Fitness chain Town Sports International has exposed 600,000 records of members and employees on the web without a password or any other authentication required to access it, Comparitech researchers report.
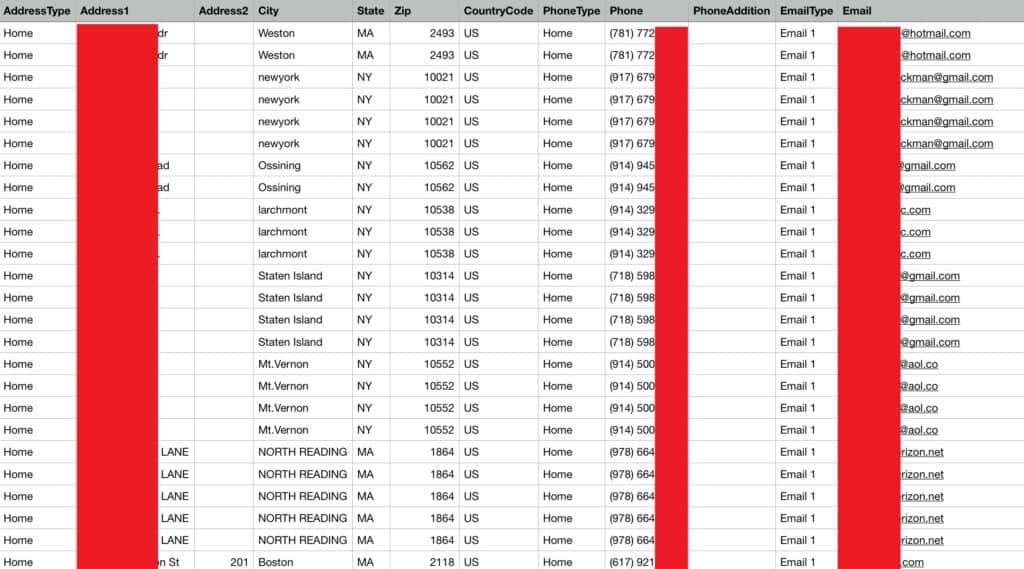
Names, contact info, billing histories, and limited payment information were contained in the unsecured database. Comparitech security researcher Bob Diachenko received a tip from cybersecurity expert Sami Toivonen about the exposure on September 21, 2020. Diachenko immediately notified Town Sports as part of our responsible disclosure policy. He also reached out to Zack Whittaker of Techcrunch to facilitate the process of responsible disclosure with the help of a top-tier media contact. You can read Zack’s take here.
Town Sports International is a chain of gyms, fitness clubs, and spas operating mainly in the northeast United States and has almost 600,000 members, according to its LinkedIn page. Their brands include My Sports Clubs, Around the Clock Fitness, Lucille Roberts and Total Woman.
Town Sports acknowledged the incident but did not reply to Comparitech’s request for comment as of time of writing.
Timeline of the exposure
When Toivonen alerted Diachenko to the exposed database, he said the database was first seen in the wild 11 months ago on November 30, 2019.
Diachenko sent a responsible disclosure notice to Town Sports on September 21, 2020.
The database was secured one day later on September 22, 2020.
We do not know if any unauthorized parties accessed the data while it was exposed, but affected customers and staff could assume as much. Our research indicates unsecured databases can be found, stolen, and attacked within just a few hours of exposure.
What data was exposed?
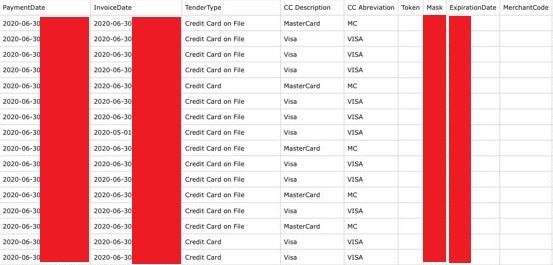
The customer and employee records were stored in an Amazon S3 bucket. Each record contained all or some of the following info:
- Full name
- Street address
- Phone number
- Email address
- Last four digits of credit card
- Credit card expiration date
- Billing history
No account passwords, CVVs, or full credit card numbers were stored in the database.
