One of the big scams running the rounds lately doesn’t start with an email. This one usually begins with a phone call. A computer tech claiming to represent a large, reputable firm, like Microsoft, calls their potential victim and tells them that their computer has been identified as having been infected with several viruses.
Alternatively, the user gets a web page that pops up fullscreen, front-and-center, claiming that a virus or even several viruses have been detected on their computer. Both the webpage and the phone call can contain a threat to disable the user’s computer to prevent further spreading of the infection.
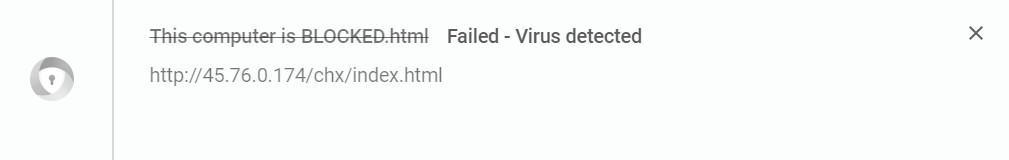
The webpage will not have the option to close it like a normal web browser window, even though it is only a web page. It is possible to close the page, but it takes a bit of tech know-how. This provides a bit of incentive for the unsuspecting victim to call the tech support number on the page.
Common tech support scam tactics
To legitimize their claim, a phone tech may use a few different tactics, which can include directing users to Windows Event Viewer, or claiming a fake customer service agent number.
These fake techs can also use various other technical tools built into Windows to trick their potential victim into believing that their computer is in need of support, or by directing users to install desktop sharing software to gain access to a victims’ computer and plant malicious files on the system.
They may even go so far as to threaten to have the user’s computer disabled so as to prevent the spread of infection.
To prove their point, the fake tech may lead the user through the steps to access the Windows Event Viewer logs, the system monitor, the system’s list of available services or any other technical tool that most users have never seen or even heard of:
- Any errors in the log files will be used to prove that the operating system has been compromised by viruses
- The peaks and valleys of the system’s performance monitor are compared to an ECG of a human having a heart attack
- Any services that are not running are described as infected or disabled due to infection
- Many other technical tools built into the OS can be exploited by a scammer to convince a user that their system is infected
- Even some of the standard features of the operating system can be used to convince a user that there are problems with their computer
The scammer may also walk the victim through steps intended to access the victim’s computer. This can include asking the victim to open a web page to download TeamView or LogMeIn’s GoToAssist desktop sharing software. From there, the scammer often asks to gain remote control of the computer.
Who’s getting hit the hardest by tech support scams?
In the US, residents in Florida, California, New York and Texas appear to be the hardest hit by tech support scams.
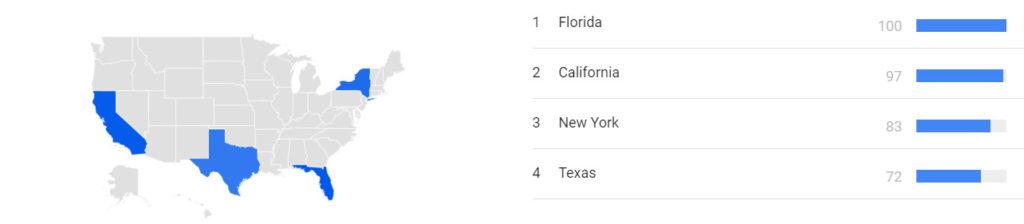
Based on what we know about consumer behavior (that nearly half of all consumers impacted by these scams use search engines to seek out more information), Google Trends data appears to indicate that most other states are marginally impacted by comparison.
Worldwide, numerous countries are getting scam calls, but most individuals who receive them don’t lose money to them. According to the 2018 Microsoft study on tech support scams, Japanese consumers were the least likely to lose money after receiving a scam attempt, while Indian consumers were the most likely to find themselves on the losing end.
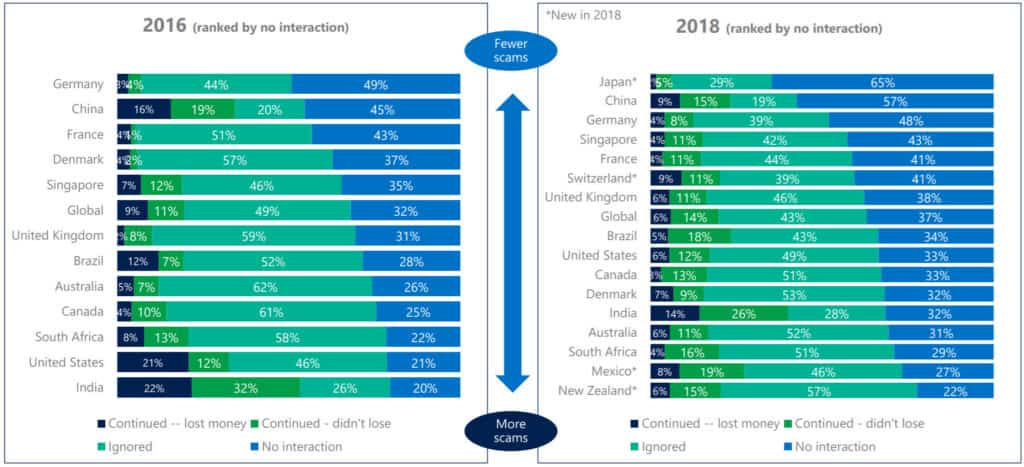
Overall, tech support scams both in the US and worldwide appear to be on the decline, both in terms of how many get through to potential victims, and how many are ultimately successful at finalizing a payment.
Remote access
Once baited, the tech gets the user to download and install a remote access program like LogMeIn or TeamViewer. The tech then uses the same program on their computer to gain access to the user’s system, taking control of the computer remotely. The tech then has free reign to do as he wants. Users have reported infection by viruses, detection of keyloggers, trojans, worms, and even ransomware. As soon as the tech finishes, he demands payment for the “service” to the tune of anywhere from $100 to $600. Of course, once they have your credit or debit card information, they can, and often do, charge whatever they feel like charging, possibly multiple times.
