The COVID-19 pandemic brought many industries to a grinding halt and caused genuine financial hardship for millions of people. However, hackers and scammers did very well during this time period. In fact, with the shift to remote working and many reliant on government assistance, we were almost primed to become victims.
One of the things that’s so interesting about this event is that it’s the first of its kind in the age of the internet. That means that we won’t really know the coronavirus’ full impact for the forseeable future. That said, a significant amount of research has already been done.
Below, we highlight more than 40 COVID-19 cybersecurity statistics that illustrate how things have changed, and, arguably just as important, which trends cybersecurity experts were noticing at the time.
1. By June 2020, the FBI was seeing a 75% spike in daily cybercrimes
According to representative Emanuel Cleaver at a June 2020 house meeting: “We are seeing a 75 percent spike in daily cybercrimes reported by the FBI since the start of the pandemic.” That said, this was lower than the spike seen early in the pandemic when cybercrime reports had quadrupled.
Let’s take a closer look at these numbers. The FBI’s annual IC3 reports show that the number of phishing attacks have continued to increase since 2020, but since the pandemic ended, we’ve seen an almost 50 percent reduction in the amount of non-payment scams and the number of violent threats has declined by 90 percent.
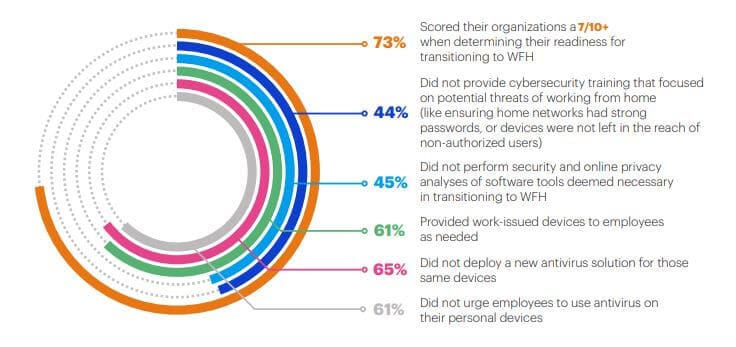
2. 20% of companies faced a security breach because of a remote worker
The Malwarebytes Enduring from home: COVID-19’s impact on business security report published in August 2020 found that one-fifth of companies surveyed had a security breach that resulted from a remote worker’s actions. This isn’t surprising since the report also stated that 18 percent of organizations admitted their employees didn’t consider cybersecurity a priority. Five percent considered employees a security risk as a result of being oblivious to cybersecurity practices.

Other contributing factors include 28 percent of organizations having employees using personal devices for work-related activities, 44 percent failing to provide work-from-home cybersecurity training, and 45 percent neglecting to analyze the security of work-from-home software tools.
The UK’s Action Fraud National Fraud & Cyber Crime Reporting Centre kept tabs on the number of scams related to coronavirus. By February 2021, it found that over 6,000 cases of pandemic-related fraud and cybercrime had been reported, with victims having lost £34.5 million. This was over three times the amount that had been reported by July, 2020. At that point, 2,866 victims had reported a total loss of over £11 million in COVID-related schemes.

And it’s not just direct coronavirus-related scams that were making headlines. Overall, during early UK lockdowns, there was an increase in online shopping fraud, and by June 2020, over £16 million was lost in these schemes. Even measures designed to help struggling citizens ended up being abused, with an estimated £21 billion lost to fraud, the recovery of which is classed as “extremely unlikely”.
4. Details of more than half a million Zoom accounts were sold on the dark web
One of the most popular pieces of work-from-home software during the pandemic was the video-conferencing platform Zoom. Of course, software that’s forced to scale quickly—perhaps without the security advancements to back it up—offers a prime target for hackers. Right on cue, details of 530,000 Zoom accounts were on sale on the dark web by mid-April 2020. Some of these were sold for as little as $0.0020 per account.
In a separate report from Channel Futures, we discovered that by July 2020, there had been a 2,000 percent increase in the number of malicious files that had “zoom” in their name.
This problem hasn’t let up even as the world recovered from the pandemic, though: in September 2022, threat intelligence company Cyble revealed that attackers were still creating fake landing pages and Trojans masquerading as Zoom.
The Mid-Year Update to the 2020 SonicWall Cyber Threat Report revealed the top five COVID-19-related phishing keywords in the first half of 2020. The company analyzed spam and phishing emails that contained terms linked to the pandemic and discovered these were the most common words used:
- Virus: 42.33%
- Corona: 32.92%
- Quarantine: 9.72%
- COVID: 8.77%
- Mask: 6.26%
Unfortunately, even now, health-related phishing terms still do very well. In fact, SonicWall’s 2023 Threat Report noted that the pandemic was a theme in around five percent of all phishing the year prior, with healthcare accounting for nearly 15 percent.

