Of the many types of criminal activity that occur on the web, few are more frustrating and difficult to prevent than distributed denial-of-service (DDoS) attacks. These attacks can bring down even the largest websites by overloading servers with more requests than they can handle. Unable to meet the demand of junk requests, servers crash and often require hours to restore.
Norton, in fact, calls DDoS attacks “one of the most powerful weapons on the internet”, and with good reason. Denial-of-service attacks can come at any time, impact any part of a website’s operations or resources, and lead to massive amounts of service interruptions and huge financial losses. DDoS attacks were once a thing of mischief, but data shows they’re increasingly becoming a way for cybercriminals to make money or cause disruption for purposes.
Already, this year, Cloudflare has noticed a staggering increase in DDoS attacks. This is despite 2021 having a relatively low number (though this was likely due to an abnormally high volumer of attacks earlier in the year, as more of us began working from home, combined with a pivot to cryptomining).
Below, we’ve laid out some major stats and facts that highlight how DDoS attacks are transforming and impacting the web.
See also: How to stop a DDoS attack
2018-2024 DDoS stats and facts
Here’s a round-up of some of the most telling DDoS attack statistics:
1. DDoS attacks are still on the rise
Cloudflare saw a 10 percent decline in the number of application-layer DDoS attacks from Q2 to Q3 of 2022. However, there have already been twice as many as last year, with a 67 percent rise in the number of ransom DDoS attacks.
When the coronavirus pandemic forced us all online in Q2 of 2020, we witnessed a huge and long-lasting spike in the number of attacks. With large numbers of us still working at home and remotely, it’s no surprise that we’re still seeing a net increase.
2. Various DDoS attack types on the rise
According to Cloudflare, in Q3 of 2022:
- Ransom DDoS attacks increased by 67 percent year-on-year and 24 percent quarter-on-quarter.
- Online industries received the most application-layer DDoS attacks, recording a 131 percent increase quarter-on-quarter (and 300 percent year on year) rise in the number of attacks.
- Gaming and gambling companies were the most targeted by network-layer attacks, with a huge 405 percent increase in Mirai botnet attacks from Q2 to Q3 2022.
3. Other data shows regionally-specific increases
Data from Yandex and Qrator Labs corroborates research from Cloudflare showing regionally-specific spikes in DDoS attacks:
- 2022 saw the government of Montenegro fend off state-sponsored ransom DDoS attacks, allegedly from Russia. Meanwhile, the Albanian government dealt with a similar situation, though all signs point to Iran as the culprit in this instance
- In Q3 2021, a wave of large-scale DDoS attacks swept across New Zealand.
- Ransom DDoS attacks on VoIP providers in Q3 affected companies in Britain, Canada, and the US.
- In early and mid-July, threat actors flooded the resources of the security agencies of Russia and Ukraine with junk traffic.
- In mid-August, attackers tried to stop users from accessing the web resources of the Philippine human rights organization Karapatan.
- At the end of August, the website of Germany’s Federal Returning Officer was briefly targeted in connection with the September 26 elections to the Bundestag.
4. 2022 was another break-out year for DDoS
The amount of DDoS activity in 2022 was higher than in previous years. Not only that but attacks are lasting longer too. In Q2 of 2021, the average DDoS attack lasted 30 minutes; a year later, they average 50 hours.
