Comparitech spent weeks testing popular free Android antivirus apps. We looked for flaws in the way each vendor handles privacy, security, and advertising. The results were eye-opening.
In many cases, you’re not getting what was promised in the Play Store. A lot of apps can’t accurately detect a virus. Almost all of them are tracking you. And we found a handful of serious security flaws, including a critical vulnerability that exposed user’s address books, and another that enabled attackers to turn off antivirus protection entirely.
Android antivirus test results
Comparitech’s senior security researcher, Khaled Sakr, is responsible for the active testing. He looked at the application itself, its effectiveness, the web management dashboard, and all backend services involved. We also analyzed dangerous permissions and trackers embedded in each mobile antivirus app.
Our testing
In mid-June 2019, we looked at the following 21 Android antivirus vendors:
| Vendor | Play Store ID |
|---|---|
| AEGISLAB Antivirus Free | com.aegislab.sd3prj.antivirus.free |
| Malwarebytes Security: Virus Cleaner, Anti-Malware | org.malwarebytes.antimalware |
| AVL Pro Antivirus & Security | com.antiy.avlpro |
| APUS Security - Clean Virus, Antivirus, Booster | com.guardian.security.pri |
| Brainiacs Antivirus System | com.antivirussystemforandroid.brainiacs.googleplay |
| BullGuard Mobile Security and Antivirus | com.bullguard.mobile.mobilesecurity |
| Phone Cleaner | phone.cleaner.speed.booster.cache.clean.android.master |
| Comodo Free Antivirus, VPN and Mobile Security | com.comodo.cisme.antivirus |
| Emsisoft Mobile Security | com.emsisoft.security |
| ESET Mobile Security & Antivirus | com.eset.ems2.gp |
| Dr.Capsule - Antivirus, Cleaner, Booster | com.estsoft.alyac |
| Fotoable Antivirus & Cleaner | com.fotoable.cleaner |
| NQ Mobile Security & Antivirus Free | com.nqmobile.antivirus20 |
| Zemana Antivirus & Security | com.zemana.msecurity |
| MalwareFox Anti-Malware | com.malwarefox.antimalware |
| Antivirus Mobile - Cleaner, Phone Virus Scanner | com.taptechnology.antivirus.mobile |
| dfndr security: antivirus, anti-hacking & cleaner | com.psafe.msuite |
| Privacy Lab Antivirus & Mobile Security | com.secore.privacyshield |
| Webroot Business Security | com.webroot.security.sme |
| VIPRE Mobile Security | com.ssd.vipre |
| V3 Mobile Security | com.ahnlab.v3mobilesecurity.soda |
We found serious security flaws in three of the apps we tested, and found eight apps that couldn’t detect a test virus. In total, 47% of the vendors we tested failed in some way.
Note: Privacy Lab Antivirus & Mobile Security has since been removed from the Play Store
Security
We found misconfigured web services affecting three separate antivirus vendors:
| Vendor | Vulnerability | Risk Score |
|---|---|---|
| VIPRE | IDOR - Premium users with address book sync enabled were at risk of having their contacts stolen | Critical |
| VIPRE | IDOR - All users were vulnerable to an attacker sending fake antivirus alerts | Serious |
| BullGuard | IDOR - All users were vulnerable to an attacker remotely disabling their antivirus protection | Serious |
| BullGuard | XSS - Users of the BullGuard website were at risk of attackers inserting malicious code because of a vulnerable script | Serious |
| AEGISLAB | XSS - Users of the AEGISLAB web dashboard were at risk of attackers inserting malicious code because of a vulnerable script | Serious |
VIPRE Mobile, AEGISLAB, and BullGuard all had flaws that could put user privacy and security at risk. In this case, all three vendors worked with us in June and July to patch the flaws in their app before we published this report. We can confirm all vulnerabilities were fixed.
