
These days, it’s hard to get by without requiring passwords for multiple online accounts. Between work and personal life, the average internet user has dozens of password-protected accounts.
Coming up with secure passwords and remembering them all can be a challenge. This goes a long way toward explaining why so many people use weak passwords and the same or similar ones across multiple accounts. If this sounds like you, you’re not alone.
Read on to find out some surprising password statistics and trends that may change the way you handle passwords. If you’d like to bump up your online security, we provide some tips for choosing and managing passwords at the end of this post.
Password statistics and trends
We’ve collected the most interesting password facts and statistics based on recent studies:
1. 75% of Americans are frustrated with passwords
A 2019 study conducted by Google in conjunction with Harris Poll found that keeping track of passwords is a source of frustration for the majority of Americans. A whopping three in four respondents say they struggle with passwords.
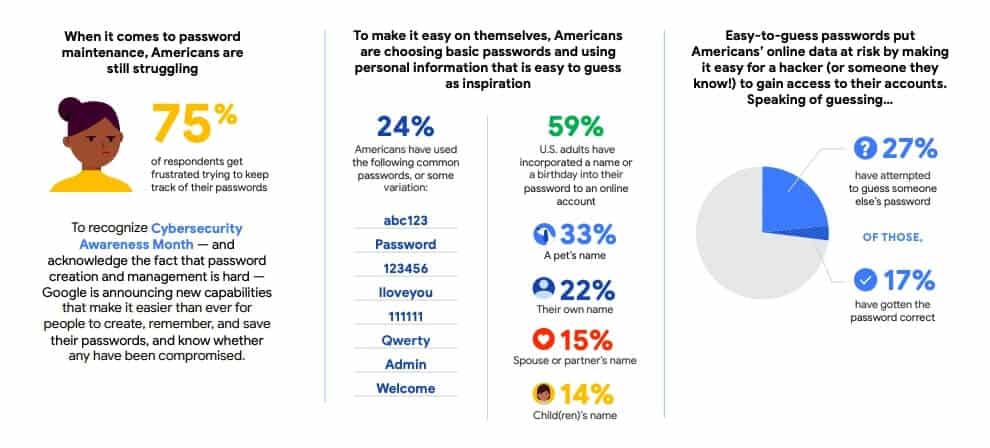
2. The most popular passwords are extremely easy to guess
The difficulty in keeping track of multiple passwords leads people to use easy-to-remember (and easy-to-guess) passwords. According to NordPass, the most common passwords in 2022 were:
- password
- 123456
- 123456789
- guest
- qwerty
Equally concerning were Google’s findings that almost a quarter (24 percent) of Americans have used some variation of the following weak passwords: abc123, Password, 123456, Iloveyou, 111111, Qwerty, Admin, and Welcome.
Clearly these are all very simple for anyone to guess and so provide very little protection. This is reiterated by Google’s findings: of the 27 percent of Americans who have tried to guess someone’s password, 17 percent have guessed it correctly.
3. 59% use their name or birthdate in their password
Even if people are smart enough not to use the passwords mentioned above, the majority of users polled by Google have included easily discoverable personal information in their passwords such as their name or birthdate.
Other common blunders include using the names of pets, spouses, or children — according to Mozilla, almost 400,000 passwords contained the name “Joshua”, with around 141,000 people including “Isabella” in their password.
Almost half of Google respondents reported having divulged a password at some point. Granted, 57 percent of these shared it with a significant other, which makes the statistic easier to digest. However, only 11 percent change their password after a breakup. This could explain why in California 10 percent of survey participants have the password of an ex-partner or former roommate or colleague.