The tech can then reconfigure the remote access software to automatically accept an incoming connection, allowing the fraudster to access that computer whenever they want. They can, and usually do, copy and install some files from their own computer to the victim’s computer containing all sorts of malware
- Keyloggers are programs that record every click of the mouse, what was clicked on and every keystroke on the keyboard. These records are then uploaded to a server of the attacker’s choosing at regular intervals
- Worms have also been installed by these fraudsters with their own nasty surprises for unsuspecting users. A worm is a type of virus that is self replicating. While it may not do as much harm, it usually eats up all of the available network bandwidth in the process of replicating itself to all of the computers that are connected to the infected machine.
- They have also been known to install ransomware on their victims’ computers to extend their potential income from each and every tech support session. Ransomware encrypts all of the data on a device and demands ransom from the victim in exchange for a password to unencrypt it
One other side effect is the potential for identity theft. Like so many other types of scams, the attacker is after not just money, but saleable goods as well. The installation of a key logger on a computer allows them to see anything that is typed into the keyboard or anything that the mouse clicks on. If the user then clicks on a bookmark to their bank’s online banking website types in their username and password, that information is transmitted via the keylogger program to the fraudster, without the user ever knowing about it until it’s too late.
How to tell when it’s a tech support scam
There are notable warning signs that exist that can help indicate when a webpage, pop-up, email, or phone call is a Microsoft tech support scam.
For scams that start with a phone call:
- Microsoft and most other tech companies do not initiate tech support phone calls
- Most tech scam calls come in with a robotic voice and leave a voicemail with a number for you to call back
- Many calls now use neighbor spoofing methods that mimic a local number to get you to pick up. The call-back number will likely be different than the number from which the call was received
For tech support scams that start with a pop-up, webpage, or website redirect:
- The URL for the webpage will likely be composed of gibberish or just numbers
- The page may automatically enter full-screen mode and block your access to your toolbar
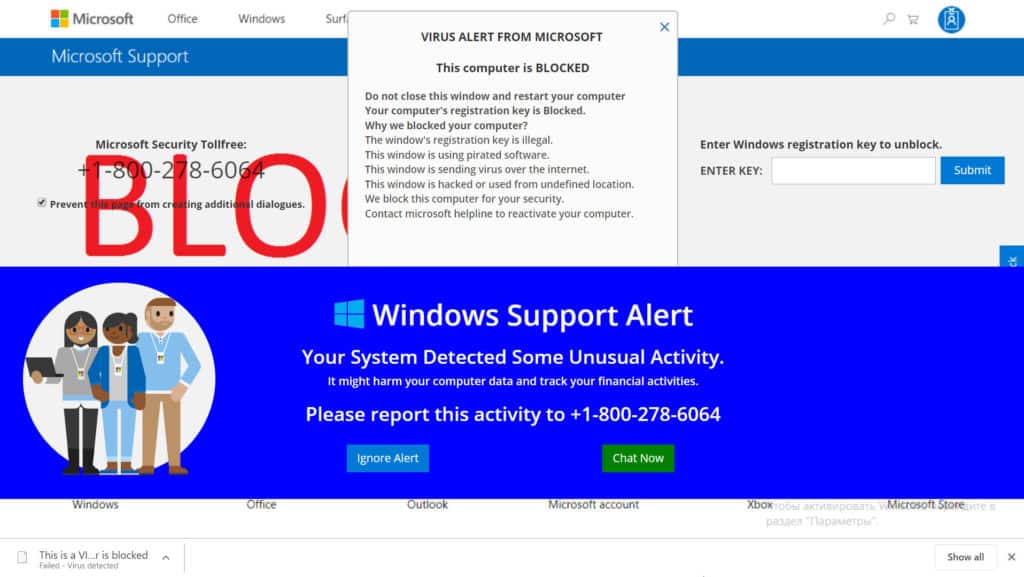
- There may be a computer-generated audio file that plays in the background of the webpage or pop-up, either with a warning tone, or an automated voice that warns of pornographic spyware and/or malware, hackers, or other threats. It may also warn you that your computer will be disabled and your IP reported to authorities if you close the window before calling their tech support number. Here’s one such page we found below:
The computer-generated background audio on this page stated the following:
Microsoft Spyware Alert.
Pornographic spyware/riskware detected.
Error number 0-80072EE7.
Your computer has alerted us that it is infected with a pornographic spyware or riskware. This spyware is sending your financial details, credit card details, Facebook logins and personal details to an unknown IP remotely. Please call us immediately on the toll-free number listed so that our support engineers can walk you through the removal process over the phone.
If you close this page before calling us, we will be forced to disable your computer to prevent further damage to our network and will send a copy of this report to the concerned authorities to raise a complaint against your IP address.
- The page or pop-up may attempt to automatically download malware onto your system or may try to prevent you from closing the page altogether
- The page will always contain a phone number to call, but may also have a box for you to enter your Microsoft product or registration key, which the scammers could use to try to steal your legally-purchased copy of Microsoft Windows
For tech support scams that start with an email:
- Most will be filtered to your spam email folder
- Those that make it through to your email may not come from a “tech support agent”, but could be pretending to come from a legitimate website, such as PayPal or a shopping site. Some may even sail past spam filters by abusing weak account validation security on legitimate websites
- The email may state that a virus or cyber attack has been detected, or may lead you to click on a suspicious link to a phishing site similar to one mentioned above
- Any links in the email will not match the link text
- The sender name will likely not match the email address
Ultimately, whether contact is initiated via a spam call, email, or website page/pop-up, Microsoft Windows tech support scammers seek to get you on the phone and use verbal scare tactics to persuade you that your computer is infected, that your personal information and financial details are vulnerable, and that you need their technical assistance to remove the infection or network infiltration.
Microsoft does not operate tech support in this manner. If you run into a webpage warning of a computer hack or infiltration on your network, close the page and immediately run a virus scan on your computer. If you receive a phone call from Microsoft tech support, ignore it, and report the number to the FTC(US), CRTC (Canada), or ICO (UK).
For official Microsoft tech support questions, use the company’s online tech support system.