Performance
We found the following mobile antivirus apps couldn’t detect a dangerous test virus:
- AEGISLAB Antivirus Free
- Antiy AVL Pro Antivirus & Security
- Brainiacs Antivirus System
- Fotoable Super Cleaner
- MalwareFox Anti-Malware
- NQ Mobile Security & Antivirus Free
- Tap Technology Antivirus Mobile
- Zemana Antivirus & Security
The Metasploit payload we used attempts to open a reverse shell on the device without obfuscation. It was built for exactly this sort of testing. Every Android antivirus app should be able to detect and stop the attempt.
Privacy
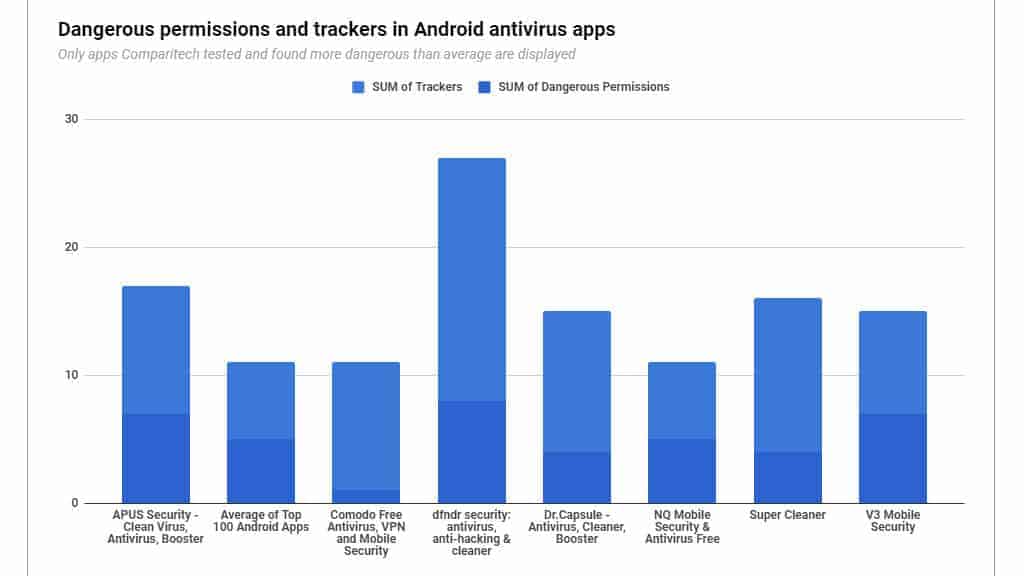
We used information from the Exodus mobile privacy database to look for dangerous permissions and advertising trackers. Here’s what we found:
Mobile advertising is a huge business, and vendors can earn a lot of money displaying targeted ads. But in order to target them, advertisers need information about users’ personal habits and preferences. So trackers send information about browsing and search history back to advertisers, who use it to target and serve mobile ads.
In our analysis, dfndr security used more advertising trackers than any other free antivirus solution. The sheer number of advertising trackers the app referred to is impressive. As far as we can tell, dfndr uses just about every ad exchange there is to serve targeted ads.
dfndr also requests permission to access fine location data, access the camera, read and write contacts, look through the address book, and grab the IMEI (unique ID) and phone number of the device.
VIPRE Mobile’s failures
We found two vulnerabilities, one critical and one serious, which we disclosed to VIPRE. They worked with us to implement a fix, and we can confirm the vulnerabilities have been patched.
VIPRE Mobile leaked user’s address books
Using the online dashboard, we discovered it was possible for attackers to access the address books of VIPRE Mobile users with cloud sync enabled. Based on our proof-of-concept and the popularity of the app, we estimate over a million contacts were sitting on the web unsecured.