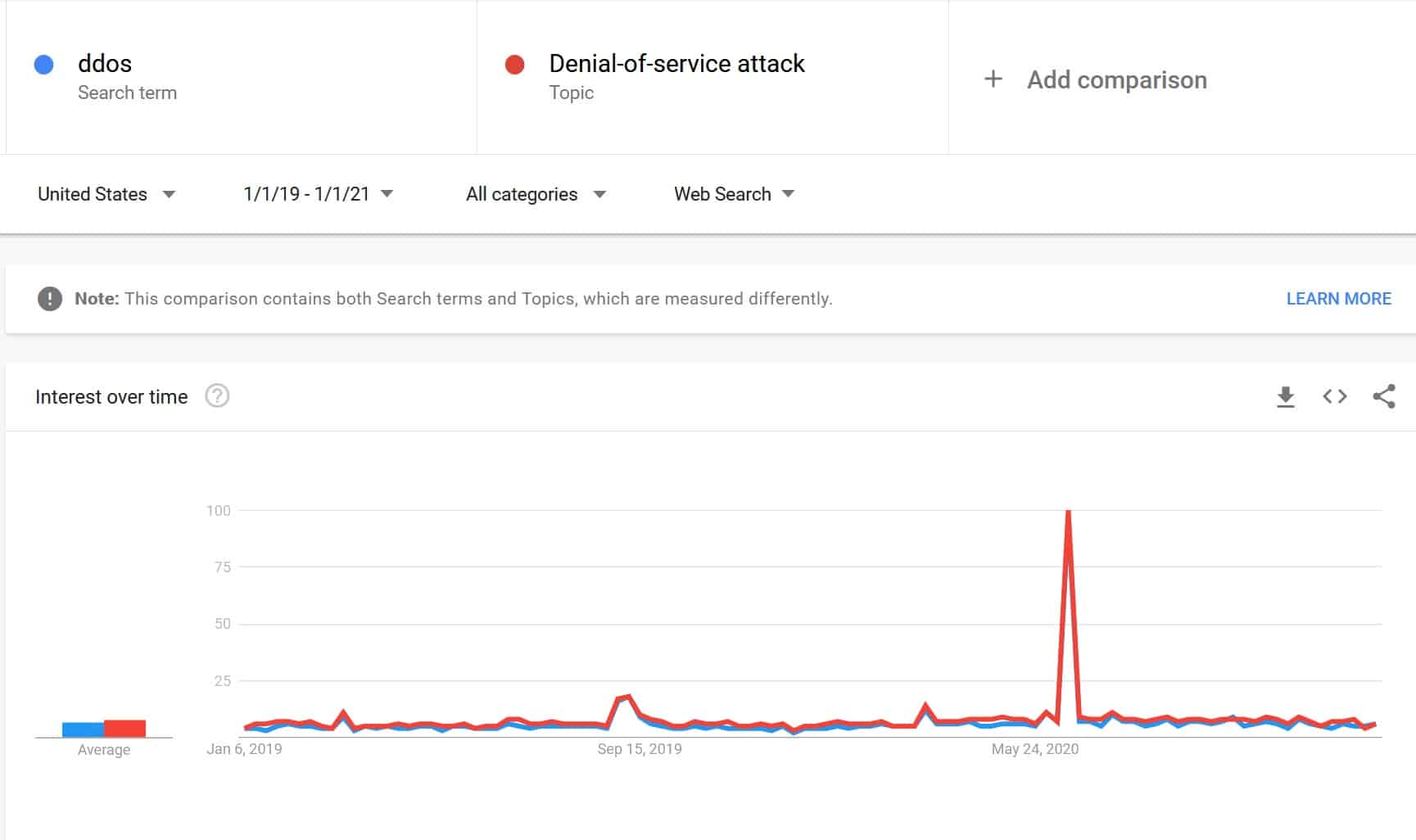
On the plus side, more people are becoming aware of the threats these attacks pose. Although searches for “ddos” and “denial-of-service attack” remained relatively stable, they spiked in June 2020. The reason for this is simple: that’s when Amazon announced that it had shrugged off what was then the largest DDoS attack ever reported.
This record no longer stands, though. In September 2022, Google announced that it had managed to stop a DDoS attack sending 46 million requests per second.
5. DDoS-for-hire sites shut down in 2018, which may have resulted in a decrease in DDoS activity that year
In late 2018, the FBI took down a dozen DDoS-for-hire marketplaces, and in April 2018, Europol shut down Webstresser, the world’s largest marketplace for buying DDoS attacks. At the time it was shut down, Webstresser had over 130,000 registered users.
This activity may have been part of the decline in DDoS attacks witnessed in 2018. However, current data shows that the number of DDoS-for-hire websites bounced back in 2019, which might also play a role in the large increase in DDoS activity in 2019.
6. The longest DDoS attack in history occurred in 2019
Back in 2018, a DDoS attack shattered existing records by flooding their target’s systems with data for 329 hours, or nearly 2 weeks. In Q2 of 2019, though, Kaspersky analyzed commands sent to DDoS networks and discovered an even longer attack, one that had lasted 509 hours.
