Update: Wireshark v2.0 has been released since this article was first published. The following tutorial is for Wireshark version 1.12.8, which is still available for download.
Do you know where your data is stored? Now more than ever this is an essential question to ask yourself. With all the hubbub surrounding mass surveillance, Safe Harbour, and data privacy, the geographic location of data you store online greatly affects who is allowed to see it, be it government authorities, corporations, or even hackers.
Unfortunately, it’s not always an easy question to answer. Many cloud storage providers don’t openly disclose where data is stored on an individual user basis, and many of them have servers all over the world, like Google, Microsoft, and Amazon. Even if a company does divulge the location of its data centers, how much do you trust it?
For these reasons, we’ve come up with a method to track your data transfer to its destination. To do this, we’ll use a free utility called Wireshark. It’s a network protocol analysis tool usually reserved for IT nerds and hackers to monitor the flow of internet traffic. We’re going to use it to figure out where in the world your computer is sending data when you use a cloud storage or backup service.
How to pinpoint where your data is being transferred to using Wireshark
Step 1: Download and install Wireshark on your computer. Windows, Mac, and Unix are all supported, though this tutorial will just cover the Windows version.
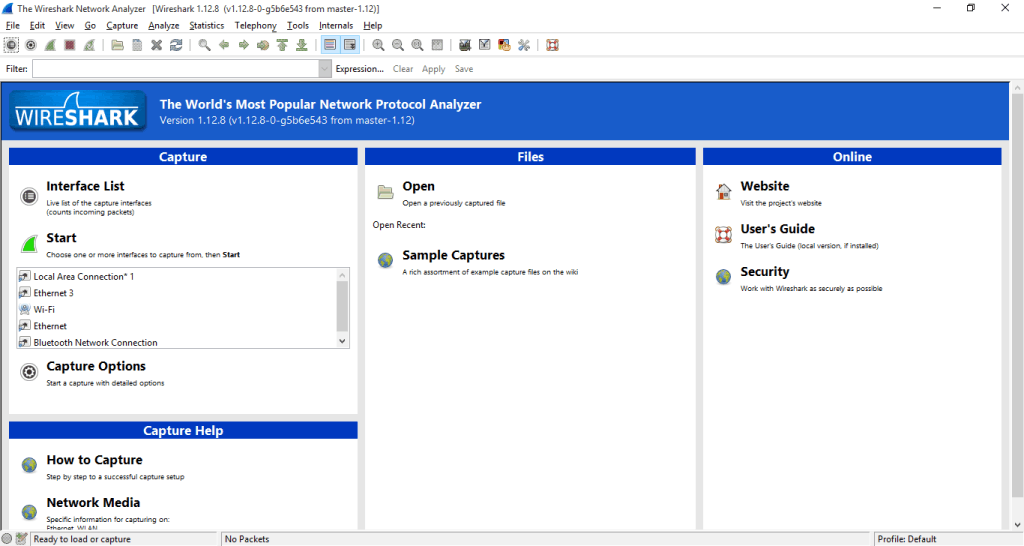
Step 2: Start up the application. You should see a GUI like this:
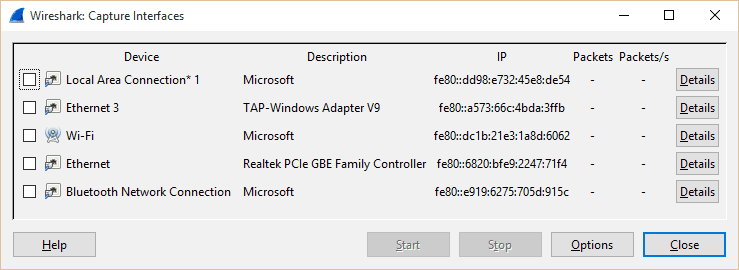
Step 3: Before we start capturing all your network traffic, let’s make sure everything is in place. Click on Interface List and make sure the method you use to connect to the internet is listed. For me, that’s Wi-Fi. For others, it may be ethernet. You may see some numbers listed under “Packets” when you navigate to a new web page or do something else that uses that connection. You don’t need to check anything; just make sure it’s listed and close out of the window.
