
Reverse tabnabbing, or simply tabnabbing, is a phishing attack in which an attacker fools a victim into entering their credentials on a fake website controlled by the attacker. I know that could describe many different online attacks. And while many online attacks spin up fake web pages to steal user data, reverse tabnabbing achieves this in a unique and clever way.
Reverse tabnabbing attacks can have very serious consequences, depending on which credentials they manage to compromise. Luckily, protecting against these attacks is fairly simple. In this article, we’re going to talk about what reverse tabnabbing is, how it works, and how to prevent it.
High-level view of reverse tabnabbing attacks
Here’s how a reverse tabnabbing attack might work:
- The victim has a website open in a tab, in their browser. Let’s assume they’re on Facebook. They log into the site and see that someone has posted something to their wall: an offer for a discounted something or other that the victim may be interested in.
- The victim unsuspectingly clicks the link and is directed to the website with the offer in a new tab. That website is actually a malicious site controlled by the attacker.
- While the victim is looking at the fake offer on the malicious site, the malicious site forces a redirect of the victim’s original Facebook tab to a fake cloned website, controlled by the attacker, that looks exactly like Facebook’s login page.
- The fake Facebook page prompts the victim to re-enter their credentials. Even though the victim knows that they’ve already logged in, there’s a good chance they will simply re-enter their email and password, thinking a small glitch must have happened. Such glitches are relatively common, after all.
- If the victim enters their credentials into the fake website, they’ve just handed their credentials over to the attacker and compromised their account.
How do reverse tabnabbing attacks work?
Reverse tabnabbing attacks are possible on websites that enable users to post links that, when clicked, open in a new tab. The link is opened in a new tab because of the link’s target="_blank" property.
When a user clicks on a link crafted with target= "_blank", their web browser injects two variables into the destination page:
window.openerwindow.referrer
The window.referrer property stores the source web page on which the link was clicked (the referring web page).
The window.opener property returns a reference to the parent window (the window that opened the window), with the target="_blank" property. You can use the window.opener property from the destination window to obtain details of, and operate changes to the parent window, such as redirecting the victim’s original open tab to a fake but legitimate-looking page that prompts them for their credentials. This is the crux of the attack.
Detailed example of a reverse tabnabbing attack
Let’s say an attacker posts the following link on a social network:
<!DOCTYPE HTML>
<html>
<body>
<h1>Crazy deal on sunglasses!!! Limited supplies!!!</h1>
<a href="https://evilsite.com" target="_blank">CLICK HERE!</a>
<body>
<html>When the victim clicks the above link, their browser will open ‘evilsite.com’ in a new tab. Because the new tab was opened through a link that used target=“_blank”, the attacker can exploit the window.referrer and window.opener properties. Let’s look at what evilsite.com’s code could look like:
<!DOCTYPE HTML>
<html>
<body>
<script>
if (window.opener) {
window.opener.location="https://fakelogin.com";
}
</script>
<h1>AMAZING DEAL ON STUFF YOU LIKE!!!</h1>
...
<body>
<html>While the victim is looking at the bogus deal on evilsite.com, evilsite.com redirects the victim’s original tab to a fake login page that appears to come from the website the victim had open. In our example above, the victim was logged in to Facebook, so the attacker will have crafted the fake login page to look like Facebook’s actual login page.
It’s the window.opener.location property that enables the redirect. If the victim enters their credentials in the redirected page, they’ll be unwittingly handing them over to the attacker.
Reverse tabnabbing attacks actually are quite simple, as you can see. But the damage they cause can be catastrophic, depending on the account that’s been compromised. Luckily, it’s not too difficult to protect against this type of attack, as we’ll see a bit further down.
Reverse tabnabbing attacks in the wild
In April 2017, it was reported that Russian hacking group APT28 had mounted an attack against French then-presidential candidate Emmanuel Macron. This is the same group allegedly behind the 2016 DNC email hack.
The technique used in the Macron attack was said to be tabnabbing by the Danish government’s security analysts, who wrote a report on the incident, after accusing APT28 of being responsible for the Danish government’s own Ministry of Defence email hack.
While the attack described here differs slightly from our playbook example above, in that there is an extra redirect from the malicious website (that is open when the victim clicks the webmail link) to the legitimate conference website. Prior to the redirect to the legitimate site, the malicious site will do its mojo and alter the open webmail tab.
From the report:
“Pawn Storm has been using a variant of tabnabbing. In this attack scenario, the target gets an email supposedly coming from a website he might be interested in—maybe from a conference he is likely to visit or a news site he has subscribed to. The email has a link to a URL that looks very legitimate. When the target reads his email and clicks on the link, it will open in a new tab. This new tab will show the legitimate website of a conference or news provider after being redirected from a site under the attackers’ control. The target is likely to spend some time browsing this legitimate site. Distracted, he probably did not notice that just before the redirection, a simple script was run, changing the original webmail tab to a phishing site. When the target has finished reading the news article or conference information on the legitimate site, he returns to the tab of his webmail. He is informed that his session has expired and the site needs his credentials again. He is then likely to re-enter his password and give his credentials away to the attackers.”
How to prevent reverse tabnabbing attacks?