7. Current data shows most DDoS attacks are decreasing in power
Research shows that the average DDoS attack in Q2 2022 used 5.17 Gbps of data, which is a slight increase over the year before. However, while this is more than enough to scuttle most small-to-medium-sized websites, it’s significantly lower than the Q1 2021 average of 9.15 Gbps.
8. Data also shows DDoS attackers shifting to repeated, short-lived attacks
Even so, DDoS attacks are becoming less about prolonged attacks and more about attack size and frequency. On average, DDoS attacks in Q3 2022 lasted 390 seconds. However, these short burst attacks are often used to test the victim’s defenses.
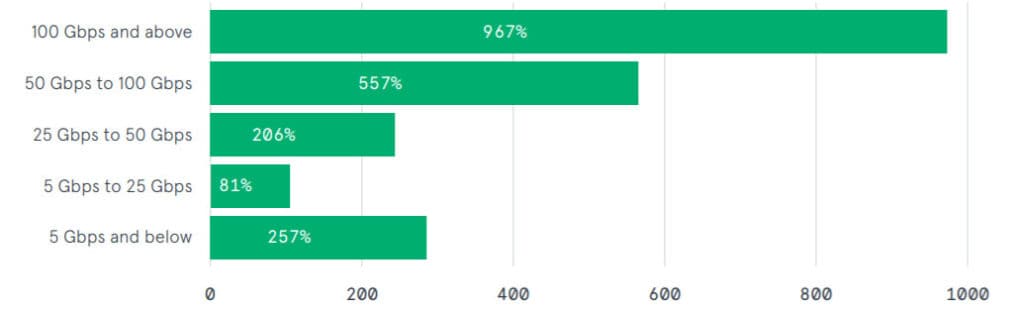
9. Attacks serving over 100 GB/s of data increased 967 percent between 2019 and 2020
Amazon revealed that in Q1 of 2020, it was forced to counter a 2.3 Tbps DDoS attack. This is important for several reasons; first, it’s the largest recorded attack in history, almost four times the throughput of the previous record-holder (587 GB/s).
Also noteworthy is the fact that attacks above 100 GB/s continue to rise, even after a stunning 967 percent growth in 2019 versus 2018. The same year, attacks between 50 GB/s and 100 GB/s also increased 567 percent.
10. DDoS attackers are now using multi-vector attacks more frequently
The methods used to create DDoS attacks are also changing. More than 20% of attackers are using multi-vector DDoS attacks, combining different DDoS attack methods into one, short attack, and then repeating again soon after. In fact, according to Link11, in 2020, one attack used 14 different vectors!
This was an outlier, but we’ve seen this shift play out for years now. Around 52 percent of all attacks in Q1 2019 used 2 or more vectors, with 47% of these using 3 vectors. For contrast, around 11 percent of attacks in 2018 used multi-vector methods, and just 8.9 percent in 2017.
This tactic continues to increase in frequency. In Q3 2021, 78% of DDoS attacks were multi-vector attacks combining several techniques. This is an increase from 62% in Q2 2021.
11. UDP attacks are once again the most common form of DDoS attack
UDP attacks dropped significantly in 2020, being replaced by SYN attacks. However, as of Q2 2022, they’re back on top, accounting for 62.53 percent of all DDoS attacks. SYN is still a significant threat, though, with 20.25 percent. TCP has become much more popular too, at 11.4 percent.
12. Few attacks completely saturate a network’s uplinks
Additionally, a majority of DDoS attacks do not completely saturate uplinks. Corero doesn’t provide specific data in its most recent report, but in 2018, it found that only 0.6 percent of DDoS attacks reached “full pipe” uplink saturation, which is defined as more than 95 percent of usage in the uplink. Of those that reached saturation levels, most (around 95 percent) lasted less than 10 minutes.