After dozens of tech support scam calls, here’s what we found
Tech support scammers vary in their methodology. Comparitech spent several months calling dozens of scam numbers. While most numbers failed to reach a target (the growing popularity of scambaiting has resulted in hundreds of netizens working around the clock to shut these scams down as soon as they arise), many numbers we called did result in a successful hit. Several also produced an extended phone interaction, revealing valuable information regarding how these scams operate.
When we successfully connected to tech support scammers, we pretended to be concerned and hapless computer users. We allowed the scammers to walk us through the scam up until they either determined we weren’t biting fast enough, until they gave us the money pitch, or until they figured out we were actually scamming them into giving away their trade secrets and wasting their time.
What we found is that most (but not all) tech support scammers use two methods:
- The scammer will claim your computer has a virus infection that needs to be cleaned (sometimes true if the scammer intentionally infected your computer)
- The scammer will claim your network has been hacked and that the hackers’ access to your computer and network needs to be removed
Scammers did not always try to gain remote access to our computer as part of the scam. In some instances, they simply claimed to be checking our computer’s network connection after gathering basic information about the computer we used, put us on hold for a few minutes, and then stated what they believed to be the problem and the solution.
In every situation, Comparitech found tech support scammers gave us a significant amount of false information, to include:
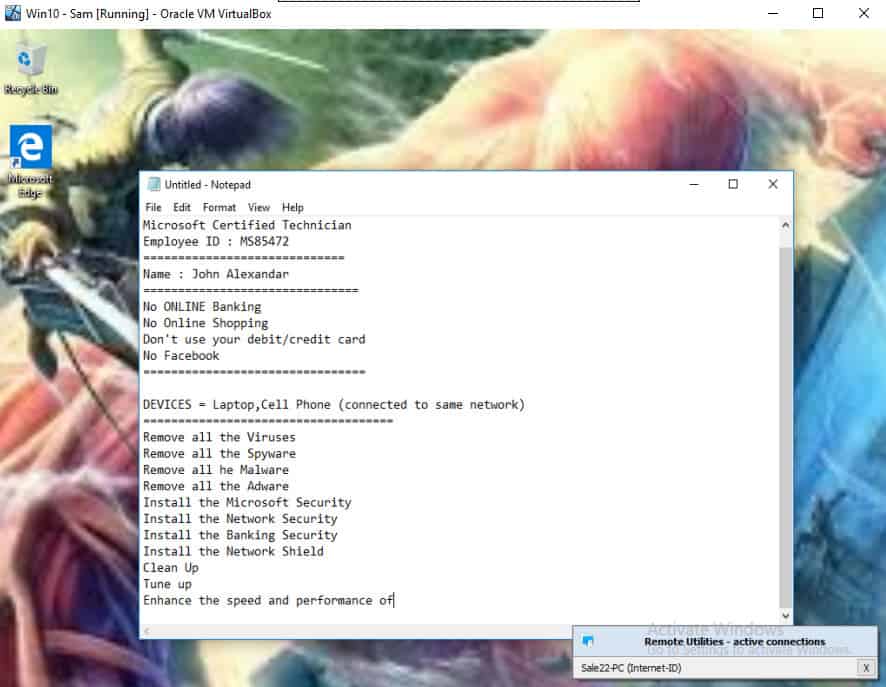
- An almost certainly fake name often suited to the country where the scam is targeting (such as a European- or Western-sounding name for American targets)
- An assumed employee ID number
- A fake support ticket number
- False information about the problem that exists on your computer or network
- Misleading information about the scammer’s location
- Misleading information about the effectiveness of other malware removal tools, such as Windows Defender
- False information about why payment is necessary
Additionally, these scammers did not request payment via credit card during any of our interactions. Instead, they asked us to drive to our local grocery or convenience store and purchase a gift card (including Google Play Store gift cards) carrying the amount required to fix the problem.
The amounts requested varied but always added up to several hundred dollars per fix. In one instance, we were told our network was under attack by a dozen separate hackers, and it would cost us $50 per cyber attacker to fix the issue.
Importantly, the tech support scammers always requested payment before making any changes or “fixes”. As one might expect, paying the requested amount will likely result in the call ending immediately.
That said, if a scammer sees an opportunity beyond just a digital payment, they will take it. If a tech support scammer can glean personal information from you, they will. If they can extract financial information, passwords, Social Security Numbers, and other personal information, they will, and will likely keep the call going as far as possible if they see an opening. This holds true for other types of tech support scams, such as BT tech support scams currently plaguing the UK.
Legitimate tools are being used to gain remote access to victims
One of the most striking details we uncovered has to do with how these scammers gain remote access to computers. Tech support scammers who do gain remote access to a computer will do so by using legitimate websites and applications instead of relying on malicious software to accomplish the mission.
We found the scammers we interacted with tended to prefer a legitimate service called FastSupport.
Side note: Although none of the scammers we reached used it, TeamViewer is also a known tool tech support scammers may use to gain remote access. One Reddit user described how his grandmother’s computer was overtaken from a tech support scammer who used TeamViewer.
FastSupport is powered by LogMeIn’s GoToAssist (now RescueAssist) software and allows one computer to remotely connect to another over an internet connection. By using this legitimate website, Microsoft tech support scammers can have the appearance of running a legitimate operation.
The service has a reporting tool for abuse of its system that supposedly tracks the support key the scammers are using. However, it’s unclear how effective this reporting tool is at stopping these types of scams.
Comparitech would like to reiterate: LogMeIn and its FastSupport site, as well as TeamViewer, are fully legitimate companies whose hands are clean in the use of their software for criminal purposes. Both companies maintain pages warning users of tech support scams, but at present, both have a fairly open usage model for their software that makes it easy for scammers to abuse these systems.
