Cybercrime and fraud are particularly worrying for small businesses, which typically lack the resources needed to recover from them. According to recent figures from McAfee’s Global Small Business study, some 44% of the surveyed small businesses had experienced a cyberattack. Of these, 61% lost more than $10,000 – a potentially crippling amount.
Clearly, the days of crossing fingers and hoping it won’t happen to you are gone. Business owners need to take preventative steps to stem losses resulting from fraud and cybercrime. Thankfully there are a number of actions you can take to secure your business,
In this guide, we discuss some of the major risks facing small businesses and provide recommendations for securing your organization.
Types of cybercrime affecting small businesses
Small businesses face many of the same risks as larger organizations. Here are some of the top types of fraud and cybercrime to be aware of:
- Phishing
- Ransomware
- Other types of malware
- DDoS attacks
- Data breaches
- Accounts payable fraud
- Credit fraud
- Chargebacks
- Other types of fraud
- Man-in-the-middle attacks
- Tech support scams
- Physical theft or attacks
Let’s look at each of these to find out what the risks are:
Phishing
Phishing schemes use social engineering to persuade victims to carry out some type of action or hand over information. Communication may be through email, text message, social media message, or phone. A fraudster will typically pose as someone else, for example, a representative of a business associated with the company or an internal employee. Phishing attacks against businesses are often highly targeted “spear-phishing” attacks.
CEO fraud is a type of phishing scheme where the attacker poses as a senior-level executive, often to persuade an employee to wire a large sum of money. There’s also whaling, another type of phishing that targets executives themselves. In some cases, attackers are able to hijack genuine email accounts, a tactic called Business Email Compromise (BEC).
Phishing schemes can play out in a number of different ways, but they usually involve the attacker trying to glean personal or financial information or persuade the victim to hand over money. For example, an employee may end up on a phishing site where they enter account login credentials. Or they could be duped into handing over customer details (many data breaches stem from phishing attacks), trade secrets, or company financial information. In other cases, employees will be instructed to send money to an account that turns out to be fraudulent.
Symantec found that smaller organizations receive malicious emails at more than double the rate that larger businesses receive similar messages.
Ransomware
Ransomware is a type of malware. It usually works by encrypting files or folders and holding them hostage until a ransom is paid. Typically, victims will see a popup message on their screen explaining what has happened, the size of the fee, and how it should be paid (often in cryptocurrency).
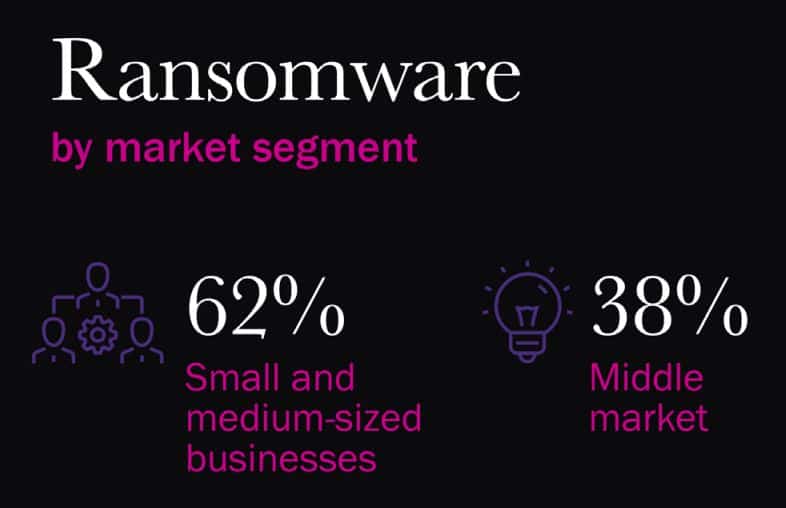
Small and medium-sized businesses account for 82% of ransomware attacks. And a Datto report tells us that ransomware is the top malware threat for SMBs. One in five say they’ve been the victim of a ransomware attack.
Other types of malware
Other types of malware such as trojans, viruses, and spyware can pose a risk to your business too. Malware could enter systems via a variety of means including malicious emails, malicious ads (malvertisements), or hardware such as an infected disk or thumb drive.
