A customer database of more than 1.1 million records was exposed on the web by SCUF Gaming, maker of high-end gamepads and other video game peripherals. The database included customer names, contact information, payment info, order histories, and repair tickets, among other data.
Comparitech’s security research team led by Bob Diachenko uncovered the data, which was accessible on the web without a password or any other authentication. The data was exposed for about two days before we discovered it and reported the incident to SCUF.
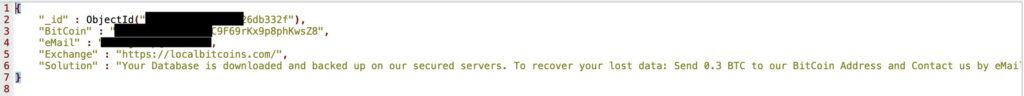
By the time we found the database, it already contained a note apparently left by criminals demanding ransom. It stated, “Your Database is downloaded and backed up on our secured servers. To recover your lost data, Send 0.3 BTC to our BitCoin Address and Contact us by eMail.” [sic]
SCUF customers could be at risk of fraud and targeted phishing attacks perpetrated by criminals who might have accessed the data.
A spokesperson for Corsair, SCUF Gaming’s parent company, responded to Comparitech with a statement, saying:
“[…] Once notified, we identified the root cause of this exposure and secured the database within two hours. While investigating Mr. Diachenko’s warning, we also discovered that a bot had connected to the database’s server and placed a ransom note there. We have no evidence that either the bot or any other actor was able to misappropriate customer data.
This issue was specific to one system, being operated off-site due to work-from-home precautions resulting from the current COVID-19 pandemic.”
Timeline of the exposure
The database was exposed for less than 48 hours according to our investigation, but that was long enough for an unauthorized party to access it. A Corsair spokesperson told Comparitech it was an automated bot, saying, “The bot script […] did not encrypt/delete any data, and was not connected long enough to the server to download the database.”
- April 2, 2020 – The database was indexed by search engine BinaryEdge.
- April 3, 2020 – Comparitech discovered the database and Bob Diachenko immediately notified SCUF Gaming.
- April 3, 2020 – The database was secured within two hours of disclosure.
Most of the records appear to have been collected by SCUF Gaming between 2017 and 2020.
What data was exposed
The database included both customer and employee information, though customers accounted for the vast majority of it.
- 1,128,649 records containing full names, email addresses, billing addresses, shipping addresses, phone numbers, and order histories
- 991,478 records containing payment details including order numbers, partial credit card numbers, credit card expiration dates, order amounts, and transaction IDs
- 754 SCUF Gaming staff records including usernames, full names, encrypted passwords, email addresses, user roles, and session IDs
- 144,379 records with repair order details
In addition to customer data, some encrypted internal API keys were exposed.
Employee session IDs were only valid for 24 hours and did not include any customer session IDs.
Dangers of exposed data
The customer records could be used by criminals to launch targeted phishing attacks wherein the scammer poses as SCUF Gaming or a related company. Customers should be on the lookout for phishing attempts sent to their phone or email address. Malicious emails or messages might encourage victims to click on links to fake login pages or download malware onto their device.
Personal information and payment details could be used for fraud. The credit card numbers were mostly redacted, though, only showing the last four digits. So there’s no need to immediately cancel credit cards—just keep an eye out for unusual activity on account statements.
Although the staff records make up a tiny fraction of the overall data, it’s potentially more valuable to criminals. The information could be used to launch further cyber attacks against the company.
Employees whose contact information was exposed are also at risk of phishing attacks.
About SCUF Gaming

Customers hand over their payment and personal details when they place an order. They can also create an account that allows for faster checkouts, multiple addresses, and order tracking.
SCUF products come with a warranty and offers online customer service, so the company also stores repair and refund details.
How and why we reported this exposure
Comparitech works with security researcher Bob Diachenko to find and report personal data that’s been exposed on the web. Upon discovering an exposure, we immediately begin an investigation to learn whom it belongs to, who might be impacted, what information was exposed, and what the potential consequences might be.
We first notify responsible parties so that the data can be secured. We then publish a report like this one to alert users who might be affected and mitigate potential harm.
Our goal is to curb malicious attacks that might result from exposure of personal data, such as identity fraud and phishing.
Previous data incident reports
Our team has uncovered several data exposures impacting millions of people, such as:
- 42 million Iranian “Telegram” user IDs and phone numbers leaked online
- 8 million UK shopping records exposed
- 250 million Microsoft customer service and support records exposed
- 267 million Facebook user IDs and phone numbers exposed online
- 2.7 billion exposed email addresses from mostly Chinese domains, 1 million of which included passwords
- Detailed personal records of 188 million people found exposed on the web
- 7 million student records exposed by K12.com
- 5 million personal records belonging to MedicareSupplement.com exposed to public
- 2.8 million CenturyLink customer records exposed
- 700k Choice Hotels customer records leaked