13. Credential stuffing attacks are now on cybersecurity radars
Finally, not all DDoS attacks are designed to crash servers. A new type of attack, credential stuffing, is currently targeting many different sites, especially video game services. In this attack, hackers test a load of credentials against their database to verify stolen account information. Although not a DDoS attack strictly by definition, credential stuffing can increase traffic volume on a site and have a similar impact to a DDoS attack. (Source: Neustar)
See also: DoS vs DDoS attacks
14. Despite their distributed nature, DDoS attacks are geographically concentrated
DDoS attacks quite often utilize botnets to send massive amounts of traffic to a single server to overload it with requests. Over 15 million “DDoS weapons”, or infected IP addresses across the world, are currently being used as part of DDoS attacks. The Mirai malware and its many variants are currently the most popular malware used to create botnets for DDoS attacks, although others do exist as well.
15. China is a botnet hub
According to Spamhaus, the country with the most botnets is China, with over 590,000 bots. The US is second-worst, with 376,000 bots, followed closely by India, which has around 350,000.
Some autonomous system number (ASN) operators—mostly ISPs—also have larger numbers of infected IP addresses due to extensive botnet malware. A10 Networks writes that the top 5 ASNs with infected IP addresses are:
- China Telecom
- Charter Communications (US)
- Korea Telecom
- China Unicorn CN
- Chungwha Telecom (China)
DDoS attacks can be launched from anywhere, however, regardless of where the infected computers exist. As one might expect, most DDoS attacks also tend to originate primarily from a select few countries.
16. Hackers in China launch the most DDoS attacks, followed by those in the US and Russia
The majority of DDoS attacks are launched from:
- China
- The US
- Korea
- Russia
- India
17. DDoS records were broken multiple times in the last four years
The security news world went into a frenzy in 2018 after the largest DDoS attack record was broken not just once, but twice in less than one week. The second-largest DDoS attack on record occurred in March 2018 against Github, with a registered 1.3 Terabytes per second (TB/s) of data sent toward GitHub’s servers. The site effectively mitigated the attack.
Amazon also reported suffering the largest DDoS attack on record in Q1 2020. The company successfully managed to mitigate more than 2 Tbps of data, a feat that would be all but impossible for almost any smaller business.
These large-scale attacks have continued since 2018. In 2021, Cloudflare said it blocked a DDoS attack that peaked at just under 2 Tbps, making it one of the largest ever recorded. Also occurring last year, in October, Microsoft successfully defended European Azure cloud users against a 2.4 Tbps DDoS attack, and then in November, it mitigated an attack with a throughput of 3.47 Tbps. The latter is believed to be the largest attack ever reported in history.
18. DDoS attacks are getting more expensive for victims
The costs associated with these attacks are mounting, as well. A Corero survey found DDoS attacks can cost enterprise organizations $50,000 in lost revenue from downtime and mitigation costs. Nearly 70 percent of surveyed organizations experience 20-50 DDoS attacks per month. Although most DDoS attacks don’t succeed, even a few successful attacks can result in hundreds of thousands of dollars in lost revenue per month.
Over 75 percent of businesses surveyed by Corero believe a loss of customer confidence is the worst result from DDoS attacks. That confidence loss can lead customers to flee to competitors, making the overall financial impact completely difficult to determine.
19. Resources in the United States were the most frequent target for DDoS attacks in Q2 2022
Kaspersky’s Securelist blog reports that the US suffered 43.25% of all reported DDoS attacks in Q2 2022. It was closely followed by China and Germany, which were hit by 7.91% and 6.64% of reported attacks in the same period.
20. Kaspersky detected 78,558 DDoS attacks in Q2 2022
Kaspersky continued, stating its intelligence system picked up an average of 923 daily attacks in Q2 2022. The worst day of attacks was June 20, 2022, when it identified 1,815 attacks.