The way to protect yourself from reverse tabnabbing attacks depends on which side of the attack you’re on: the server-side or the user-side. We’ll look at both.
Preventing reverse tabnabbing attacks from the server-side
On the server-side, the way to protect against reverse tabnabbing attacks is quite simple. However, this is applied in one of two ways depending on whether your site uses HTML or JavaScript to open new windows. We’re going to show you both ways.
HTML
In HTML, we need to make sure to set the rel HTML attribute with the noreferrer and nooperner parameters whenever the web server/application creates links.
Taking the same example as above, this would look like this (emphasis mine):
<!DOCTYPE HTML>
<html>
<body>
<h1>Crazy deal on sunglasses!!! Limited supplies!!!</h1>
<a href=“https://evilsite.com" rel=“noopener noreferrer”
target="_blank">CLICK HERE!</a>
<body>
<html>noopener ensures that the linked page does not have access to window.opener from the source page. While noreferrer makes sure that the request referer header is not sent along with the request. This way, the destination site does not see the originating URL that the user is coming from.
JavaScript
Using JavaScript, we can achieve the same thing as above by setting the opener property to null. This would look like this (again, emphasis mine):
var newWindow = window.open()
newWindow.opener = nullIf you’re going to be showing user-generated content, you should also make sure the server sanitizes the user input and applies “nooperner,noreferrer” to each generated link. Like so:
var newWindow = window.open(url, name, 'noopener,noreferrer')
newWindow.opener = nullPreventing reverse tabnabbing attacks from the user-side
As a user, there isn’t that much you can do. Most of it comes down to following basic security precautions that apply to pretty much any online activity. We’ll get to those.
But first, there is something concrete you can do as a user to protect yourself from reverse tabnabbing attacks. However, you must be using Mozilla Firefox as your web browser. Firefox is open-source and comes with a lot of tools to enhance your privacy and security out of the box. So I’d recommend using it anyway.
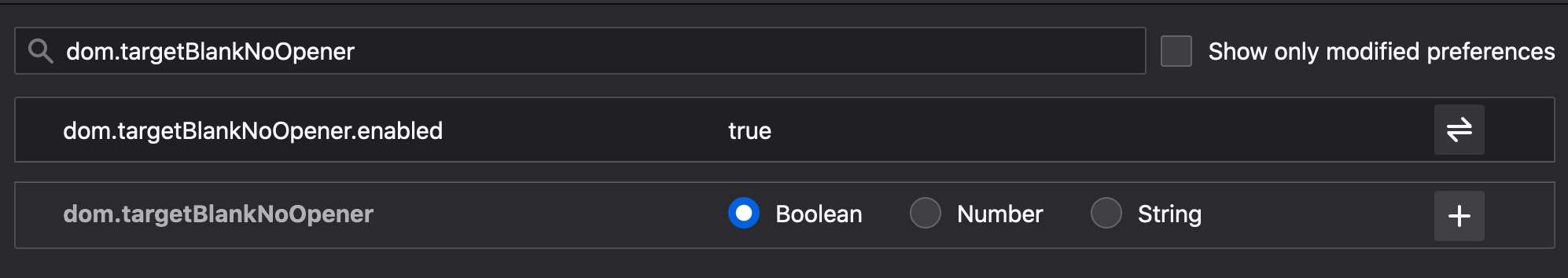
Firefox fix
- Open a new window in Firefox.
- In the URL bar, enter: about:config and hit Return. A warning message is displayed.
- Click Accept the risk and continue.
- From the search bar type: dom.targetBlankNoOpener.dom. The dom.targetBlackNoOperner.enabled property is displayed.
- Set its value to true. Close the window.
This bars your browser from using the window.opener property. So you should be safe from reverse tabnabbing attacks if you use Firefox as configured above.
Other things you can do is apply general vigilance when online and follow the tips below.
- Use a firewall – All major operating systems have a built-in incoming firewall, and all commercial routers on the market have a built-in NAT firewall. Make sure these are enabled as they may protect you in the event that you click a malicious link.
- Never click on pop-ups. You never know where they’ll take you next.
- If your browser displays a warning about a website you are trying to access, you should pay attention and get the information you need elsewhere. In a reverse tabnabbing attack, if the attacker’s site uses a self-signed or otherwise invalid HTTPS certificate, your browser will warn you about that. And listening to your browser may just save you from a tabnabbing attack.
- Don’t click on ads. Just don’t. Regardless of whether the ad is a banner, a pop-up, or a user post. If you’re interested in something, you can probably find it yourself in a few seconds using a search engine.
- Limit the amount of personal information you post on the internet. The more information that’s publicly available about you, the easier you may be to manipulate. The internet is a hostile place with no shortage of actors just waiting to exploit you. Before posting something revealing, ask yourself whether it’s really necessary or not.
Wrap up
So there you have it. Reverse tabnabbing attacks can have major consequences. But at least the vulnerability is easy to fix with a bit of coding etiquette. And, again, remember that the internet is a hostile network and treat it as such. You don’t want to be the weakest link in your own online security.
Stay safe.


Nice, short, and sweet article 🙂
And I thought it was just regular phishing!