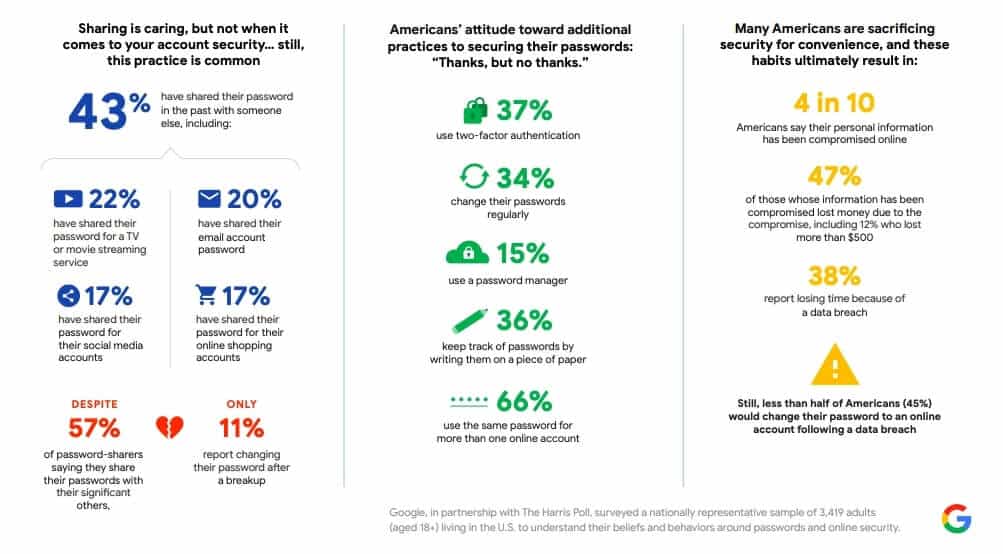
You’d think that your email account password would be the last thing you’d want to share with anyone, but one-fifth of users polled by Google have done just that. What’s more, 22 percent have shared their password for a streaming site, 17 percent for a social media platform, and 17 percent for an online shopping account.
6. Only 45% would change a password after a breach
According to the Google survey, fewer than half of Americans say that they would change an online account password if they discovered it had been breached. This is in spite of the fact that 40 percent admit their personal information has been exposed online, 47 percent have lost money due to compromised information, and 38 percent have sacrificed time as a result of a data breach.
7. A 12-character password takes 62 trillion times longer to crack than a six-character password
Have you wondered why the length of a password is so important? Every character you add makes it much more difficult to crack. For example, assuming all lowercase characters and a 26 character alphabet, there are around 3 x108 possibilities for a six-character password. On the other hand, as discussed in a Scientific American article, there are around 19 x 1021 possibilities for a 12-character password with lowercase and uppercase letters, numbers, and symbols (say 10 options).
To put it in perspective, if a given computer could crack the six-character password in one second, it would still take more than two million years to crack the 12-character password.
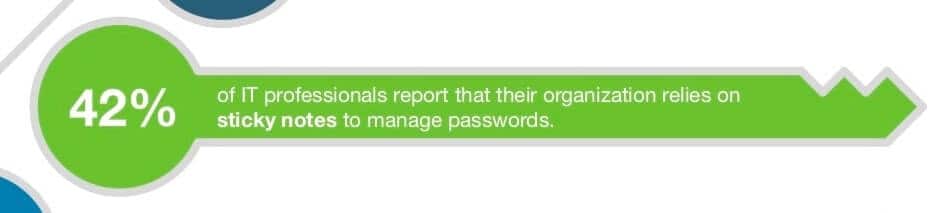
8. 42% of organizations rely on sticky notes for password management
The Ponemon Institute’s The 2020 State of Password and Authentication Security Behaviors Report showed the results of a survey of more than 3,000 individuals and IT specialists. There were some surprising results including the fact that almost half of IT specialists reported that sticky notes are used to manage passwords in their organization.
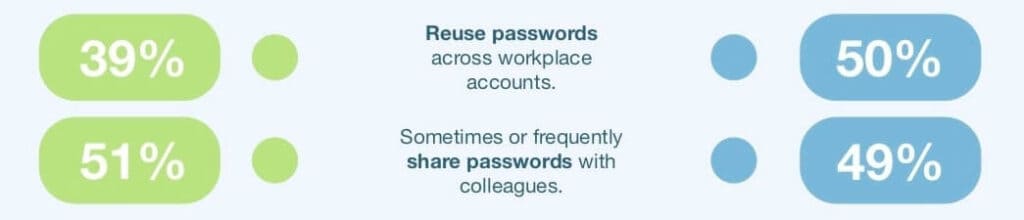
9. IT professionals reuse passwords more than average users
Another surprising revelation was that password reuse was more common for IT professionals (50 percent of whom admitted to reusing passwords on work accounts) than for other individuals (39 percent of whom were guilty of the same). IT professionals were also almost as likely as other individuals to share passwords with others (51 percent and 49 percent respectively).
One of the more shocking statistics was that after experiencing an account takeover, 75 percent of individuals changed the way they protected their accounts and managed passwords, but a much lower percentage (65 percent) of IT specialists did the same.
10. More than half of users would prefer an alternative method to passwords
The Ponemon Institute report found that 55 percent of individuals and IT specialists would like to protect their accounts by an alternative method that doesn’t involve the use of passwords. Most individuals are looking for ease of use on top of better security.