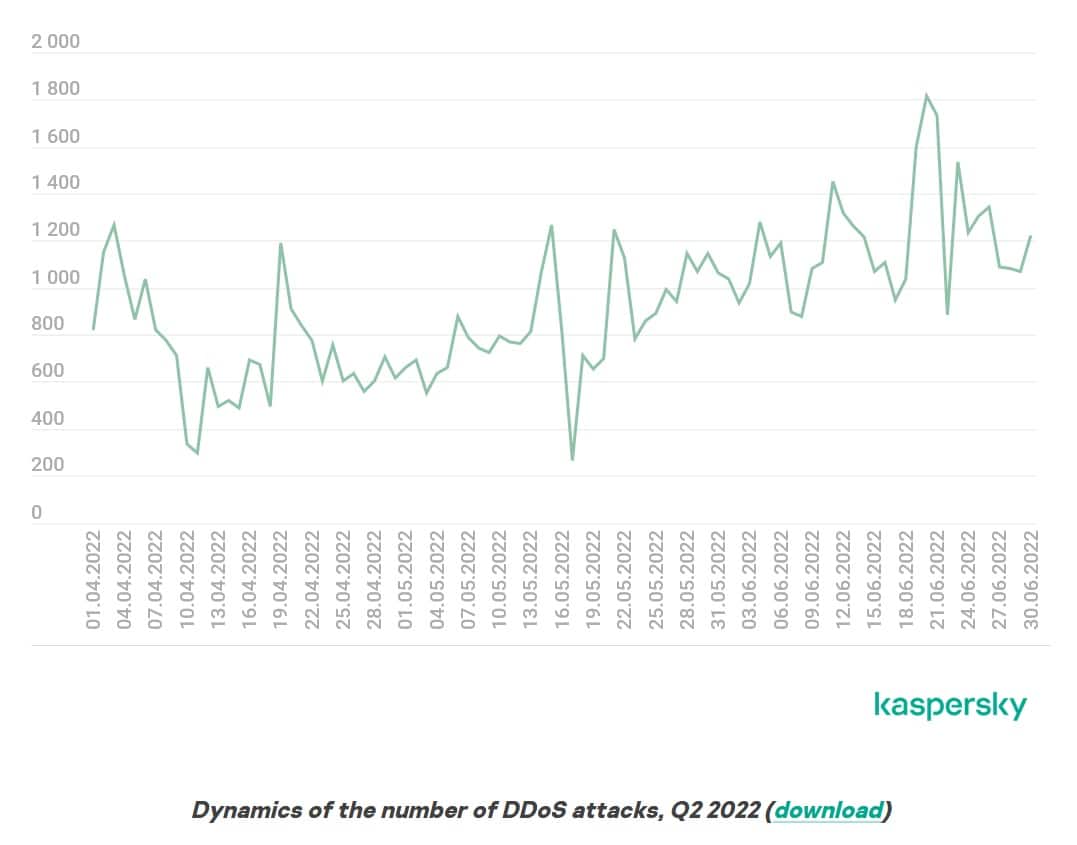
21. The average attack duration in Q2 2022 is very similar to Q1
At just under four hours, the duration and type of attack remain almost unchanged in Q2 2022 versus Q1, Kaspersky reports. However, there was a reduction in the number of long-term attacks, with those lasting 140 hours accounting foir just 0.01 percent of all reports.
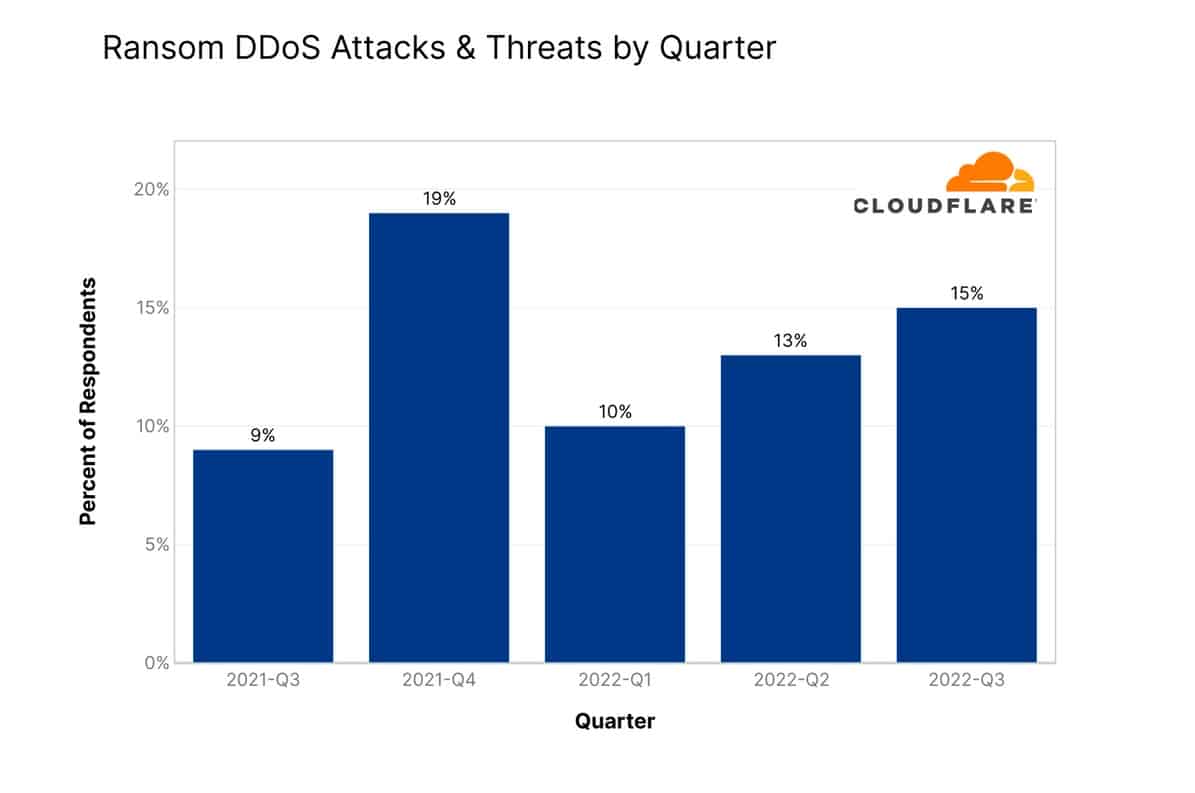
22. Ransom DDoS attacks rose again in 2022
Despite an almost 50 percent reduction at the start of the year, 2022 has seen the number of ransom demands creep upwards steadily. In