Step 4: Next we need to do a little preparation. Find a small file to upload to your cloud storage or backup provider of choice. For the purposes of this tutorial, I’m going to use Google Drive. Don’t upload it just yet, but keep it handy in a separate file explorer window. Also, close out of any apps that connect to the internet that you don’t need. This will help us narrow the search.
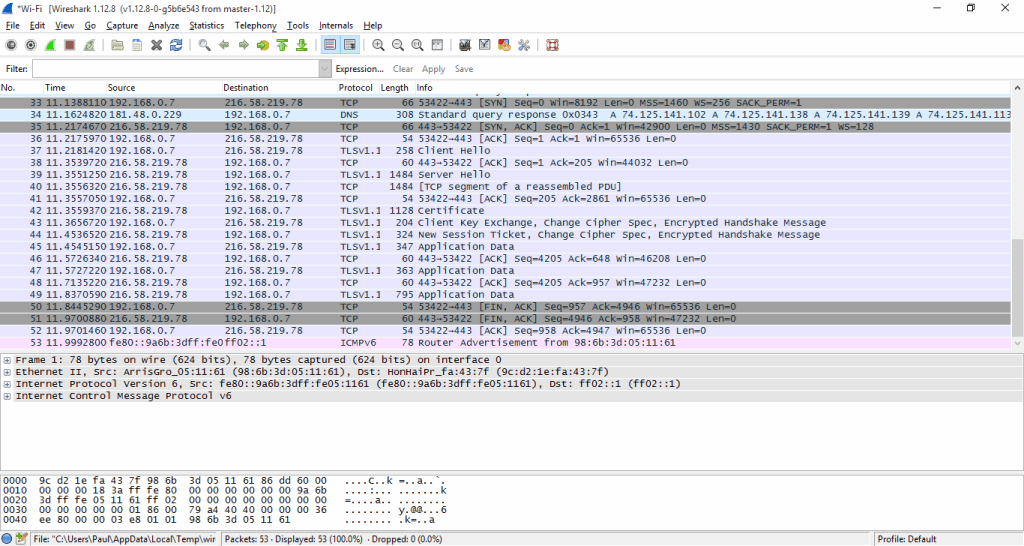
Step 5: Back on the main GUI, under “Start”, you’ll see those interfaces listed. Click to highlight the one you’re using to connect to the internet, then hit Start. Next you’ll see a quickly growing list of every packet sent to and from your computer. Go ahead and hit the red square Stop button. Obviously, we don’t need to capture all that traffic as most of it is unrelated to your cloud backup/storage. You’re Wireshark application should look something like below. If not, something is wrong, and you need to troubleshoot using Wireshark’s website.
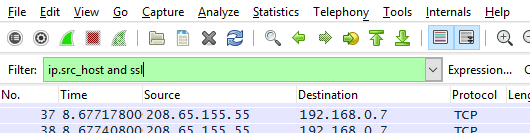
Step 6: If you’re new to this sort of thing, Wireshark can look pretty intimidating. But don’t worry, just keep following along and we’ll make this as painless as possible. Enter the following capture filter into Wireshark: ip.src_host and ssl
Hit Apply. The input bar will turn green if the syntax is correct. If it’s red, check for typos. This assures we only see outgoing traffic, i.e. uploads, from the host computer. We’re additionally using an SSL filter because the vast majority of backup and storage services will at least do you the courtesy of encrypting the transfer of your data. SSL is the most common encryption protocol. If your transfers aren’t encrypted for some reason, they will probably be listed under a normal TCP protocol. Wireshark has a ton of filters you can use, but we’ll stick to these for now.
Step 7: Hit the green shark fin to start another capture. When Wireshark asks if you want to save your previous capture, just click “Continue without saving.”
Step 8: With the capture running, upload a small file, like a text document, to the cloud. Immediately after, go back to Wireshark and halt the capture. There should have been a flood of packets that appear almost simultaneously as the file was uploaded. That’s where we begin the search.