65 percent of IT professionals and 53 percent of individual users believe biometrics offer better security.
11. Over 40 million Microsoft users were found to have reused passwords
In a study that spanned just three months (January to March 2020), Microsoft found that a whopping 44 million of its users had used the same password on more than one account. Microsoft scanned its users’ accounts comparing the usernames and passwords to a database of more than three billion sets of leaked credentials. For users whose details matched a credential set in the database, Microsoft forced a password reset.
12. Almost two-thirds of people use the same password across multiple accounts
Another 2019 Google study in conjunction with Harris Poll found that 13 percent of people reuse the same password across all accounts, and a further 52 percent use the same one for multiple (but not all) online accounts. Only 35 percent use a different password for every account.
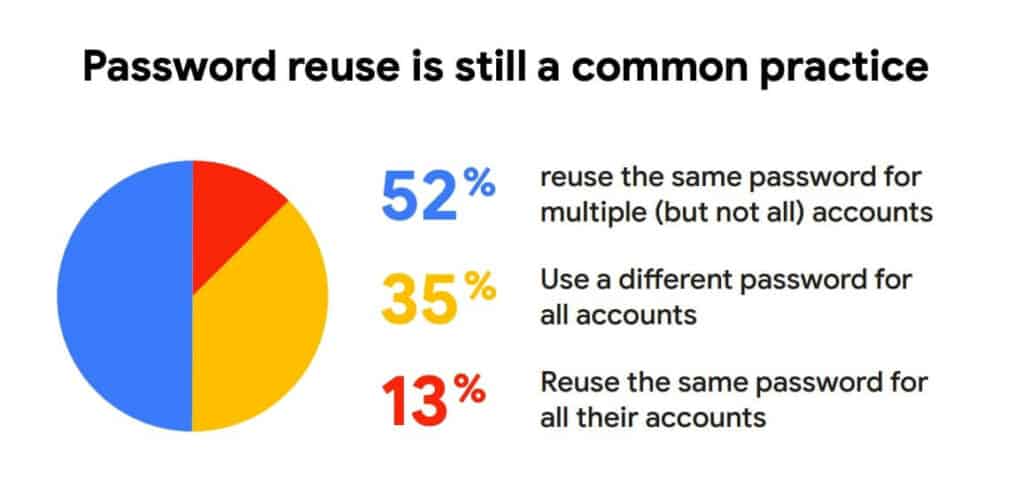
This is corroborated by other studies including a 2021 Spycloud study that says 70 percent of people reuse passwords for their personal accounts. This even applies to Fortune 500 employees, 64 percent of whom have the same password on multiple accounts.
13. More than one-third of people have over 20 passwords
According to the HYPR password usage study, 37 percent of people deal with more than 20 passwords, and that’s just in their personal life. 19 percent also have more than 10 passwords for their work life.
In its 3rd Annual Global Password Security Report, LastPass determined the number of work passwords to be much higher at 85 for SMB employees and 25 for workers at larger companies. These numbers depend on industry and country. Media and advertising employees manage an average of 97 work passwords. Belgian workers deal with an average of 100 passwords.
Even with these high numbers, only half of businesses offer a single sign-on solution that allows employees to sign in to more than one account with a single password.
14. 42% rely on memory for work passwords
Bitwarden has found that, as of 2022, 42 percent rely on memory to manage their work passwords. Perhaps more worrying, 53 percent had shared a password over email, with just 24 percent saying that they never share passwords.