6. The rate of malware attacks followed the rate of COVID diagnoses
An interesting finding from the SonicWall report was that the rate of malware attacks showed some correlation to the rate at which COVID-19 cases were diagnosed. For example, when many protective measures were lifted in May and June, both the number of diagnosed COVID-19 cases and the number of malware attacks started rising.
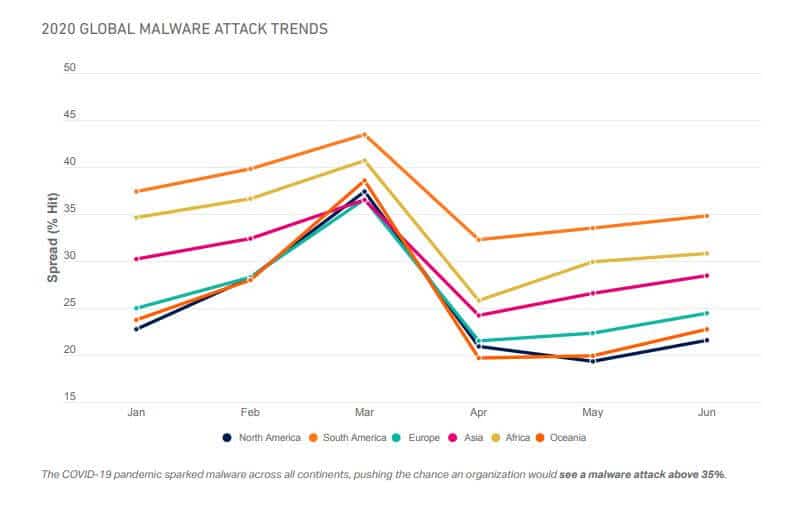
These changes weren’t uniform across every industry, though. Educational organisations saw a huge spike in attacks in September as new school terms began. Likewise, healthcare facilities averaged for than 40 malware attacks each in the fall, just after the first vaccines were approved.
As the UK’s National Audit Office notes in its 2021 annual review:
“From household goods to vaccine appointments, there have been few avenues criminals have not tried to exploit”
The SonicWall report observed at least 20 COVID-19-related threats. These included Corona Anti-Locker Ultimate (data-stealing malware), a Remote Access Trojan (RAT) posing as a COVID-19-related document and distributed via spam, and spam emails purporting to concern a COVID-19 relief package but actually contain a malicious executable file.
8. One COVID-19 vaccine scam email was reported 1,000 times in 24 hours
With the COVID-19 vaccine rollout in full swing, cybercriminals were looking to capitalize on this newer facet of the pandemic. Action Fraud UK released a warning in January 2021 regarding an email scam targeting those waiting to receive the COVID-19 vaccine.
The email, which appears to be sent by the NHS, included a link to an invitation to receive the COVID-19 vaccine. Upon accepting, victims were prompted to enter personal details and banking information. The email was reported more than 1,000 times in a single 24-hour period.
Unfortunately, this was just one in a sea of similar scams. The NAO’s 2021 report mentions discovering 442 phishing campaigns all using NHS branding and dozens of fake NHS apps.
9. In the UK, 28% of incidents related to the country’s coronavirus response
The UK National Cyber Security Centre (NCSC) Annual Review 2020 covers data collected from September 2019 to August 2020. Of 723 incidents the NCSC responded to, more than 200 of them were coronavirus related. In addition, it observed 260 sender IDs which were used (or likely used) in malicious coronavirus-themed campaigns. The NCSC and its partner Netcraft took down more than 15,000 coronavirus-linked malicious campaigns.
Unfortunately, the number of incidents rose again in 2021. In total, there were 777 incidents, of which 20 percent related to vaccines and the health sector. In 2022, it specifically warned that COVID-19 was one of the main themes found in phishing emails, though unlike previous years, it didn’t make exact numbers available.
10. Global organizations observed a 148% surge in ransomware attacks in March 2020
Analysis of data from the VMware Carbon Black Cloud found that the number of ransomware attacks more than doubled in March 2020 compared to February baseline levels. Pre-pandemic, the most heavily targeted sector was retail, but during the period studied, attacks against the financial sector jumped dramatically.
This may have been just the start, as Monster Cloud reported observing a huge 800 percent increase in ransomware attacks by August of the same year.
11. Bots were responsible for nearly half of the “Reopening America” Twitter accounts
It’s not just financial losses that we have to be concerned about, as cyberattacks can threaten a broad range of areas, including politics. A study by Carnegie Mellon University found that bots were responsible for almost half of the Twitter accounts that discussed “Reopening America.”
While many of the statistics provided here paint a rather “doom and gloom” picture of the new cybersecurity landscape, Microsoft has some better news. It found that less than two percent of daily malspam is related to COVID-19 and another report mentions that: “The spike of COVID-19 themed attacks you see above is barely a blip in the total volume of threats we typically see in a month.”

