Have you ever been out and about with your phone in desperate need of a charge? Probably. We’ve all been there. And did you happen to stumble upon a public charging station and plug your phone into one of its USB ports? Maybe. Many of us have. But did you know that you could have fallen victim to a juice jacking attack when you did that? Probably not.
We tend to associate charging with electricity rather than data. But when you plug your phone into a USB port, it can technically transfer both electricity and data. And if it can transfer data, it can do things like exfiltrate your personal information and upload malware to your device.
This post looks at what juice jacking is, how it works, and what you can do to steer clear of it.
What is juice jacking?
Brian Krebs coined the term juice jacking in 2011 after he conducted a proof of concept attack at DEFCON. When users plugged their phones into a free (and compromised) charging station, a message was displayed on the kiosk screen:
“You should not trust public kiosks with your smartphone. Information can be retrieved or downloaded without your consent. Luckily for you, this station has taken the ethical route, and your data is safe. Enjoy the free charge!”
And that message illustrates the crux of juice jacking. Juice jacking occurs when a malicious actor has infected a USB port (or the cable attached to the port) with malware. That typically occurs on public charging stations you find in airports, shopping centers, and coffee shops, among other places.
Once your phone is connected and charging, the attacker could download your files and information or monitor your keystrokes on the device. They could also infect your phone by uploading a virus or malware onto it, leading to all sorts of fun stuff.
That’s a high price to pay for a free charge…
How does juice jacking work?
When you connect your phone to your computer via USB, it typically gets mounted as an external drive, and you can access and copy files to and from your phone. That’s because, as mentioned above, your typical USB port isn’t simply a power socket but a data channel as well.
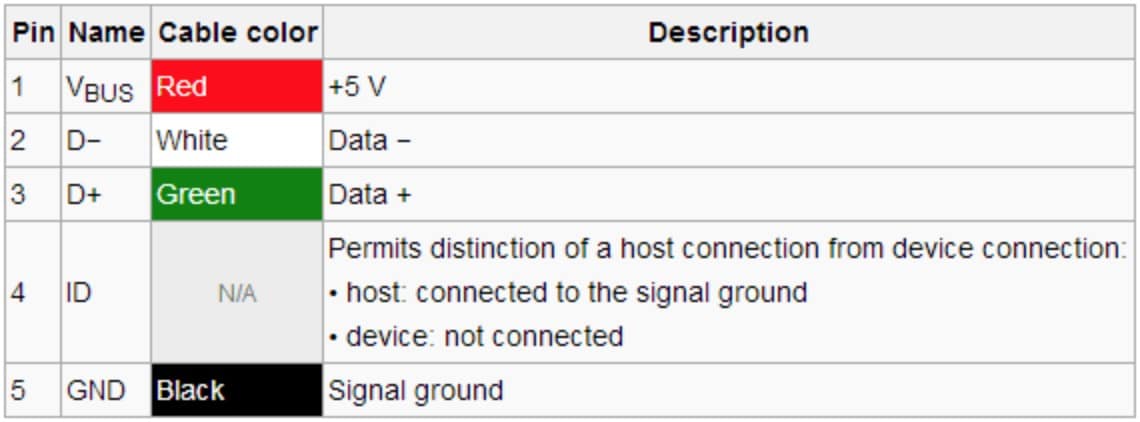
A typical USB port comprises five pins, only one of which is used for charging. Two other ones are used for data transfer, and the remaining two are used as an attached device presence indicator and the ground, respectively.
Source: surnom.com
Usually, the phone’s operating system disables the data transfer capabilities as soon as the phone is plugged in. You may have seen a prompt on your phone asking you to “trust” the computer you’re connected to.
Trusting the host computer enables data transfers. If you choose not to trust the host machine or ignore the prompt, data transfers will not be possible — unless you connect your phone to an infected public charging station.