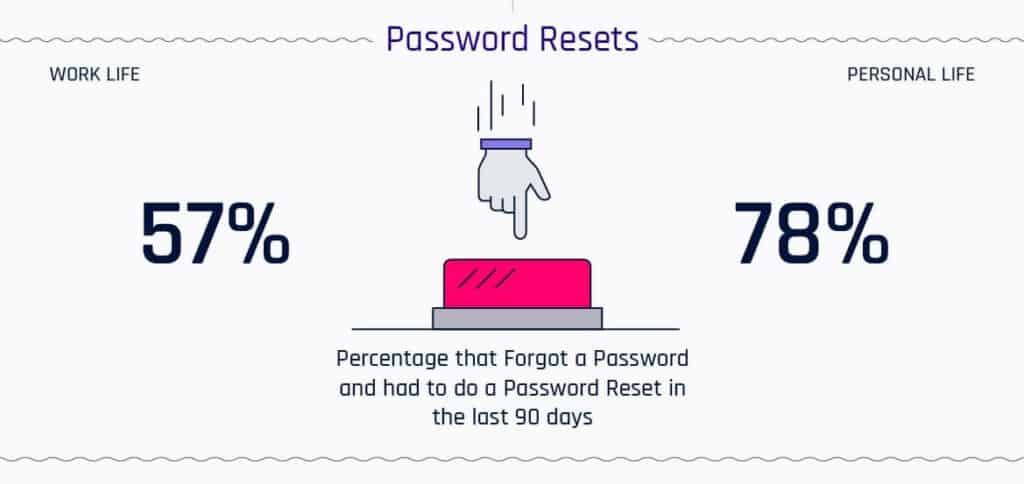
15. 78% of people have had to reset their password in the last three months
A HYPR study in 2019 uncovered the high rate of password resets. More than three in four users admitted to forgetting a personal password and having to reset it within the past 90 days. This number was quite a bit lower when it came to work passwords, but still, well over half (57 percent) had required a work password reset in the same time period.
16. Employees use the same password an average of 13 times
LastPass found that employees reuse a password an average of 13 times. Reused passwords represent a huge risk as someone with access to one set of stolen or compromised credentials could use them to hack into other accounts.
LastPass breaks down the results by company size, industry, and country. Employees of small businesses are the worst offenders. Those working for companies with 1-25 staff reuse passwords an average of 14 times. Media and advertising companies are by far the most likely to reuse passwords, with an average of a whopping 22 reuses per password.
As for which country is the worst, Canadians lead password reuse with an average of 15 times, closely followed by several countries including Australia and Belgium, where users tend to reuse passwords an average of 14 times.
17. MFA blocks 99.9% of all attacks
If Multi-Factor Authentication (MFA) is enabled on an account, this means you need to complete two or more steps to access it. The multiple factors could be, for example, a password, a text or email code, or biometric solutions.
In a 2019 blog post, Microsoft manager Alex Weinert stated, “Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.”
18. More than half of individuals use 2FA
In 2004, Bill Gates predicted the death of the password as he envisioned the mass adoption of more secure systems such as Two-Factor Authentication (2FA). While Gates’ vision hasn’t come to fruition as quickly as expected (passwords are still very much alive), there has been a surge in the awareness and adoption of 2FA in recent years.
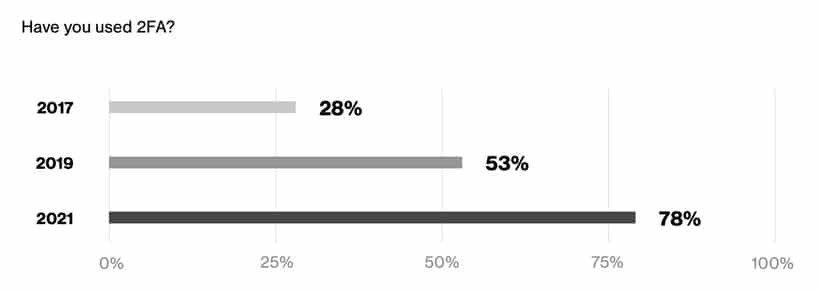
According to Duo Labs’ 2021 State of the Auth report, which surveyed users in the US and UK, 78 percent of respondents had used 2FA. This figure had jumped from 53 percent just two years prior. The most common type used was SMS authentication, at 85.2 percent. Meanwhile, just 8.1 percent relied upon a hardware token.
19. Employees at 57% of businesses use MFA
According to LastPass, 57 percent of global businesses have employees who use multi-factor authentication. This figure is 12 percent higher than in 2018. The study also found that some countries are more likely than others to use MFA, with Denmark, Netherlands, and Switzerland being the most prominent users.