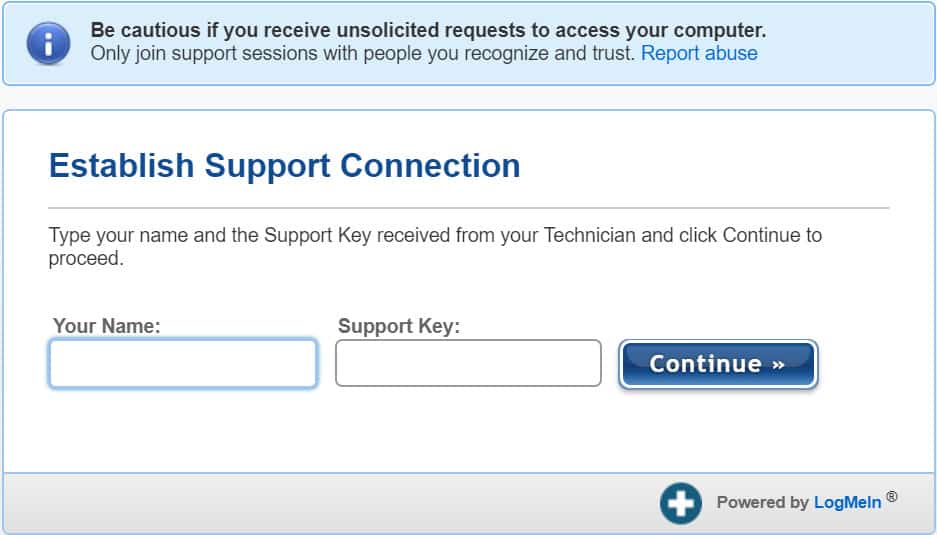
How do scammers use LogMeIn’s FastSupport?
LogMeIn is mostly unable to stop its FastSupport system from being used in tech support scams due to how it’s operating the service. All a scammer needs to do is go to the GoToAssist website and quickly create an account using the 7-day free trial.
The only barrier to gaining access as a FastSupport user is the requirement of a business email address to sign up (e.g., it does not accept free email services, such as @gmail.com or @yahoo.com). A unique email address can easily and cheaply be created using a number of different email service providers, often with a free trial.
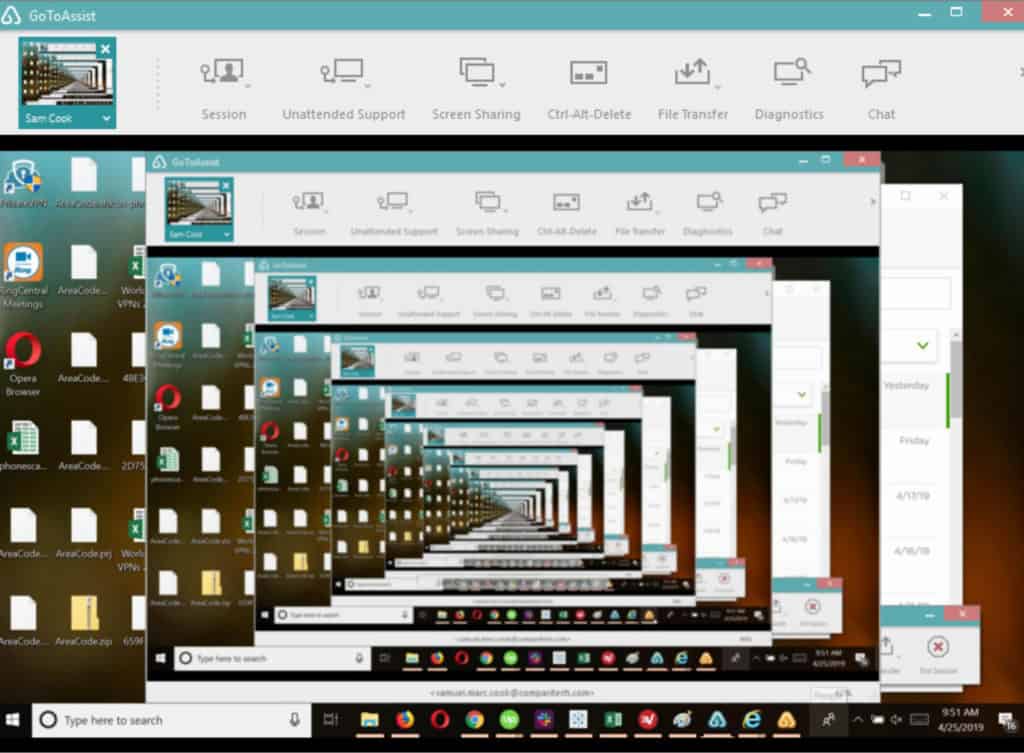
Within minutes, Comparitech was able to create a GoToAssist account and was immediately issued a support key. Scammers use that support key to direct victims to FastSupport. After entering the support key into FastSupport, the website prompts the user to download the remote login software. From there, the scammer has unfettered access to a victim’s computer until the victim closes the connection.

As an example, I used this process to gain remote controlled access to my own computer (as it were, a trippy experience similar to a mirror-in-mirror reflection).
Once a scam operation has started, tech support scammers will attempt to make the remote login look more official and more technical by directing users to access Internet Explorer using the Windows Run Command box.
Here’s the simple (and completely unnecessary) method they gave us:
- Hit the Windows Key+R
- In the Run command box and then type “/iexplore fastsupport.com”
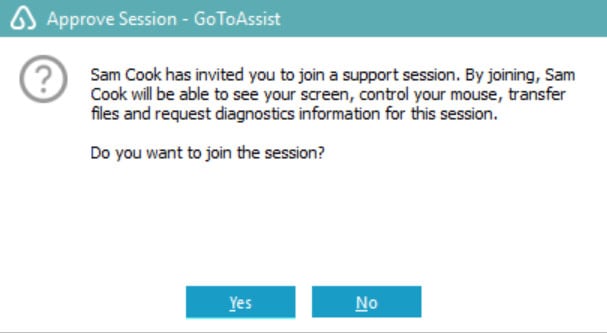
From there, scammers who gained remote access to our virtual machine asked us to input a name and the support key. The webpage immediately redirects to a download which may automatically download the LogMeIn software. The software also asks the victim to give remote control of the system to the scammer, which is important as this is what allows scammers to make covert changes to a victim’s machine.
Notably, GoToAssist gives the option for remote viewing. However, scammers prefer the option to take full control over a computer, and will always prompt victims to allow this level of control.
On the phone, the tech support scammer always guided us to say “yes” to everything happening without giving any information as to what we were agreeing to. We were never given an explanation regarding what the scammer was doing before and after remote access was given.
