A database of 2.8m records containing sensitive information regarding hundreds of thousands of CenturyLink’s customers was left open online for anyone with internet access to see. The records making up the database were logs from a third party notification platform used by CenturyLink. They included multiple pieces of personal information including name, email address, phone number, and address, along with account-specific information.
CenturyLink is a Fortune 500 technology company that provides residential, business, and enterprise customers with a variety of products and services, including internet, phone, cable TV, cloud solutions, and security.
Comparitech discovered the exposed MongoDB database in collaboration with security researcher Bob Diachenko. The discovery was made on September 15th and Diachenko notified CenturyLink that day, but the database had already been exposed for many months by that point. As of September 17th, it was closed.
After alerting CenturyLink and allowing them time to resolve this issue, they requested we hold off on publishing this report. This was to allow time for CenturyLink to conduct an internal investigation and refer the matter to the FCC before notifying their customers.
The database comprised API logs with customer information and contained more than 2.8 million records in total. Because some customers were the subject of multiple records, the estimated number of customers affected is much lower, but still in the hundreds of thousands.
CenturyLink gave Comparitech the following statement:
Since becoming aware of this situation, we have worked to confirm that the security issue has been addressed and we are conducting a thorough investigation of the incident. The data involved appears to be primarily contact information and we do not have reason to believe that any financial or other sensitive information was compromised. CenturyLink is in the process of communicating with the affected customers. We will continue to work to protect customer information. CenturyLink takes the protection of our customers’ information seriously, and we will work to ensure that we earn our customers’ trust.
Timeline of the data leak
The MongoDB database was made publicly available such that no authentication was required to access it. Here’s what we observed:
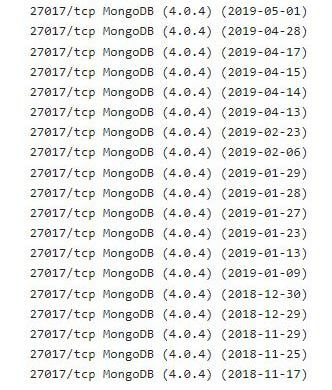
- November 17th, 2018: The database was first indexed on Shodan.
- September 15th, 2019: Security researcher Bob Diachenko discovered the exposed database. He immediately contacted CenturyLink.
- September 17th, 2019: The database had been closed.
- October 17th, 2019: We received notification that FCC investigation had concluded
It appears the database was exposed for around 10 months before being closed to the public.
This would have given malicious parties more than ample time to use the data in various schemes.
What information was exposed?
The exposed MongoDB was affiliated with a third-party vendor. This was a multi-channel notification platform for internal and external communications, for example, between customers, technicians, and agents.
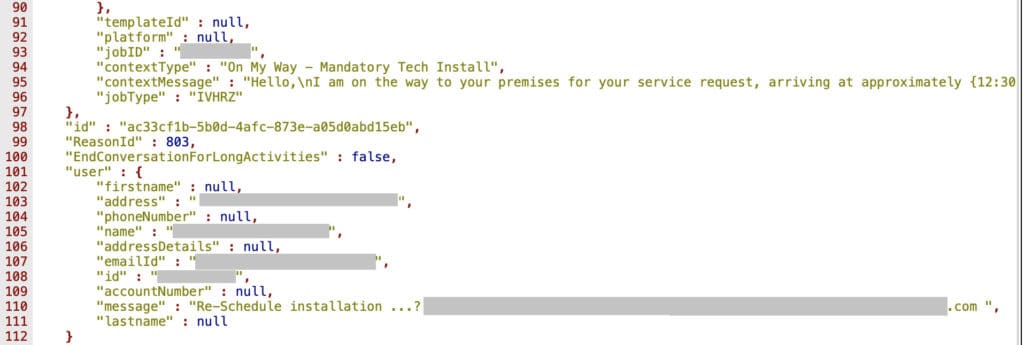
The type of data exposed was API logs of those communications. The customer records were in plain text (not encrypted) and held the following data:
- Name
- Email address
- Phone number
- Physical address
- CenturyLink account number
- Notification logs
- Conversation logs
Among other data, there was information about which CenturyLink services each customer subscribed to, for example broadband or home security. It is unclear whether the subjects were residential or business customers, but based on the addresses, it appears that most, if not all, are residential.
Dangers of data exposure to CenturyLink customers
The personal information exposed in the database isn’t considered highly sensitive in nature. For example, there is no banking information or Social Security numbers. That being said, a set of information such as a person’s name, email address, phone number, and mailing address can be very valuable to criminals.
CenturyLink customers should look out for targeted phishing schemes and related scams that could be carried out over email, phone, or even mail. Knowing that you’re a CenturyLink customer and in particular which services you subscribe to, a fraudster could convincingly pose as a company representative in an attempt to get you to hand over additional information such as your account password or credit card number.
The information pertaining to accounts seems fairly harmless on the surface. However, given the length of time the database was exposed for, it’s possible that malicious parties have had the opportunity to track individual customers over time. The information included in the logs could even assist in physical crimes. For example, knowing that a technician is scheduled to visit could give a criminal an opportunity to attempt to enter a person’s home.
About CenturyLink
CenturyLink is the sixth-largest broadband internet provider in the US with about 4.8 million subscribers as of Q1 2019.
CenturyLink is a high-profile company and has provided products and services to both residential and commercial customers for many years. It sells internet, phone, and TV packages, as well as security and cloud solutions, among other things.
Given the nature of the company’s products and services, many customers have CenturyLink hardware in their homes or on their business premises, such as internet modems and security devices.
The contents of the database indicate that CenturyLink used a third-party vendor for communication with and between customers, technicians, and other members of the company.
This isn’t the first time CenturyLink has been implicated in a leak involving personal information. In March 2018, a class-action lawsuit was launched against the company (along with DirecTV) by a group of consumers who discovered their personal information was freely available online.
The plaintiff who initiated the case ran an internet search for his phone number and discovered a publicly available copy of a bill for a CenturyLink and DirecTV service bundle. It displayed his name, address, phone number, and other information. Around 1,000 other customers were included in the settlement later that year.
How and why we discovered the leak
At Comparitech, we conduct ongoing security research including scanning the internet to uncover exposed databases that may be unintentionally accessible to unauthorized parties. We then act as quickly as possible to minimize the potential risk to affected end users.
Bob Diachenko has many years of experience in cybersecurity and utilizes his vast knowledge to uncover leaks and breaches and analyze the information involved. Once he discovers leaked information, he ascertains its owner and notifies the organization responsible so that the data can be secured.
We then take things a step further and investigate the composition of the leaked data and to whom it pertains. We compile our findings in a report such as this one to help notify those affected. By spreading the word about these instances, the hope is that affected organizations and users can take steps to limit access to and misuse of the data by malicious parties.
Previous reports
This is just one in a series of leaks and breaches that Comparitech and Diachenko have uncovered. Here are some others we’ve worked on:
- 700k Choice Hotels customer records leaked
- 7 million student records exposed by K12.com
- Detailed personal records of 188 million people found exposed on the web
- Stock market listed cryptocurrency retailer QuickBit exposes over 300,000 records
- 5 million personal records belonging to MedicareSupplement.com exposed to public