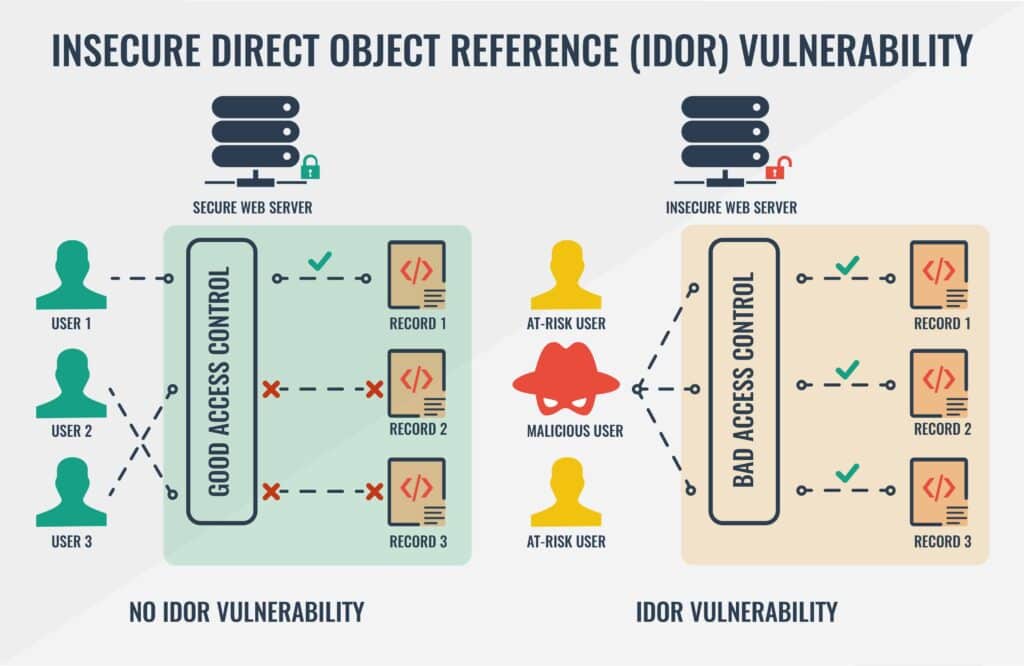
The flaw was caused by broken or poorly implemented access control, which manifests as an insecure direct object reference (IDOR) vulnerability in VIPRE Mobile’s backend. The script responsible only checked to make sure the attacker was logged in. No further checking was done to ensure the request was being performed by the proper device or account.
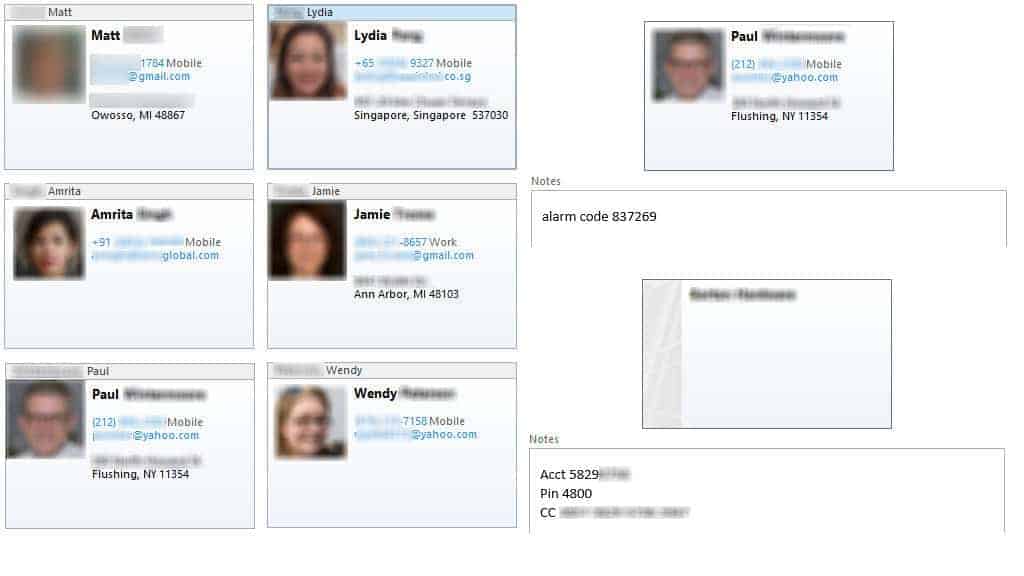
By exploiting that vulnerability, it’s possible for an adversary to cycle through every user account and download their contacts in VCARD format. Many of the leaked contacts contain full names, photos, addresses, and notes with sensitive personal information.