DDoS attacks
In a Denial of Service (DoS) attack, an organization’s systems (networks or servers) are flooded with traffic. The result is that bandwidth and resources are exhausted and the system is unable to deal with regular (legitimate) requests. A Distributed Denial of Service (DDoS) attack involves multiple compromised devices—a botnet—combining forces to overwhelm the target system.
Data breaches
A data breach occurs when someone gets their hands on information that should have been secure. There is a wide range of causes of data breaches, including phishing, hacking, misconfiguration, and privilege abuse. A Verizon report tells us 83 percent of breaches involve external actors who tend to be financially motivated.
Data breaches result in higher costs per employee for smaller companies than larger organizations. Small businesses typically lose $3,533 per employee whereas large companies lose $204 per employee.
Data breaches can have serious short and long-term impacts on businesses such as lost income, fines, and a damaged reputation.
Accounts payable fraud
Accounts payable scams are those that involve a company’s outgoing payments. There are many types of internal and external accounts payable fraud including billing schemes (such as overbilling or fake vendors), payroll fraud, kickback scams, check fraud, Automated Clearing House (ACH) fraud, and expense reimbursement scams.
One report found that 14 percent of occupational fraud involves accounts payable departments. Fraud cases last an average of 14 months and result in a mean loss of $8,300 per month. Many of these schemes can last years without being noticed.
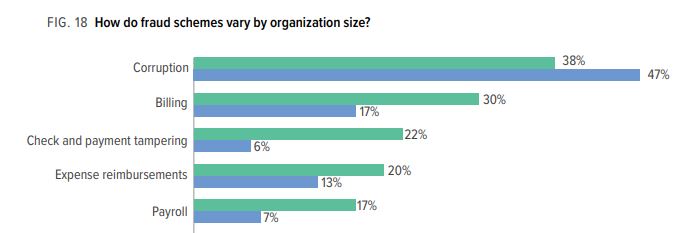
According to the report, small organizations are twice as likely as larger companies to be the targets of billing and payroll fraud. They are four times as likely to be involved in check and payment tampering.
Credit fraud
Another type of fraud that affects both individuals and businesses is credit fraud. This is where a fraudster uses the credit standing of a person or business to apply for credit cards or take out loans. These types of schemes often go undetected for years. This is a form of identity theft and is unfortunately quite common. American companies lose billions to fraud and identity theft each year.
Chargebacks
A chargeback occurs when a customer contacts their bank to get a refund on a payment. This is often at the merchant’s expense and in many cases, the product is not returned. Chargebacks are often legitimate, for example, if a merchant has sent the wrong or defective product but refuses to take any action.
However, chargebacks are often abused. This occurs when there is no issue with the item (or service) but the customer requests a chargeback and keeps the item. Other cases involve stolen credit cards that are used to purchase merchandise. The original cardholder then makes a legitimate chargeback request but the merchant is often the one who loses out.
Other types of fraud
While accounts payable fraud covers many of the most common types of fraud affecting small businesses, there are plenty of other schemes to look out for. These include fake currency schemes, return scams, workers’ compensation, wire scams, debit and credit card skimming, new account fraud, and more.
Man-in-the-Middle (MitM) attacks
A MitM attack involves an attacker eavesdropping on an organization’s communications. The goal is usually to steal data or to attempt to filter or change it. For example, an MitM attack could be used to steal login information or personal or financial data, spy on victims, corrupt data, or redirect funds.
MitM attacks usually involve a hacker intercepting a business’ network traffic. They might compromise the office wi-fi router or employees’ VPN connections, for example.
Tech support scams
Tech support schemes often target individuals but they can affect businesses too. In this scheme, a fraudster will pose as a computer technician, usually over the phone. They will use social engineering tactics to persuade the victim (a company employee) to hand over company information or allow remote control of a company computer or other device.
Physical theft or attacks
Of course, physical theft is always a risk. These days, we can keep vast troves of company information on a thumb drive, which makes it incredibly easy for that data to fall into the wrong hands.
Criminals might have an interest in stealing a range of hardware such as computers, disks, USB sticks, hard drives, or other devices that may contain sensitive information. They may even try to gain physical access to a device to install malware such as spyware.
Other physical attacks might target company vehicles, for example, to install a GPS tracking device.