Q3, the number of ransom requests are almost back to where they were in Q4 of 2021. In September 2022, nearly 25 percent of Cloudflares’ respondents had received a ransom threat.
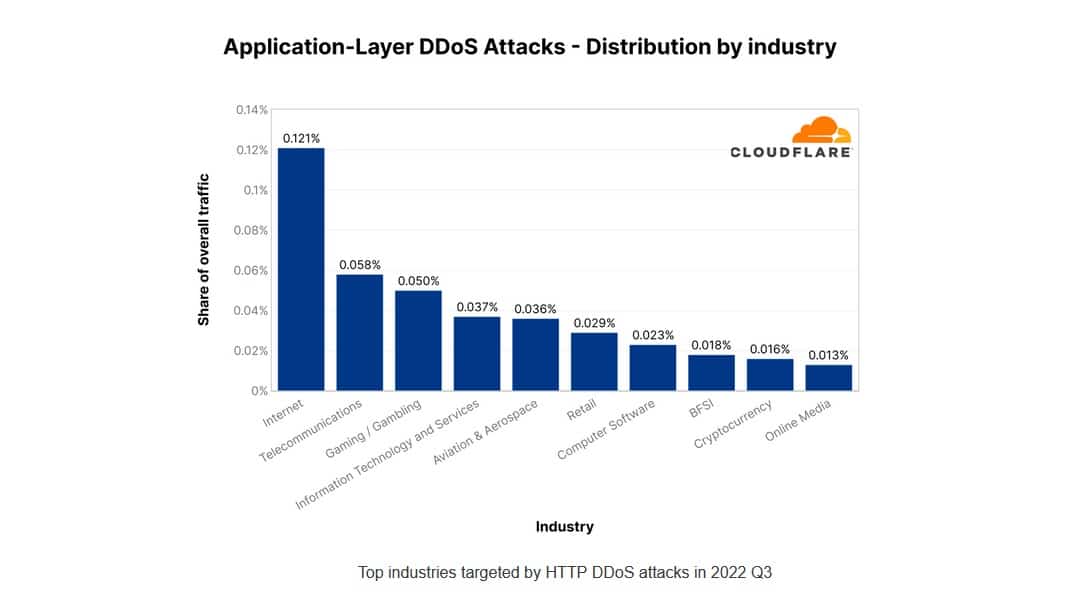
23. Digital services were the hardest-hit in Q2 2022
Although manufacturing had been a popular target in the past, online applications became the most-attractive targets in Q2 of 2022. This industry saw an 300 percent increase in volume year-on-year, likely because of how much damage a DDoS attack can do to a service whose existence requires it to be online at all times.