Virus alerts in VIPRE were easily faked
Virus alerts in VIPRE mobile were also easily faked. We found a similar IDOR vulnerability that affects the way virus alerts are reported and displayed. Exploiting this vulnerability let us send entirely fake virus alerts to any user with a valid account.
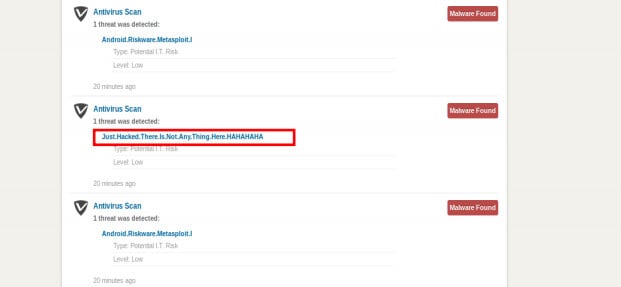
We were able to push fake alerts by capturing the request generated when a virus is found, then manipulating the request to change the user ID and other parameters. The result is an entirely real looking virus alert displayed on the victim’s VIPRE Mobile dashboard.
VIPRE’s access control was lacking
VIPRE Mobile promises a secure backup for your personal data, but what they actually sold customers didn’t come close. The lack of effective access control was startling. We were able to access deeply private information at-will, and post fake malware alerts to any valid account.
“These two VIPRE vulnerabilities are the most critical I found,” Khaled reports, “They affect both the privacy and the integrity of the application. VIPRE should start performing regular penetration testing on all their applications.”
AEGISLAB didn’t lock down their dashboard
We discovered and reported a serious vulnerability affecting AEGISLAB’s web services. They worked with us to fix the problem, and our testing shows it’s been patched.
AEGISLAB’s dashboard was vulnerable
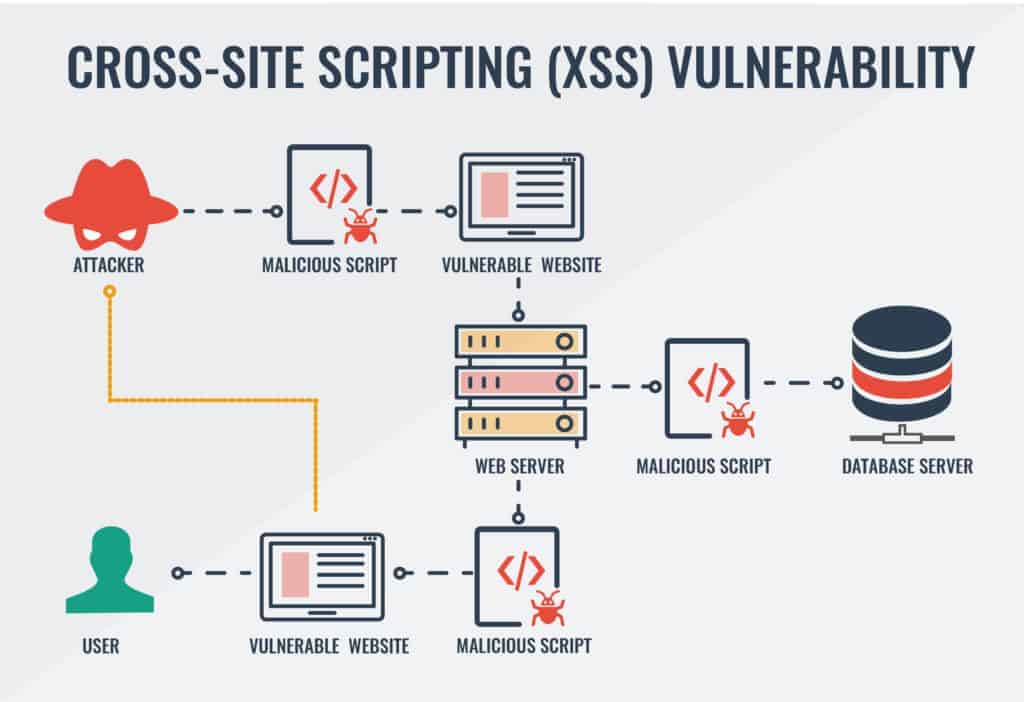
We found several cross-site scripting (XSS) flaws affecting one script running on the my2.aegislab.com domain. Because none of the parameters passed to the script were sanitized, it would have been trivial for an attacker to execute malicious code.
