Botnets are trending in 2022. We’ve scoured the web to find some of the most interesting and relevant statistics surrounding the use of botnets and the concerning ways they are being used.
What is a Botnet?
A botnet is a collection of devices connected via the internet, each running a single bot or series of bots. Distributed Denial of Service Attacks (DDoS) are the most common use of botnets. However, crypto mining and click fraud are other activities performed by botnets to enable hackers to access the device. Once a botnet is set up, the attackers can use Command and Control (C&C) software to take control of it.
One of the main advantages of a botnet is harnessing the computing power of hundreds or thousands of machines. Because attacks come from so many different devices, it hides the attacker’s C&C, making them harder to block or trace.
1. Botnet attacks increased by 23% in a quarter
Spamhaus’s Q4 2021 Botnet Threat Update reported a 23% increase in botnet C&Cs (command and control) attacks from 2,656 in Q3 2021 to 3,271 in Q4 2021.
2. Russia has the most significant proportion of Botnet C&Cs
The report continued, showing that Russia saw a 64% rise in botnet C&Cs between Q2 and Q3 2021. Q3 to Q4 saw a much more dramatic increase with a 124% rise in these attacks.
3. The most used malware type used was credential stealers
Malware droppers, a malware bot that performs a series of malicious activities like downloading and executing additional malware, participating in DDoS attacks, and stealing login information, was the highest recorded malware bot in Q3 2021. Spamhaus’s report showed this was overtaken in Q4 2021 by an even greater threat of credential stealers.
4. DDoS attacks set a new record in the first half of 2021
A 1H 2021 threat intelligence report from NetScout found that 5.4 million DDoS attacks were launched in the first half of 2021, which shows an 11% year-on-year increase. DDoS attacks are typically launched using botnets to overwhelm a target’s servers.
5. DDoS extortion attacks target ISPs
NetScout also reported a rise in cybercriminals targeting ISPs in 2021 via the Lazarus DDoS extortion campaign, focusing on authoritative domain servers. These DNS servers match IP addresses with domain names and provide details on where websites can be found to recursive DNS nameservers.
6. Adaptive DDoS attacks increased in 2021
In 2021, attackers developed adaptive DDoS attack strategies to evade traditional mitigation techniques. Adversaries tailor each attack to bypass several layers of DDoS mitigation for both cloud and on-premises-based attacks.
7. The finance sector is the most targeted industry for botnets
Interpol’s ASEAN Cyberthreat Assessment 2020 measured how botnets affected different organizations based on their industry. The report found that the finance sector and its customers were prime targets in 2019. Attackers aimed to gain remote control of victims’ computers to harvest personal data such as banking details or to install and spread other types of malware.
8. Gafgyt and Mirai IoT botnets make up half of all DDoS attacks
The NetScout 1H 2021 report also showed that adversaries use tracked botnet clusters worldwide to facilitate over 2.8 million DDoS attacks. Gafgyt and Mirai botnets made up more than half of these attacks. The report states, “Ransomware gangs added triple-extortion DDoS tactics to their repertoire. Simultaneously, the Fancy Lazarus DDoS extortion campaign kicked into high gear threatening organizations in multiple industries with a focus on ISPs and specifically their authoritative DNS servers.”
9. Networks in the LatAm region hosted the most active botnet C&Cs
Spamhaus reports the Latm region hosted 60% of active botnet C&C listings in Q4 of 2021. The graph below shows the networks that hosted the most significant number of C&C botnets in the final quarter of 2021. Spamhaus explained that the hosts in the chart either have an abuse problem or don’t take the required action when abuse reports are received.