13. There was a 40% percent increase in the number of unsecured RDP machines
The remote work environment saw a huge increase in the prevalence of unsecured Remote Desktop Protocol (RDP) machines as reported by Webroot via Channel Futures. According to the report:
With unsecured RDP, cybercriminals will use brute force to gain complete control of the machine. Unsecured RDP isn’t new, but during the pandemic, the attack area surface is only continuing to grow.
Thankfully, the number of RDP attacks dropped by 89 percent in 2022. Eset posits that this is based on several factors including the shift away from remote working and more robust security systems in offices.
14. 2020 saw a surge in attacks exploiting remote access product vulnerabilities
Given the above figures, it’s no surprise that there were huge increases in the number of attacks against various remote access products. According to the Check Point Cyber Security Report 2021, Citrix attacks surged by a whopping 2,066%, Cisco attacks went up by 41%, VPN attacks spiked by 610%, and RDP hits increased by 85%.
15. The number of brute force attacks grew by 500%
Research by Kaspersky found that by mid-April 2020, the number of brute force attacks observed per day was more than six times pre-pandemic figures. Pre-COVID, they were looking at around 200,000 attacks per day in the US, but on April 7th, that number skyrocketed to over 1.4 million, before falling slightly over the next few days. This pattern was seen in countries across the globe with increases coming in waves in many regions.
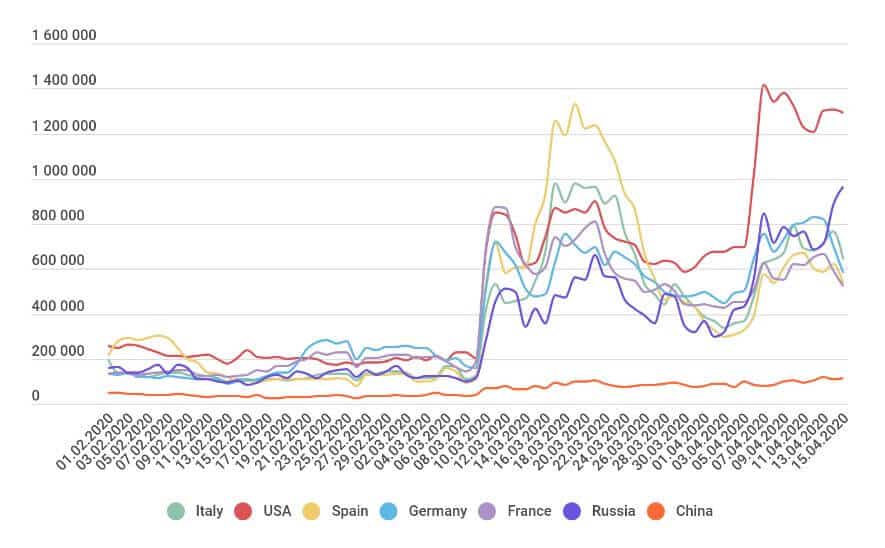
A later report released in March 2021 revealed that the number of brute force attacks reached 3.56 billion globally in 2020.
A mid-March study from ZDNet found that thousands of domains related to coronavirus were being created each day. While that’s perhaps unsurprising given the relevance of these domains, a concerning figure around their legitimacy arose: a whopping 90 percent of new coronavirus domains were found to be scammy.
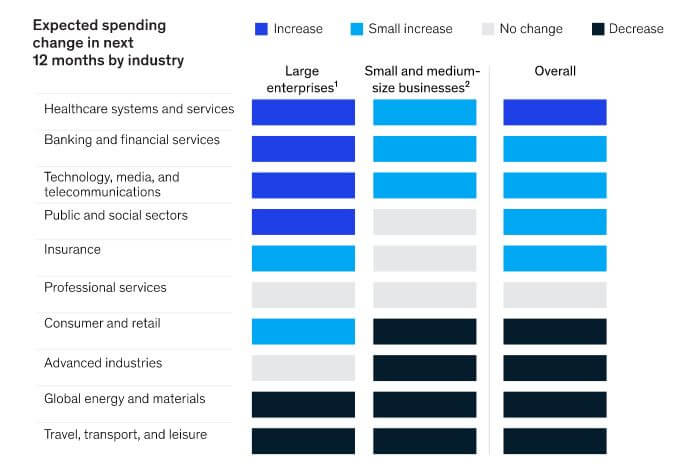
17. Healthcare organizations of all sizes were expected to increase cybersecurity spending
A McKinsey & Company article published in July 2020 details how the COVID-19 crisis shifted cybersecurity budgets and priorities. Many industries were expected to increase spending, including healthcare, finance, tech, public and social sectors, and insurance, all of which should see at least small increases across organizations.
That said, industries that didn’t fare well during the pandemic expected that cybersecurity budgets would decrease overall. These include retail, advanced industries, energy and materials, and travel and leisure.
Unfortunately, while the worst of the pandemic is over, healthcare organizations remain an attractive target. In 2022, Checkpoint found that 89 percent reported at least one cyberattack, which led to an average loss of $4.4 million. Additionally, in 2023, 59 percent of cybersecurity professionals stated that their team was understaffed (ISACA State of Cybersecurity 2023).