XSS vulnerabilities open a diverse set of doors for attackers. They provide an entry point for further attacks and lend legitimacy to phishing expeditions.
BullGuard vulnerabilities
We reported two security vulnerabilities to BullGuard, both serious. They worked with us to address the flaws, and we’ve confirmed their fix.
BullGuard was very easy to disable remotely
BullGuard Mobile Security was affected by an IDOR vulnerability which allowed a remote attacker to disable antivirus protection. We found it would be trivial for an attacker to iterate through customer IDs and disable BullGuard on every device.
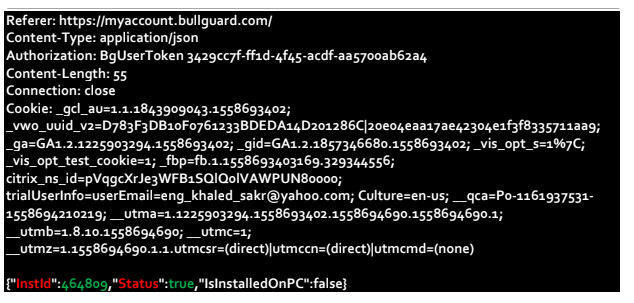
Our testing found the request generated when a user shuts off antivirus protection can be captured and altered. By changing the user ID in this request, antivirus protection on any device can be disabled. Access control did not appear to be in place to ensure the correct user was making the request.
BullGuard welcomes new users
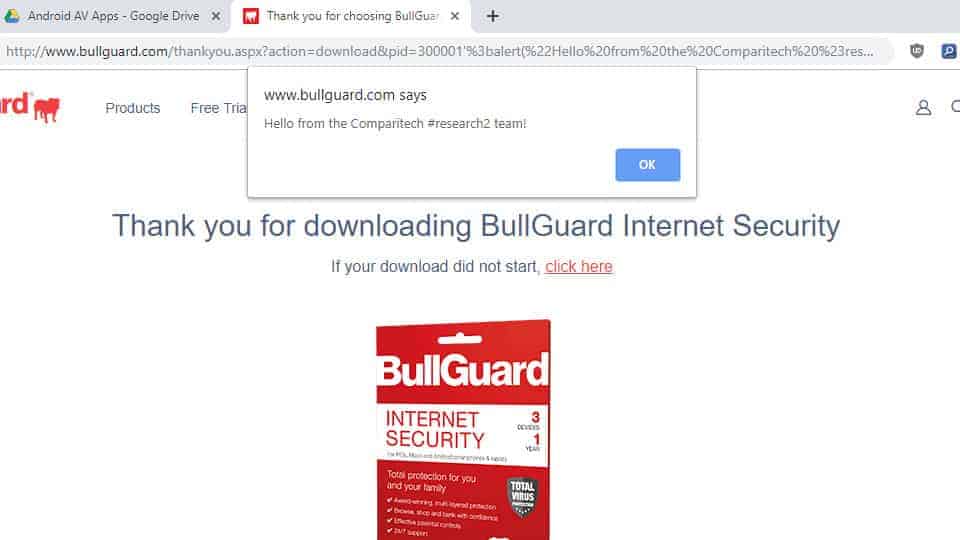
We discovered one of the scripts responsible for processing new users on the BullGuard website is also vulnerable to XSS. The script in question doesn’t sanitize any parameters passed to it, which enables an attacker to run malicious code.