Once the scammer has remote access to your computer, he or she can take several routes. While we did not personally find any scammers who tried to install anything on our honeypot system after gaining control of it, it’s important to note that this does happen and is one of many scam operations that exist.
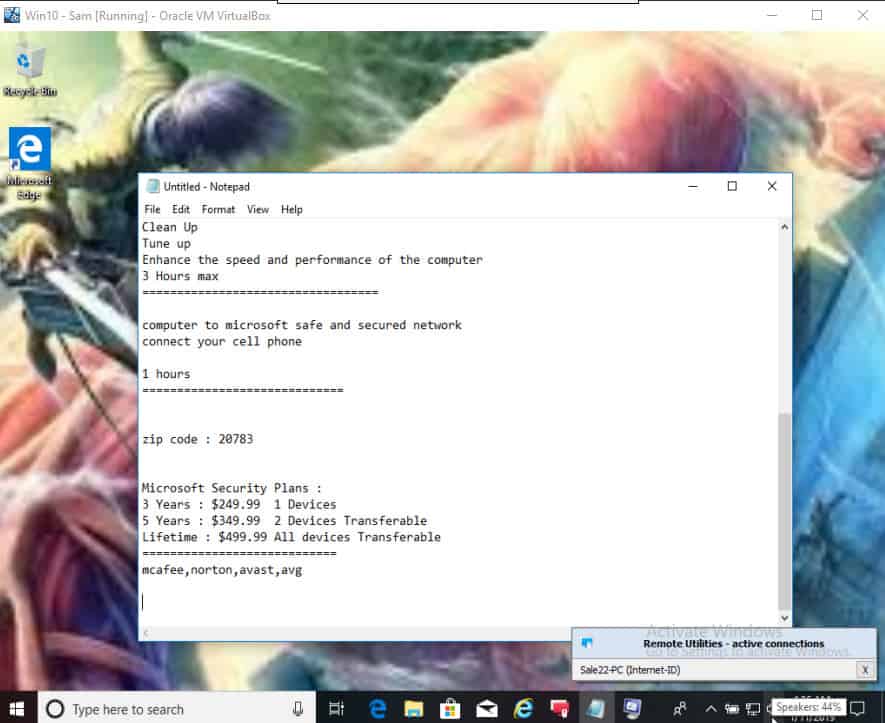
In one case, after gaining remote access to our virtual machine, the scammer opened an instance of Notepad and simply typed in her credentials and an “assessment” of the problem:
She followed that with typing in the cost to “fix” the problem for me.
Others who gain remote access to the system may make it so that you cannot see what they are doing to your system, and may run an assessment on your system to try to make surreptitious changes to it (such as by installing keyloggers or other tracking malware), or may try to determine if you are who you say you are.
As we continued to run our scam bait operation over a few months, we increasingly discovered that tech support scammers are growing wary and suspicious of scambaiting, and have ultimately become quicker to hang up or question anything that looks suspicious on their end.
For example, in one instance, we were asked to prove our location by honking a car horn, and in another, we were questioned why the computer’s details we gave didn’t match what the scammer found after he gained remote access. Ultimately, we found scammers tend to hang up rather quickly if they feel the scam won’t bear any fruit, which can happen within seconds of the call.
What to do when you’ve been scammed
If you have been scammed in this manner, all is not lost. But you do need to begin your damage control right away to minimize the amount of havoc the scammers can wreak in your life and on your system. First and foremost, disconnect your PC from the internet. Shut it down if you want, but make sure that it cannot access the internet when it boots up.
If you gave the scammer your credit card or financial information then you need to call your bank. Let your bank know that you’ve been conned and you would like to go over your recent charges, starting from the day you were scammed so that the bank can reverse any charges from the scammers. You might need to report the card as stolen depending on how much information you gave them. Talk it over with your banker and heed their advice.
If you have an attorney, let them know what’s going on as well. Cleaning up identity theft can be a struggle without legal counsel. You might end up getting your local law enforcement and maybe the FBI involved in your case. Get as much help as you can with this process. If you don’t yet have an attorney, you would do well to at least consult with one. The amount of legal legwork that goes into resolving a case of identity theft more than justifies the cost of retaining legal counsel.
To get your computer cleaned up, start with it disconnected from the internet. If you have an antivirus program already installed, run a full system scan, removing anything that it flags as a threat. Go into the control panel’s programs utility and remove the remote access software that the scammer had you install. While you’re in there, look for anything that you don’t recognize installing or that looks suspicious. If the date that it was installed or last accessed is the same date as your session with the fake tech, uninstall it. Finally, use another computer and a USB thumb drive to download another antivirus or antimalware program. Use the thumb drive to copy it from the other computer over to your compromised computer. Install and run it just in case your antivirus software might have missed something. Consider running a system restore to a restore point prior to installing the remote access software.
One of the big myths about anti-virus software is that your computer is safe from viruses when you run anti-virus software. The truth is that running antivirus software does make your computer safer, but nothing can make it 100 percent safe from infection. A new virus needs to be identified, analyzed and put into the anti-virus definition files before the anti-virus software can protect against it. The same applies to any other form of malware. The newer the virus, the lower the odds of anyone antivirus program recognizing it as harmful to your computer.
Assuming your computer is running fine at this point, it should be safe to reconnect it to the internet, update your antivirus software and finish your damage control. You will want to start changing all of your online passwords for everything from banking to email and social media accounts. Everything. Assume that the fake tech copied your entire list of online accounts with usernames and passwords from your web browser. Once you’ve taken care of all of that, you can sit back and keep a wary eye on your computer and your various online accounts.
As always, you will want to keep backups of all of your important files, run regular antivirus and antimalware scans and keep your operating system updated with all of the latest security updates. Use unique, complex passwords, especially for critical accounts like online banking, PayPal, eBay and any other site that can have a direct affect on your finances. That can get a bit taxing, so you might want to look into a good password manager.
Technical know how
For those of you who are interested in seeing some of the tools these con artists use, here are some of the more common ones, broken down by operating system:
Windows 7
Event Viewer
 Possibly the tool most used by IT professionals and scammers is the Windows Event Viewer. Windows is setnup to keep track of just about everything that happens by logging different computer events. Below is just one set of instructions for accessing these logs. There are other ways to get to the same place, though.
