
2FA and 2SV
Always enable two-factor authentication (2FA) and/or two-step verification on your accounts when possible. These security measures require anyone logging into one of your accounts from a new or unfamiliar device to verify their identity through some alternative means.
2FA includes technologies like smart cards, Yubikeys, and biometric scans to verify your identity.
A common 2SV example occurs when, after entering your username and password, you must also enter a PIN number or code sent to your device via SMS. Google Authenticator and Authy are trustworthy apps used for 2SV and are a good option if you don’t have a phone number or frequently change numbers.
Email verification is another form of 2SV, but it’s the weakest option. Email verification would not have helped Zed by the time her attacker took control of her email accounts.
“I am using [2FA/2SV] on every account I have that offers it,” Zed says.
Links and malware
Zed’s attacker didn’t infect her devices with malware as far as we know, but tricking users onto imitation sites where they either input private information or are tricked into downloading and installing malware are common tactics. For executives and IT personnel in particular, this is often the criminal’s objective.
Malware can damage computer systems, steal data, and even encrypt entire drives and hold them for ransom. The lattermost, known as “ransomware”, is particularly popular and effective as of late. Organizations can lose access to vital data and are forced to pay huge sums of bitcoin to hackers in return for a password that can decrypt their devices.
It’s important to always be wary of links. Don’t click on links in emails, messages, or web pages that you don’t recognize. Spoofing the addresses where email is sent from or replied to is common. Read more about how to spot phishing emails here.
On desktop browsers, you can hover over a hyperlink to display where it actually leads in the bottom-left corner of the browser window. Be wary of subdomains used to make URLs look legitimate. For example, Paypal’s website is “www.paypal.com”. An imposter website can put “paypal” as its subdomain and an official-looking top level domain so it uses the URL “paypal.official-paypal.com”.
Always use anti-malware with real-time scanning, and keep it up to date.