The personal details of more than 106 million international travelers to Thailand were exposed on the web without a password, Comparitech researchers report. The database included full names, passport numbers, arrival dates, and more.
Bob Diachenko, who leads Comparitech’s cybersecurity research, discovered the database on August 22, 2021 and immediately alerted the Thai authorities, who acknowledged the incident and secured the data the following day.
Diachenko surmises that any foreigner who traveled to Thailand in the last decade might have had their information exposed in the incident. He even confirmed the database contained his own name and entries to Thailand.
Timeline of the exposure
Dates on the records ranged from 2011 to present day. Here’s what we know happened:
- August 20, 2021- The database was indexed by search engine Censys.
- August 22, 2021 – Diachenko discovered the unprotected data and immediately took steps to verify and alert the owner in accordance with our responsible disclosure policy.
- August 23, 2021 – Thai authorities were quick to acknowledg the incident and swiftly secured the data.
Notably, the IP address of the database is still public, but the database itself has been replaced with a honeypot as of the time of writing. Anyone who attempts access at that address now receives the message, “This is honeypot, all access were logged.” [sic]
Thai authorities responded quickly to Diachenko’s disclosure, however we do not know how long the data was exposed prior to being indexed. Our honeypot experiments show attackers can find and access unsecured databases in a matter of hours.
Thai authorities maintain the data was not accessed by any unauthorised parties.
What data was exposed
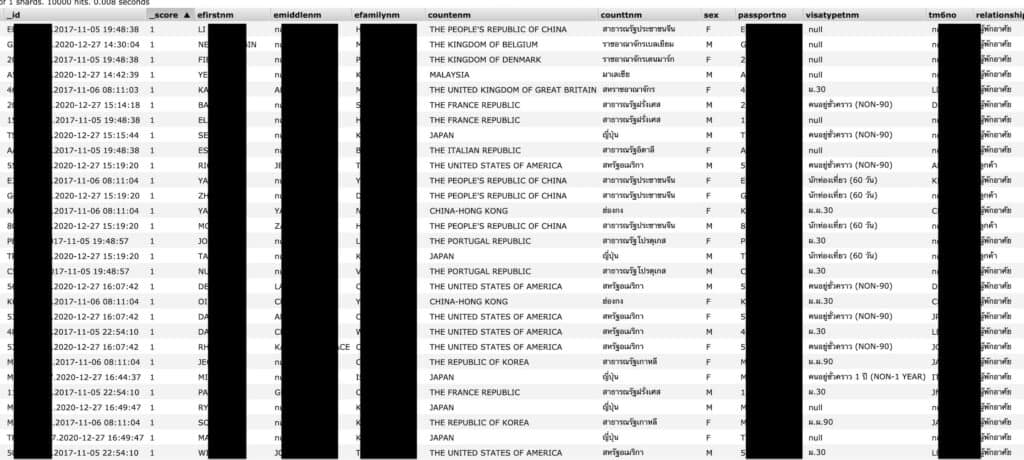
The Elasticsearch database totalled about 200GB and contained several assets, including a collection of more than 106 million records, each of which included some or all of the following info:
- Date of arrival in Thailand
- Full name
- Sex
- Passport number
- Residency status
- Visa type
- Thai arrival card number
Dangers of exposed data
Any foreigner who traveled to Thailand in the last decade or so probably has a record in the database. There are many people who would prefer their travel history and residency status not be publicized, so for them there are obvious privacy issues.
None of the information exposed poses a direct financial threat to the majority of data subjects. No financial or contact information was included.
Although passport numbers are unique to individuals, they are assigned sequentially and are not particularly sensitive. For example, a passport number can’t be used to open bank accounts or travel in another person’s name on its own.
Related: Passports on the dark web: how much is yours worth?
Why we reported data incident
Comparitech’s cybersecurity research team regularly scans the web for unprotected databases containing personal data. When we find such a database, we immediately begin an investigation to find out to whom it belongs, what information it contains, who could be affected, and the potential consequences for data subjects.
Once we identify and verify the owner of the data, we alert them according to our responsible disclosure policy. Once the data has been secured, we publish a report like this one to curb harm to end users and raise cybersecurity awareness.
Previous data incident reports
Comparitech has published many data incident reports like this one, including:
- 35 million US residents’ personal details exposed on the web
- India visa agency exposes 6,500 traveler’s visa applications on the web
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- UFO VPN exposes millions of logs including user passwords
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database