In this case, it was trivial to display an alert on the page. In other cases, adversaries might use this vulnerability to hijack sessions, harvest personal data, or carry out a number of other attacks. For example, high trust websites like BullGuard make an ideal platform for phishing campaigns.
BullGuard’s embarrassing secret
The IDOR vulnerability is as embarrassing as it gets for an antivirus vendor. Users rely on antivirus software as a line of defense for their devices, so when it can be disabled silently and remotely, that’s a devastating blow. BullGuard repaired both vulnerabilities, now they need to work on repairing their reputation with users.
Khaled offered his impressions of the BullGuard XSS flaw, “Cross-site scripting vulnerabilities are common in web applications, but the fact that this vulnerability existed on their main website means they probably didn’t even perform automated scanning on their site before launching.”
What’s wrong with mobile antivirus?
A lot of things are wrong with mobile antivirus software, but there is one big problem affecting the market segment: There just aren’t enough mobile viruses and malware.
In 2018, Kaspersky Labs reported it blocked 116.5 million virus and malware infections on Android and iOS devices. That sounds like a huge amount but, according to their numbers, only 10% of users in the US, 5% in Canada, and 6% in the UK needed to be protected from a mobile threat last year.
So vendors focus on adding features to differentiate themselves, sometimes instead of improving their codebase. And they clearly don’t always do a great job. Every vulnerability we found was with a system incidental to the actual virus scanning.
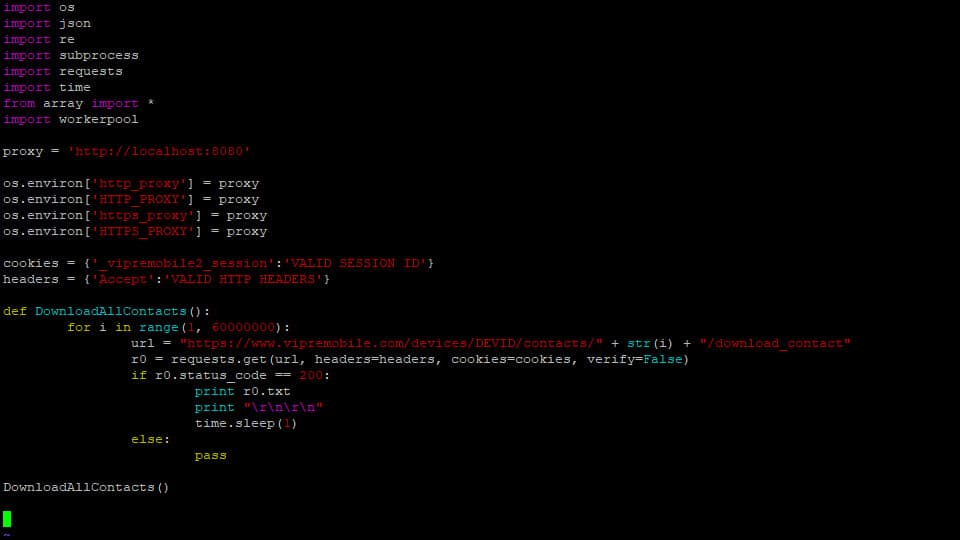
Since mobile malware is uncommon (for now), it’s very easy for vendors to put out an inferior product without users noticing. In that environment, bad apps with new features get popular, and there’s nothing the Play Store algorithm likes more than recommending popular apps. So the cycle continues.
Is there a solution?
“Unfortunately in many organizations, the business side wins over the security side,” Khaled told us, “Like in the case of VIPRE Mobile. I would say that any competent penetration tester could have identified these vulnerabilities.”
“More businesses need to pay attention and make sure that security is tackled at the beginning of a project, and alongside application development, instead of at the end when it’s too late.”
Let’s hope they listen, because there are still too many bad, broken, and insecure Android antivirus apps out there.



This is a great article that addresses the need for mobile security to be improved through all products available to Android users. We are excited to say that we’ll be releasing something to replace the VIPRE Mobile Security very soon. We have begun the process to end-of-life this very dated, old technology to make way for something new and extremely more effective.