How to prevent fraud and other types of cybercrime
After reading about the threats, you may be pretty worried. However, there are a ton of steps you can take to secure your business. There are plenty of privacy and security tools available to help small businesses, with options to suit a broad range of budgets.
Here are some of the ways you can help protect your business from cybercrime:
- Invest in personnel and training
- Practice good password hygiene
- Utilize a solid firewall and antivirus software
- Use a VPN
- Keep software up to date
- Have anti-fraud measures in place
- Run penetration tests
- Encrypt email and messages
- Implement HTTPS
- Back up data
- Use mobile device management
- Consider a hosted virtual desktop
- Implement network access control tools
- Use data loss prevention software
- Tighten physical security
- Consider cyber insurance
Below we’ll examine each of these in a bit more detail:
1. Invest in personnel and training
One of the most important steps to take in securing your business is to create a culture of security awareness. Errors such as software misconfigurations or falling for phishing schemes can lead to massive losses.
Educating employees on security is one of the top priorities in cybercrime prevention. This means having the proper protocols in place and ensuring staff is properly trained. It may even mean hiring additional personnel with cybersecurity expertise to drive initiatives.
You also need to ensure that employees feel comfortable coming forward with pertinent information. Lots of cybercrimes, including many data breaches and cases of fraud, involve intentional actions by internal actors. And the Harvard Business Review tells us that employees are the best at fighting fraud. It’s important to foster a culture in which whistleblowers feel safe. You may even consider job protections and rewards for employees who come forward with information.
Statistics from the Association of Certified Fraud Examiners’ Report to the Nations show the value of employee training and avenues for reporting. Some 42 percent of schemes were uncovered as a result of a tip, more than half of which came from employees.
In 40 percent of cases, whistleblowers used email. Calls to a telephone hotline were made in 27% of cases. Employees with training on fraud awareness were more likely to send tips via a formal reporting mechanism.
Some internal cybercrime can be avoided by improving the hiring process. Be sure to carry out background checks (including a social media audit) on all prospective employees and consider requiring a credit report to be run on new hires.
2. Practice good password hygiene
Using strong passwords is vital for individuals and businesses alike. It’s important that employees use a different strong, unique password for each account. Business owners can encourage the use of strong passwords by providing employees with a password manager such as Dashlane, Sticky Password or LastPass. These will securely store passwords and autofill them so the user only has to remember one master password.
For extra account security, you can use two-factor authentication (2FA) or two-step verification (2SV) where available. These add an extra step to the login process, for example, an SMS or email code, biometric authentication, or a USB key (such as YubiKey).
Other areas that may need attention are social media accounts and online collaboration tools. These platforms are increasingly used for work duties, but may be utilized for personal activities too. It’s important that employees are clear about the privacy and security practices they must maintain on any platform used for work tasks or to discuss work activities. For example, privacy settings on social platforms may need to be tweaked and it might even be advisable to set up separate accounts for personal and work activities.
3. Utilize a solid firewall and antivirus software
A firewall provides an initial layer of defense for your systems by monitoring traffic flowing in and out of ports. Software firewalls are the ones that are usually built into a device’s operating system while hardware firewalls may be found in your router. If you’re relying on these, it’s important to make sure they’re enabled.
If you don’t have a built-in firewall or you want added protection, there are third-party firewalls available. These range in price with lots of free and paid options available.
A solid antivirus software will provide another layer of defense and is usually worth paying for. An antivirus will detect known threats and may be able to remove them from your system. Again, there are plenty of quality antivirus tools available.
4. Use a VPN
A VPN can play a crucial role in keeping your network secure by protecting data in transit. A VPN encrypts all information traveling to and from your network helping to protect it from snoopers. VPNs can enable employees to securely access the internet and also to connect to a company server for securely accessing company resources such as shared folders and apps.
There are a number of options for business VPNs, with the optimal setup depending on your resources and the structure of your business. There are even free tools available, such as OpenVPN, so with the right know-how, it can be cheap to set one up.
Most large companies operate their own VPN. However, most small businesses lack the IT expertise and resources to make this an effective option and would be better off signing up with a business VPN provider. You can check out our list of the best VPNs for small businesses for information on the top providers.
Businesses with multiple sites might opt for a site-to-site VPN. Open-source software is available to set these up, but again, they can be quite complex. Providers like Palo Alto and Cisco are popular options for paid solutions but can be pricey.