Telecommunications companies were the second most-popular target. In fact, the number of victims in this industry rose an unprecedented 2,317 percent in a single year.
24. DDoS attack duration down in 2022
Lumen Technologies’ Q4 2022 DDoS report reveals key insights into the nature of DDoS attacks during the period. It was noted that most (nearly 90%) DDoS attacks were short “hit and run” types, typically under 30 minutes, often used to test defenses before larger attacks. Additionally, the report highlighted a significant rise in DNS amplification attacks.
Lumen’s analysis showed an increased frequency of DDoS attacks, with a 22% rise in mitigated attacks compared to 2021. The largest attack handled by Lumen in 2022 was notably large, peaking at 1.06 Tbps. The report also underscores the substantial financial impact of these attacks, with a simulated case study suggesting millions in potential damages from downtime. For more detailed insights, you can explore the full Lumen Q4 2022 DDoS Report.
Notable DDoS attack examples and news
The number of websites impacted by DDoS attacks is on the rise. As “DDoS-for-hire” marketplaces proliferate, it’s now easier than ever for just about anyone to pay cybercriminals to disrupt a website’s operations.
2023
- The pro-Russian hacking group KillNet has been particularly active, focusing on the healthcare sector in the US. In early 2023, KillNet launched over 90 DDoS attacks against US-based health systems, hospitals, and medical centers. Despite the high number of attacks, the impact was reported as minimal and temporary, with no significant disruption to care delivery services. These attacks by KillNet highlight an evolving trend in DDoS attacks, where specific sectors, particularly those critical to public welfare, are targeted. It underscores the importance for organizations in the health sector to review and strengthen their cybersecurity defenses, including implementing web application firewalls and multi-content delivery network (CDN) solutions. More details about these attacks can be found in this StationX report.
2022
- Google repels a Layer 7 DDoS attack, sending 46 million requests per second. For context, in 10 seconds, this attack sends an entire day’s worth of Wikipedia traffic through Google’s infrastructure. All in all, the attack lasted around an hour and likely only stopped because of the financial cost to the attacker.
- North Korea’s internet was downed by DDoS attacks, with the incident lasting for about six hours. At the height of the attack, all traffic to and from North Korea was taken down.
2021
- The Nobel Foundation’s website was hit by a DDoS attack during the award ceremony on December 10, 2021.
- Microsoft mitigates a DDoS attack peaking at 3.47 Tbps, with a packet rate of 340 million packets per second (pps), targeting an Azure customer in Asia. This is believed to be the largest such attack ever reported.
- More than 200 Belgian organizations, including colleges, research centers, and the country’s parliament, are targeted by a massive DDoS attack. Allegedly, this was the largest-scale attack the country has seen, completely saturating the government-funded Belnet ISP’s network.
2020
- It is revealed that Amazon has successfully mitigated the largest DDoS attack ever recorded, with an incredible 2.3 Tbps throughput.