An infected public USB port can silently enable data transfer modes on your phone once connected. You won’t be prompted and won’t have any indication that this is happening. Once you unplug your phone, you may have had your personal information stolen, and your phone may well be infected with a virus or malware — lucky you.
Types of juice jacking attacks
There are different types of juice jacking attacks, which are outlined below.
Data theft juice jacking attack
We touched upon this payload above. One of the common goals of juice jacking attacks is to exfiltrate unsuspecting users’ personal information. The actual stealing of the data will typically be fully automated and will happen very quickly. And given how intimate we are with our phones today, this could lead to compromised credit cards, bank accounts, email, health records, etc. It’s just not worth a quick charge.
Malware/virus infection juice jacking attack
Once the attacker restores data transfer capabilities, it can flow both ways. That means that they will be able to upload malware or a virus onto your phone. Once infected, your phone will be susceptible to all of the harms associated with malware/virus infections: data loss, loss of functionality, random network connections, device slowdown, installation of other malware, etc.
Multi-device juice jacking attack
A multi-device juice jacking attack is essentially the same as the malware/virus infection attack in that the attacker infects your device with malware. The difference is simply that the malware that was loaded onto your phone is designed to infect the other USB charging ports on the charging station. That scales up the attack and enables the attacker to compromise multiple devices simultaneously, growing their payload.
Disabling juice jacking attack
In a disabling juice jacking attack, the mobile phone is, well… disabled. Once connected to the infected charging port, the attacker will load malware onto the phone, effectively disabling it for the legitimate user while retaining full control over the device for themselves. The same harms as above follow a disabling juice jacking attack, with the added bonus of potentially being used as part of a DDoS attack.
Where are you most at risk of juice jacking attacks?
Anywhere there’s a public USB charging station, there’s a risk of falling victim to a juice jacking attack. But the place where these attacks are the most prevalent is airports. And there are a few reasons for this.
First, to maximize the return on their investment, attackers need a lot of potential targets. Airports are high transit areas, and so they fit the bill perfectly. Also, the airport is one of those places where many will feel it’s critical to have their mobile phone nicely charged, maximizing the chances they would plug their device into the charging station.
Add to that the fact that airports are often stressful and time-pressured environments, which tend to promote quick decisions – such as ignoring sound advice and plugging your phone into a public charging station.
That being said, all public charging stations are a security risk.
What devices are vulnerable to juice jacking attacks?
Most juice jacking attacks end up happening on mobile phones. But that doesn’t mean mobile phones are more vulnerable to juice jacking attacks than other devices. It’s simply because they’re the most used mobile device and hence, the device that’s most likely to need a charge on the go.
But any electronic device that charges via USB is vulnerable. That means mobile phones and tablets, but also smartwatches, fitness bracelets, and even laptops (if they support USB charging – and many do).
How to prevent juice jacking attacks
Avoid public charging stations
The first and most fool-proof way to avoid juice jacking attacks is simply not to use public charging stations. If your cell phone runs out of power, bite the bullet and go phoneless until you can charge it safely. That may be a big ask, but you’re guaranteed success with this method!
Enable and use your device’s software security measures
Mobile devices come with some technical protections against juice jacking and other security threats. If you must use a public charging station, put as many of the following tips into practice:
- Disable your device’s option to automatically transfer data when a charging cable is connected. This is the default on iOS devices. Android users should disable this option in the Settings app.
- Lock your device once connected to the charging station. That will prevent it from being able to sync or transfer data.
- If your device displays a prompt asking you to “trust this computer,” it means you’ve connected to another device, not simply a power outlet. Deny the permission, as trusting the computer will enable data transfers to and from your device. This last point may not be fool-proof, but it’s still better than actively allowing data transfers
You can also turn your device off before charging it. However, many mobile phones (I’ve experienced this with an iPhone) automatically turn on when connected to power. So your mileage may vary. If your mobile phone does not turn on automatically when connected to power, this is an effective safeguard.