Some VPN providers are branching out to expand their services and offer Zero Trust Access systems. Nord Security, the provider of NordVPN is an example of this phenomenon. Their NordLayer service combines VPN protection with identity and access management (IAM) to protect access to applications on an individual basis rather than controlling access to a network or a server. This “microsegmentation” solution enables businesses to unify the security management of on-premises and cloud-based software and simplifies the lives of the user community by creating a single sign-on (SSO) environment.
Another example of a VPN-based security system for small businesses is Perimeter 81. This cybersecurity startup was created by the team that began Safer VPN. The team sold off their VPN provider to focus on the new, cutting-edge field of Secure Access Service Edge. This innovative new field of hybrid network security marries together protection for remote access to company resources and the need for on-site employees to securely access cloud-based SaaS packages.
Although the concept seems complicated, it is achieved by adding Identity and Access Management (IAM) to the standard VPN client. Perimeter 81 provides reasonable per-user pricing, which is much the same as any team VPN account.
5. Keep software up to date
Keeping software up to date is crucial for security. Vulnerabilities in software can be exploited by cybercriminals who use them to gain access to systems or install malware. Updates typically include patches for known flaws, so it’s important that you install them soon after they’re issued.
Some 90 percent of web applications are vulnerable to attacks by hackers, but 80 percent of attacks use vulnerabilities that are two years or older, so installing updates can drastically reduce your risk.
6. Have anti-fraud measures in place
Fraudulent activity is often very difficult to spot. Business owners and employees need to learn the signs to look out for to detect internal and external fraud. Employee theft can be particularly hard to detect, but common signs that accounts payable fraud may be taking place include missing checks and employees who are suddenly flush with cash.
Having the right policies and processes in place can not only help detect fraud but also deter it from happening in the first place. Some suggestions are:
- Monitor for stolen checks
- Ensure new vendors and information changes are verified
- Carry out unscheduled internal and external audits
- Use automated fraud detection technology
- Utilize employee monitoring software
- Have more than one employee handle sensitive tasks such as invoice details, payroll, deposits, and reconciling statements
- Train employees to detect malicious emails and messages that may be part of fraud schemes
- Put a fraud alert on your business credit report
- Investigate chargebacks and consider using chargeback management software
The strategies you implement will depend on the size and nature of your business and how individual tasks are usually handled. Again, a culture of awareness and a safe avenue for employee reporting is crucial.
7. Run penetration tests
It’s always good to have a benchmark that shows you the key areas in which your security practices could be improved. Penetration testing assesses your applications, systems, and network to tell you exactly where your security flaws lie. Ongoing testing will then tell you how much you’re improving and what you still need to work on.
There are several routes you can take to perform penetration testing. If you have in-house information security personnel, they should be able to set up testing tools for you. Most companies will benefit from using third parties for penetration testing. Some offer simulations and ongoing surprise tests so you can continuously monitor your exposure to threats like phishing, malware, and more. Many will offer employee training programs tailored to the test results.
Penetration testing usually doesn’t come cheap, but there are solutions to fit a range of budgets.
8. Encrypt email and messages
If you’re concerned about the interception of messages, you may want to look into various methods of email encryption. There are a few options available ranging from easy-to-use web-based email clients like Hushmail to more complex encryption setups that involve key pairs and certificates.
If employees or customers tend to communicate via messaging apps, consider which apps are most secure and whether their settings are being used appropriately. For example, Telegram offers end-to-end encryption as an option, but Signal uses it by default.
It’s important to keep up to date on the latest changes in privacy policies for these apps too. For example, a change to the WhatsApp privacy policy with respect to business communications led to some businesses revaluating the best messaging app to use.
9. Implement HTTPS
Many businesses set up a website without giving security a second thought. Implementing HTTPS on your site protects information being sent between your sites and its visitors, which can help prevent MitM attacks and snooping by internet service providers. It also signals to customers that you value security and data privacy.
Setting up HTTPS involves obtaining an SSL certificate; this sounds a bit complicated but the whole process is actually very simple. Nowadays, trying to run a website without HTTPS will negatively impact your business’s ranking in search results and drastically reduce the number of visitors to the site overall.