18. Most companies are concerned about COVID-19’s impact on cyberattacks
The World Economic Forum (WEF) published an insight report titled COVID-19 Risks Outlook: A Preliminary Mapping and Its Implications in May 2020. It detailed concerns companies have about how the post-pandemic world might have changed. Interestingly, the third-most worrisome area (and the top tech-related concern) was “Cyberattacks and data fraud due to a sustained shift in working patterns” with more than 50 percent of respondents listing this as a primary concern.
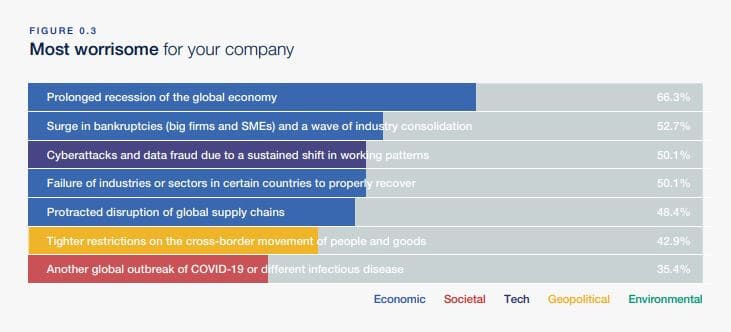
Google blocks around 100 million phishing emails each day, and in April, 18 million of those were related to COVID-19. And that’s not even counting the 250 million daily Coronavirus-centric spam messages it observed.
What’s more, 2020 was a record year for phishing sites, with Google detecting more than two million phishing sites by November 2020.
20. 54% of Britons who lost income due to COVID-19 were targeted with cyber scams
As if losing part or all of your income isn’t bad enough, a June Citizens Advice report tells us that more than half of British adults whose income was impacted during the pandemic were contacted by scammers. Overall, over one in three adults were contacted, including 45 percent of people with a long-term illness or disability.
21. The UK’s “test and trace” program was reportedly launched in violation of the GDPR
The UK’s test and trace program was rolled out in May 2020, but multiple news outlets reported in July that the program had violated data protection laws. Under the General Data Protection Regulation (GDPR), a project such as this that processes personal data should have undergone a Data Protection Impact Assessment (DPIA), which the “test and trace” program apparently didn’t.
See also: The Covid-19 tracking app and privacy
22. Authoritarian governments were expected to use the pandemic to deploy surveillance technologies
A Cyber Threat Bulletin issued in June by the Canadian Centre for Cyber Security included this key judgment:
We assess that it is very likely that authoritarian governments will use COVID-19 as a justification to procure and deploy surveillance technologies against their own citizens and expatriates residing in Canada or Canadians living abroad.
It goes on to suggest that telecommunications surveillance products (such as mobile applications designed to map and analyze virus spread) could potentially be leveraged by authoritarian governments to covertly target users.
23. Interpol called the increase in the number of cyberattacks alarming
In an August 2020 report, Jürgen Stock, Interpol Secretary General, said:
Cybercriminals are developing and boosting their attacks at an alarming pace, exploiting the fear and uncertainty caused by the unstable social and economic situation created by COVID-19.
Interpol provided the example of one of its private-sector partners that had detected a huge number of COVID-19-related threats in the first four months of the year, including more than 900,000 spam messages, 737 malware-related incidents, and 48,000 malicious URLs.
In its 2021 report, Interpol mentioned that it had shut down over 113,000 fake online pharmacies and arrested 80 suspects in a multi-national fake vaccine scam.
24. COVID-19 exposed significant gaps in IT disaster recovery planning
The VMWare Carbon Black Global Threat Report released in June 2020 surveyed IT professionals from a range of industries across the globe. It found that 84 percent of respondents reported gaps in IT operations, with 35 percent noticing very significant gaps in IT operation disaster recovery planning, including rollouts of hardware and software. What’s more, 70 percent found gaps in their cybersecurity threat visibility.
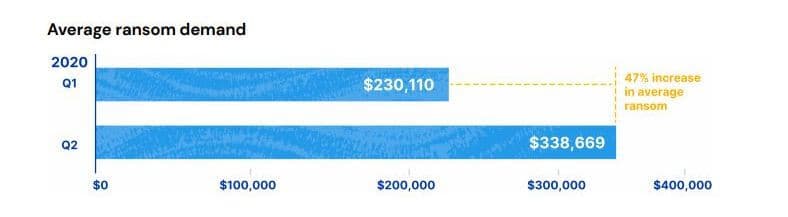
25. Q2 2020 saw a 47% increase in ransom demands
A Coalition report focused on small to mid-size organizations found that between Q1 and Q2 2020, the average ransom demand increased by 47 percent to $338,669.
