You know about computer viruses, but what about macro viruses? No, macro viruses aren’t bigger viruses. A macro virus bears that name because it is written in the same macro language as the application it infects. The applications most commonly vulnerable to macro viruses are Microsoft Excel and Microsoft Word. However, because Macro viruses target applications rather than the device the apps are running on, they can infect any operating system — not just Windows.
This post looks at how macro viruses work and provides real-world examples. We tell what you can do to avoid macro viruses and how to remove them.
How macro viruses work
Macro viruses typically spread by being embedded in documents and spreadsheets (typically Excel spreadsheets and Word documents). Macro viruses are written in a macro language, which is supported by the applications they infect. A macro language is a simple programming language that enables a user to write and execute macros. A macro is, according to Microsoft, “a series of commands and instructions that you group together as a single command to accomplish a task automatically.”
Usually, a macro is written to make the user’s life easier by executing (usually) redundant tasks quickly, such as inserting a particular table into all the documents created from a specific template and connecting to a database to validate the table’s values. It might take just a few key presses to trigger the macro.
However, a malicious macro won’t make your life easier – quite the opposite. A malicious macro could perform any action that’s supported by the macro language in which it was written. That means things like creating new files, moving text, sending files, inserting pictures or videos, or more destructive things like formatting the hard drive or corrupting your data. A malicious macro could even contact a remote server and trigger the download and installation of malware.
Because macro viruses are embedded within documents and spreadsheets, their attacks typically depend on social engineering. Malicious actors send emails or text messages to prospective victims, including the infected document or spreadsheet as attachments or a URL linking to the infected file. If the user opens the file, they’re dangerously close to a macro virus infection.
I say “dangerously close” because, since 2022, Microsoft Word, Access, Excel, PowerPoint, and Visio block macros in files from the internet. Users can still access them, but must be persuaded to click the “Learn More” button, where they’re presented with information on the dangers of malicious macros, and then given the option to enable them if necessary.
Macro viruses tend to spread because we’re so used to opening remote documents and most users expect macros to be present in spreadsheets — at least within a work setting. And suppose an infected file makes it onto a shared network drive within your organization’s network? In that case, the amount of damage the micro virus embedded in the shared document could be massive.
Also, macro viruses can be configured to run both automatically and silently, making it difficult even to realize you’ve been infected. And, as mentioned above, macro viruses are OS-agnostic, meaning they can infect any operating system that can host vulnerable applications. That’s pretty nasty.
Examples of macro viruses
The Concept virus
The Concept virus is probably the most “famous” macro virus. It first emerged in 1995 and was specifically designed to infect Microsoft Word documents. This was also the first time we observed a virus in the wild spreading by attaching itself to a document rather than an application.
The origins of the Concept virus are unclear. But many believe a Microsoft employee may have created it because it was bundled in Microsoft Office installation CDs (remember, this is 1995). Anyone who installed Microsoft Office from these infected installer CDs would become infected by the Concept virus.
The Concept virus had the potential to cause massive damage, as it would infect any document saved using Windows’ ‘Save As’ functionality. The Concept virus also managed to infect the document templates that ship with the applications, infecting any new document created in the application. Luckily, the virus didn’t actually do much, and many believe it to have been more of a ‘proof-of-concept’ than anything else — giving credence to the idea it originated from a Microsoft employee, as well as a reason for its name. Still, it was very difficult to get rid of it once infected.
The Melissa virus
Four years after the Concept virus, in 1999, the world was introduced to the Melissa macro virus. Like the Concept virus, the Melissa virus could infect the document templates, infecting all subsequent documents created in the application. But beyond that, the Melissa virus was programmed to automatically send the opened, infected document to the first 50 contacts of the unsuspecting victim’s email address book. Needless to say, this virus spread faster than wildfire.