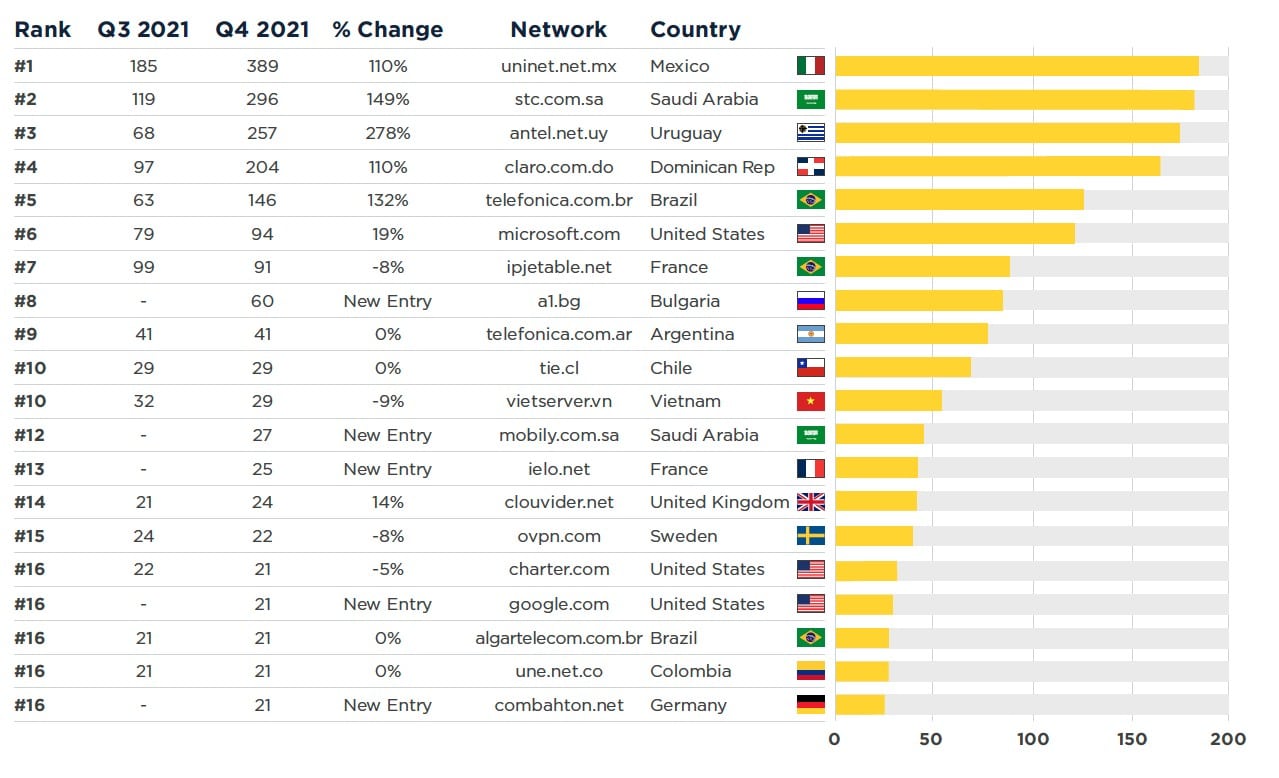
10. Canada has the most abused domain registrar overall
The United States and China came in the top three locations where the most domain registrars are abused, with 926 and 864 botnets respectively at the end of 2021. Meanwhile, Canada swooped the top spot with the most botnets overall at 1115, claiming over 23% of the total botnets identified in Spamhaus’ survey.
11. 1 in 20 IoT devices are protected by a firewall or a similar software
Enisa’s 2020 Botnet report showed that 7.7 million IoT devices connect every day, and of these, at least one in 20 is backed with firewall protection or similar software.
12. Credential theft is on the rise
Enisa’s findings showed that 60% of botnet activity is associated with stealing user credentials.
13. 300,000 instances of Emotet were observed in 2019
Enisa found a significant increase in notifications of Emotet botnet traffic in 2019, up 100,000 from the previous year. In comparing the second half of 2018 and 2019, researchers believed Emotet botnets surged by 91.3%.
14. Mirai variants increased significantly in 2019
There was a 57% increase in Mirai botnet variants identified in 2019. Mirai variants are typically used for brute force attacks on IoT devices. These attacks increased by 51%, while web exploits rose 87% in 2019.
