Encryption is part of everyday internet life these days. The underlying technologies that encrypt many web pages are provided to us by default and are mostly invisible.
Email encryption hasn’t had such an easy ride. It actually needs us to participate in the setup, and it’s not wildly popular yet due to that complexity. Some companies are working to make email encryption less complicated, which helps increase the adoption rate.
In this article, I’ll explain how to use Hushmail to encrypt your email at rest and send encrypted email to people who otherwise don’t use email encryption.
First thing’s first – you’ll need a Hushmail account to follow along. You can sign up for a 14-day free trial here without needing to supply a credit card.
Email encryption at rest
By default, email is not encrypted as it is sent across the internet. That’s a problem, but since data in transit is harder to capture than data at rest, your trove of emails resting on your email server is an easier target. If a bad guy were to gain access to your email server, they’d normally have full reign to read everything. If you use Hushmail to encrypt your email, it rests on the mail server encrypted so all a bad guy will get is a big bunch of scrambled blobs.
Sending email to people that don’t use encryption
Email encryption typically requires both parties to have the necessary tools to encrypt and decrypt email. While you can set up PGP encryption or something similar on your own for free, it’s just not very convenient, so most people never bother. Hushmail helps solve this problem by allowing you to send encrypted emails to anyone.
To send an encrypted email to someone who does not use encryption you will need to use the Hushmail site rather than an email client. When composing a message, simply click the ‘Encrypted’ checkbox and you’ll be prompted to set a security question and answer.
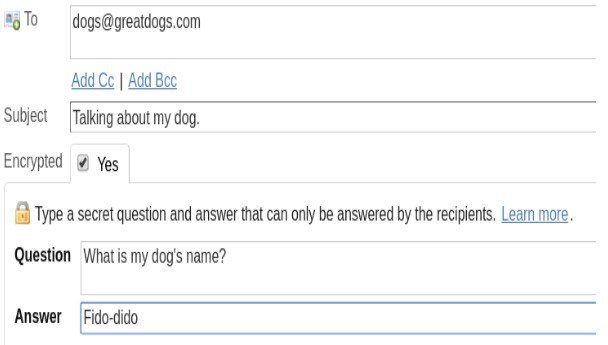
The recipient will get a notification like the one below. When you use Hushmail to encrypt your email, it never leaves the Hushmail servers. Recipients need to visit the Hushmail site, enter the code provided in the notification, and then correctly answer your challenge question.

There’s even an option to reply, which will be sent back to your Hushmail inbox. All without your email leaving the security of the Hushmail servers.
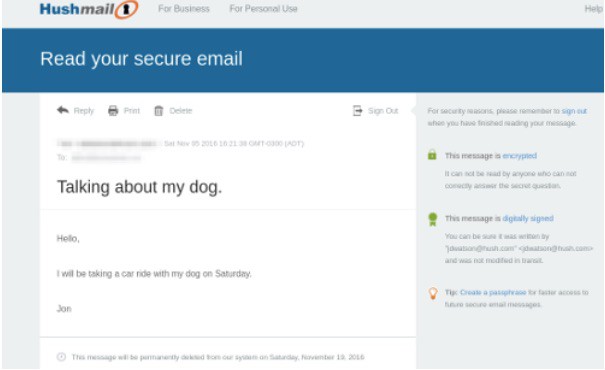
Email client support and two-factor authentication
Along with a very functional web interface, Hushmail also supports POP and IMAP and has a dedicated iOS app. This makes it possible to integrate Hushmail into your normal routine without too much disruption.
Two-step verification is an important step to securing any of your web-based accounts. Hushmail supports two-step verification by either SMS (text) message or the Google Authenticator app. You can set this up on the Security page of your Preferences.
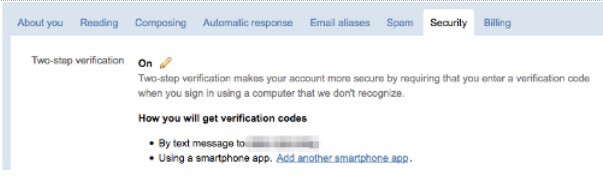
On the same page, but not shown here, is a unique IMAP/POP password you’ll need to set up your Hushmail account on your email client. Due to the two-factor authentication, you can’t use your normal Hushmail passphrase for IMAP or POP.
This article on encrypting and protecting your email has some good tips on apps that can enhance your Hushmail security.
Unlimited email aliases
This is a sleeper feature. It may not seem like you’d have much use for email aliases, but Have I Been Pwned shows almost 2 billion compromised email/password combinations in data breaches. The reason that stealing login credentials is such a big business is that bad guys know we tend to reuse them. There’s big money in stealing logins from unimportant sites like your school or hockey team website because there’s a good chance they’ll also work on more important sites such as your Amazon or PayPal account.
Creating an email alias is as simple as visiting your Preferences page and creating a new alias. I’ve found that the new alias is added instantly and I can receive email at it right away.
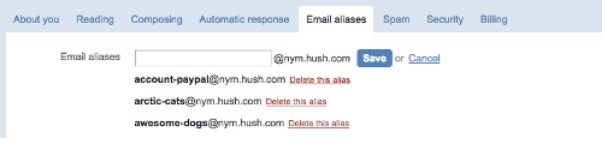
It’s also possible to send email from any of your aliases. A drop-down list box appears on the web interface to allow you to select an alias to send from.
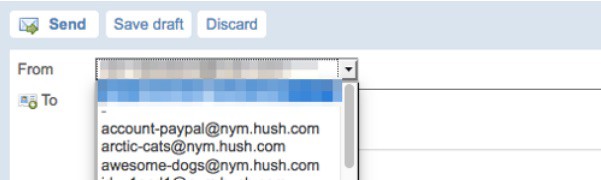
It’s normally not practical to use a different email address for every site, but this email alias feature makes it easy. You may need a Password Manager to keep track of them all, but it’s worth the significant increase in security.
Passphrase storage
Under the normal course of business Hushmail does not store your passphrase. However, it will capture your passphrase and turn over your data if compelled by law. Hushmail defines that as full compliance with any legal order enforceable within the jurisdiction of the province of British Columbia in Canada. It further goes on state that if you intend to engage in activities that could result in an enforceable legal order in British Columbia, then Hushmail is not a good choice for you.
Storing your passphrase is not quite the same as knowing your passphrase. When you sign up for Hushmail, a public/private key pair is generated for you. In order to encrypt, decrypt, or sign your email the web server must know your passphrase. Your passphrase is held in RAM when you log in and is not written to disk in normal circumstances. However, it is theoretically possible for your passphrase to be captured from RAM if the web server is compromised. Hushmail has a nice Security Analysis here which indicates the level of protection it offers for various circumstances.
Hushmail won’t save you from unauthorized access to your account or legal warrants for your email. But it will save you from situations where the mail server is exploited, breached, or otherwise falls into the wrong hands.
Good security requires many layers. There isn’t one thing that will fully secure your email, but there are steps you can take to make it harder. Unless you’re being specifically targeted by someone, the tactic of making your email harder to get than the next guy can significantly add to your security.