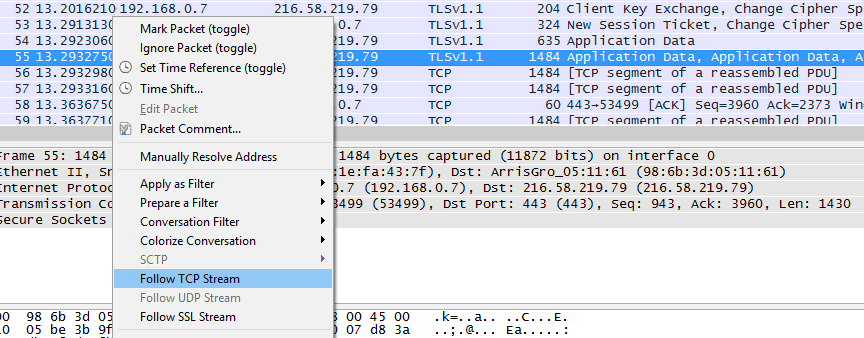
Step 9: This next part might take some trial and error. You need to find the packets sent to the cloud server. If you’ve followed all the above steps, it shouldn’t take long. Look for an entry with SSL or TLS protocol and a relatively long length. Right click it and hit Follow TCP stream.
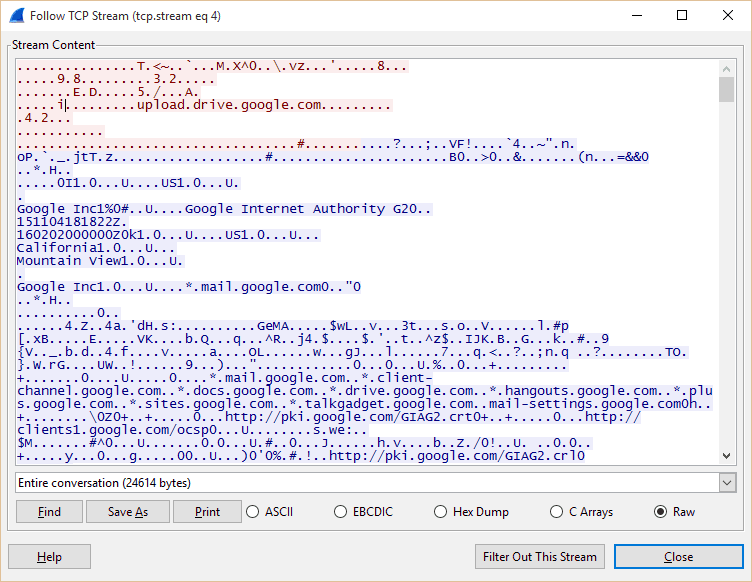
Step 10: Another window should pop up showing you the contents of that packet. Near the top should be some info indicating whether this is one of the packets we’re looking for. In this example, you can clearly see lots of text stating that this packet went to Google Drive.
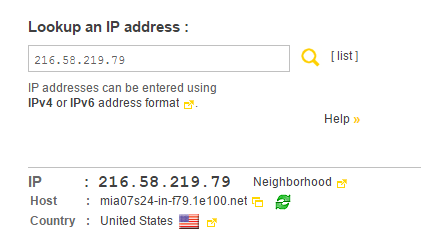
Step 11: Once you have confirmed the packet is part of your upload, close out of the pop up window. Open a browser and go to this website. Input the destination IP address of the packet under “Lookup an IP address:” and hit enter.
Step 12: Among some other data, you can now see the destination country of your data. In this case, it’s the United States. Wave to the NSA as they go past.
What this method doesn’t account for
So now you know the destination country of your data, but there are a couple caveats that this method doesn’t account for. A backup service can still choose to migrate your data from one server to another, possibly in another country. This is unlikely as it’s just more time and effort for the provider, but it’s possible.
Another more common catch with cloud storage and backup providers is geo-redundancy. This means copies of your data are stored on more than one server in geographically diverse locations. Backup and storage providers do this in case of disk failure and other hazards–if one server goes down, another is immediately available. The Wireshark method can’t account for geo-redundancy, but your data is probably at least all stored in the same country. Probably.
Theoretically, this method can be used for any sort of cloud data upload or backup: Facebook, iCloud, Evernote, etc. If you want to do some more sleuthing, learn more about Wireshark and it’s capabilities. It’s a powerful tool, but please be responsible!








Thanks Paul; very helpful for a newbie.
I ended up using http://www.iplocation.net for the geo-lookup. As you probably already know, it uses a number of different lookup sites so you can get a ‘consensus’. Also give more detailed location info (city, lat/long).