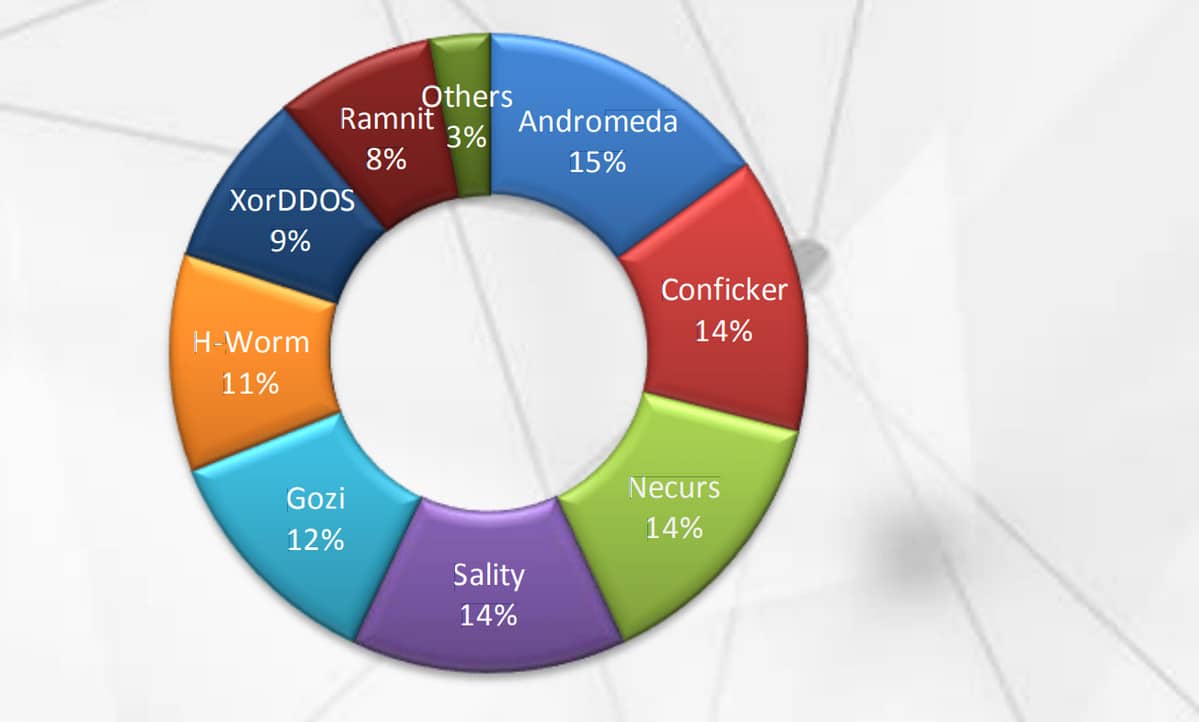
15. The Andromeda botnet dominated in 2019
Although the Andromeda botnet was dismantled in 2017, Interpol reports that it was the most dominant botnet variant in the first half of 2019, accounting for 15% of all botnet infections. It was closely followed by Conficker, Necurs and Sality with 14% each respectively.
16. Gafgyt grew by 3.9 times in 2019
The Botnet Trend Report from NSfocus showed that Gafgyt was still very much active in 2019. There was 3.9 times more malware compared to the previous year, and the average number of C&C servers rose by 34.5%.
How Do Botnet Takeovers Work?
The first step for an attacker to create a botnet is by obtaining or creating malware that can be remotely controlled over the internet.
The attacker deploys malware on the target computer over the internet. This might be by hosting the file on a compromised website for a victim to download, sending the file as an email attachment, or sending a fake URL via a messaging app that infects the device when the user opens the link. The hacker could also scan the web for vulnerable IoT devices to perform brute force login attempts to infect the device remotely.
Once a computer is infected, it makes the hacker’s job easier to spread the infection to other devices that interact over the internet. For example, the hacker could set up the malware so that the infected system sends spam emails to other systems to spread the infection, thus giving them control of a larger botnet cluster.
The malware used is often a trojan-style variant disguised as a legitimate file hiding behind an executable. Opening the executable is enough to spread the infection to another device, but sometimes IoT infections (see example below) like Mirai don’t require any user input to infect and spread between devices.
Examples of botnet attacks
Malware used to create a botnet comes in many forms, but the following examples are some of the commonly used methods to trick users into opening an infected file:
- You visit a compromised website (without knowing) to find a valuable piece of software designed to speed up your computer. You download the executable, and it has the filename you expected, so you go ahead and open it. This infects your device, allowing the hackers to create a botnet.
- Someone sends you an email message, the sender looks authentic, and an image attachment or a billing agreement asks you to act urgently. You open the attachment, but it’s not a PDF or JPG, but an exe containing malware ready to infect your device.
- Malvertising is a new method attackers use to infect a device. They inject malware into a pop-up ad or a banner ad. When you visit the compromised website, you don’t even need to click the ad to get infected, sometimes it’ll auto-download a file to your device containing the infection needed to create the botnet.
- An IoT (Internet of Things) botnet attack called Mirai (named after a popular anime TV series) emerged in 2016 when a botnet consisting of 100,000 computers was created after being infected with malware. Mirai launched attacks against major cyber security organizations and generated traffic volumes in the region of 1Tbps, which took down a significant part of their infrastructure. Mirai began by sending TCP SYN probes to random-root IPV4 addresses on Telnet TCP ports 23 and 2323. Once it scanned and detected open Telnet ports, it began performing brute force login attempts to infect and spread the malware to more computers.