Dangers of exposed data
In the wrong hands, cybercriminals could use the information stored in the database to scam and phish Town Sports customers and employees. Staff and gym members should be on the lookout for emails, text messages, and phone calls from fraudsters posing as Town Sports or a related company.
Scammers can use the database’s personal information to make the message seem more convincing. Phishing messages usually contain links to phishing pages that look authentic and often identical to the official website, but in fact are copies designed to steal passwords or payment info.
Affected staff and customers could also see an increase in spam to their inboxes.
About Town Sports
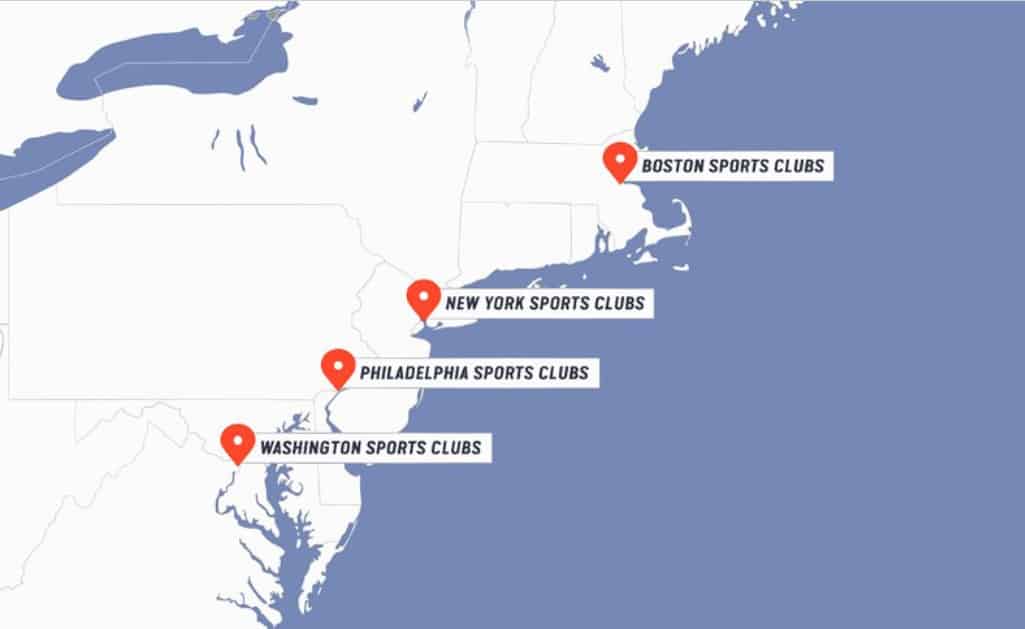
Town Sports International Holdings, Inc is a chain of gyms, fitness clubs, and spas that operates in 14 states.
The company was hit hard by the COVID-19 pandemic, which forced its gyms to shut down for months. Bloomberg reported on September 14, 2020 that Town Sports filed for Chapter 11 bankruptcy.
Why we reported this data incident
Comparitech researchers routinely scan the web for unprotected databases containing private and personal information. When we find exposed data, we immediately begin an investigation to find out to whom it belongs, what information is at risk, who might be impacted, and what the impact might be. Once we track down whomever is responsible for an exposed database, we immediately disclose the incident so the data can be secured as quickly as possible.
Once the data has been secured, we publish a report like this one. Our hope is to make the internet a safer place by alerting people who might be impacted and raising awareness about data exposure.
Previous data incident reports
Comparitech has published several data incident reports like this one, including:
- Prison phone service Telmate exposes messages, personal info of millions of inmates
- Social media data broker exposes nearly 235 million scraped profiles
- UFO VPN exposes millions of logs including user passwords
- 42 million Iranian “Telegram” phone numbers and user IDs were breached
- Details of nearly 8 million UK online purchases leaked
- 250 million Microsoft customer support records were exposed online
- More than 260 million Facebook credentials were posted to a hacker forum
- Almost 3 billion email address leaked, many with corresponding passwords
- Detailed information on 188 million people was held in an unsecured database
- Over 2.5 million CenturyLink customer records leaked