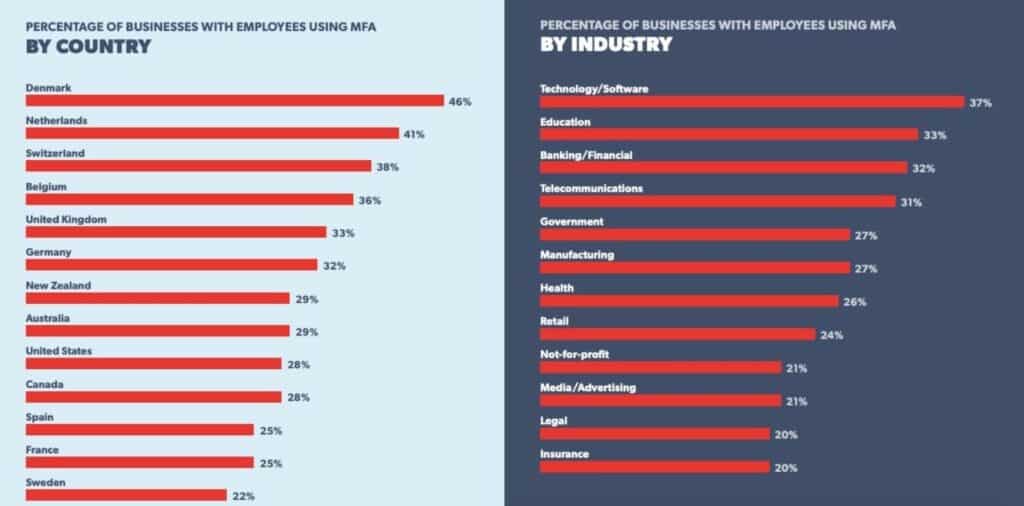
Usage rates depend on industry and company size too. As expected, technology and software companies are 2FA trailblazers. They are closely followed by the education, banking and financial, and telecommunications sectors. Larger companies are more likely to have employees using MFA than smaller organizations.
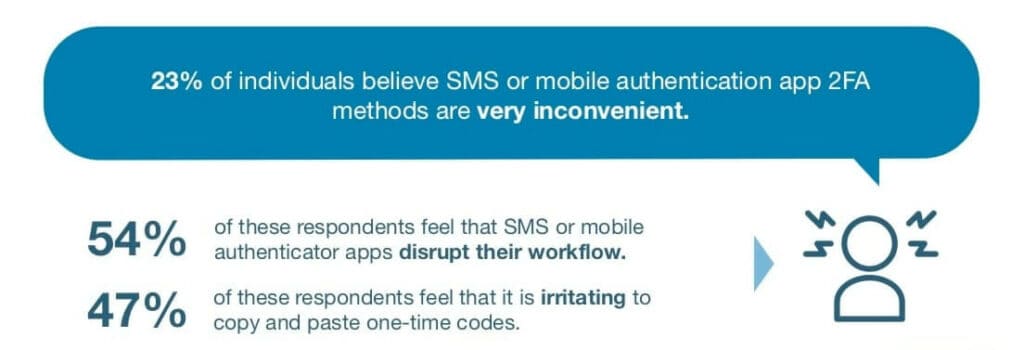
20. 2FA still has issues to contend with
According to the Ponemon Institute report mentioned above, there are complaints about 2FA, which could explain why adoption rates aren’t growing even quicker. 23 percent of users find 2FA methods involving mobile authentication apps or SMS to be inconvenient. More than half (54 percent) of these feel they interrupt workflow and almost half (47 percent) are irritated by having to copy and paste temporary codes.
21. Mobile apps boost employee password manager adoption rates
LastPass’s study showed that the rollout of user-friendly mobile apps is encouraging employees to use password managers. Almost a quarter (23 percent) of employees access their password manager vaults on their phones.
22. Regulations are prompting increases in MFA adoption rates
As LastPass points out in its report, regulations such as the EU’s General Data Protection Regulation (GDPR) and the Notifiable Data Breaches (NDB) scheme in Australia are changing the way businesses deal with data and may be responsible for things like better password security and more widespread adoption of MFA.
For example, it is now mandatory for companies under the jurisdiction of the GDPR to disclose data breaches in a timely manner. To support compliance, hefty fines have been issued. One example was Google’s €50 million fine in January 2019 over a user consent matter. And in 2021, an even bigger fine of €746 million was issued to Amazon for non-compliance.
While LastPass can’t directly correlate data to the GDPR rollout, it notes that significant increases in MFA adoption rates in many EU countries are likely tied to the regulation.
23. MFA adoption in Australia increased almost five-fold in one year
LastPass notes that since the introduction of Australia’s NDB scheme, the number of reported breaches increased from just over 100 to almost 1,000. What’s more, the adoption of MFA by businesses in the country increased dramatically from six percent to 29 percent.
See also: Best VPN for Australia
24. Just over half of users know what password managers and 2FA are
Google found that only 55 percent of polled users could correctly define the terms “password manager” and “two-step verification.” Somewhat more concerning is that only 60 percent of users could correctly define the term “phishing” and a mere 32 percent knew what all three terms meant.