Use a wall outlet, a USB battery, or a backup battery
Instead of having no plan B and being stuck using a charging station, unleash your inner MacGyver and have a backup.
- Carry an extra charger and cable with you, and find a wall outlet to charge your device if needed.
- Carry a USB battery or power bank with you. These are cheap, readily available, and many of them can recharge your device multiple times.
- Bring a backup battery with you. If your device has a removable battery, you can simply swap it out with a fully charged one when needed.
All of the above options are better than using a public charging station and will prevent you from falling victim to a juice jacking attack.
Use a USB passthrough device
USB passthrough devices are small devices that look like a USB flash drive. You insert your USB cable into the passthrough device, and it prevents any data from being transmitted over that cable. It does this by disabling the data pins (see above) in the USB cable.
USB passthrough devices, sometimes called USB condoms, are a great way to protect yourself from juice jacking attacks. They’re cheap, work well, and are readily available in electronics shops (primarily online ones).
Alternatively, you can use a USB charging cable that only allows for charging, barring the potential for data transfers by either disabling or not including the data transfer pins in the USB connector. These cables provide the same protection as USB passthrough devices.
Wrap up
Although technically possible, there have been no known real-world cases of juice jacking. Indeed, public concern about the potential for attack appeared to be dwindling until April 2023, when the FBI tweeted the following:
“Avoid using free charging stations in airports, hotels or shopping centers. Bad actors have figured out ways to use public USB ports to introduce malware and monitoring software onto devices. Carry your own charger and USB cord and use an electrical outlet instead.”
The media seized on the tweet as an indication that juice jacking was, in fact, something that was a very real, current risk. However, the truth was more mundane.
Subsequent investigation by the Slate revealed that the FBI’s media team was experiencing a slow-news day, so had decided to re-release part of an old warning from the Federal Communications Commission (FCC) that was originally penned in 2019.
Ironically, the original FCC release actually mentioned that there had not been “any confirmed instances of it [juice jacking] occurring.”
In the four years since then, there appears to have been no new cases either. So, do we need to worry about juice jacking? Probably not. However, just because there haven’t been any documented cases yet, it doesn’t mean it won’t happen. Rather than put your device at risk, we’d still recommend taking the precautions mentioned in this article.


This blog is an eye-opener! 👀 I had no idea about the potential risks of juice jacking until stumbling upon this insightful article. 💡 The detailed explanation of how it works and the practical tips for staying safe are incredibly valuable. 🔒💻 Now, armed with this knowledge, I’ll definitely think twice before plugging my device into public USB charging stations. 🚫🔌 Thank you for sharing this important information – it’s definitely going to change my charging habits for the better! 🙏💪
The article is very informative. I also read that they are low instances of juice jacking occurring. I would think someone would notice if someone were ‘infecting’ an airport’s USB charging port. I would think airport maintenance would know who should be working on ports throughout the facility.
Really helpful. Was only talking about bringing my charging cable with me to charge my phone at the airport tomorrow! WHAT a big mistake that would of been! Thank you for alerting me. There should be more ways to make this issue more aware!
Really helpful. Was only talking about bringing my charging cable with me to charge my phone at the airport tomorrow! WHAT a big mistake that would of been! Thankyou for alerting me. There should be more ways to make this issue more aware!
This seems about like worrying that you’ll be hit by a meteor. The only way that this can happen — at all — is if the bad actor is able to physically tamper with the USB wall outlet and place a card inside it. A standard USB port has no capacity to store programmatic data, let alone an app. Even if they can accomplish that, in order to do anything, they have to bypass security built into the phone. This vector has been recognized since 2011 and no one issuing the current warnings has any credible evidence of it occurring outside of a research environment. This is real henny penny stuff.
I never heared of this before.
Thank you for this great article!
I have made me more aware of an unknown Vector to me.
Really helpful – this was a new threat to me: thank you