2019
- After launching his first major DDoS attack against video game servers back in 2013, 23-year-old Austin Thompson, also known as “DerpTrolling”, was sentenced to 27 months in prison. Thompson was initially arrested in 2014 after he was doxed. He later pleaded guilty to the Christmas-time DDoS attacks in 2018. (Source: US Department of Justice)
- Security company Imperva announced the largest Layer 7 DDoS the company had ever witnessed come against one of its customers in the video streaming industry. The attack, which was launched primarily from Brazil, utilized a botnet comprised of 400,000 IoT device IPs in the attack, which lasted for nearly two weeks. (Source: Imperva)
- Telegram was hit by a large DDoS attack which the service’s founder, Pavel Durov, suggests was designed to target Telegram during massive protests in Hong Kong. Telegram did not say how large the attack was, but Durov described it as a “state-actor sized” attack, which he stated served 200-400 Gigabytes per second (Gb/s) of junk data. (Source: Security Boulevard)
- In January 2019, a Connecticut man was given a 10-year prison sentence for several DDoS attacks carried out against hospitals in 2014. He was also ordered to pay over $440,000 in restitution. (Source: Boston Globe)
- Two men allegedly part of the hacker collective Apophis Squad were charged with instituting multiple DDoS attacks, including a weeklong attack on encrypted email service Proton Mail. (Source: Court House News)
- A British hacker was jailed for three years in January 2019 after being charged with launching a DDoS attack against Liberian telecom Lonestar in 2015 and 2016. The hacker was hired by an employee from one of Lonestar’s competitors, Cellcom. The attacks were powerful enough to knock out internet access across the entire country and resulted in a loss of millions of dollars for Lonestar. (Source: CNN)
2018
- In October 2018, the then 22-year-old co-author of the Mirai botnet malware was sentenced to six months home confined, 2,500 hours of community service, and ordered to pay $8.6 million in restitution after repeatedly targeting Rutgers University with DDoS attacks. (Source: Krebs on Security)
- In October 2018, Ubisoft’s Uplay service experienced a DDoS attack that disrupted operations for several hours. (Source: Newsweek)
- The Bank of Spain was hit with a DDoS attack in August 2018 that took it offline for several hours. (Source: Bank Info Security)
- In May 2018, the cryptocurrency Verge experienced a DDoS attack that allowed the hacker to acquire $35 million XVG (a cryptocurrency), or $1.75 million based on exchange rates at that time. (Source: Bitcoin Magazine)
- The National Tax Office in the Netherlands was sent offline for 5-10 minutes in January 2018 after a DDoS attack of unspecified size. (Source: Reuters)
DDoS terminology
Digging through DDoS facts might require brushing up on a few key terms. Distributed denial-of-service attacks are highly technical, and you may encounter some unfamiliar terminology while reviewing the latest stats.
- Denial-of-service attack: An attack on a website that sends an overload of traffic (requests) to a web server. A distributed denial of service attack (DDoS) uses multiple compromised computer systems to increase the number of requests that can be made to a server at one time, making server overloads easier to accomplish and more difficult to prevent.
- Amplification: A term used to describe a DDoS attack where the number of requests made to a target’s server is multiplied beyond the original request. There are several ways attackers can do this, including DNS amplification, UDP amplification, and ICMP amplification (Smurf Attack).
- Botnet: A network of computers infected and remotely controlled through a virus or malware program, that is used to make the requests to servers in a DDoS attack.
- Memcached: A distributed memory caching system popularly used in DDoS attacks.
- Mirai: Malware created to target Linux-based IoT devices, including home security cameras and routers. Mirai and its many variants are currently among the most-used malware to create DDoS botnets.
- Gigabytes-per-second and Terabytes-per-second: A measurement of how much data is sent to servers in a DDoS attack, typically denotated as GB/s or TB/s.
- Saturation: A term used for the amount of volume sent to a server during a DDoS attack. Supersaturation occurs when all of a system’s resources are filled with requests from the DDoS attack, completely shutting down the system, while sub-saturation refers to small DDoS attacks that can negatively impact system performance and resources but are not nearly large enough to shut down a server completely. Sub-saturating attacks are increasingly common, often go undetected, and are commonly used as a “smokescreen” for larger attacks.
DDoS attack FAQs
Should I be worried about DDoS attacks as a gamer?
DDoS attacks, which target a specific website or game server by flooding it with traffic, can quickly ruin your gaming experience. The consequences range from slow load times and lagging to complete network outages. That’s why gamers need to have a robust DDoS mitigation solution in place—it should be able to detect and prevent these malicious attacks before they cause any damage. This way, you can enjoy hours upon hours of uninterrupted gaming bliss!
What are the motivations behind DDoS attacks?
DDoS attacks are a real pain, and they can happen for various reasons. Some people might do it to try and make some quick cash by threatening to take down a company’s website or services unless they get paid some kind of ransom. Other times, it might be politically or ideologically motivated, with groups trying to make a statement or raise awareness about something they believe in. There are cases where businesses might try to sabotage their rivals by launching a DDoS attack to disrupt their online presence and services. And unfortunately, sometimes it’s just a matter of someone wanting to cause chaos and damage out of pure spite.