25. Younger people are more likely to use 2FA
There is a generational divide when it comes to account security. While both younger and older generations view online security as important, they tend to take slightly different approaches. One example, according to Google, is that 16–24 year-olds are more likely to use 2FA and regularly install application updates. That said, they are less likely to change their passwords regularly or have knowledge of basic security terms.
26. Older people are more likely to use a different password for each account
While they might not be as quick to use 2FA or install application updates, it seems that older people are more likely to be savvy when it comes to password use. Google found that those in the 50+ age range are more likely to use different passwords for their online accounts and view security software updates as very important. That said, they are less likely to use password managers or set up recovery methods on their accounts.
27. 34% of people use a password manager
According to the Verizon 2020 Data Breach Investigations Report, 506 of the breaches studied involved malware. The most prominent type of malware observed was password dumper malware which was involved in almost 40 percent of malware-related breaches. Password dumpers, also known as credential dumpers, are used to steal credentials (usually usernames and passwords) from the victim computer.
Verizon also studied 868 breaches involving hacking. The vast majority (four in five) of these were linked to passwords in some way; they either involved brute force attacks or the use of stolen or lost credentials.
Related:
- How to tell if you’ve been hacked
- Phishing statistics and facts for 2019–2020
- 300+ Cybercrime and Cybersecurity statistics
Tips for choosing and managing passwords
Want to avoid being part of some of the less desirable statistics and trends? Follow these tips to choose secure passwords and keep them safe.
- Choose strong passwords: Select a password that has at least 12 characters and contains a mix of uppercase and lowercase letters, numbers, and symbols. Our password generator and strength checker tools can help.
- Never reuse the same or similar passwords: Use a different strong password for every account.
- Use a password manager: Multiple strong passwords can be difficult to remember but a password manager makes handling them simple.
- Don’t write passwords down: Whether it’s on a sticky note, in a notebook, or in a file on your computer, writing down passwords is simply bad for security.
- Don’t share passwords with others: If you do need to share a password as a one-off, change it as soon as possible.
- Use 2FA where possible: Enabling 2FA on your online accounts will greatly reduce the risk of being hacked.
- Change your password after a data breach: If you discover your information has been breached, you should change your password right away and check that there has been no unusual activity on the account.
- Sign up for data breach notifications: While the relevant company should tell you if your data has been exposed, signing up for a service like haveibeenpwned? will increase your chances of hearing about a data breach before it’s too late.
- Watch out for phishing emails and sites: These use social engineering to steal personal information such as account credentials and banking information.
- Monitor your accounts: Check your online accounts regularly for any suspicious activity.
Password statistics FAQs
How do passwords work?
Passwords work by encrypting data so that only the person with the correct password can decrypt and access it. They are typically used to protect sensitive information, like credit card numbers or personal data. Passwords are usually case-sensitive, meaning that the correct password must be entered with the right combination of upper and lower case letters. Some passwords are also time-sensitive, so they expire after a specific time and need to be renewed. To make a password more secure, it is recommended to use a combination of letters, numbers, and symbols.
Why are passwords important in cybersecurity?
Passwords are essential in cybersecurity because they help to keep data safe and secure. By encrypting data, passwords make it much more difficult for cybercriminals to access and misuse sensitive information.
How do hackers crack passwords?
Hackers can use a variety of techniques to crack passwords. One method is dictionary attacks, which involve using commonly used words or phrases as passwords. They may also use brute force attacks, which involve systematically trying every possible combination of characters until they find the correct one. Another technique is known as rainbow tables, which are pre-generated lists of hashes and associated plaintext passwords that can be used to quickly determine a password’s value if its hash is known. Finally, hackers may use social engineering tactics such as phishing emails or even phone calls to trick people into revealing their passwords. No matter how strong your password is, it’s always important to choose one that you can remember easily, but others won’t guess easily, so hackers will have difficulty cracking it. Additionally, using two-factor authentication and changing your password regularly can help keep your accounts secure.
Can my data be stolen if my password is cracked?
If your password is cracked, your data can be stolen or accessed without authorization. Once inside a system or account, a hacker may be able to access sensitive information such as financial records, passwords, emails, and other personal data. If your password is compromised, then it’s important to take steps to protect yourself and your accounts by changing your passwords, setting up two-factor authentication where available, and monitoring for suspicious activity. Additionally, it’s always important to use complex passwords that hackers cannot easily guess or crack.