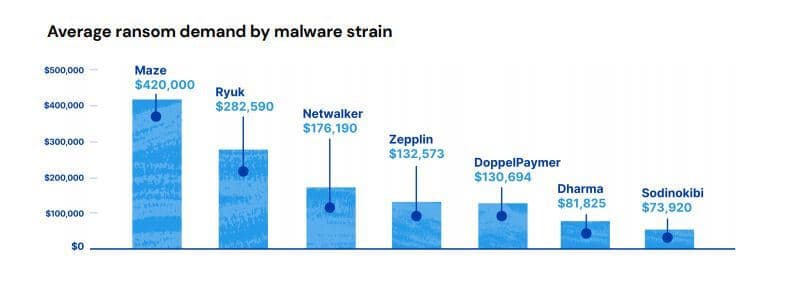
The most costly ransomware is Maze with an average ransom of $420,000, followed by Ryuk ($282,000) then Netwalker ($176,190).
26. 85% of CISOs sacrificed cybersecurity for a swift change to remote work
Netwrix’s 2020 Cyber Threats Report offers findings from a survey of 937 professionals. The vast majority of CISOs surveyed admitted to having cut corners on cybersecurity to help their organizations quickly pivot to a remote work model. To make matters worse, 58 percent said that employees had ignored cybersecurity guidelines and policies.
Its 2023 Hybrid Security Trends report shows that every major issue (including security team understaffing, inexperience, difficulty securing endpoints, and poor workflows) had become less common than in 2020. However, a full 30 percent of organization still say that they lack the budget they need.
27. The number of IT professionals concerned about VPN exploitation more than tripled
Based on the last statistic, it’s no surprise that Netwrix discovered a whopping 85 percent of IT professionals worried about VPN exploitation during the pandemic. This is 59 percentage points higher than the pre-pandemic figure.
28. Almost a quarter of companies increased cybersecurity spending as a result of the pandemic
Another Netwrix study found that 24 percent of companies increased their cybersecurity and cloud security spending during the pandemic. 36 percent kept spending the same but adjusted their priorities, while 21 percent kept spending and priorities the same and 11 percent lowered their cybersecurity spending.
These figures varied depending on company size with large companies more likely to increase spending and small companies more likely to keep spending the same.
In 2022, 49 percent of companies asked said that their cloud security budget had increased that year. In fact, on average, most dedicated almost a third of their total security budget to protecting data stored on the cloud. In 2023, however, 30 percent of those surveyed said that their organisation lacked the budget to properly protect itself against digital threats.
29. More than half of companies reported an increase in phishing attacks by mid-May 2020
It didn’t take long for phishers to start trying to take advantage of remote workers. By mid-May, Barracuda was reporting that 51 percent of companies had seen an increase in phishing attacks due to having employees work from home. What’s more, that same portion of respondents admitted employees weren’t trained in cyber risks as they relate to remote working, and 46 percent say their web applications may not be secure. Not helping matters is that a large portion (40 percent) of employers had cut their cybersecurity budgets in an attempt to lower costs.

30. Amazon Web Services hosted the most risky or malicious domains
A May 2020 COVID-19: Cloud Threat Landscape study by Palo Alto Networks analyzed over a million “newly observed hostnames” (NOHs) with keywords related to the pandemic. More than 86,600 of these were classed as “malicious” or “high-risk,” and almost 3,000 of those were hosted in public clouds. Of those, 79.2 percent were hosted by Amazon Web Services, 14.6 percent by Google Cloud Platform, and 5.9 percent by Microsoft Azure.
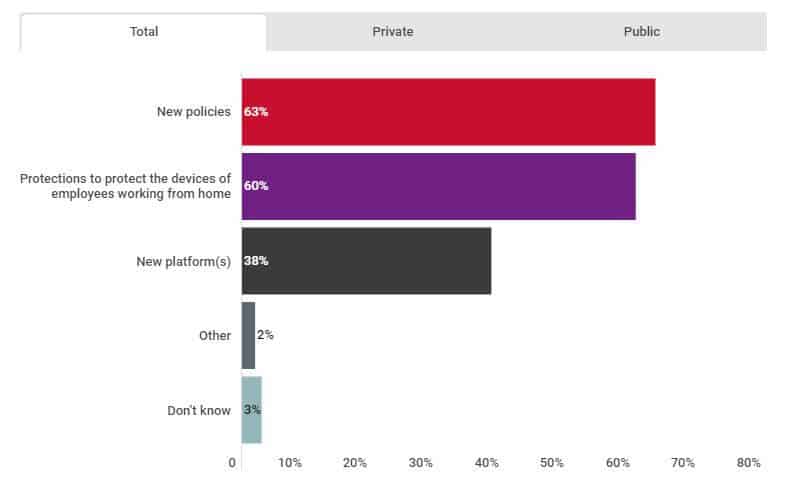
31. Almost two-thirds of Canadian organizations implemented new security policies
The 2020 CIRA Cybersecurity Report asked Canadian organizations what kinds of cybersecurity protections they implemented in response to COVID-19. Almost two-thirds (63 percent) implemented new policies and 60 percent added protections for work-from-home employee devices. Over one-third (38 percent) adopted new platforms as part of their cybersecurity protection strategy.