W97M/Marker virus
In 2007, another Microsoft Word macro virus was discovered. W97M/Marker would infect Word templates and documents and disable macro content warnings and virus protection in Microsoft Word. Once installed, the virus would be triggered every time an infected Word document was closed. Infected files would contain the string “<- this is a marker!,” which served as an infection marker for the virus and is also what gave it its name. This macro virus has multiple versions, but all of the different versions work in the same basic way.
macOS macro virus
In 2017, security experts discovered the first macOS macro virus. Though, thankfully, it was stopped before it could do significant damage. The macro was included in a Word document passed along to unsuspecting macOS users through phishing. Opening the compromised Word document would prompt the macro to contact a remote server and trigger the download and installation of malware. By the time the virus was discovered in the wild, the remote server had already been taken down, so security researchers were unable to determine what the exact malware was. However, we know that the macro’s code was derived from a spyware exploit kit, so there’s a good chance the goal of the attack was data theft.
Symptoms of macro virus infections
The symptoms caused by a macro virus infection don’t really differ that much from the symptoms of other computer viruses. But there are some side effects that may signal a macro virus. This, hence, isn’t an exact science, but be wary of the following:
- Your computer is running noticeably slower than usual (a common symptom for any virus, but still…)
- Certain files prompting you for a password to open them when they aren’t actually password-protected
- Your computer saves documents as templates
- Unusual error messages pop up on your screen
How to remove macros viruses in Microsoft Windows
You can use an antivirus program to scan for and remove macro viruses. If your antivirus app has updated virus signatures, it should detect most known macro viruses. But you can also remove macro viruses manually. To learn how to do that, follow the steps below.
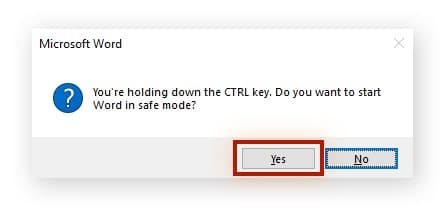
- Launch Microsoft Word in Safe Mode. Safe Mode makes sure that no macros will run, even if they were previously enabled. To do this, hold the left Control key as you click the app’s icon. A prompt will appear asking you if you want to launch Word in Safe Mode. Select Yes.
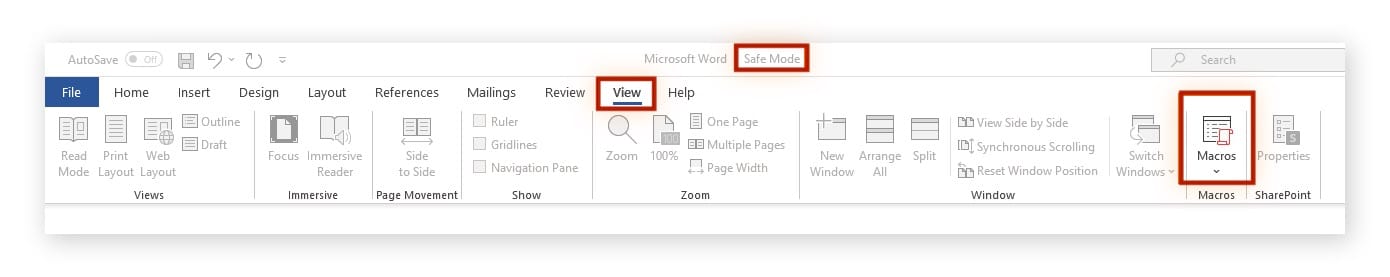
- Click the View menu at the top, and then click the Macros button.
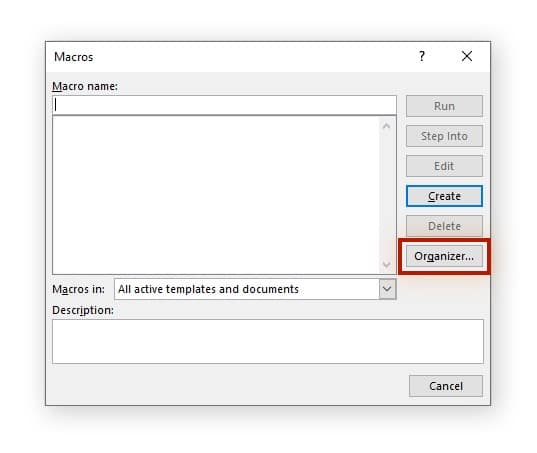
- The Macros window is displayed. Click on Organizer.