10. Back up data
Do you only have one copy of your data? If all of your business’ data is stored on a PC or hard drive, there’s always a risk it could be wiped, corrupted, lost, stolen, or physically damaged, for example, due to a flood or fire.
As a safeguard, it’s a good idea to have at least two copies of all important data. Regular backups are the best way to do this. You may choose to use a cloud backup system or you might prefer hardware backups. Just remember if you choose the latter, the backups should be stored in a separate location from the original. This way, if one is stolen or damaged, it’s less likely the other will be too.
Cloud systems are increasingly popular as they make it easy to set up automatic backups and keep your information secure. Backup services don’t have to break the bank, although completely free tools tend to offer very limited storage space.
Most cloud backup and storage services encrypt your information by default, but you may be extra cautious about certain files or folders. In that case, you can add another layer of encryption with a service like nCrypted Cloud or Encrypto.
11. Use mobile device management
Mobile Device Management (MDM) has become an increasingly hot topic, especially since the pandemic when many employees began – and then continued – to work remotely. MDM enables you to effectively manage devices remotely. Features of MDM tools might include:
- Tracking, locking, and wiping utilities
- A dashboard for monitoring devices
- A detailed view of installed applications
- Remote control for troubleshooting
- Policy and restriction configuration and management
- Deployment of new applications and updates
The exact functionality will depend on which tool you go for, so it’s worth comparing different providers carefully before settling on the right fit for your needs.
12. Consider a hosted virtual desktop
Another tool you can use to protect your systems from certain risks is a Hosted Virtual Desktop (HVD) such as Amazon WorkSpaces (AWS). Also called Desktop as a Service (DaaS) or Virtual Hosted Desktop (VHD), an HVD places a PC desktop (including its operating system and other applications) in the cloud, enabling access from anywhere.
This has practical benefits in that you don’t have to install software on numerous devices and resources can be easily shared between employees. It’s particularly helpful from a security perspective because it avoids threats at the device level, such as risks related to wi-fi connections, disk drives, USB ports, and cameras.
13. Implement network access control tools
Access control is a crucial part of network security, but it’s a difficult area to manage. One popular approach is least privilege, in which employees have access to the minimum information and tools they require to perform their duties.
This is especially important when you have employees on a Bring Your Own Device (BYOD) program or working remotely. Network Access Control (NAC) tools can help you control who has access to what. They even enable you to stipulate where and when employees can access specific applications or data.
14. Use data loss prevention software
Human error is unavoidable, but you can mitigate the impact that mistakes have on your business. Data Loss Prevention (DLP) software enables you to apply rules to data so that employees are unable to share it, accidentally or intentionally. For example, you could apply filters to stop employees sending an email that contains a certain keyword or prevent specific files from being shared.
15. Tighten physical security
Digital security is of huge importance, but you also need to make sure you don’t let physical security slide. Lost, stolen, or damaged devices can lead to significant issues for a business.
Full disk encryption is a good idea for protecting information stored on an actual device, and is especially important for laptops that may be used in public spaces and easily stolen. You can also use physical locks to prevent someone swiping a laptop or tablet in the first place. For example, Kensington offers a range of solutions for multiple device types.
Another thing you can do to secure devices in the event of loss or theft is to enable remote erase software. For example, iOS users can enable Find My iPhone and Android users can install Find My Device. These tools can help you locate a lost or stolen device and enable you to lock or erase the device remotely. MacOS has a similar app option and you can find remote-erase tools for Windows PCs. Many MDM tools mentioned above offer these capabilities too.
You should also report any lost or stolen devices to the police. There’s usually only a slim chance they could recover them, but it’s better than no chance at all. Plus you will likely need to report loss or theft for insurance purposes.
16. Consider cyber insurance
Speaking of insurance, do you have cyber insurance included in your coverage? This has been around for some time but in the wake of mass data breaches and expensive ransomware attacks, it’s becoming far more common for insurance providers to bundle it in with business insurance packages.
Cyber insurance will usually cover you against financial damages caused by things like viruses and other malware, data loss and theft, and network damage. Ideally, businesses should assess their risk of various types of attack and have a cyber insurance policy that is tailored to those risks. Note that you don’t have to go with the same provider that handles your standard business insurance and you should shop around and compare the various offerings.