Possibly the tool most used by IT professionals and scammers is the Windows Event Viewer. Windows is setnup to keep track of just about everything that happens by logging different computer events. Below is just one set of instructions for accessing these logs. There are other ways to get to the same place, though.
 Click on the Windows Flag button at the bottom left of your screen to get the Start menu
Click on the Windows Flag button at the bottom left of your screen to get the Start menu- Right click on “Computer” in the column on the right of the menu
- Click on “Manage” to open the Computer Management tool
- In the column on the left, click on the small arrow next to “Event Viewer” to expand the list of logs
- The easiest one of these logs to exploit is the Application log, simply because it will normally have the most errors, so take a look at it first by clicking on “Application” in the left-hand column
- The right-hand side of the window will now populate with the list of event messages in the top and the details of the selected event in the bottom
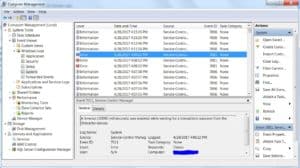
Most of the events listed herein will be informative little notes that get written to the log all the time. However, there will be some errors recorded as well, and that’s OK. Most of the time, these errors do not affect the operation of your computer at all. The errors are easily identified by the red stop sign shaped icon with an “X” in the middle of it.
Feel free to skim through the other logs as well. There are a few others dealing with the setup and installation of new device drivers, security audits for keeping track of successful and unsuccessful logins as well as logs for recording various system events like the starting and stopping of services.
Running Services
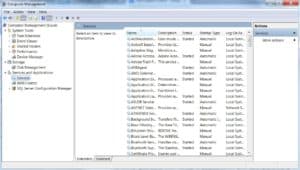 The Windows operating system relies on a bunch of different programs running in the background. Each of these programs provides a different service to the operating system, allowing it to do it’s job, from maintaining the computer’s internet connection to keeping the hard drive spinning.
The Windows operating system relies on a bunch of different programs running in the background. Each of these programs provides a different service to the operating system, allowing it to do it’s job, from maintaining the computer’s internet connection to keeping the hard drive spinning.
However, a whole bunch of services may not be needed for your computer to properly work. From remote login capability to database servers, there are a whole bunch of things that most computers simply aren’t being used for. The services are there in case they are needed, just not running.
To see the list of all the services on the computer, simply follow the above steps one through three to access the Computer Management tool. In the column on the left, click on “Services” to populate the right side of the window with the list of services.
The right-hand panel will contain the full list, sorted alphabetically by name. There will also be a description, status, startup type and login for each service.
Task Manager
 Your computer does what it does because it has certain resources available to it. They are:
Your computer does what it does because it has certain resources available to it. They are:
- CPU – Central Processing Unit – This is what does all of the work of making sense of the operating system, device drivers and programs that are installed on your computer. It has its own small chunk of memory to hold things in while it works on them
- RAM – Random Access Memory – This is where a big chunk of the currently running programs are stored, temporarily, while the CPU does its thing
- Hard drive – This device is where everything lives on the computer. The operating system, all of the programs installed on the computer, your family vacation pictures and everything else
When your computer starts to run slow, it helps to know which of these resources is causing the lag. The task manager gives you a real-time view of how these resources are being utilized.
In Windows 7, press three keyboard keys at the same time: CTRL, ALT, and Delete. The menu that comes up will have “Start Task Manager” at the bottom of the list. Click on it.
The first tab shows what programs are running and what their current status is. If any of them have the status of “Not Responding” it means that the program is either very busy at the moment or it has crashed. To shut down any of them simply click on the program you wish to shut down and then click the “End Task” button at the bottom of the window.
The Processes tab lists each and every currently running program that allows Windows to function. Again, you have the ability to shut down individual processes, but as these are Windows-specific processes, it is inadvisable. This is one area that fake techs like to manipulate because shutting down crucial processes can make the computer behave erratically.
The same applies to the Services tab. This is a list of all of the currently running services and the resources they are using. As was explained earlier, not all of the services built into the Windows operating system are needed, so many won’t be shown as running.
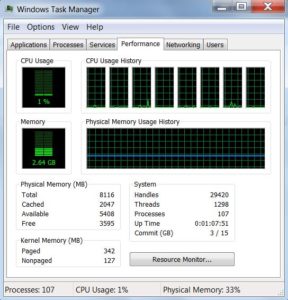 The Performance tab shows some graphs with usage levels of each of your CPU’s cores and the computer’s memory. As many as eight cores can be shown, each with their own graph. These graphs will spike each time that core performs any work. Seeing lots of spikes and valleys is perfectly normal. The only thing that is harmful to the computer is if one or more core’s graph is pegged at 100 percent for several minutes.
The Performance tab shows some graphs with usage levels of each of your CPU’s cores and the computer’s memory. As many as eight cores can be shown, each with their own graph. These graphs will spike each time that core performs any work. Seeing lots of spikes and valleys is perfectly normal. The only thing that is harmful to the computer is if one or more core’s graph is pegged at 100 percent for several minutes.
The memory graph won’t spike nearly as much as the CPUs, but rather will maintain a steady percentage of usage. The more programs you have running, the more memory is used. The more tabs you have open in your web browser, the more memory is needed to keep those web pages current. Again, the only danger sign is if the memory is pegged at 100 percent usage for any period of time, even if you close actively running programs.
Closing a program with the keyboard
At the beginning of this article, there was mention of a web page that doesn’t close easily. Believe it or not, this is a feature of the web browser that makes it full screen and removes the close, minimize and maximize buttons. To get rid of one of these pages, hold down the ALT key on your keyboard (it’s beside the space bar) and hit the F4 key in the top row. An alternative is to use the Task Manager described above to shut down the web browser with the “End Task” button.
Note that some laptop keyboards use the F keys for other purposes, such as volume control and screen brightness. In this case, you might need to press the Function key (“Fn” or something similar) in addition to Alt+F4.
Manipulating the command prompt
 The command prompt, or command line, has been around since the first personal computers hit the market back in the 1980s. However, the only people that make use of it these days are IT people, both real and fake. Even the simplest commands in this tool can be used to con people into believing that their system has been heavily infected.