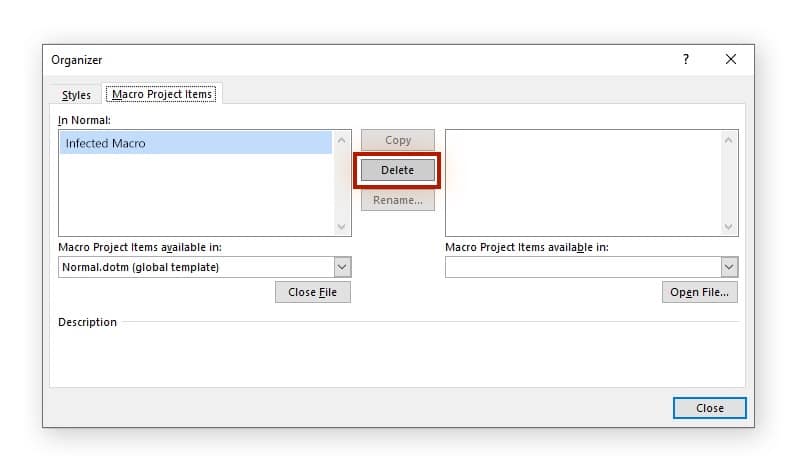
- Select the infected macro and click Delete.
- Close Microsoft Word and restart it normally.
You can also take some simple steps to make sure that all of your Microsoft Office apps are free of malware. From the Start menu, locate Microsoft Office from your list of programs. Right-click it and select Repair. That will remove any macro viruses you may have in your Microsoft Office apps.
Defending against macro viruses
The proper defenses against macro viruses are different for organizations than for users. Though, of course, organizations should make sure their employees follow the security tips for individuals. These measures work in tandem.
For organizations
Educate your organization about the risks of macro viruses
One of the best defenses against online threats is vigilance and mindfulness. Make sure you provide your workforce with adequate training on the different threats they may face and the relevant mitigation measures. That will reduce the odds of your organization falling victim to a macro virus attack.
As macros are blocked by default, individuals should now how and when to unblock them. Unblocking is achieved by selecting the Unblock checkbox on the General tab of the Properties dialog for the file.
Use an Antimalware Scan Interface (AMSI)
Antivirus applications and other security solutions can use AMSI to scan macros and other scripts at runtime to check for validation. AMSI enables pretty much any security solution to have greater visibility into potentially malicious activity and can alert the IT department of any detected high-risk activity happening over the network. While this is a worthwhile step in securing your infrastructure from macro viruses, be aware that attackers are already leveraging publicly available AMSI bypass code to attempt to circumvent its use.
For individuals
- Don’t open attachments in emails without identifying who the sender is and confirming with them that they sent you the email with the attachment. Check with them — ideally through non-email communication — that any included macros are genuine.
- Don’t click links (URLs) in emails unless you’re sure you know who sent the URL and its destination and that they are not being impersonated. And even then, scrutinize the link. Is it an HTTP or an HTTPS link? Most legitimate sites use HTTPS today. And of course, check the link for spelling errors (faceboook instead of facebook or goggle instead of google)? If you can get to the destination without using the link, do that instead.
- Use an antivirus program. And only buy well-reviewed and genuine antivirus software from legitimate vendors. Keep your antivirus updated and perform frequent scans regularly.
- Keep your operating system updated. The latest OS updates contain the latest security patches. You want these.
- Use a firewall – All major operating systems have a built-in incoming firewall, and all commercial routers on the market provide a built-in NAT firewall. Make sure these are enabled. They could protect you if you click a malicious link.
- Never click on pop-ups. Ever. You never know where they’ll take you next.
- If your browser displays a warning about a website you are trying to access, pay attention to that warning and get your information elsewhere. If you clicked a link that was sent to you by email or SMS, it might be sending you to a malicious site to retrieve an infected file. The displayed error message is your friend.
Wrap-up
So that’s the lowdown on macro viruses. They’re somewhat of a unique flavor of virus, as they’re tied to a particular application rather than to a device. But given how ubiquitous the apps it infects are today, macro viruses have the potential to do serious damage. By following the above security tips, for both organizations and individuals, you and your organization can avoid them altogether – or, at the very least, know what to do if faced with a macro virus attack.
As always, stay safe (and virus-free).