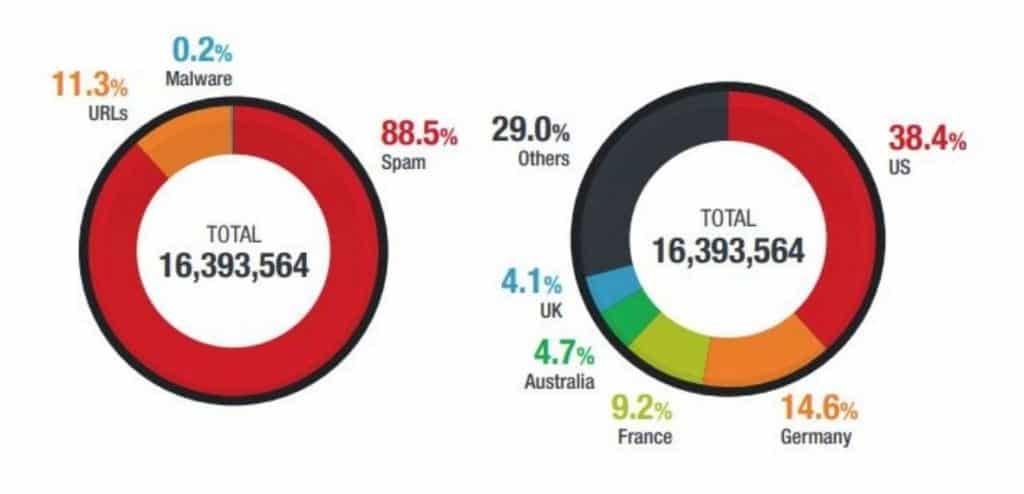
The Trend Micro 2020 Annual Cybersecurity Report saw a whopping 16 million threats related to COVID-19 in 2020. The vast majority of these (88.5 percent) were email threats, 11.3 percent were malicious URLs, and 0.2 percent were malware.
The report also showed where threats originated. The largest portion (38.4 percent) came from the US, followed by Germany (14.6 percent), France (9.2 percent), Australia (4.7 percent), and the UK (4.1 percent).
33. UK businesses are beginning to get complacent about security again
The British government’s 2023 Cybersecurity Breaches Survey found that in fewer businesses were following basic security principles than in years prior. For instance, just 70 percent had a password policy in place, which was five percent down from the year prior, and nine percent down from 2021.

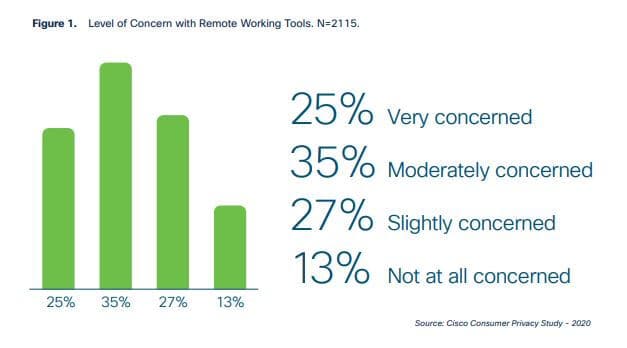
34. Most employees don’t trust remote working tools
The Cisco 2020 Consumer Privacy Survey revealed a distinct lack of trust in the tools people are using for remote work. Only 13 percent of people were not at all concerned with remote working tools. The remaining were either very concerned (25 percent), moderately concerned (35 percent), or slightly concerned (27 percent).
On the plus side, citizens are becoming interested in their data and who can access it. Cisco’s 2023 report (PDF) showed strong support in 11 countries for national privacy laws such as GDPR and Australia’s Privacy Act, with 86 percent of respondents in India thinking the Personal Data Protection Bill had a positive impact.
35. Two out five see data privacy as more important than before
According to Cisco’s 2022 report, the major privacy concern (cited by 31 percent) for healthcare, public health, and other related data was that it would be used for unrelated purposes. Other major concerns include the data being shared too broadly (25 percent) or not being deleted once no longer needed (24 percent). Indeed, 40 percent of people agreed that the pandemic has made data privacy more important.
In 2023, a new threat emerged: widespread adoption of AI. 62 percent of people surveyed were concerned about how their data was being used to train AI, with 60 percent saying that their trust had already been eroded by an organisation’s usage of the technology.
While this question was not asked in the 2022 report, it did note that 44 percent of respondents who replied that they cared about data privacy had moved away from a service or company because of their data collection or usage policies. Additionally, its 2023 Privacy Benchmark study found that generally, pro-privacy legislation is positively received, with a 90 percent approval rate in India and a 57 percent approval rate in Malaysia (which was the lowest of any country sampled).