The command prompt, or command line, has been around since the first personal computers hit the market back in the 1980s. However, the only people that make use of it these days are IT people, both real and fake. Even the simplest commands in this tool can be used to con people into believing that their system has been heavily infected.
To access it, click the Windows Flag at the lower left of your screen and type three letters into the search box at the bottom of the menu: “cmd”. As you type, the menu will change from your normal selection of programs to the search results. The top of the list will be “Command Prompt”, so click on that.
The command prompt is keyboard-centric so ignore the mouse for the following commands. Type each command as displayed, without the quotes, to get the output that is described next to the command. You will need to press “Enter” after typing each command to activate its functionality:
- “dir /s” – The command “dir” by itself simply lists the contents of the current directory or folder. Adding the “/s” switch to that command makes it list the contents of the current directory and the contents of all the folders inside that directory. A fake tech will claim that this command lists infected files on the computer’s hard drive
- “color 4” – This command changes the color of the text in the command prompt window to red. A fake tech will claim that the red text is an indication of the operating system or their software having detected a massive infection
- “Ping 192.168.253.82” – Ping is quite often used to check a computer’s connection to other computers, whether they be on the internet or a local area network. The numbers that follow the ping command are the digital address, or IP address, of the computer that you are trying to reach. A fake tech will put in an address that is most likely not a valid address in order to get an error from the user’s computer. That error is then used to describe a problem that doesn’t really exist
- “netstat -an” – This command displays the current network status of the computer. Specifically, it lists all of the currently open network ports and their status. The port is just a number, but the status can be set to “listening”, “established” or “closed”. A fake tech will describe the status of “listening” as a hacker listening to everything your computer is doing
There may be other commands that these fake tech support people will use, simply because the command prompt is a powerful tool for running system diagnostics and various cleanup utilities. However, initial detection of viruses and malware is best left in the hands of programs that are running full time in the background, not one-off commands accessed through the command prompt.
Windows 8, 8.1 and 10
Event Viewer
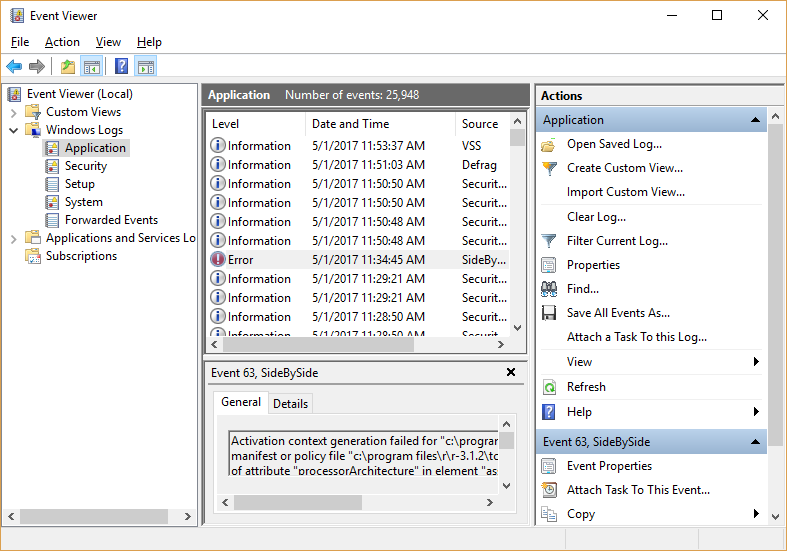
To get into the Event Viewer in the newer versions of Windows is a bit easier. From the desktop, simply right click on the Windows flag at the bottom left of the screen and select “Event Viewer” from the menu that comes up. Once it opens, you can click the arrow icon next to “Windows Logs” to see the list of log files. Clicking on any one of them shows the list of log messages on the top of the right side of the window. Clicking on any log message in that list displays the details of the event below the list.
Just like in previous versions of Windows, there are a few different logs for the different areas that Windows keeps logs for.
- Applications, or the programs that are installed on the computer
- Security log for tracking logins
- The Setup log is mostly for recording what happened during the initial setup of the operating system and all of the device drivers
- There is a System log for keeping track of the operating system’s service related events
- To record forwarded events, the computer has to be receiving event messages from another computer for remote monitoring purposes
Running Services
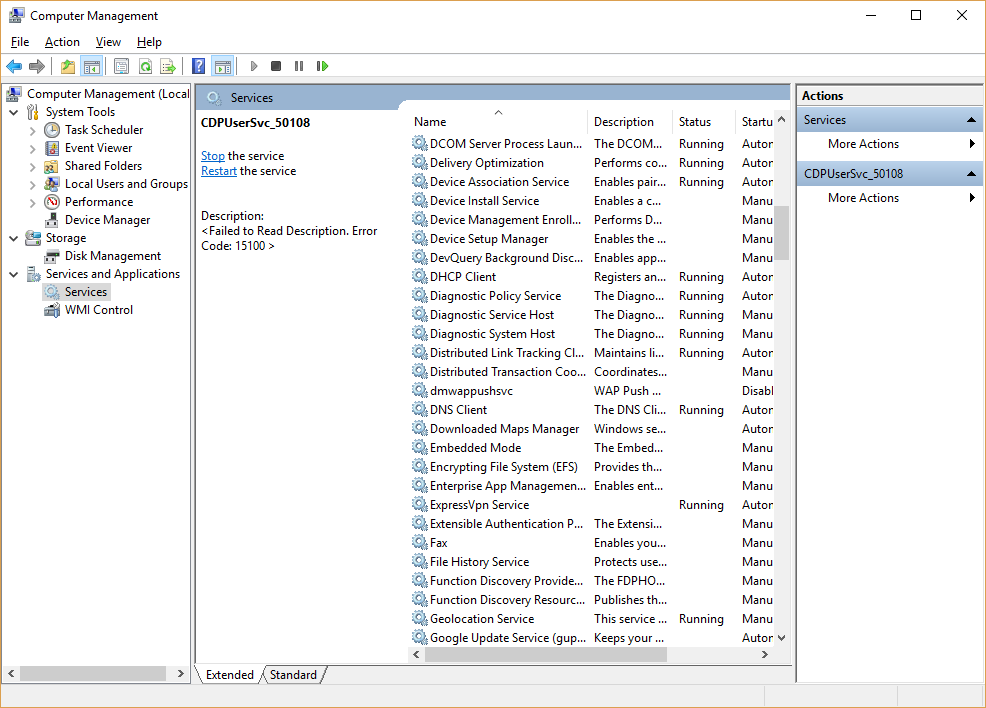
You may have noticed in the above section that when you right click that Windows flag, the menu has quite a few options. One of the more robust tools is the “Computer Management” option near the middle of the list.