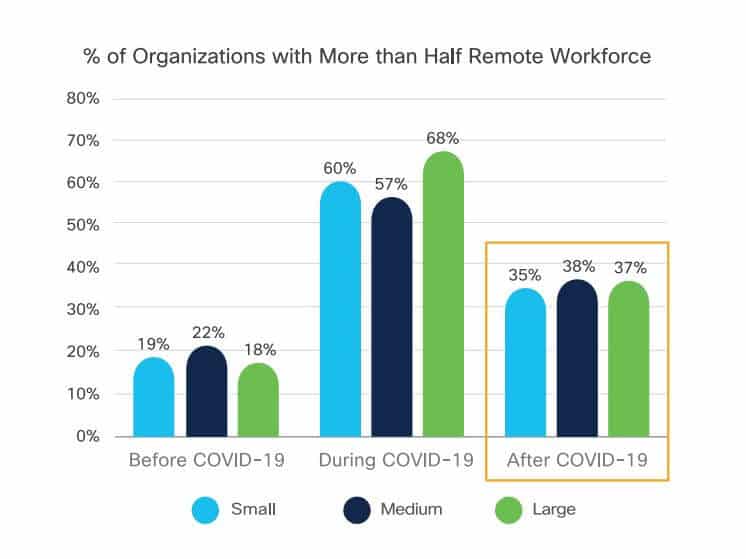
36. More than one-third of organizations set to have a predominantly remote workforce
The Cisco Future of Secure Remote Work Report published in 2020 tells us that post-COVID, 37 percent of organizations will have more than half of their workforce working remotely. While this is lower than the peak figure during the pandemic (62 percent), it’s almost double the pre-pandemic figure of 19 percent.
This switch is viewed positively by workers too. The UK’s Office of National Statistics found that in 2022, 84 percent of employees planned to continue hybrid working, with just eight percent planning to move back to the office permanently, down from 11 percent in 2021.
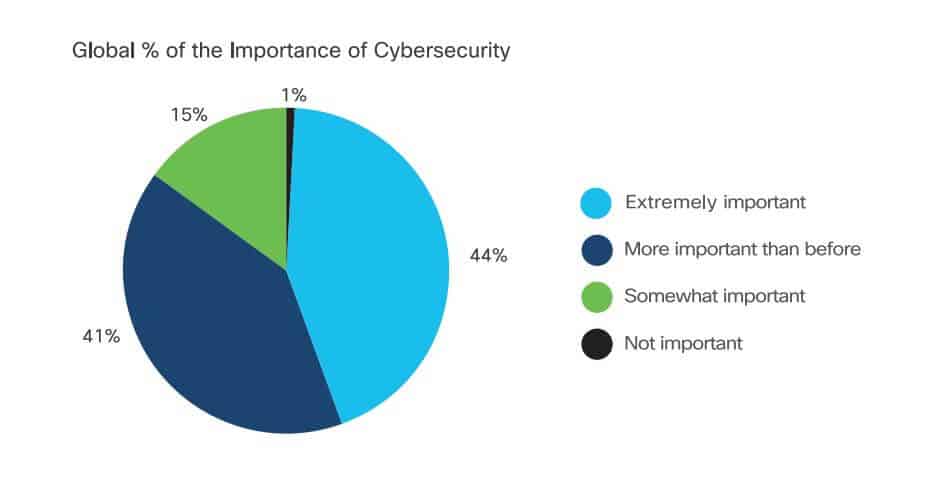
37. Cybersecurity is more important than before
The 2020 Cisco report also tells us cybersecurity has become a main priority for many organizations. Cybersecurity is cited as “extremely important” for 44 percent and “more important than before” for a further 41 percent.
This could have a lot to do with the fact that globally, 61 percent of surveyed organizations had seen an increase in at least 25 percent of cyber threats or alerts since the beginning of the pandemic. This was experienced by most small businesses (55 percent), medium-sized organizations (70 percent), and large enterprises (60 percent).
There are several financially-sound reasons to invest in cybersecurity. Chief among these is reducing the amount of losses from ransomware, scams, and phishing, but as Cisco notes, as of 2023, around 98 percent of managers now report cybersecurity metrics such as audit results and data requests to their company board, with 30 percent reporting two or three.
38. Work computers pose the biggest challenge in cybersecurity protection
The Cisco Future of Remote Work report also reveals some of the biggest challenges organizations face when trying to protect components of their adjusted networks. 56 percent say office laptops and desktops pose a challenge, closely followed by personal (employee-owned) devices (54 percent). 46 percent say customer information is difficult to protect and the same number admit that cloud applications pose a challenge.
These statistics go a long way in explaining why more than half of businesses say that they were only somewhat prepared to shift to a remote work model at the start of the COVID-19 pandemic. A further six percent say they were not prepared.
39. 96% have changed cybersecurity policies due to remote work
The huge majority of organizations participating in the Cisco study said that they had made changes in their security practices to support a remote-work environment. Businesses of all sizes cite changes, including small organizations (93 percent), medium companies (97 percent), and large organizations (97 percent).