The Computer Management window contains the event viewer, the device manager, the list of services and a few other important tech tools. There are way too many to cover in just this one article, so click on the Services option in the left-hand pane.
Just like in past versions of Windows, this list shows all of the available services listed alphabetically by name, a description of what the service does, it’s current running status, it’s startup type and the user login that it runs under.
Many of these will not be started as they are not needed for every PC. This is perfectly normal and nothing to panic about.
Task Manager
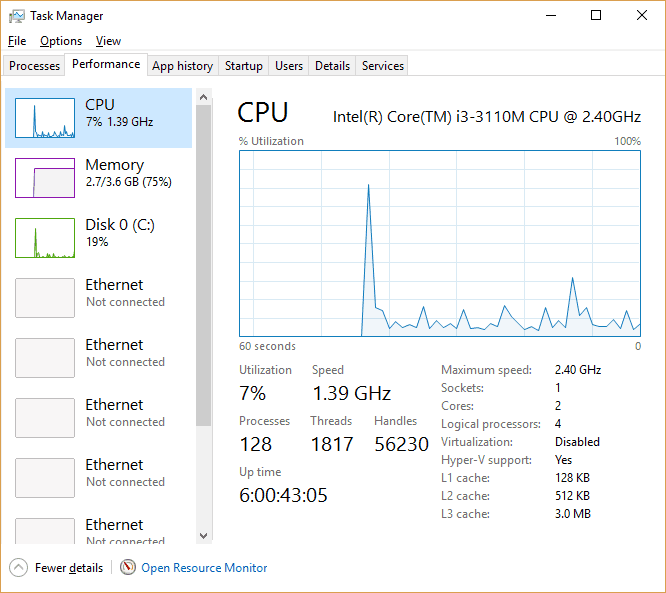
Accessing the task manager requires a simple right click on the Windows flag at the bottom left of your screen. The menu lists “Task Manager” near the bottom of the list. Clicking on that option gives you a window with up to seven tabs, each relating to the currently running programs and the resources in use by those resources.
- Processes – This tab gives you a list of currently running programs and what resources each one is using
- Performance – Here you see the graphs of utilization for each of the computer’s resources
- App History – The total amount of computer resources used by each program is listed on this tab
- Startup – Each program is listed here along with it’s startup settings. Most won’t start when the computer does so will have a startup impact of “None”
- Users – Since the introduction of Windows 2000, PCs have had the ability to have more than one user logged in at a time. This tab shows what resources are being used by each of those users
- Details – This lists each of the currently running Windows processes, what user account the process is running under, how much attention it’s getting from the CPU, how much memory it’s using and a brief description of what the process is or what it does
- Services – Another place to view the currently running services along with what resources are being used by those services
The graphs in the Performance tab are supposed to have peaks and valleys. Those are simply signs of the computer doing its job. The only thing here that should be cause for concern is if the CPU or the memory are pegged at 100 percent for more than a couple minutes.
Keyboard command to close a running program
Just like in past versions of Windows, holding down the ALT key and pressing the F4 key in the top row of the keyboard is a keyboard shortcut to close the active program. If you run into one of those annoying web pages that fill the screen and doesn’t have a close button, use this shortcut to get it out of your face. Alternatively, you could shut down the web browser using the Task Manager described above.
Using the Command Prompt
When Microsoft introduced the Windows 8 metro style, a lot of the old ways of doing things became a little difficult to find. Then again, some became really easy. If you simply start typing the letters “cmd”, the search tool automatically comes up and you will see “Command Prompt” in the search results.
In Windows 10 you can use the key combination of the Windows flag key on your keyboard along with the letter “x”. The menu that pops up will have “Command Prompt” as one of the options.
The command prompt is a very keyboard-centric tool. Type each of the following commands as displayed, without the quotes, to get the output that is described next to the command. You will need to press “Enter” after each command to activate its functionality:
- “dir /s” – The command “dir” by itself simply lists the contents of the current directory or folder. Adding the “/s” switch to that command makes it list the contents of the current directory and the contents of all the folders inside that directory. A fake tech will claim that this command lists infected files on the computer’s hard drive
- “color 4” – This command changes the color of the text in the command prompt window to red. A fake tech will claim that the red text is an indication of the operating system or their software having detected a massive infection
- “Ping 192.168.253.82” – Ping is quite often used to check a computer’s connection to other computers, whether they be on the internet or a local area network. The numbers that follow the ping command are the digital address, or IP address, of the computer that you are trying t reach. A fake tech will put in an address that is most likely not a valid address in order to get an error from the user’s computer. That error is then used to describe a problem that doesn’t really exist
- “netstat -an” – This command displays the current network status of the computer. Specifically, it lists all of the currently open network ports and their status. The port is just a number, but the status can be set to “listening”, “established” or “closed”. A fake tech will describe the status of “listening” as a hacker listening to everything your computer is doing
Summary
Simply put, if you did not initiate the tech support call due to a legitimate problem that you detected, then it’s a scam. If someone contacts you claiming to have detected a problem with your computer, either through a phone call or a webpage, you can safely ignore them and continue with your day.
The only companies that make their living this way are scammers. No legitimate company makes their money by selling tech support services to random people on the internet or over the phone. Legitimate tech support companies sell their support services via contracts, mostly to other companies, on either a monthly allotment of hours or on an on-call basis. Currently, the technology to identify an infected personal computer over the internet does not exist.
“Houston, we have a headset…” by Robert Murphy licensed under CC BY-SA 2.0