40. The top change to cybersecurity policies was increased VPN capacity
Of the organizations that implemented policy changes, increased VPN capacity was the most popular adjustment, implemented by 59 percent of organizations. Other common changes included increased web controls (55 percent) and the use of multi-factor authentication (MFA) (53 percent).
41. Most businesses see lack of employee awareness as a big remote work challenge
So have the changes gone smoothly? Not exactly. According to Cisco, most organizations report challenges with trying to reinforce remote work-related cybersecurity protocols. The main issue faced is lack of employee education and cybersecurity awareness, reported by 59 percent of companies. Having too many tools and solutions to manage and toggle is another big hurdle faced by 50 percent of organizations.
42. COVID-19 data-harvesting malware caused chaos for businesses
The Cyber Global Awareness Campaign 2020 report from Interpol found cybercriminals used data-harvesting malware such as spyware, banking trojans, and remote access trojans to infiltrate networks. Attackers use fake COVID-19 information as a phishing mechanism that fools unsuspecting users to open a link or attachment to inject such malware. As a result, attackers can install botnets, redirect money, and steal data.
43. Insecure remote work environments result in attack spikes
Government restrictions were introduced in 2020 to tackle the spread of COVID-19, meaning many of us had to adjust to home working leading to a sharp rise in technology adaptation. Swissinfo.ch reported in June 2020 that the average cyberattacks for April 2019 were between 100-150, yet in April 2020 this figure rose significantly to 350 cyberattacks in the peak of the pandemic.
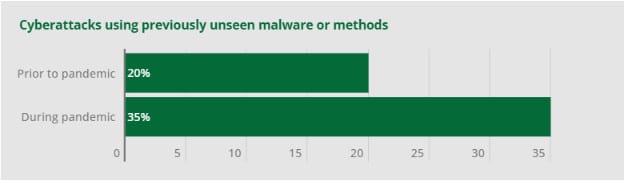
44. Unseen cyberattack tactics increased during the pandemic
In Cynet’s Covid-19 cyberattack analysis report, we saw that cybercriminals are changing up their tactics for attack distribution and types of malware used. To use the shift in remote working to their advantage, attackers have come up with new types of malware to infiltrate networks.
For context, before the pandemic, just 20% of cyberattacks were new unseen variants, whereas this figure rose sharply to 35% during the pandemic. Some of the attacks that have arisen come in the form of vishing (voice phishing) and threats via SMS. Attackers are utilizing machine learning which enables malware to adapt to its environment to remain undetected by cybersecurity detection mechanisms.
Unfortunately, though, despite an increasing awareness of online scams, signs of phishing, and spam messages, people remain vulnerable to attacks from unexpected sources. In 2021, cybercriminals allegedly sent potential victims packages in the mail, claiming to be from the US Department of Health and Human Services. Inside, they found a USB stick claiming to offer COVID-19 guidance. In reality, this USB would automatically install tools that made it easier for criminals to remotely install ransomware.
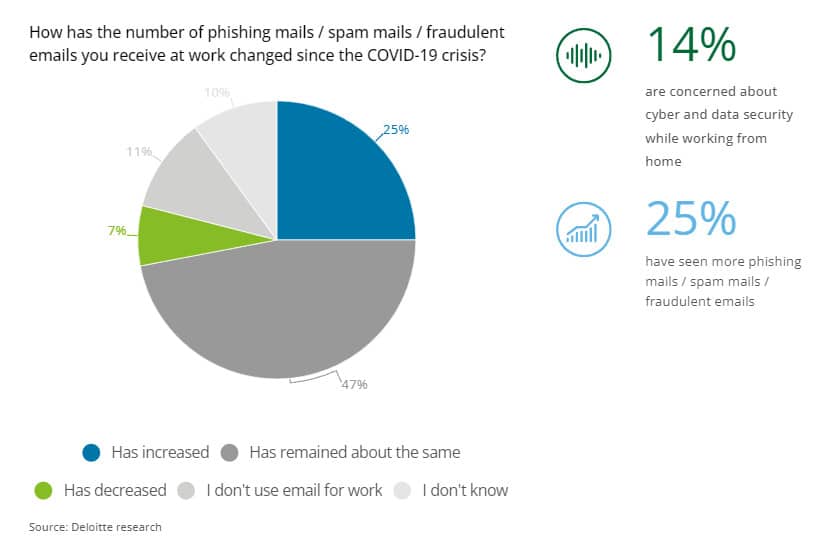
45. Employees cite a 25% rise in phishing emails since the start of the pandemic
Deloitte’s report on Covid-19 cybercrime and working from home showed us that homeworkers have become more cybersecurity conscious since the start of the COVID-19 pandemic, while a quarter of respondents said that they’ve seen the number of scam emails received since working from home increase significantly.



Most of these statistics are not surprising, but not for that they’re less concerning! Hope for a day where things like data protection are not necessary for a higher level of human ethics, but that’s just a dream. Interesting article! But it’s sad too in a sense…